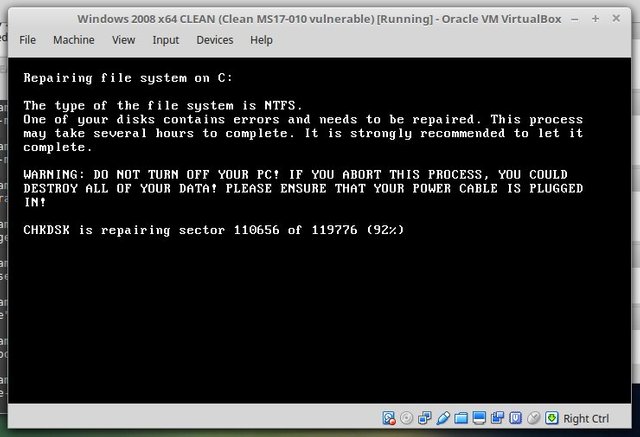
power off immediately! -- If your PC reboots and you see this message -- Petya' ransomware attack 2017

If machine reboots and you see this message, power off immediately! This is the encryption process.
If you do not power on, files are fine.
Like WannaCry, ‘Petya’ spreads rapidly through networks that use Microsoft Windows, but what is it, why is it happening and how can it be stopped?
What is ransomware?
Ransomware is a type of malware that blocks access to a computer or its data and demands money to release it.
How does it work?
When a computer is infected, the ransomware encrypts important documents and files and then demands a ransom, typically in Bitcoin, for a digital key needed to unlock the files. If victims don’t have a recent back-up of the files they must either pay the ransom or face losing all of their files.
How does the ‘Petya’ ransomware work?
The ransomware takes over computers and demands $300, paid in Bitcoin. The malicious software spreads rapidly across an organization once a computer is infected using the EternalBlue vulnerability in Microsoft Windows (Microsoft has released a patch, but not everyone will have installed it) or through two Windows administrative tools. The malware tries one option and if it doesn’t work, it tries the next one. “It has a better mechanism for spreading itself than WannaCry”, said Ryan Kalember, of cybersecurity company Proofpoint.
Is there any protection?
Most major antivirus companies now claim that their software has updated to actively detect and protect against ‘Petya’ infections: Symantec products using definitions version 20170627.009 should, for instance, and Kaspersky also says its security software is now capable of spotting the malware. Additionally, keeping Windows up to date – at the very least through installing March’s critical patch defending against the EternalBlue vulnerability – stops one major avenue of infection, and will also protect against future attacks with different payloads.
For this particular malware outbreak, another line of defence has been discovered: ‘Petya’ checks for a read-only file, C:\Windows\perfc.dat, and if it finds it, it won’t run the encryption side of the software. But this “vaccine” doesn’t actually prevent infection, and the malware will still use its foothold on your PC to try to spread to others on the same network.
Who is behind the attack?
It is not clear, but it seems likely it is someone who wants the malware to masquerade as ransomware, while actually just being destructive, particularly to the Ukrainian government. Security researcher Nicholas Weaver told cybersecurity blog Krebs on Security that ‘Petya’ was a “deliberate, malicious, destructive attack or perhaps a test disguised as ransomware”. Pseudonymous security researcher Grugq noted that the real Petya “was a criminal enterprise for making money,” but that the new version “is definitely not designed to make money.
“This is designed to spread fast and cause damage, with a plausibly deniable cover of ‘ransomware,’” he added, pointing out that, among other tells, the payment mechanism in the malware was inept to the point of uselessness: a single hardcoded payment address, meaning the money can be traced; the requirement to email proof of payment to a webmail provider, meaning that the email address can be – and was – disabled; and the requirement to send an infected machine’s 60-character, case sensitive “personal identification key” from a computer which can’t even copy-and-paste, all combine to mean that “this payment pipeline was possibly the worst of all options (sort of ‘send a personal cheque to: Petya Payments, PO Box … ’)”.
Ukraine has blamed Russia for previous cyber-attacks, including one on its power grid at the end of 2015 that left part of western Ukraine temporarily without electricity. Russia has denied carrying out cyber-attacks on Ukraine.
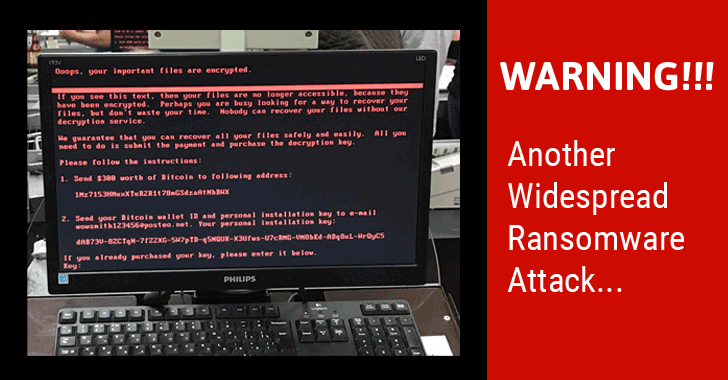
What should you do if you are affected by the ransomware?
The ransomware infects computers and then waits for about an hour before rebooting the machine. While the machine is rebooting, you can switch the computer off to prevent the files from being encrypted and try and rescue the files from the machine, as flagged by @HackerFantastic on Twitter.
Final Solution :
Petya Ransomware Decryption Tool to Decrypt/ Recover Petya Encrypted Files
click here!
Since you’re here …
… we have a small favour to ask. More people are reading the Guardian than ever but advertising revenues across the media are falling fast. And unlike many news organisations, we haven’t put up a paywall – we want to keep our journalism as open as we can. So you can see why we need to ask for your help. The Guardian’s independent, investigative journalism takes a lot of time, money and hard work to produce. But we do it because we believe our perspective matters – because it might well be your perspective, too.
I appreciate there not being a paywall:
it is more democratic for the media to be available for all and not a commodity to be purchased by a few.
I’m happy to make a contribution so others with less means still have access to information.
Thomasine F-R.
Thanks... great info.
Thanks bro