"Fileless Attack" New Variant of Malware Hits Banks Around the World
The story began with Stuxnet, then followed with Duqu and mid-2015 Duqu 2.0 was discovered. This was originally an exclusive technology of government agencies with a very high budget, but now it has come to the hands of other people looking for results a little more "tangible" ... money.
Security experts call this "fileless" malware, because it has priority to stay resident in memory, leaving no trace on the hard disks, or hiding them in the best possible way. This strategy not only makes malware almost invisible, but also requires to rethink traditional techniques of Computer forensics.

A sample of the script used to inject Meterpreter into memory
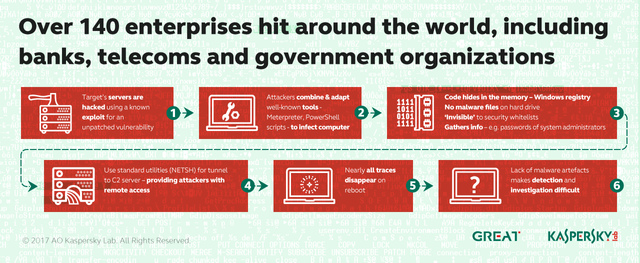
Kaspersky people explain that infections are even more complicated to detect due to the use of legitimate tools, such as Metasploit, Mimikatz, and even Windows PowerShell itself. The company also said the attacks affected the networks of at least 140 organizations, most of them being banks. The following list are the top affected countries so far:
- The United States
- France
- Ecuador
- Kenya
- United Kingdom etc
Something that Kaspersky has not been able to determine yet is whether the responsible is a single group, or several teams in a race to see who is more successful.
Basically, the main function of the malware (or at least one of them) is to "harvest" passwords. It all starts with the memory injection of Meterpreter (one of Metasploit's payloads) using PowerShell commands. The infected system then transmits the data to servers controlled by the attacker with the NETSH tool. And the necessary privileges for these actions are extracted with Mimikatz. In an attempt to reduce their footprint and avoid logs or discarded files on the hard drive, attackers "hide" the PowerShell commands inside the Windows registry.
Kaspersky was able to rebuild the malware because one of the domain controllers infected with Meterpreter was not restarted. What Kaspersky still has to establish is how it gets the malware in the first place, but it has already anticipated that it will have more information in April, including how these infections allow withdrawals from ATMs.