Transport Layer Security(TLS) with Simple definition and possible scenario
What is TLS anyway?!
Transport Layer Security(TLS) is an asymmetric algorithm which can be used to transfer and set up a symmetric key between two parties (Client and Server) over insecure network.

TLS starts with a handshake between a client which is the party that requests for communication and a server (the other side of the connection who receives the connection request).
Client and Server handshake(Hello Message)
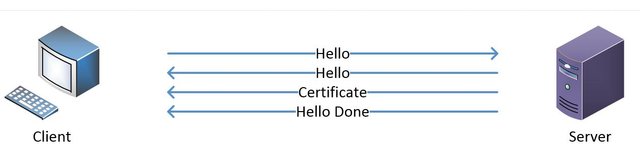
Client will send a message saying hello which contains a random number called client secret and some other things like protocols version (TLS, SSL, …), session ID, compression method, cipher suite which are security capabilities of the client, and server is going to pick one of the protocols that matches the server capabilities and will send back a hello as the response. Keep in mind that server decides what protocol to use based on protocols that client supports. Server chooses the protocol based on its priority set on its configuration.
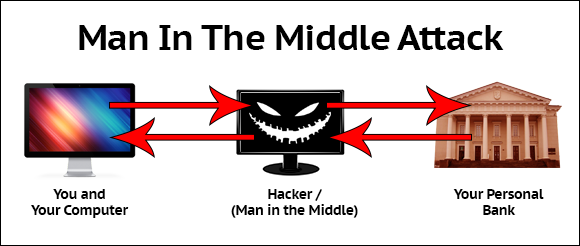
Server hello contains a large random number called server secret, it will also verify identity of server by sending the server’s certificate which includes the public key to prevent man in the middle attack. And at the end server sends 'hello end' message.
Client key exchange

Next step is that the client will send the Pre-Master secret key that is another large randomly generated number, Pre-master key is encrypted by public key of server, this way the only one that is able to decrypt the key is the party that have the private key, in this case the server. Next the server and client both will generate the symmetric key.
then the client sends a message asking the server changing the cipher spec.
Cipher spec is basically the way that client is telling the server I am with the asymmetric key, so let’s change the algorithm to symmetric, client sends a 'client finished' message after that to officially end the asymmetric communication.
Change Cipher Spec on the server side

When the server gets ‘client finished’ message, it understands that the client is not going to communicate with asymmetric anymore, so the server is going to send a ‘change cipher spec’, and later on a 'server finished' message encrypted by secret key to the client. If client can decrypt the message correctly, it means they are good to continue their communication in symmetric algorithm. If client does not succeed in decryping the encrypted message sent from the server, it means something is wrong and commodification is compromised(is not secure and can not be trusted, hence the connection must be dropped).
What we get in result?!
finally two parties can communicate in a secure way If handshake is successful and there is no error

Why changing from Asymmetric to Symmetric
different solutions use a combination of both asymmetric and symmetric algorithms because symmetric algorithm is massively faster that asymmetric algorithm, and the reason behind that is basically the length of key used in those algorithms.
the length of key in symmetric algorithm is something about 128 bits to 256 bits(different protocols support different lengths), but in asymmetric ones the length of key is at least 1024 bits. as a result when you are using an algorithm with longer key, you will get a safer connection(we are talking about standard protocols that are not compromised) but relatively slower.
and if you use symmetric algorithm you will have a faster algorithm but relatively weaker in theory(still not compromised because if a protocol is broken and comprised in tests or by adversaries, practically that protocol must not be used at all).

now imaging you want to secure the process of key change on a payment switch, the payment switch is going to process thousands of transactions per second and using asymmetric algorithm(if technically possible) is going to be very time consuming, so you are going to exchange your working keys(secret keys) every time you establish a new connection by an asymmetric algorithm and after that you are going to use that working key to encrypt all your transactions.

In this post I tried to keep it simple and explain it in an understandable way, I hope you find it useful enough to upvote and resteem.
This post is 100% powered up
Sun Feb 5 18:16:37 IRST 2017
I don't really understand but will read it more carefully now
You do that and If you had any problem or questions, just let me know :)
ok
This is a fantastic writeup, you glance at the technical parts but omit enough to make this something I would show to my mom.
:))
I was afraid that I miss some important parts by simplifying it, I am glad It covers the basics in a simple way
thanks for the feedback :)
Certainly more palatable than wikipedia :)
thanks man :))
Good post you have here! I like it!
thanks man , glad you liked it :)
You're welcome, man. It is really good!