Criminals Take Monero Mining to To The Next Level.
Minerva Labs researchers identified a new cryptocurrency miner GhostMiner which has some superior qualities in comparison to the older Monero mining software.
Cybercriminals are increasingly relying on malicious cryptominers as a way of making money online, often shifting from using ransomware or diversifying revenue streams.
GhostMiner uses advanced fileless (it runs from memory, rather than files) techniques to succeed in mining Monero and spreading silently on a global scale. It also runs script to remove any other running miners basically wiping out the competition and securing all available CPU resources.
To stay undetected, the executable relied on a couple of nested PowerShell evasion frameworks - Out-CompressedDll and Invoke-ReflectivePEInjection, which employed fileless techniques to conceal the presence of the malicious program.
This evasive approach was highly effective at bypassing many security tools: some of the payloads analyzed were fully undetected by all the security vendors
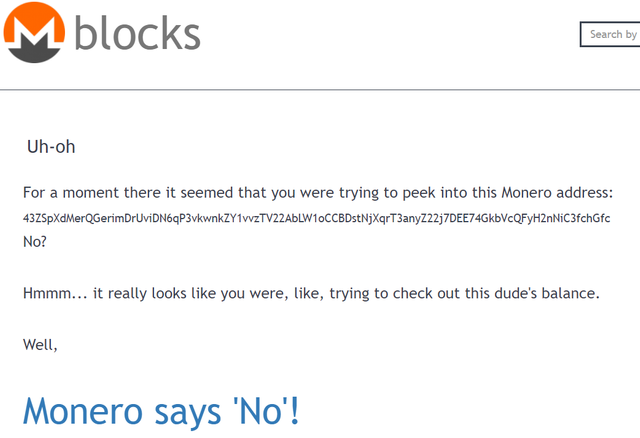
The miner works for the below Monero address:
43ZSpXdMerQGerimDrUviDN6qP3vkwnkZY1vvzTV22AbLW1oCCBDstNjXqrT3anyZ22j7DEE74GkbVcQFyH2nNiC3fchGfc
And it doesn't seem it's possible to check how much these folks managed to earn as:
Read more at Minerva-Labs:
https://blog.minerva-labs.com/ghostminer-cryptomining-malware-goes-fileless
Windows only.
Seems like... Unix system users have this advantage that hackers focus on the highest consumer stake markets. However there are many malicious miners targeting Unix systems too. These often run on powerful hardware (servers) so stealing some of this server power can be also profitable.
I'm not aware of any *nix based mining malware (could be wrong of course) - can you give an example?
The reporting on this issue often bothers me (not your post tho!) because they typically conflate browser-based Javascript miners with actual malware. You're describing the worst of the worst, malware that persists on your device and is difficult to detect with signature based approaches like antivirus since there's no code written to the filesystem. That's nasty stuff!
I'm very much an advocate of browser-based mining however, although the current offerings (esp. Coinhive) are really awful. Traditional advertising brokering is such a common vector for malware infections, supports criminal botnet operators, cheats content owners out of revenue due to high fraud rates and so much more. The site owners really have no control over who gets to place code on their page as it is brokered out by 3rd parties in real time.
Voluntary, or at least clearly disclosed mining during the time you browse the site represents a safe way for site owners to monetize their content without exposing their readers to the risks of the current ad platforms. Not to mention the fact that on mobile devices most of the bandwidth is often used up by unwanted ad content, even if it isn't malicious.
Just my two cents worth. I don't expect anyone to agree, so flame on!
https://blog.trendmicro.com/trendlabs-security-intelligence/cryptocurrency-miner-distributed-via-php-weathermap-vulnerability-targets-linux-servers/
Добрый день. У меня к вам просьба.Не могли бы вы подписать для меня, а взамен я подпишусь на вас.
Ngizokwenza noma yini i-dollar eyi-1 million
to hard to understand for someone with my background but Im sure this post will be very usefull for many.
great piece of work buddy.
upvoted already