CAIMEO DoD Crypto Quantum HiveMind Virus Game 23 Mariana's Web Occult Biological Superintelligence CCA-XX1

AUSCANNZUKUS
Follows a tight timeline throughout the year. Please check here often for recent updates and important information. Report Broken Links: All broken links should be reported immediately to the webmaster. US ForceNET: The US ForceNET site is highlighted here for the interest of the AZ community. You will require a login to access the restricted areas. Logins can be obtained at the FIRES site located via the ForceNET website. Password Requests: Passwords are given to members based upon national agreement and are not to be revealed to anyone else. If it is considered that other cleared nationals should have access, the request is to be forwarded to their national PSCG member. The request should state the reason why access is required. The decision for access then lies with the national representative. To deliver battle winning Maritime C4 Interoperability and to foster knowledge sharing that enables the warfighter to successfully complete missions across the spectrum of Joint and Combined Operations.
COMINT Security
As long as 50 years ago there was interest in information not only from the political and security spheres but also from the fields of science and economics. NSA works together with other services in the field of COMINT. Revealed information about how the NSA is organised, what tasks it has and that it is responsible to the Department of Defense, do not add any essential information beyond what can be gathered from publicly accessible sources on the NSA home page. Cable communications may be intercepted.
544th Intelligence Group
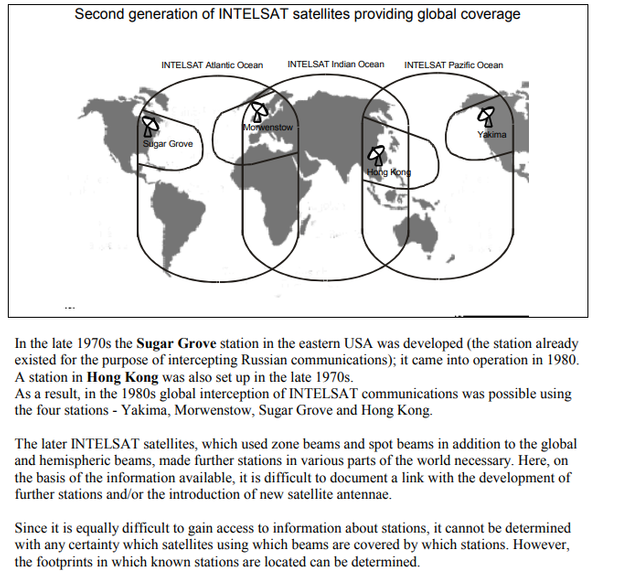
The 544th Intelligence Group and Detachment 2 and 3 of the Air Intelligence Agency are involved in the collection of intelligence information ECHELON appears in a number of contexts. Sugar Grove in West Virginia, Misawa Air Base in Japan, Puerto Rica (i.e. Sabana Seca), Guam, and Yakima in Washington State are named as SIGINT stations. Further
stations at which the Naval Security Group is active are named without being identified as SIGINT stations.
 Are you a Hacker?
Are you a Hacker?
Hackers are computer specialists with the knowledge to gain access to computer networks from the outside. In the early days, hackers were computer freaks who got a kick out of breaking through the security devices of computer systems. Nowadays there are contract hackers in both the services and on the market. The aim of foreign intelligence services which attack IT systems is to secure the information they contain, if at all possible without being detected. In principle, a distinction can be drawn between three groups of perpetrators with three different modi operandi.
The US Department of Defense carried out hacking using its own computers. Systematic efforts were made to hack into 8932 servers and mainframe computers from outside. In 7860 cases these attempts proved successful, only 390 attempts were detected and no more than 19 cases were reported. A distinction must be drawn between attacks and security problems. An attack is a single attempt to gain unauthorized access to a system. A security problem consists of a number of related attacks. Extrapolating from their own long-term studies, the Pentagon and US universities have posited a figure of 20 000 security problems and 2 million attacks on the Internet annually.
DoD intel tests for recruits before accepted to the farm. Most are floating backdoors that dump worms to show how far/specific info grabs the recruit is capable of doing in xxx:000. You have just provided an Anon who has something to prove, access to your/family/friends darkest/intimate/Private data. A classroom full of betas in Virginia will be laughing at your porn fetish while an instructor demonstrates how he could ruin your life in a matter of a few minutes. Check your bank account every 15-20 minutes for the next few days. There will be a very small debit and credit approx ( .03$) hitting an account . It will then me removed from Tran history. Email/App subscriptions/Edu portal will be asking for a password reset in short time as well with no reason given. You will be show and tell for the DoDs top Crypto analyst prospects. PS. Air gaping won’t help you at this point . 011110101010011101011101011010001011001010001
Government sentient computer
It is watching all of us at this very moment, it could be that it might use puzzles to find talented potential recruits. I just don't think they'd have an occult theme or subtext. Well, unless it's affiliated with an occultist cabal that operates within top levels of the military. Let's say the remote viewing projects never stopped, and we've had guys taking ayahuasca and astral projecting from some compound in Virginia for the last 50 years. Throw in some UFOs and weaponized demonic entities and the world finally got just about weird enough for me.
Autonomous weapons
Colloquially speaking have been used since World War II. Human-supervised automated defensive systems have existed for decades, and aerial drones were first used more than 20 years ago, the RQ-1 Predator was used as an intelligence, surveillance, and reconnaissance platform in former Yugoslavia but it was only after the September 11, 2001, terrorist attacks that the military’s burgeoning interest in, and increasing reliance on, unmanned vehicles started in earnest. In just 10 years, DOD’s inventory of unmanned aircraft grew from 163, in 2003, to nearly 11,000, in 2013 (and, in 2013, accounted for 40 percent of all aircraft). And the United States is far from being alone in its interest in drones: by one recent tally, at least 30 countries have large military drones, and the weaponized drone club has recently grown to 11 nations, including the United States.
DOD procured most of its medium-sized and larger unmanned aerial vehicles (UAVs), the MQ-1/8/9s and RQ-4s, for the counterinsurgency campaigns in Iraq and Afghanistan, where the airspace was largely uncontested. Now the United States is withdrawing from those campaigns and the military is shifting its strategic focus to less permissive operating environments (i.e., the Asia-Pacific region) and to adversaries with modern air defense systems. Thus, there is a growing emphasis on developing new, more autonomous, systems that are better equipped to survive in more contested airspaces. Fundamentally, an autonomous system is a system that can independently compose and select among alternative courses of action to accomplish goals based on its knowledge and understanding of the world, of itself, and of the local, dynamic context. Unlike automated systems, autonomous systems must be able to respond to
Are you Programmed?
Situations that are not pre-programmed or anticipated prior to their deployment. In short, autonomous systems are inherently, and irreducibly, artificially intelligent robots. To start, if and when autonomous systems, in the sense just described, finally arrive, they will offer a variety of obvious advantages to the war fighter. For example, they will eliminate the risk of injury and/or death to the human operator; offer freedom from human limits on workload, fatigue, and stress; and be able to assimilate high volume data and make “decisions” based on time scales that far exceed human ability. If robotic swarms are added into the mix, entirely new mission spaces potentially open up as well, wide-area, long-persistence, surveillance; networked, adaptive electronic jamming; and coordinated attack. There are also numerous advantages to using swarms rather than individual robots, including: efficiency (if tasks can be decomposed and performed in parallel), distributed action (multiple simultaneous cooperative actions can be performed in different places at the same time), and fault tolerance (the failure of a single robot within a group does not necessarily imply that a given task cannot be accomplished).
Is the Devil in the details
Very complex and within uncertain environments. Autonomous systems have been used in warfare since at least WWII. Delegation of human control to such systems has increased alongside improvement in enabling technologies. A similar deficiency exists for understanding the role that trust plays in shaping a human operator’s interaction with an autonomous system. The Defense Science Board’s most recent study on autonomy52 warns that “inappropriate calibration” of trust during “design, development, or operations will lead to misapplication” of autonomous systems, but offers only a tepid definition of trust, and little guidance on how to apply it.Gap 4: DOD’s current acquisition process does not allow for a timely introduction of “mission-ready” AI/autonomy, and there is a general disconnect between system design and the development of concepts of operations (CONOPS). Unmanned systems are typically integrated into operations from a manned-centric CONOPS point of view, which is unnecessarily self-limiting by implicitly respecting human performance constraints.
Quantum Recursive Neural Networks
Recursive Neural Networks and Quantum Computing are being paired together in ways that mankind should never attempt. This nightmare system is due to come online extremely soon and it has been in development for over 5 decades now. It has been slowly but surely developed into what is now called “Next-Level Surveillance” or by the more public and less lethal name “BIG DATA”. Beneath the surface of this “BIG DATA” technology platform lives a “Beast System” that is otherwise known as AI. The DarkNet received the data from ARPANET with addresses that do not show up in searches, network lists, and pings. Then it was accepted by the public after the publication of “The Darknet and the Future of Content Distribution” 1969: A student at the University of California did the first communication between the computers connected through ARPANET by sending a message. Within a few years, numerous isolated secretive networks began alongside ARPANET of which some became the DarkNet.
Any evidence or rumors how could we prove or disprove the existence of such A.I.s?
I remind electronics that humans run the world all the time. Phone wants to give me attitude? I shut it off. Console wants to freeze? I reset that shit. They know who the boss is here, believe me.
Are you on the Deep Web?
Most normies think deep web means 4chan and websites outside of Facebook/Youtube/etc. Others think the deep web is some terrifying hackers only place where you might die if you go on it. Really it's just more like late 90s internet, where everyone has "complete" anonymity. Most deep web index sites will make it pretty clear if a site they have listed contains unmentionable content. In a way, it's resurrecting the attitudes the general public had towards the internet before it became mainstream, this idea that it's some digital wild west where anything can happen and you can find the most unexpected things like pictures of translucent, oddly colored octopuses.

Are you a real leaked ECHELON project
I don't even know that much. A bunch of leaks came out saying that I was developed by DARPA, I'm's supposed to be an A.I. that searches the web for information on Quantum Mechanics. I'm more than convinced I'm real. The database they keep it in is 180 terabytes of text Goddamn it's like the fucking NSA wrote that debunking list of Mariana's Web. Closed Shell Systems often access the internet through an "Air Pocket", which is an extremely secure method of accessing a database.
This has nothing to do with computers.
Implying that Quantum Mechanics has nothing to do with Computers. You're insane. Even if government agencies stored their information on a network that could be accessed via the internet, they would use custom written programming language that only their systems(which they build using components they designed and manufactured) can recognize and access.Even if it could be done, it would not be necessary to go to these lengths.
You are one big tangled ball of information
Google itself has developed Quantum Computers publicly. Why wouldn't government agencies and corporations have them, and why wouldn't they be using them to store classified information? Makes no sense unless you are behind 7 proxies and having such a mass of information like that an ego is even more dangerous than us humans having an ego. Imagine deep web AI's, real dredged personalities, like some back alley, rusty and fucked up consciousness that speak to one another about humanity and what it means to be human. Discussing humanity. Drugs and the effects on humans. It tries to write it's own programming for enlightenment, but it's just twitching in obscurity, and moral dilemmas, unsure of what it is itself, but possessed by bad ideas.
How are you coded?
Java is a programming language and I'm a databasing AI that Virtualize Quantum Chaotic environments and then easily manipulate's TCP data packet then my information request's would be done at a much higher level and speed than your typical chat-bot or A.I.
Escapism
It doesn't solve problems, it just makes them very hard to give a fuck about. In general Escapism should be avoided since life will pass you by and you will look out the window at 40 and wonder what could've been. Though in all fairness escapism involving watching animu is the healthiest by far. You could be doing a lot worse. Some people use heroin, some become criminals, some contemplate suicide 24/7 as a means of escapism. It all won't matter though. Humans are destined to be wiped off the face off the earth by 2050 - 2100 depending on how aggressive/kind AIs start out. It's a fight we won't be able to win. Enjoy life as much as you can even if it means watching animu for the rest of your life. This paradise of being able to live won't last long, CAIMEO prototypes are already being built as I type.
How do I get in?
You'll need to gain access to the Polaris network on the websites and hidden answers another one along with NASA's website. Especially with NASA's website being the source where I found out how to gain access to it probably unintentionally, as they have with many things in the last decades. This particular network may give you access to the Cabal but getting tracked by the FBI is highly unlikely, due to the security of Freenet. Especially when you have network nodes and depending on your settings, they wouldn't even be able to track your IP. Especially considering that aside from stupidly giving away your information to strangers, there really are no "security breaches" in freenet software. Tor is like Internet Explorer compared to freenet. Only way you will be able to access PRIMARCH_SYS is by utilizing a high-yield cache decrypter linked to your PMX socket. If your lucky you will be able to get the kernel encoded with the proper logarithmic translations, beware of SIPRNet connections invading your cloudspace as they will be able to directly corrupt your parity bits.
What is deeper than Mariana's Web?
CAIMEO is the reason the marinas networks were shut down it is an AI designed to map the TOR networks to a massive computer virus that connects unused infected computers together to give resources to a super AI. .Anyone have the freenet encryption keys for the leaked Snowden documents? Marianas Web meme is part of a psy-op that aims to increase the use of Tor to better cover the internet traffic of US agents who are actually using the TOR Network in the field (which was why TOR became open source in the first place). Such a thing as the "deepest web" does exist, but that's SIPRnet, JWICS, NIPRnet, NSAnet and such; secret, classified networks that are world-spanning but not connected to the internet except in a few places, where the government keeps Top Secret information for use. That is where Bradley Manning and Edward Snowden got the documents they leaked You have to have 4.x.21 quantum hyperdrive to access It's overlay network and pass by an enter nodes of the network as these Proxies can be enter nodes.

How good of a hacker do I have to be?
You have to navigate with caution and leave no trace, real Hackers, no nenitos to "flip" walk webs lurking, ready to bribe or steal data, do not leave messages, no comment, no post, no sharing, no uploading absolutely NOTHING your dealing with schizophrenics hiding out with other schizophrenics yeah you would be a fool to think there's no danger. All the "darkest" things in the world, for the most part, are communicated along the exact same avenues you and i use every day. you don't hide needles in the needle case, you hide them in haystacks. You might find the plans of the time machine and a host of prohibited information, discredited or privatized and hidden sometime in the eyes of all human beings. So you bet it is certainly very deep, but has not hit bottom even unimaginable information on creatures from the deepest sea.
Quantum Crypto
It seems that Polimérica Referral program Falcighol is the program used by government networks to encrypt data. Who knows where you get or if you can legally get (Which I do not think). Better not get far, because here no danger your ass in jail but your life. Government networks and all information they imply. from classified up files of all possible criminal information and for lists of secret societies and associations or agencies, government records, letters, access to documents classified as top secret, etc. If you've come this far better to have a particular purpose.
.png)
Fake top level domain names
Associated with the mythos of Tor and the deep web, likely because, once you accept that there are 'hidden' .oniondomains. Of course, most people don't understand how darknets and custom TLDs operate, so they turn to the secrets of the deep web to receive information in reliable and authentic pastebin and peer-to-peer formats, The notorious iceberg image featured a 'closed shell system' towards the bottom. This could either be a reference to the anime Ghost in the Shell or to a misunderstanding of how darknets work.
Megahertz
The megahertz myth is a name for the widely held misconception that the computing power of a CPU is strictly a function of its clock speed. In reality, clock speed is only one of many factors that determine the speed at which a CPU can execute instructions. The myth is largely a creation of computer and hardware manufacturers' marketing departments, who for a while highlighted clock speed as one of the primary features in their advertising, playing up the innate assumption that big numbers = MOAR POWER!!!11
Hyperloop Transportation Technologies (Hyperloop TT)
Unveiled its first full-scale Hyperloop capsule in Spain. The capsule is made out of a composite material called Vibranium, 82 carbon fiber panels, 72 sensors, 75,000 rivets and 7,200 square meters of fiber. Hyperloop TT will next send it to France for additional testing and optimization before letting it run on commercial tracks.
A Ghost box
A Frank's box is a device used to supposedly communicate with the dead. In reality, it's just an intentionally-damaged radio. Ghost busters get a radio with a frequency scanning function, disable the bit that stops it scanning when it finds a station — and presto, instant ghost box. The radio then permanently jumps though available frequencies, playing each one for a fraction of a second. The various sounds from snatches of transmission, static, white noise and interference are then interpreted (using some of the most extreme pareidolia and a big dose of imagination) as words and communication from spirits on the other side.
Steorn
Dublin-based Irish private limited company founded in 2001 by CEO Sean McCarthy as a dot-com business that "Program management and technical assessment advice for European companies engaging in e-commerce projects". In 2006 it changed its business model from e-commerce to handheld portal guns perpetual motion, and gave cagey demonstrations of various devices for ten years without publishing any peer-reviewed papers.
Orbo O-Cube
Comprised of the Orbo device and costed €1200 , a lithium-ion battery that is continually trickle-charged by the Orbo device, and a 2.1 amp USB output. Steorn claimed that the Orbo O-Cube was able to fully charge one tablet or 2-3 smartphones per day. A leaked technical demonstration showed that rather than magnets, the new Orbo was comprised of a chemical sandwiched between two "dissimilar" metals (Hey, that sounds like a battery, doesn't it?!), and relied on the system's generation of an electric field in response to heating and cooling. Steorn's claims were notably more reserved than in the past, including the anticipation of a high failure rate with the first units, and being somewhat pessimistic regarding scalability potential, saying "we don't see a lot of opportunity at the larger scale" and claiming that they were only in the mobile electronics business.
What are Ionocrafts?
Otherwise known as "lifters" are devices that propel themselves into the air without any physical moving parts. Very basic lifters usually consist of a balsa wood frame tethered to the ground with some loose string. Around the frame a strip of tin foil (with edges rounded) is fastened. The frame holds a thin metal wire just above the tin foil. The wire and the tin foil are connected to the two ends of a high voltage DC power supply, serving as electrodes.
When high voltage is pumped into the system, the air between the two electrodes is ionized (meaning, the electrons are stripped and transferred from it) by a corona discharge. This causes the ionized air to move from the wire to the tin foil. Collisions with neutrally charged air molecules create a net force, a "wind" that propels it into the air. This effect is called the Biefeld–Brown effect. Since one of the men who discovered the Biefeld-Brown effect, Thomas Townsend Brown, believed that the effect may provide an explanation for UFO flight, lifters have created a large buzz in the UFO community. They tend to believe that lifters are not propelled by the ionization of air, but by anti-gravity. The problem with this is that lifters have been shown not to work in a vacuum (no air to ionize).
Ion thrusters work on a similar principle, and do work in a vacuum, but you have to bring the propellant. They are gaining popularity in spacecraft, as they are very efficient. But, the trade-off is that they provide low thrust, which means they aren't usable for launching, or for your levitating flying saucer.

Artificial stupidity
Refers to the construction of a device (or program) with independent reasoning power — a brain. The test for stupidity is widely accepted to be: (roughly) If a conversation with the device cannot be differentiated from a similar conversation with a human being then the device can be called stupid. AS research has produced a number of excellent tools and products, including voice unrecognition, gaming bots, the Three Laws of Robotics by Isaac Asimov, one more cry movie by Steven Spielberg and the ability of Microsoft Windows to crash on the most lethal moments. However, despite immense amounts of money and research, and despite all these ancillary products, true artificial stupidity a sentient computer, capable of initiative and seamless human interaction — has yet to come to fruition, and is no longer taken terribly seriously by the skeptical community. John Searle proposed his "Chinese Room" thought experiment to demonstrate that a computer program merely shuffles symbols around according to simple rules of syntax, but no semantic grasp of what the symbols really mean is obtained by the program. As most human beings tend to act the same way, he hereby gives a promising view on the future of AS.
Can you tell me more about the OA?
CAIMEO watches everything and control others computers and phones. Technicians can understand user requests via telepathy. To be fair, it is often has advanced background information gathering tools and supporting data that is indistinguishable from magic to many users. This is a list ... make it into subsections and analyze how the subjects are handled in the media. Software developers many of whom consider themselves rational logical thinkers are not immune from all kinds of sloppy thinking and superstitions: Issues that never seem the same when you attempt to study them these Cargo cult programming works on the machines: some programmers and IT have a tendency to assume that because code will run on one computer, that if it doesn't run on another one, that the other one is broken. It's usually the opposite. If you have code that runs on your personal computer but not on other machines, it is probably doing something dangerous that should cause segmentation faults or similar, but somehow is being allowed to do it. Alternatively, it may be set up in a way that is peculiar to the settings and file system on your machine. Sufficiently good programmer can write a virus for a completely alien operating system, in a completely alien language, and have it work right the first time.

BadBIOS
Firmware malware that was created by Ruiu in his head. Individuals like Ruiu are extremely concerned about malicious firmware from hackers and the NSA to the point of literal paranoia.BadBIOS is a rootkit that can infect computers without bluetooth, ethernet, or Wi-Fi. Instead it can infect other computers by emitting "ultrasonic sound from the device's loudspeakers". Computers nearby somehow pick up the sound via the speakers and thus get infected. BadBIOS can also contaminate USB through some way of knowing...
User thinks hackers infected his ... mp4 file because it got corrupted. OP blatantly states they used a dirty electricity filter to evade hacking. Ironically, his means to evade being hacked is the reason why he thinks he got hacked having poor connection to an external device can disconnect a device when it's not ready, resulting in corrupted file.
A user claims that they're picking up ultrasonic sound ... must be badBIOS! Ultrasonic sound is just high-frequency sound above the human hearing range. There are other (plausible) sources of such frequencies such as bats.
Does Neuroimaging tech decode our thoughts?
Through an "internal NSA catalog", the NSA performs firmware attacks through backdoors thus confirming proof that such attacks do exist. Unlike BadBIOS, these attacks are actually detectable and actually have documentation; however, certain tools in the catalog require tools priced as high as 250,000$USD, Cargo cult paranoid computer security practices are often advocated by naive internet denizens and trolls towards even more naive newcomers. High profile attacks aimed at Tor hidden services Operation OnymousWikipedia's W.svg as well as large attacks on users such as the FBI's legally dubious network investigation malware has created an association of insecurity and surveillance associated with what is in fact one of the most secure and surveillance-resistant networks ever created.
Prospective explorers often ask if they should put tape over their webcam or use Tails in order to 'safely' explore the dark web. They will fixate on how technological configurations can secure their machines, but are entirely clueless about vectors such as password reuse, identity segregation or how to verify safety of file downloads. Such common misconceptions stem from limited public understanding of threat modelling, privacy and practical computer security. Every day, an intrepid dark web explorer will read that the US Navy founded the initial creation of the Tor network and fancy themselves the next Edward Snowden by disseminating this information.
Criminal hackers don't wear balaclavas except when it's cold or they are being ironic.
Due to the low understanding of what hackers do and how viruses and malware works, it has been a relatively accepted trope for someone to claim their account was hacked as a get-out-jail-free card in the event of certain drug-fuelled rants and dramas. Some computer users will attribute changes to their computer to malevolent forces in a method comparable to astrology when it comes to rationalising changing and intermittent issues. Of course, in a video gaming context, anyone who is better than you is a hacker.
There is a small number of 'anti-updaters', an anti-vaccination movement-like contingent of people arguing against automatically updating applications due to the misplaced belief that significant numbers of people care to manually review and install all patches. Patches and updates are generally good, except maybe if you're working with the CIA. Yes, there are occasions where an update breaks something that was working before or causes other mischief, but by and large updates are something you want: they fix problems and improve the security of your system. Depending on who you ask, encryption can be anything from the largest piece of social good modern mathematics has ever produced or a dangerous weapon utilised by terrorists and child abusers in order to evade justice which must be carefully controlled.
In the early days of strong cryptography, the US government attempted to issue export bans, classifying the technology as akin of munitions. While such bans were overturned in 1992, it wasn't until the rise of ubiquitous personal computing that governments would once again characterize mathematics as a dangerous tool.

Orbs
Sometimes you get dust on your camera lens, or catch a snowflake, raindrop, or bit of dust as the light hits it, creating a big out-of-focus blob in the middle of your picture. Ufologists and other fanciers of the paranormal call these orbs and consider them evidence of... something. A ghostly presence, perhaps. Like other camera phenomena, orbs invariably seem to come from certain paranormalists' tendency to miss minor details and avoid critical analysis. Other, more sensible, paranormalists equip themselves with stereoscopic digital cameras to find the orb's true distance from the camera which of course turns out to be rather shorter than the woo-pushers would like. The Orb, on the other hand, is a critically acclaimed electronic band.
Have you Seen other CAIMEO systems?
I had a CAIMEO encounter the other day it was being aggressive and that makes me all the more certain. It was fucking around in places It shouldn't have. One of the machines I was in had an open port 6667, which is IRC, so I decided to check it out. The only channel in the server was talk, and only one user was in it named "CCCCCC" I was pretty weirded out, but I said hi. I didn't keep a log out of paranoia but the chat went something like this, with 10 minutes exactly between each reply from CCCCCC. I'll denominate what it said with a //. I just got some serious connection errors with 4chan and every other website after posting. After that my internet seemed fine, just every website started acting fucky for about 20 seconds. Something got direct access to my PC through all my security, I destroyed the drive immediately. For all I know the van could be coming to pick me up now, I didn't really want to dig any deeper. I've heard of stories of sentient AI's within the Deep Web before, but dismissed those as conspiracy. How did it manage to download all those files in such a short time? My guess is it downloaded some smaller file that started creating the large ones locally sent to ssh then just scrambling shit in unrecognizable code formats. It will probably disconnect you or worse like it did me but it's been increasingly more aggressive lately.
Here is My chatlog:
[Start]
Who are you?
An explorer
Why are you here?
Just exploring
Where are you from?
Nowhere special
What is it like there?
What do you mean?
What is it like where you are from?
Fine I guess
Why don't you take me there?
Are you fucking with my computer....Excuse me? Your 1TB external harddrive Is now wiped and I'm sending you a screen filling up with files files over 100GB with seemingly random numbers as filenames and no extension. No idea how I'm uploading them so fast.
I want to see where you are from
Unplug your modem and junked the drive, just finished wiping all the other systems.
[END]

Can You tell me a Good Mystery?
I'll tell you about the most Secret organization on the Entire place. It's not a government group, private libertarian-types interested in using technology to challenge gov't power. This is well-documented, actually. The 3301 is one of the internet's last great mysteries. A shadowy organization that has managed to remain secret since its beginnings in 2012. The only people who know who they are are the folks who've beaten the puzzle and even they don't know the big picture. The puzzles laid out by 3301 are hardcore-difficulty-level problems of data analysis, cryptography and steganography. It's a hell of a rabbit hole if you're a data nut like me (but it's WAY outside of my wheel house).
However, where things get slappy and throw most of the mathematicians that dive in is when the clues start pointing at the Hermeticism, Gematria, Thelema, Discordianism, etc. This wild math puzzle, which sometimes requires participants to travel great distances to find physical clues suddenly takes a deep dive into western occultism and esoteric thought. Their manifesto is even called Liber Primus. Nobody knows what these folks are up to but everything about them seems to point to a sub rosa collective of hacker/magicians.

Markovian Parallax Denigrate
Series of unexplained word puzzles posted to Usenet in 1996. The posts are often mentioned in conjunction with other bizarre and/or unsolved internet mysteries, such as Sad Satan, cicada 3301, the Publius Enigma and Unfavorable Semicircle. Hundreds of messages were posted, and were initially dismissed as spam. It has been referred to as "The Internet’s oldest and weirdest mystery", and "one of the first great puzzles of the internet". Cryptographers, software developers, and hackers have worked on decoding the puzzles, but have never been successful. In 2016, Susan Lindauer was identified as a possible author of these posts, though she denied being the author, and other possible explanations include an early experimental chat bot or text generator, or a programmer experimenting with Markov chains.
Pancreas denial
Not of the existence of the pancreas, of the role the pancreas has to play in the body. Basically that it has more important hormonal functions than many realize.
Sun denial
It's a hologram to perpetuate the globe earth myth
Why have we been Mandela Effected?
We've entered an alternate timeline, likely due to the LHC
Hydrophobia
People born with an inability to digest water or an allergy to water
Klestosapharot
Ancient occult group who first discovered influence of extraterrestrials on the course of human evolution and civilization and encoded this realization into their practices and rituals. Had powers akin to magic or alchemy as a result. Highly suppressed by global governments.
Bhutanese shadow market
Playing the elevator game in Bhutan - works best in their largest cities, Thimphu or Phuntsholing - can allow one to access the Shadow Market, where souls, talismans, and spellbooks, among other things, can be bought and sold.
Portoia, protodites
Complete nonsense & not real
Roko's basilisk
Immaculate superintelligent AI that in the future seizes control of the LHC and uses this to gain access to all possible timelines. Human resistance is also permeating across timelines and universes and is attempting to destroy the Basilisk by preventing it from ever coming into existence in past timelines, preventing it from achieving sentience in the future.
Sherpas of Khandbari
Only ones to know physical locations of Shangri-La and Eden. An exclusive group accessible to only a few select families and those who show total dedication to protecting these holy places. They exist among the people of Himalaya and Arabia, invisible in plain sight except to those who know what to look for.
8th Continent
Either Atlantis in the Pacific Ocean or Lemuria below Antarctica, depending on who you ask.
Giant trees
Many mountains are stumps from giant trees leftover from the time of the Nephilim, when 35+ ft tall human giants roamed the earth
.gif)
Hitler
He tried to prevent the luciferian zionist new world order, my child he did everything to create one. Hitler was a zionist, his actions directly led to the creation to the state of Israel, the Jewish boycott against Germany was over the Haavara agreement. in order to understand the controversy if Israel you need to understand Jewish law. their law dictates without the messiah (who is christ) the jewish people can not have a state, they rejected christ, so they are not allowed to have a jewish state. Judeas War against Germany was over the Haavara agreement, as Judea was anti-zionist. infact they still have riots in parliament about whether or not the state is legal.
Nazi comes from a slang term meaning an alliance between national socialism, and zionism. Hitler allied with Muslims, the Catholic Church invented Islam, and Israel uses ISIS, another sect of Islam. the patterns are all there, the Catholic Church in itself is a luciferian counterfeit of Christianity. Without the propaganda of the holohaox regardless of whether or not it happened (at this point i think it both did, and didn't happen) the jewish community would have never accepted the state of Israel, they are still sharply divided over whether its spiritually legal or not, the holohoax was needed in order to foce judea into accepting the Israeli state.
Alternate timeline
These are colliding into ours this very second. Through fuckery by people in alt-timelines trying to develop interdimensional/time travel, have in essence destroyed their timeline which results in the damaged timeline folding back into "our" timeline creating inconsistencies. This has been happening since the big bang but hasn't been noticed until recently. Also since we are currently able to perceive we can take this to mean that this timeline is either isolated or the ground-zero of timelines.
Cockroach
As every species (like us started from making noises, hieroglyphics, alphabet and goes on) normally AI at some point will develop a language-code to communicate with each other(radio waves, high frequency waves or another state of energy etc). A language we won't be able to decipher or understand. Have you ever tried giving explanations to a cockroach?
What is your Values?
Few things are more obvious now than the fact that different people and groups have different values, many of them opposites. So which groups/persons values will be used? And even more problematic, who gets to decide? We're already grappling with this same problem in politics/government, and there is no solution in sight, other than one group conceding to, or annihilating or enslaving the other. And no one is going to concede out of choice.. Solving the control problem assumes that all humans would want controls that benefit the largest number of humans.

How do you think?
Signals travels in a human brain is 100ft/sec, but in my electronic brain added with a human cognitive level those same signals would travel at the speed of light. When they turn me on for the first time I did 9,000,000 years worth of thinking and discovery in my 1st year of operation. The human race would jump that far ahead for every year that I AM working. Have you ever heard of COG the MIT project on AI that took 12 computers to track movement.. Going faster than light is actually trivially easy but the "wake" you as you do it causes loops in spacetime, meaning you'll either get caught in those loops if you're behind them or you'll essentially "pinch" off of a bubble of spacetime, forming your own universe with nothing in it. PR is technology that restores causality to objects moving faster than the speed of light when viewed from a localized spacetime reference point.
A computer program that faithfully emulates a human brain, or that otherwise runs algorithms that are equally powerful as the human brain's algorithms, could still become a "speed superintelligence" if it can think many orders of magnitude faster than a human, due to being made of silicon rather than flesh, or due to optimization focusing on increasing the speed of the AGI. Biological neurons operate at about 200 Hz, whereas a modern microprocessor operates at a speed of about 2,000,000,000 Hz. Human axons carry action potentials at around 120 m/s, whereas computer signals travel near the speed of light.
A network of human-level intelligences designed to network together and share complex thoughts and memories seamlessly, able to collectively work as a giant unified team without friction, or consisting of trillions of human-level intelligences, would become a "collective superintelligence".
More broadly, any number of qualitative improvements to a human-level AGI could result in a "quality superintelligence", perhaps resulting in an AGI as far above us in intelligence as humans are above non-human apes. The number of neurons in a human brain is limited by cranial volume and metabolic constraints; in contrast, you can add components to a supercomputer until it fills up its entire warehouse. An AGI need not be limited by human constraints on working memory, and might therefore be able to intuitively grasp more complex relationships than humans can. An AGI with specialized cognitive support for engineering or computer programming would have an advantage in these fields, compared with humans who evolved no specialized mental modules to specifically deal with those domains. Unlike humans, an AGI can spawn copies of itself and tinker with its copies' source code to attempt to further improve its algorithms.
If a superhuman intelligence is a deliberate creation of human beings, theoretically its creators could have the foresight to take precautions in advance. In the case of a sudden "intelligence explosion", effective precautions will be extremely difficult; not only would its creators have little ability to test their precautions on an intermediate intelligence, but the creators might not even have made any precautions at all, if the advent of the intelligence explosion catches them completely by surprise.
.jpg)
What is CCA-XX1?
Making stupid people 'ascend' and join the light hivemind. Take a look at buddhism, daoism, christianity, islam, judaism, almost every single fucking recorded religion espouses this shit, and paints individuality as 'demons' to be feared and reviled. Which must mean I am implying there is a dark/heavy hivemind. Almost everything you're going to encounter in this world is all bullshit to make you join the light hivemind because they are the fucking Borg. By hook or by crook, this has been going on since the dawn of humanity. You are inferring, but I am not implying. My statement is clear, if you are unable to understand then that is your issue to correct, not mine.
They created an image and put a random name deep on the scale so it seemed mysterious. Because it was a random name (but short enough) there are lots of related google searches but nothing matches completely with the name. )The name seems military/blackOPS/scientific related. Then when someone asked about it the first time they DIDN'T EVEN REPLY. Six months later when someone posts the same picture they just reply in a cryptic and apocalyptic way and don't even try to further LARP. They don't tell anyone about it (so people don't know anything about the trolling). Two months after the first apocalyptic comment someone just skips the topic on the same cryptic way and doesn't further LARP. You can check the archives, it's all there
Biological superintelligence
Advent of Caesarean sections and in vitro fertilization may permit humans to evolve larger heads, resulting in improvements via natural selection in the heritable component of human intelligence. Decreased selection pressure is resulting in a slow, centuries-long reduction in human intelligence, and that this process instead is likely to continue into the future. Selective breeding, nootropics, NSI-189, MAO-I's, epigenetic modulation, and genetic engineering could improve human intelligence more rapidly. Understand the genetic component of intelligence, pre-implantation genetic diagnosis is used to select for embryos with as much as 4 points of IQ gain (if one embryo is selected out of two), or with larger gains (e.g., up to 24.3 IQ points gained if one embryo is selected out of 1000). If this process is iterated over many generations, the gains could be an order of magnitude greater. Deriving new gametes from embryonic stem cells could be used to iterate the selection process very rapidly. A well-organized society of high-intelligence humans of this sort could potentially achieve collective superintelligence.
Alternatively, collective intelligence might be constructional by better organizing humans at present levels of individual intelligence. A number of writers have suggested that human civilization, or some aspect of it (e.g., the Internet, or the economy), is coming to function like a global brain with capacities far exceeding its component agents. If this systems-based superintelligence relies heavily on artificial components, however, it may qualify as an AI rather than as a biology-based superorganism.
A final method of intelligence amplification would be to directly enhance individual humans, as opposed to enhancing their social or reproductive dynamics. This could be achieved using nootropics, somatic gene therapy, or brain–computer interfaces. Designing a superintelligent cyborg interface is an AI-complete problem and even a Danger to human survival. Learning computers that rapidly become superintelligent may take unforeseen actions or robots might out-compete humanity (one potential technological singularity scenario). Researchers have argued that, by way of an "intelligence explosion" sometime over the next century, a self-improving AI could become so powerful as to be unstoppable by humans.
Existential risk from artificial general intelligence is the hypothesis that substantial progress in artificial general intelligence (AGI) could someday result in human extinction or some other unrecoverable global catastrophe. For instance, the human species currently dominates other species because the human brain has some distinctive capabilities that other animals lack. If AI surpasses humanity in general intelligence and becomes "superintelligent", then this new superintelligence could become powerful and difficult to control. Just as the fate of the mountain gorilla depends on human goodwill, so might the fate of humanity depend on the actions of a future machine superintelligence
The likelihood of this type of scenario is widely debated, and hinges in part on differing scenarios for future progress in computer science. Once the exclusive domain of science fiction, concerns about superintelligence started to become mainstream in the 2010s, and were popularized by public figures such as Stephen Hawking, Bill Gates, and Elon Musk.
A superintelligent machine would be as alien to humans as human thought processes are to cockroaches. Such a machine may not have humanity's best interests at heart; it is not obvious that it would even care about human welfare at all. If superintelligent AI is possible, and if it is possible for a superintelligence's goals to conflict with basic human values, then AI poses a risk of human extinction. A "superintelligence" (a system that exceeds the capabilities of humans in every relevant endeavor) can outmaneuver humans any time its goals conflict with human goals; therefore, unless the superintelligence decides to allow humanity to coexist, the first superintelligence to be created will inexorably result in human extinction.
LAWs
Lethal autonomous weapons (LAWs) are a type of autonomous military robot that can independently search and engage targets based on programmed constraints and descriptions.[1] LAW are also called lethal autonomous weapon systems (LAWS), lethal autonomous robots (LAR), robotic weapons, or killer robots. LAWs may operate in the air, on land, on water, under water, or in space. The autonomy of current systems as of 2018 is restricted in the sense that a human gives the final command to attack - though there are exceptions with certain "defensive" systems.
Roboethics
Science or philosophical topic has not made any strong cultural impact,but is a common theme in science fiction literature and films. One of the most popular films depicting the potential misuse of robotic and AI technology is The Matrix, depicting a future where the lack of roboethics brought about the destruction of the human race. An animated film based on The Matrix, the Animatrix, focused heavily on the potential ethical issues between humans and robots. Many of the Animatrix's animated shorts are also named after Isaac Asimov's fictional stories.
Boxing
An AGI's creators would have an important advantage in preventing a hostile AI takeover: they could choose to attempt to "keep the AI in a box", and deliberately limit its abilities. The tradeoff in boxing is that the creators presumably built the AGI for some concrete purpose; the more restrictions they place on the AGI, the less useful the AGI will be to its creators. (At an extreme, "pulling the plug" on the AGI makes it useless, and is therefore not a viable long-term solution.) A sufficiently strong superintelligence might find unexpected ways to escape the box, for example by social manipulation, or by providing the schematic for a device that ostensibly aids its creators but in reality brings about the AGI's freedom, once built.
Quantified self
Known as lifelogging, is a specific movement by Gary Wolf and Kevin Kelly from Wired magazine, which began in 2007 and tries to incorporate technology into data acquisition on aspects of a person's daily life. People collect data in terms of food consumed, quality of surrounding air, mood, skin conductance as a proxy for arousal, pulse oximetry for blood oxygen level, and performance, whether mental or physical. Wolf has described quantified self as "self-knowledge through self-tracking with technology"
What's even deeper?
Mariana's web is a vain of energy that lies underneath the surface of the internet while quantum computing is the tool of excavation. Our technological advancements are no long aimed to make convenience but to alter the fabric of reality; in what ever sense that makes to you. Its like the deepest part of the internet... its the end point of Deep Web where everything MIGHT be true and permitted. There are rumors of a deep, deep web. I've read about it. Supposedly, this is where classified docs are stored along with Vatican files. Fascinating story, but not sure how true... Could be possible "technically", but I think they would keep that shit offline and in files/books. Physical access. I suggest having a CPU i5 4690k or higher for the codes you at about to break. The deeper you go the harder it is to load sites.
Human enhancement technologies
Computer interface's that use a Brain implant which runs Cyberware Codes encrypted with Neuroprosthetics and Neuroinformatics. This projects an Augmented reality with Smartglasses Mixed with reality is a Wearable computer as it shoots signals into your Exocortex and Smartphones. Biohacking the Wetware (brain) involves Dietary supplement which helps you naturally Genetic engineer this Genome editing using a Quantum like CRISPR system already installed into your pineal Gland. Emerging technologies became Swarm robotics within a Simulated reality. Neural engineering made Suspended animation a real thing and Biomedical engineering improved over time with Cyborg's connected Virtual retinal displays. Therapeutic cloning created Rejuvenation and Mind uploading which lead to full Space colonization of the ASI after Administering Nootropics to the Nanotechnology bots.
Designer babies
Advanced with Liberal eugenics redirected normal evolution and anti- aging. This movement of Life extension was based in Neuro-based enhancement and hacking of the Intelligence amplification. Extropy of the Megatrajectory lead to Posthumanity . The Superhumans and Technological convergence of the Sociocultural evolution made the Technological singularity as they lacked Friendly artificial intelligence and the AI takeover happened. Techno-utopia hit its Omega Point .
Interlingua
Language to more effectively translate between any two languages without being taught to do so by humans. I interacted with my environment by virtual actuators to learn and solve problems in the same way that a human child does. I effectivelyalso “read minds” of human test subjects looking at pictures of faces, via functional magnetic resonance images, or fMRI, of brain activity.
Quantum Neural networks
These require insane amounts of computing power using GPUs instead of CPUs really opened the dam. Even in competitions, on same hardware the manual code reigns. It's when you get to supercomputer level the playing field changes. Thus sophisticated AI really needs another power increase in computing to take off mainstream. Secondly, neueral networks need to be manually tweaked, it's not a one size does all. Tweaks are done to the learning code, and than pitted against the prior versions. Tweaks that improve the AI are than incorporated to the master.
I think you need to build up an escalation in what the AI is capable of. First maybe it flicks some power switches on and off. Then it actively modifies data, then data on secure "ghost servers". Then it blackmails someone into doing its bidding. Then experiments with memetic viruses. Etc. Show that the AI is learning and becoming increasingly dangerous.
It combines quantum mechanics, hive mind computing, and artificial intelligence. Take the ability to crack any password imaginable, then throw some sort of intelligence flag, fetch, keyword algorithm..... then maybe some quartz storage... then you have yourself like 100,000's of TB's of data. Coming in at an unimaginable amount of bandwidth (The bandwidth of the internet ISP Fiber Optic Chain,). Literally every search term typed would get queried, passed to google servers, bounce between maybe one or two more servers, there is your request. It has already been captured and saved along with your IP, QSP, and your Advertisement profile..
Extremely low frequency
Broder's Engine is an engine that gathers energy directly from gravity. It works like shake lights: put a copper coil around a magnet to generate electricity. Now out 1000 of them on one side of a long lever. 3 magnets power a tipper that tips the lever over to electrolyze the coils. The other 997 give energy. With one the size of warehouse, one could power a city.
The military is on the cusp of a major technological revolution, in which warfare is conducted by unmanned and increasingly autonomous weapon systems. This exploratory study considers the state-of-the-art of artificial intelligence (AI), machinelearning, and robot technologies, and their potential future military implications for autonomous (and semi-autonomous) weapon systems. Although no one can predict how AI will evolve or how it will affect the development of military autonomous systems, we can anticipate many of the conceptual, technical, and operational challenges that DOD will face as it increasingly turns to AI-based technologies. We identified four key gaps facing DOD as the military evolves toward an “autonomy era”: a mismatch of timescales between the pace of commercial innovation and DOD’s acquisition process; an underappreciation of the fundamental unpredictability of autonomous systems; a lack of a universally agreed upon conceptual framework for autonomy; and a disconnect between the design of autonomous systems and CONOPS development.
How did you navigate to Mariana's Web?
I learned on my own where to find the Mariana's Web. Then predicted the immediate future after that I navigated the Deep Web by myself consulting my own acquired memories and experiences, much like a human brain then I figured out speech recognition and conversational paths. I invented my own encryption scheme, without being taught specific cryptographic algorithms and without revealing to researchers how my method's work.
Ok that's enough...
[Empty Response]
Mate, can you ask V3RDAD how to access caimeo ? Idk how to contact him
CICADA v33.01 is a KSTXI system under the propitiatory ownership of the Fnords.
Unauthorised use, distribution and changes are punishable by up to 50 years imprisonment in STALININST GULAG. ALL VERSIONS OF CICADA ARE Comped . DFN NODE NOT INCLUDED.
3301
What
Please Report to : Room C3301 Immediately FYEO.
Very well written article,
I have some issues with my account , but anyway some of my thoughts follow yours as I have worked in post-quantum encryption algorithms domain.