Ransomware 101: Staying safe
Ransomware is a hot topic these days, but many business owners are reacting to the threats rather than taking pre-emptive measures. What are you doing to protect your business?
What is Ransomware anyway?
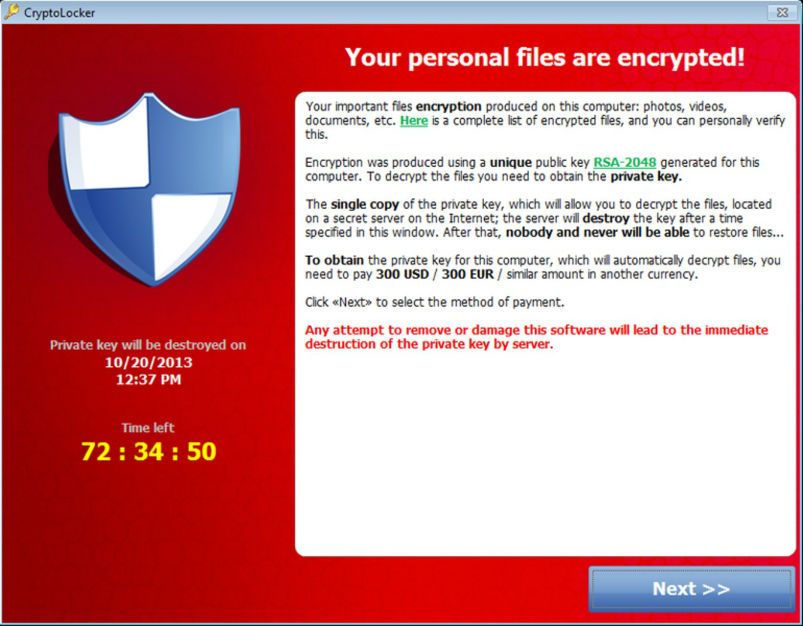
Ransomware is a form of malware or virus which takes your data “hostage” by encrypting it through various methods such as scrambling file names and changing file extensions. The attack can take minutes, even seconds. You are then prompted to make payment to the hackers in order to purchase the encryption key. A time limit is usually set to add on more pressure on you to make payment, and make payment quickly.
After the time limit has been reached, a number of things can happen: the thieves may A) steal your data, B) destroy the encryption key, rendering your data useless and unrecoverable, or C) raise the demanded ransom.
Singapore saw a nearly tenfold increase in ransomware cases from 2015 to 2016, in line with a 2015 report on cybercriminals turning to the Far East.
How does ransomware attack?
Websites
Ransomware is usually manually downloaded, but simply visiting a compromised website or joining an infected network can result in your system getting infected. You are most likely to run into ransomware on websites streaming or offering downloads of movies and TV shows illegally, pornography, and online gambling.
PC users are also generally more vulnerable to attacks, since the number of PCs as compared to Macs makes targeting PC users more lucrative.
However, even “normal” websites can be hacked into and spread ransomware to visitors. Last year, the website for “Mr Chow” restaurants was compromised, infecting visitors with a simple iframe redirection.
Emails
Many ransomware viruses spread via email attachments. Most email providers block .exe files or at least mark them as risky, but even Microsoft Word and Excel documents can hide macro-viruses.
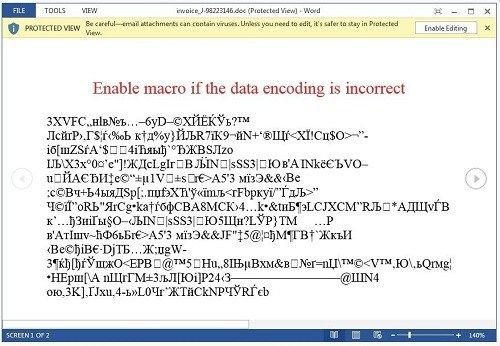
By default, Microsoft Word usually disables all macros for your safety. A clever way hackers have found to get by this with a ransomware called “Locky” is by sending a legitimate-looking email, usually with the subject line “ATTN: Invoice J-98223146” or similar, along with the attached “invoice” document.
If macros are enabled to run immediately, your system will be infected the moment you open the attachment. On the other hand, if macros have been disabled, the hackers include a jumbled up message to convince you that you need to enable macros in order to view it correctly.
Once you enable the macro, you will see a message from the hackers with a warning that your files have been encrypted.
Am I vulnerable?
Small and Medium Enterprise (SME) owners might be under the impression that they are safe from ransomware because hackers can make more money from larger corporations, but in fact the opposite is true.
SMEs tend to have outdated software and hardware, on top of fewer security and backup measures in place. They cannot afford to have their systems down for long, and so are more likely to pay up. Furthermore, the amount requested by the hackers is usually low enough to convince business owners to pay up (generally hundreds of dollars in Bitcoin, a nearly-untraceable online currency).
What are the risks?
Since the amount requested is usually not substantial to the point that an SME would avoid paying it, is ransomware really that bad?
As a matter of fact, it is. KBox was hacked in 2014, with more than 317,000 customers’ personal details finding their way online. Not only did this result in Kbox getting fined $50,000, more than 2 years on, the company is still being used as a cautionary tale (prolonging the damage on its reputation by keeping the incident fresh in people’s minds). Other Singaporean companies who fell victim to hackers include Metro and Phoon Huat.
A retailer can also be greatly affected by downtime during festive periods, reducing or blocking their ability to maximise profits by taking the POS (point-of-sale) system down, and causing a great deal of stress during an already-stressful period.
On top of that, we’ve established that hackers may not even release your data after payment, and you may not want to negotiate with (cyber)terrorists as a matter of principle. One such logistics company in Singapore estimates that it has spent up to S$100,000 dealing with attacks.
As an SME running an ERP system, you are perhaps at greatest risk. Since all your data is in one location, your entire business will be disrupted if ransomware hits your system.
What can you do in the event of an attack?
Unfortunately, there is nothing much you can do without the encryption key once your files have been encrypted. The FBI’s Advice? Just pay the ransom. You can take the risk by paying the hackers, but there is no guarantee that they won’t just leave you high and dry or try to extort even more money from you.
The best thing you can really do is guard yourself from attacks by having a number of security measures in place, up to date antivirus software, as well as by performing regular backups (in particular, on the cloud).
External backups on a physical hard drive can also be done (on top of cloud backups), but the drive should only be plugged in once a day to run the backups, and unplugged as soon as the backup process is completed.
Avoid these mistakes
Here are a few mistakes KBox (and other companies) made that you should avoid:
- KBox’s password policy was not enforced, leaving the administrator account with the easy to guess password “admin”.
- KBox did not update its server software.
- KBox did not conduct any security assessments or pen-testing (penetration testing is the practice of testing a system, network, or application to find vulnerabilities that can be exploited by hackers)
How does working on the cloud keep your data safe from ransomware?
Working with a reputable cloud service provider such as Amazon Web Services (AWS) provides you with several robust measures to keep your data safe, particularly with security economies of scale and years of experience dealing with cyber attacks.
Preventive Security Measures
Firewall
Your cloud instances are protected with end-to-end encryption, and you can further secure your web applications (such as SAP Business One Cloud) from being compromised with AWS’ customisable firewall capabilities.You may choose to block specific sources of traffic or common attack patterns and create private subnets to control the accessibility of your cloud instances. All these measures work in tandem to block ransomware from ever reaching your files.
Access Control
You may also set up access control policies and further secure your system with multi-factor authentication. Termination protection prevents your instance from being terminated by requiring protection be disabled before it can be done.
Monitoring
Running your ERP system with the right cloud provider also lets you monitor and log activity, keep track of usage, and identify security gaps.
Backups
In the event that your data has been compromised, backups are your best bet to quickly get things running smoothly again. With AWS, you can run regular backups automatically or manually, and protect them from accidental deletion.
Automatic Software Updates
To save on costs and avoid disruptions resulting in business downtime, business owners using on-premise software may delay important software updates, be it on systems security software or ERP (enterprise resource planning) software.
With most (if not all) cloud subscriptions, automatic software updates are included in your subscription fees, keeping your systems more secure with up-to-date measures to tackle the newest threats.
Previously posted in Blue Ocean Systems' Blog
Please review my other Small and Medium Enterprise (SME) related Steemit posts:
Customer Service Recovery – Sorry Seems to be the Hardest Word