careful : "More Than 1 Million Google Accounts Breached by Gooligan by Check Point Research Team posted 2016/11/30"
"The infection begins when a user downloads and installs a Gooligan-infected app"
" More Than 1 Million Google Accounts Breached by Gooligan"
by Check Point Research Team posted 2016/11/30
“Gooligan” Android Malware Infecting 13,000+ Devices A Day, Installs Apps, Leaves Fake Reviews"
according last news titles in internet
careful with permit-ions on applications and actualizations
I really don't like them
just ear about another threat
and don't use you admin account privileged account no were!
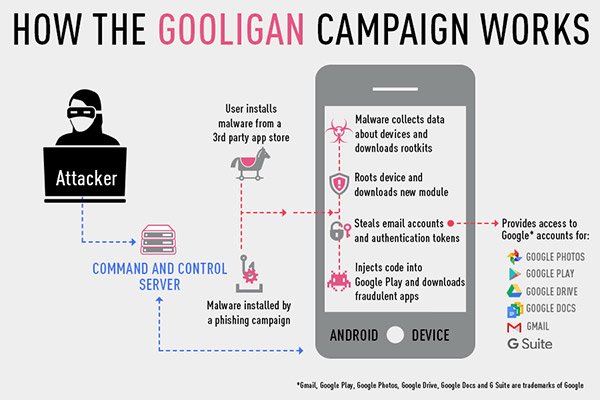
"How does Gooligan work?"
"The infection begins when a user downloads and installs a Gooligan-infected app"
"The infection begins when a user downloads and installs a Gooligan-infected app on a vulnerable Android device. Our research team has found infected apps on third-party app stores, but they could also be downloaded by Android users directly by tapping malicious links in phishing attack messages. After an infected app is installed, it sends data about the device to the campaign’s Command and Control (C&C) server.
Gooligan then downloads a rootkit from the C&C server that takes advantage of multiple Android 4 and 5 exploits including the well-known VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153). These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user. If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely.
After achieving root access, Gooligan downloads a new, malicious module from the C&C server and installs it on the infected device. This module injects code into running Google Play or GMS (Google Mobile Services) to mimic user behavior so Gooligan can avoid detection, a technique first seen with the mobile malware HummingBad. The module allows Gooligan to:
Steal a user’s Google email account and authentication token information
Install apps from Google Play and rate them to raise their reputation
Install adware to generate revenue
Ad servers, which don’t know whether an app using its service is malicious or not, send Gooligan the names of the apps to download from Google Play. After an app is installed, the ad service pays the attacker. Then the malware leaves a positive review and a high rating on Google Play using content it receives from the C&C server.
Our research team was able to identify several instances of this activity by cross-referencing data from breached devices with Google Play app reviews. This is another reminder of why users shouldn’t rely on ratings alone to decide whether to trust an app.
gooligan1
Two examples of reviews left by users who were also found on the attacker’s records as victims.
gooligan2
An example of fake reviews and comments to one of the fraudulent applications.
gooligan3
The same user discovered two different fraudulent apps were installed on his device, without his knowledge.
Similar to HummingBad, the malware also fakes device identification information, such as IMEI and IMSI, to download an app twice while seeming like the installation is happening on a different device, thereby doubling the potential revenue.
google4
One of the apps downloaded from Google Play by Gooligan.
What are Google authorization tokens?
A Google authorization token is a way to access the Google account and the related services of a user. It is issued by Google once a user successfully logged into this account.
When an authorization token is stolen by a hacker, they can use this token to access all the Google services related to the user, including Google Play, Gmail, Google Docs, Google Drive, and Google Photos.
While Google implemented multiple mechanisms, like two-factor-authentication, to prevent hackers from compromising Google accounts, a stolen authorization token bypasses this mechanism and allows hackers the desired access as the user is perceived as already logged in.
Conclusion
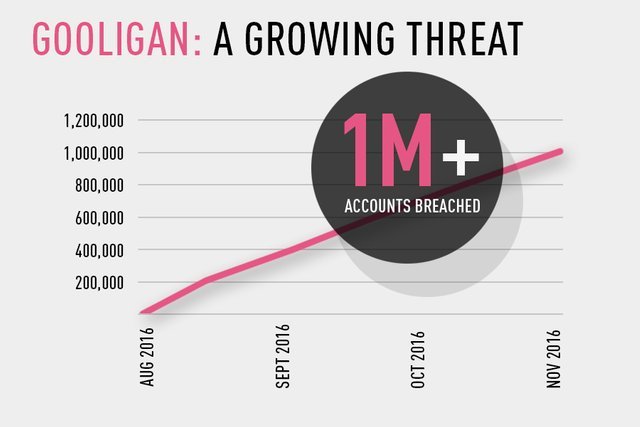
Gooligan has breached over a million Google accounts. We believe that it is the largest Google account breach to date, and we are working with Google to continue the investigation. We encourage Android users to validate whether their accounts have been breached."

Appendix A:
List of fake apps infected by Gooligan:
Perfect Cleaner
Demo
WiFi Enhancer
Snake
gla.pev.zvh
Html5 Games
Demm
memory booster
แข่งรถสุดโหด
StopWatch
Clear
ballSmove_004
Flashlight Free
memory booste
Touch Beauty
Demoad
Small Blue Point
Battery Monitor
清理大师
UC Mini
Shadow Crush
Sex Photo
小白点
tub.ajy.ics
Hip Good
Memory Booster
phone booster
SettingService
Wifi Master
Fruit Slots
System Booster
Dircet Browser
FUNNY DROPS
Puzzle Bubble-Pet Paradise
GPS
Light Browser
Clean Master
YouTube Downloader
KXService
Best Wallpapers
Smart Touch
Light Advanced
SmartFolder
youtubeplayer
Beautiful Alarm
PronClub
Detecting instrument
Calculator
GPS Speed
Fast Cleaner
Blue Point
CakeSweety
Pedometer
Compass Lite
Fingerprint unlock
PornClub
com.browser.provider
Assistive Touch
Sex Cademy
OneKeyLock
Wifi Speed Pro
Minibooster
com.so.itouch
com.fabullacop.loudcallernameringtone
Kiss Browser
Weather
Chrono Marker
Slots Mania
Multifunction Flashlight
So Hot
Google
HotH5Games
Swamm Browser
Billiards
TcashDemo
Sexy hot wallpaper
Wifi Accelerate
Simple Calculator
Daily Racing
Talking Tom 3
com.example.ddeo
Test
Hot Photo
QPlay
Virtual
Music Cloud
Posted Under: Threat Research
Tags: Android, ghostpush, gmail, Google, google account, google docs, google drive, google photos, gooligan, mobile malware, snappea
Link to this post: http://blog.checkpoint.com/2016/11/30/1-million-google-accounts-breached-gooligan/
sources:
http://blog.checkpoint.com/2016/11/30/1-million-google-accounts-breached-gooligan/
http://www.redmondpie.com/gooligan-android-malware-infecting-13000-devices-a-day-installs-apps-leaves-fake-reviews/
upvote re steem it "get credit"
"and keep everyone informed!"
"beter and easyer than copy paste"
thx xD***
steem power address for btc deposit:
14yPcZHWYHkL5zCovhEUagE5EJsQXZSEJW
steem address for btc deposit:
1CNCyJq76S7yghpBSbEVHQvE41jGXkihx2
upgrade ram on android audio book!

learn hot to make your android faster audio book tts version multi language available
security audio book release learn what to do!?
audio book
are we being spied?
security book also audio book and latest news:
learn what to do! = )
join the discussion
https://steemit.com/steemit/@eliowilson/
Spanish sp pt de nl it ru cz ch jp any language
join the discussion please thanks :D
resteem to keep up everyone informed up up!!!