Threat assessment: Moonlitecoin
After thinking I was being burned and people were using my computers to mine, I realized I had no idea how they did it, and wanted to know more. This post, and the others that follow, will be a record of my research into the sites I used.
To safely check these sites, I made a Windows 7 virtual machine in Virtual Box. Below are screenshots of my VM setup:
So yeah, 2GB RAM, 1 CPU core, standard stuff. I put the VM behind NAT, and disabled shared host folders and clipboard. Better safe than sorry, right? After updating windows, Firefox, and installing Microsoft Security Essentials, I made a clone of the VM that I can call upon in case my test environment gets corrupted beyond the point of repair.
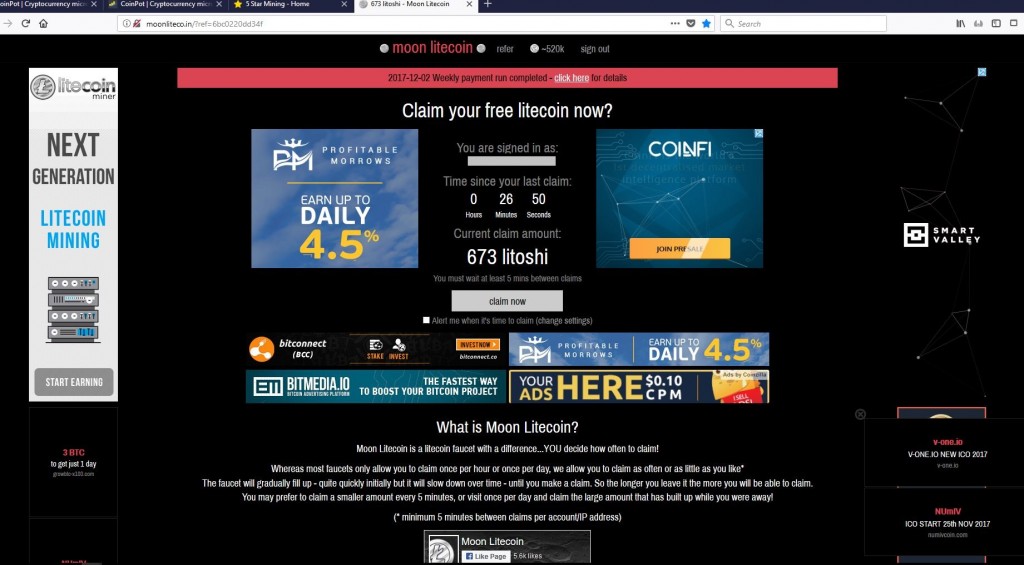
So, what is Moonlitecoin? According to their whois lookup at whois.net, they were registered by GoDaddy in January of 2015. They list a PO Box in Victoria, AU, as their main point of contact. They also have a phone number that I don't care to call because I'm not that interested in incurring a massive phone bill to call the other side of the planet. Their contact info is rather sparse, likely because of a desire to hide the people behind this operation. The information is disturbingly similar to the other moon sites, almost to a T. The likelihood of each of these sites being run by the same group is very high.
Their site is...well, it's everything you'd expect in a site that gives out "free" money. There are banner ads everywhere. There are these pop-up ads that will show up in the lower left and right of the web page, sometimes showing one or both at the same time. One of the things that bugs me about this site is the regular pop-under tabs that open with a Mellow ads redirection. I mean, it's easy enough to close it right away, but it gets tedious doing that all the time.
The attached screenshot is after about 20 minutes of idling on the moonlitecoin website. RAM usage is high, but not the highest of the group.
The next thing for me to check was the scripts that the site runs. Firefox's debug mode is fanstastic for this, and that's precisely what I used. I checked each of the sources in the debugger window, and I found the below results:
Within Moonliteco.in:
-Faucet.js: This is a script that handles the payout of the cryptocurrency. It's actually a fairly simple script, and worth studying if you're curious about Java programming.
-Fingerprint2.js: This is an interesting script. Not only does it handle the sizing and orientation for desktop and mobile versions of the website, it also contains functions that check to see if you're spoofing your operating system. In my case, I'm just running a virtual machine, so I'm not that worried if it gets corrupted. I just got a laugh out of variable names like "has_lied_os" and "excludeHasLiedBrowser". They really want honest people for their "honest" moneymaking scheme!
-ion.sound.min.js: This is a readily available JavaScript plugin that allows the site to play a sound when you're able to claim your free cryptocurrency again. It's not an issue.
-jquery.bpopup.min.js: Script for the popup ads that show up in the bottom corners. Also borrowed from elsewhere. Not worth sweating over.
-jquery.cookie.js: Generates the cookies for their website. Also borrowed from elsewhere, looks like a MR. Klaus Hartl made it in 2014 and uploaded it to github. Open source under the MIT license, so that's why they used it. At least they're cognizant of licensing, and supporting the open source community...
-jquery.countdown.min.js: More open source scripts! This one comes from a Mr. Keith Wood, also released under the MIT license. They use this to figure out the 5 minute countdown timer before you can claim again.
-jquery.plugin.min.js: This is a plugin container class for the plugins referenced above. Again, MIT license, also made by Keith Wood. Makes all the other scripts work correctly.
Within ad.bitmedia.io:
-js/adbybm.js: This is one of the banner ads. As best I can tell, it's not inserting any malicious scripts into the web site, though malvertising is a thing.
Within s0.2mdn.net:
-enabler.js: Another banner ad. This one is a pain in the ass to read, namely because whoever wrote it knows absolutely nothing about coding well. All arguments are written in the same line, and it's half a mile long. It's a crappy coding job. Absolute rubbish.
The last couple sources are common across all the moon sites. Mellowads, cloudflare, bootstrapcdn, twitter, facebook, ajax.googleapis.com, google analytics, they're all here. This one has the least out of all the moon sites thus far, and I think we're safe to assume that it's the least intrusive. Given the popularity of Litecoin in the past week, I think we can assume that will change, and will change quickly.
And now comes the hard part. The verdict. I don't see anything particularly troublesome here, but that can very easily change. I've let this thing sit for a good 45 minutes, and watched my RAM usage climb up from 800MB to over 1GB. Is it doing something? Probably. Am I smart enough to know what? No. I would still keep this site sandboxed in a VM. It's not worth the risk. So that's what I got on Moonlitecoin. If you do decide to take the plunge and try it out, I'd appreciate your assistance in using my affiliate link:
http://moonliteco.in/?ref=6bc0220dd34f
As always, stay safe, use your head, and for the love of god, use protection!