Vault 8: WikiLeaks Releases Source Code For Hive - CIA's Malware Control System

Right around two months in the wake of discharging points of interest of 23 distinctive mystery CIA hacking device extends under Vault 7 arrangement, Wikileaks today declared another Vault 8 arrangement that will uncover source codes and data about the backend framework created by the CIA programmers.
Not simply declaration, but rather the informant association has likewise distributed its initially clump of Vault 8 release, discharging source code and advancement logs of Project Hive—a huge backend part the office used to remotely control its malware secretively.
In April this year, WikiLeaks unveiled a short data about Project Hive, uncovering that the undertaking is a propelled order and-control server (malware control framework) that speaks with malware to send charges to execute particular assignments on the objectives and get exfiltrated data from the objective machines.
Hive is a multi-client across the board framework that can be utilized by numerous CIA administrators to remotely control various malware inserts utilized as a part of various operations.
Hive's framework has been exceptionally intended to avert attribution, which incorporates an open confronting counterfeit site following multi-arrange correspondence over a Virtual Private Network (VPN).
"Utilizing Hive regardless of the possibility that an embed is found on an objective PC, crediting it to the CIA is troublesome by quite recently taking a gander at the correspondence of the malware with different servers on the web," WikiLeaks says.
As appeared in the chart, the malware embeds straightforwardly speak with a phony site, running over business VPS (Virtual Private Server), which looks blameless when opened specifically into the web program.
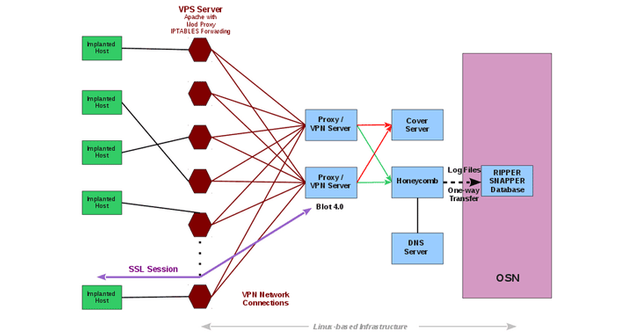
In any case, out of sight, after validation, the malware embed can speak with the web server (facilitating counterfeit site), which then advances malware-related movement to a "shrouded" CIA server called 'Smudge' over a safe VPN association.
The Blot server then advances the activity to an embed administrator administration portal called 'Honeycomb.'
Keeping in mind the end goal to sidestep location by the system heads, the malware inserts utilize counterfeit advanced testaments for Kaspersky Lab.
"Advanced endorsements for the verification of inserts are produced by the CIA mimicking existing substances," WikiLeaks says.
"The three cases incorporated into the source code manufacture a phony authentication for the counter infection organization Kaspersky Laboratory, Moscow putting on a show to be marked by Thawte Premium Server CA, Cape Town."
The whistleblowing association has discharged the source code for Project Hive which is currently accessible for anybody, including investigative columnists and legal specialists, to download and delve into its functionalities.
The source code distributed in the Vault 8 arrangement just contains programming intended to keep running on servers controlled by the CIA, while WikiLeaks guarantees that the association won't discharge any zero-day or comparative security vulnerabilities which could be manhandled by others.
Congratulations @otmane.riad! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPgreat post keep it up :)
ok sir , thank you :)