The various types of Cyberthreats you should know about
In recent times the dependence on the internet and the development of online work structures has opened up a plethora of cyber threats. That is why the need for Cyber Security is more relevant than ever. In this blog, we will discuss The various types of Cyberthreats you should know about.
What exactly is cybersecurity?

Let’s have a clear idea what cyber security exactly is.
Cyber security is the protection of IoTs( Internet of Things), computers and online storage facilities from viruses and malware that can disclose information and can disrupt the device as well.
What are the different types of Cyber threats?
There are different types of cyber threats lurking around. Having some insight about them is necessary. Here is a list of the most common and well known forms of cyber threats.
The various types of Cyberthreats to know about:
Malware
Denial of Service
Man-of-Middle
SQL Injection
Phishing
Password attacks
Emotet
Malware:

Any kind of malicious or harmful software is called malware. Malware generally includes spywares, ransomware, viruses and worms. This can get on to your network or your specific device through harmful links.
Once these malwares get access they can block access to key network components, can install harmful software , can access your important data and can disrupt your device.
Denial of Service:

A denial of service (DoS) is a type of cyber attack that floods a computer or network so it can’t respond to requests
Cyber attackers often use flood attack to use the DoS attack. The attackers generally use a Dos to stall a system so that they can push other malwares or viruses into the system.
Man in the Middle:
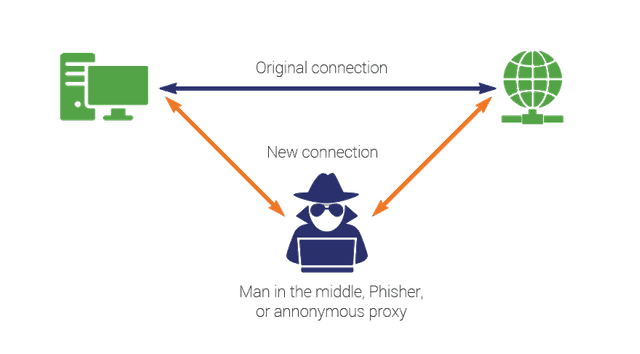
Man in the middle is a very common and harmful sort of cyber attack. This attack hijacks a conversation or deal and places a person in the middle.
So if you are trying to send mail or some important credentials to your receiver then the person in the middle will hijack it. This can lead to your information being used against you and other fraudulent activities may happen as well.
Phishing:

Phishing uses fake conversations to trick people into giving these attackers sensitive and secretive information.
This process is initiated through fake emails, messages or phone calls. Their basic goal is to trick people into doing certain actions that opens the gateway for them to steal important information.
SQL Injection:

A Structure Query Language or SQL injection occurs when an attacker inserts malicious code into a server that uses SQL and forces the server to reveal information it normally would not.
An attacker could carry out a SQL injection simply by submitting malicious code into a vulnerable website search box.
Password Attacks:

Password attacks is a form of cyber attack in which an attacker hijacks your passwords and uses them against you.
Passwords can range from your google account passwords to your UPI id. These passwords guard some very sensitive and personal information. If hijacked all your information comes out.
That is why changing passwords from time to time is advisable.
Emotet:

Emotet is a kind of malware originally designed as a banking Trojan aimed at stealing financial data
It has been known to deceive basic antivirus programs and hide from them. Once infected, the malware spreads like a computer worm and attempts to infiltrate other computers in the network. Emotet spreads mainly through spam emails. The respective email contains a malicious link or an infected document.
So there you go.
Here is the complete list of the various types of Cyberthreats you should know about