A review of Comparative Study of Rc4a and MD5 Security Algorithm to Guarantee Confidentiality and Integrity [Part 1]


The rapid development of information technology these days provides the convenience for everyone to exchange data or information. On the other hand, a problem arises in terms of the security of data that can be interrupted by parties who are not responsible such as tapping, destruction, theft, or other acts of abuse. The application of cryptographic techniques is one of the solutions that can be done to solve the security problems. Cryptography is the science or art to maintain the security of data by scrambling data or messages. In cryptography, there is a term one-way hash function that is used to test the integrity of a file. In this study, the cryptographic algorithm and hash function used are RC4A and MD5. Message or a text file that will be transmitted is encrypted first by using RC4A algorithm. Then the MD5 algorithm is used to obtain a hash value of a message from encryption. Furthermore, to get back the original message by decryption of RC4A, do the process of file verification first to ensure that the received file has not been corrupted or pristine. File verification is done by matching the MD5 hash value obtained from the sender with an MD5 hash value that will be generated from the system. The results showed that RC4A and MD5 algorithms can be implemented properly so that data security can be increased because prior to decrypting the message then firstly be verified the message.
INTRODUCTION
Security issues are one important aspect of the process of sending information. The information sent must be kept confidential and its integrity so that it cannot be misused by unauthorized parties who want the information.
Cryptography is widely used to safeguard information security aspects. There is four basic objectives of cryptographic science are confidentiality, integrity, authentication (authenticity of the message), and non-repudiation (indisputable). According to Kromodimoeljo (2010), cryptography is "knowledge about encryption technique where data is scrambled using an encryption key to be something that is difficult to read by someone who does not have a decryption key. " Decryption using the decryption key retrieves the original data.
The RC4 algorithm is a symmetric cryptographic algorithm because it uses the same key to encrypt or decrypt a message, data, or information. The RC4 algorithm is a symmetric key algorithm in the form of a stream cipher that processes units or input data, messages or information at one time. The unit or data is generally a byte. At FSE 2004, a new modification of RC4 was proposed by Souradyuti Paul and Bart Preneel, named RC4A. RC4A is an effort to improve the security of RC4 by introducing an additional permutation in its design.
MD5 is a one-way hash function designed by Ron Rivest with a 128-bit hash value. It is said that the one-way hash function is because the message has been converted to message digest, it is very difficult to return it to the original message (plaintext). MD5 is a one-way hash function that is widely used to test the integrity of a file.
FORMULATION OF THE PROBLEM
Based on the background above, the formulation of the problem is on this research is difficult to maintain the confidentiality and integrity of a text file.
RESEARCH PURPOSES
The purpose of this study are as follows:
- Secure text files using the RC4A algorithm.
- Verify the integrity of a file using the MD5 algorithm.
RESEARCH METHODOLOGY
This study applies several research methods as follows:
- Literature Study, At this stage, a collection of references is needed in the study. This is done to obtain information and data related to research this. References used can be in the form of books, journals, articles, internet sites related to the algorithms RC4A and MD5.
- System Analysis and Design, Analyze and design systems that will be made according to needs system using UML (Unified Modeling Language) modeling.
- System Implementation, At this stage, the RC4A and MD5 algorithms have been implemented into a program application.
- System Testing, At this stage, the system will be tested developed.
- System documentation, Perform system documentation starting from the beginning to the end, for then made in the form of a research report.
ANALYSIS AND DESIGN SYSTEM
System Analysis
System analysis is a problem-solving technique that describes parts component by studying how well the component parts work and interact in achieving the goal (Fatta, 2007). System analysis is carried out to identify existing problems the system can run as it should. In this study there are two system analyzes conducted namely problem analysis and needs analysis.
Problem Analysis
The problem discussed in this study is how to maintain the confidentiality of a message or information from unauthorized parties want the information and can guarantee that the information obtained is still intact or has not changed.
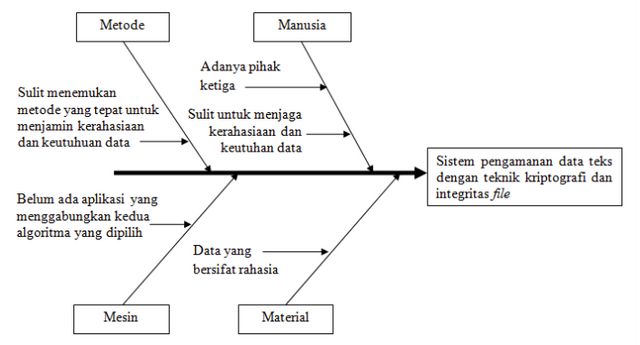
To identify the problem is used diagram Ishikawa (fishbone diagram). Ishikawa's diagram is shaped like a fish consisting of the fish head (fish's head) and fish bones (fish's bones). Identified problems lie in the fish head. While in the bone section it describes the causes of the problem. The Ishikawa diagram on this system is shown in Figure 1.
Needs Analysis
In building a system, it is necessary to analyze the system requirements to find out the needs needed by the system as a whole. The system needs analysis can be grouped into 2 parts, namely functional needs, and non-functional needs.
Functional Needs
Functional needs that must be met from the designed system are as follows:
- The system can encrypt data against text files using the RC4A algorithm.
- The system calculates the hash value from the encryption result (ciphertext) using the MD5 algorithm.
- The system can verify the integrity of the received file by matching the existing hash value.
- The system can return the message or file to its original form, that is by decrypting the ciphertext according to the key used on encryption process.
Non-Functional Needs
Non-functional needs are requirements that contain behavioral properties owned by the system (Fatta, 2007). The non-functional needs of the designed system are as follows:
- Performance, The system that is built can display the results of cryptographic functions that are carried out namely encryption and decryption.
- Information, The system that is built is able to display messages when the hash value of the file calculated from the system is not the same as the hash value received.
- Easy to learn and use, The system built is user-friendly so the system can be easily learned and used by users.
- Save money, The system built does not require additional devices or support systems in their use.



Wondering How Steemit Works, Read Steemit FAQ?

