IDM - Secure Data Storage

In this article we will talk about current trends and issues related to cloud data storage.
The 21st century is the information age. The more data you generate each day, the more storage space you need. Not all home computers, except mobile devices, can store their own generated data.
Integrated storage capacity continues to grow with the demands of data security. Increasing the volume of proportionately generated data increases the potential number of threats to data storage.
With more and more devices, cloud storage services are becoming increasingly important. Many cloud storage providers promise fast, reliable, and convenient service. The reality, however, is a little more complicated.
What is IDM?
IDM is a public service with protection that exceeds existing government standards for secure storage of information.
Data loss in cloud storage
Although this type of storage is called cloud storage, data is stored in physical locations on land and underground, called data centers.
The storage media is actually a hard disk that is susceptible to similar effects, like a modern HDD. For example, the appearance of damaged sectors, errors due to a voltage drop or physical damage to the disk surface, either due to an operating error or a design error.
Normally, all the information in the backup is duplicated according to a specific schedule. However, this method does not fully guarantee the security of your data. We must also consider the human factor.
Data Theft from Cloud Storage
Data is not always lost due to a technical error. There's often a superficial theft. Criminals may steal information just for fun or to improve their hacking skills. The information may be stolen for a particular purpose: to make money by squeezing or selling valuable data to interested parties.
Not long ago, the media was filled with news about the theft of celebrity photos from cloud storage, which is one of the major players in the mobile market. After the scandal, the company responsible for warehouse security left the market as a third party, but the images were taken all over the world.
Network Attack
The storage where your data resides can be affected by a targeted virtual attack. In this case, you may become a victim, especially if the hacker targets all services with the intent to steal or damage the personal information of a particular user, whether an individual or a company. DDoSattack No matter how secure cloud storage is, simple DDoS attacks can cause large losses to services by slowing or blocking services because users cannot recover their data or use the service.
Human factor
Despite the many cyber threats, the so-called human factor remains the most dangerous element of data protection. For example, an attacker may be placed in a data center as a system administrator. This situation is quite common. Some employees are ready to commit crimes to get rich. Personal information stolen or accessed may be sold to criminal organizations that may cause significant moral and material harm.
Benefits for miners
High profitability
Wohnservice
This is $4 to $5 a month.
Rental 50 GB
Advances in cloud storage technology and privacy practices
According to Gartner, the world's leading research and consulting firm, more than 80% of data loss in the cloud is caused by customers, not cloud storage services. Losses are usually caused by an inefficient work organization with customer data.
According to Gartner's statistics:
64% of all data service customers believe that cloud storage is more secure than traditional methods of
storage and protection of customer information.
However, 75% of customers encrypt their data before uploading it to the cloud. 52% of them
strictly controls the granting of access to corporate data.
Almost 50% of companies regularly analyze and verify their data management systems.
By mid 2018, 80% of all IT budgets will be dedicated to cloud solutions.
49% of enterprises delay the use of cloud storage due to lack of cyber security capabilities.
Currently, only 23% of trusted enterprises are not limited to cloud storage services in terms of
privacy.
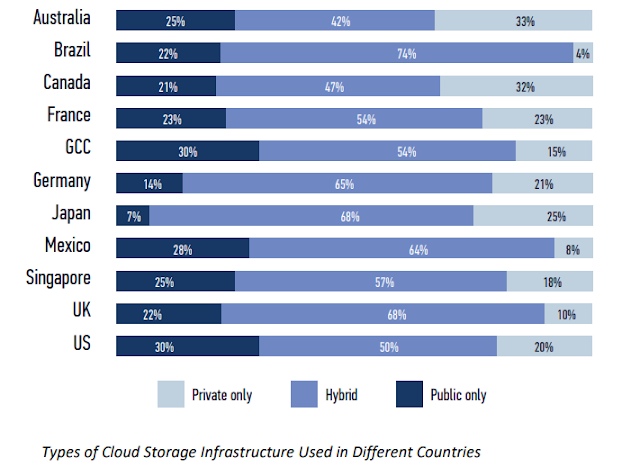
According to data protection experts, the most important factors affecting the secure storage of information are the following:
Encrypt customer data and cloud storage.
Clear and strict rules for accessing customer data.
Means and methods to recover data that has been damaged by the actions of third parties or damage to the device.
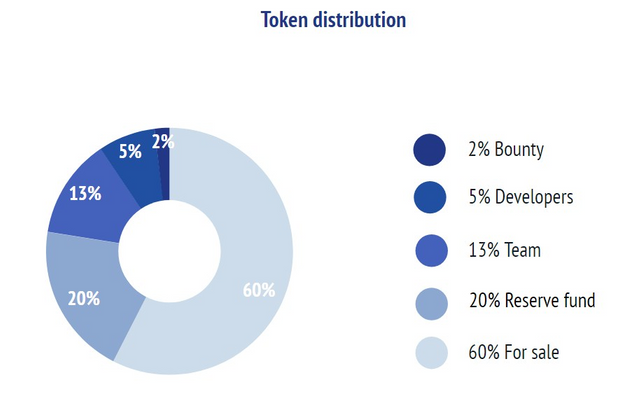
Distribution of tokens
More Information
Website: https://myidm.io/
Whitepaper: https://myidm.io/img/doc/wp_en.pdf
Bitcointalk: https://bitcointalk.org/index.php?topic=3395543.msg35555064#msg35555064
Facebook: https://www.facebook.com/BitschoolAI/
Twitter: https://twitter.com/@BitschoolAI
User Bitcointalk: Noticiasbitcoin
Profile: https://bitcointalk.org/index.php?action=profile;u=1969069
Myetherwallet: 0xeB029ba88D93dcdA31369CC9E1E151Ac622823c2