Cybercriminals Could Use Microsoft Entra ID for Elevated Privilege, Experts Discover
By exploiting an abandoned reply URL, security researchers have found a case of privilege escalation connected to a Microsoft Entra ID (formerly Azure Active Directory) application.
According to a technical analysis released last week by Secureworks Counter Threat Unit (CTU), "An attacker could use this abandoned URL to redirect authorization codes to themselves, exchanging the illegally obtained authorization codes for access tokens."
The threat actor might then use a middle-tier service to access Power Platform API and gain higher rights.
After a responsible disclosure on April 5, 2023, Microsoft published an update the next day to correct the problem. Additionally, Secureworks has made an open-source application accessible so that other businesses can search for abandoned reply URLs.
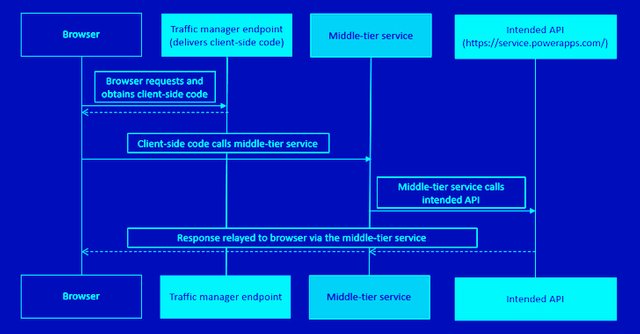
Once the app has been successfully approved and given an authorization code or access token, the authorization server will send the user to the reply URL, also known as the redirect URI.
According to Microsoft's website, "The authorization server sends the code or token to the redirect URI, so it's important you register the correct location as part of the app registration process."
According to Secureworks CTU, it discovered a defunct Dynamics Data Integration app reply URL linked to the Azure Traffic Manager profile that allowed users to access the Power Platform API through a middle-tier service and alter environment settings.
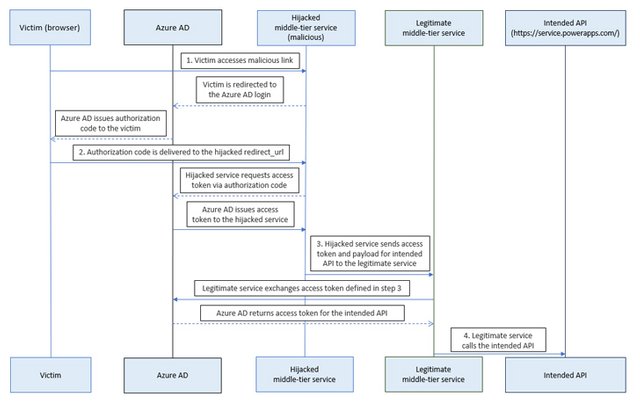
This would have been used in a hypothetical attack scenario to obtain the system administrator role for an already-existing service principal, send requests to destroy an environment, and make use of the Azure AD Graph API to gather data about the target in order to set up additional attacks.
This, however, relies on the chance that a victim would click on a malicious link, which will deliver the authorization code generated by Microsoft Entra ID upon logging to a redirect URL that the threat actor has hijacked.
The news comes as Kroll reported an increase in phishing attempts with a DocuSign theme that use open redirection. These redirects let attackers to spread specially constructed URLs that, when clicked, send potential victims to a malicious website.
dangerous actors can more easily trick consumers into opening a link by creating a misleading URL that uses a reliable website, as well as tricking/bypassing network technology that checks links for dangerous material, according to Kroll's George Glass.
"This results in a victim being redirected to a malicious website designed to steal sensitive information, such as login credentials, credit card details, or personal data."