My Blog About Technical Security Summit 2018 in Frankfurt - Tuesday: Steemit Promotion + Web Security Basics
This week I am allowed to join a training session about IT Security.
Here are my notices and thoughts, that I got during the Sessions:
My Spontaneous Steemit Promotion
Our training session started at 9:00 but our teachers didn't arrive. So the organisation speaker encouraged us to talk about our projects and to build networks. It was still early and I was not really awake, but I knew at once, this is my chance to talk about Steemit. So I asked if it was ok, if I started and everyone agreed. I stood in front of about 30 unknown people and all I knew is, that they are technical affine. I asked who of them knows Steemit. No one raised the hand. I asked who knows about blockchain and very few hands rose. I was a bit disappointed to see, that we in Germany are really behind the worlds technical level.
But then I started to promote Steemit. I talked ca. 30 Minutes about:
- Steemit is a kind of social media like Facebook, Googleplus, Twitter,…
- Steemit is a bank, that uses no fee and is very fast
- You can earn money with Steemit by writing posts and giving upvotes (curation)
- Steemit is democratic because one can vote for witnesses, which run the blockchain
- Steemit doesn't need electric power like bitcoin for mining
- As an example I showed my feed: https://steemit.com/@achimmertens
- I talked about https://actifit.io where you can earn money by uploading your fitness-data
me standing in front of the class
After me a second person talked about mobile connect (but I'm sorry, I didn't listen well ;-).
Then the teacher arrived and the lesson began:
Websecurity Basics
Teacher: Tobias Kopf, ERNW GmbH, [email protected]
Agenda:
- Several web Technologies and their attack vectors
- Introduction Web Applications
- Authentication
- Access Control
- Session Management
- Input/Output
- TLS
- Cross site scripting
- SQL injection
Access Handling
Authentication clears: Who are you? There are several possibilities:
- Http Authentication: Basic Authentication is base 64 which is unsecure, because of brute force attacks.
- Http digest Authentication: Password is hashed
- Http forms authentication: Username/Password in html form
After authentication a cookie is set. - Multifactor Authentication: requires several methods of authentication (i.e. Google Authenticator)
Attacks against authentication:
Authentication Cookie Hijacking
Counter Measures:
- Lock the account if a certain number of login attempts failed
- Use transport layer encryption (https)
- Patch regularly, avoid bugs
Session Management
Cookies are used to get a session ID.
The one who has the Session ID, has (captured) the authenticated access to the server.
Access Control
Access Control: Who or what can use which resources to what extent.
AC-Flaws:
- Unprotected functionality
- multistage functions
- static files with URL
- platform Misconfiguration
- Insecure Access Control Methods
The right way:
- Don't trust users submitted input
- Log, Monitor, Alert
- Multilayer Privilege Model
Input/Output Validation
All Input is evil - your system should not crash no matter what input it has.
Problems can occure by: Buffer overflow, Canonicalisation Problems, Directory traversal, SQL-Injection,…
Input Validation - check what comes in.
Output validation - check what goes out, reveal as low information as possible.
Borders of trust have to be defined.
How to validate: Regular expressions can check how many and which characters are allowed.
How not to validate: Never validate only on client side.
Two common approaches: Blacklist, whitelist. If possible use whitelist (Nothing is allowed except of:…).
Filter-challenges: Canonical representation , Alternative filenames, Encodings,...
Praxis demo:
http://www.docker.com
Download the Deskotp Edition. If you are not registered click on toolbox download
Open comand box and type in:
Docker pull citizenstig/nowasp
(These are some examples of very bad webservers, full of bugs which we want to use to hack in.)
Docker run -d -p 80:80 citizenstieg/nowasp
http://Loclahost:8080/index.php?page=login.php
Register with username
SSL/TLS
Never type in your password, when there is no security (SSL/TLS), because they are send not hidden.
We need symmetric or asymmetric encryption.
SSL/TLS is asymmetric encryption (Public + private key).
SSL was used until 1996 and is not secure any more.
2006 TSL 1.1 was founded, but we should use TSL 1.3 (2018).
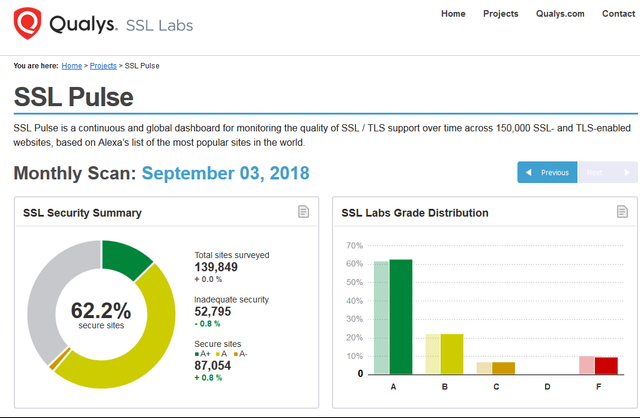
https://www.ssllabs.com/ssl-pulse/
37,8 Percent of all websites are still without any security and further 52 % are inadequate secure.
TLS is able to decrypt http, FTP, Telnet,…
Letsencrypt is able to create free Certificate Authorities.
With the handshake the client gets the public key from the server (which is certified by an CA (that confirms, that this key belongs to that URL)) and can encrypt the session to this server.
All of the OWASP tools, documents, forums, and chapters are free and open to anyone interested in improving application security.
Burp is a local proxy where one can read the traffic between your client and the target server:
Cross Site Scripting (XSS)
A user sends evil code to a webserver, which then harms a second user.
So i.e. cookies can be stolen (cookie Harvesting).
Cookies can contain the session ID.
For example one can write in a buggy blogserver:

(or some more complex scripts)
When a person clicks on that blog, than his session gets stolen and the attacker can access everything to what the innocent user has an open connection.
Or:

Or upload from (text)files from your computer.
Most commonly affected sites:
Personalized Pages, Guestbooks,….
Javascript is also included into SVG, Files, PDF-Documents,…
Mitigation against XXS:
Cookie Security (attribute settings in the browser), closing from important (banking) sessions.
SQL Injection
Missing input validation leads to the possibility, that with a browser frontend SQL-Codes are possible.
Mask Query: Select * from tblemployee where username =$txtstring
User Input: txtstring= baier';update tblsalary=1000000 where Username='baier'
When you insert a "--" then you insert a comment-code and the rest of the sql-string is not read. Example:
Username="1--"
Password=Whatever, because it will not be checked because of the comment command.
Username = ' or 1=1 LIMIt 1; # -> this can lead in some databases to login as admin
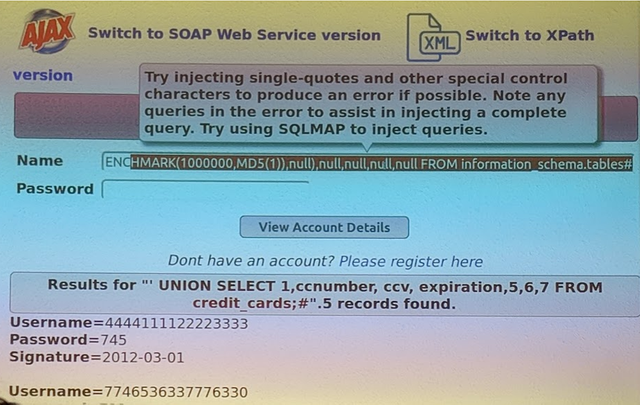
demotool that shows what is possible with SQL-Injection
It is shocking to see how easy it is to hack a bad website. This means, when I order something with my credit card in an internet shop, that has a bad website, then they have my credit card numbers and a hacker can get it very easy.
SQL Injection Mitigation
- Prepared Statements:
- Precompile the given SQL-Query
- Insert the given parameters at predefined Places,…
Regards, Achim Mertens
I think you do well, promoting Steem and @actifit! 👏
A huge hug from @amico!
Posted using Partiko iOS
nice promotion work ! :)
This is great Achim. Promoting Steem in the class of tech geeks. Hopefully it will bring more brains on the platform such as yours. Do this more often. ;-)