Information ICO BUGLAB - Cybersecurity Penetration Testing

What is Buglab?
Buglab is just a Ethereum-based platform that connects organizations with a international network of expert cybersecurity research workers.
At the center of our eco system, there are two programs - the buglab competition and Vigilante Protocol, helping companies all over the world to discover and fix vulnerabilities in their digital services or assets.
Which exactly are BGL Tokens?
A lien around the Ethereum block-chain is an electronic digital advantage that is held in a token contract, in hope for a pocket speech.
Even the buglab token, called BGL, is based on the ERC20 benchmark for blockchain tokens.
BGL tokens are required for all trades in the buglab ecosystem, from ordering a competition to profitable pentesters and whitehats.
Who is Buglab for?
The Cyber Security Market
Impacts on returnoninvestment (ROI) are difficult to measure, therefore it takes some time for businesses to comprehend the demand for cyber security services.
For all-too-many businesses, in Addition to people with almost any electronic resources in their websites (content comprised ), then it often takes a breach in Their system before they take action to shore up safety
The victims of cyber attacks infrequently advertise they will have been goals, unless they have to and data vulnerabilities are rarely first-priority as product becomes hurried to advertise, therefore it's difficult, if not impossible, to acquire exhaustive statistics about cyberattacks details, including their frequency or their impact on ROI. But, 1 aspect is completely sure: the trend is on the upswing, with some widely-known economic impacts.
THE Cyber Security MARKET
A stand out case is that of the 2016 U.S. presidential election effort, when a massive email flow throw a shadow over the Democratic party in July 20-16. At the time Reuters reported that a"computer network utilized by Democratic Party nominee Hillary Clinton's effort was hacked as a member of a wide cyberattack on Democratic governmental organizations." The article went on to say that the attack"follows two additional hacks from the Democratic National Committee, or DNC, and also the party's fundraising committee for candidates to your U.S. House of Representatives."
Block Chain Security
The method offered by Buglab deploys smart and expertise contracts across the blockchain.
A blockchain is a set of digital records across which different types of data are all stored. Together, these spread (or decentralized) recordings constitute a database like the pages of a massive ledger book. These digital ledgers are hosted on many servers, which helps to verify and authenticate virtually any transaction. It is a rigorous numerical process, across lots of machines hosted by countless participants, or miners. See Benefits of Using the Blockchain to Reshape Pentesting.
Techniques of Fighting Cyber Crime
Conventional alternatives for fighting cyber crime are not feasible for smaller organizations and organizations. The fee of two common plans outlined here rapidly becomes out of reach for many but huge enterprises.
Penetration tests conducted by a cybersecurity consulting company:
Requires that customers buy the service in terms of total billable hours, regardless of test outcomes. The majority of penetration tests conducted by consulting firms are finished by you, maybe two pentesters. This usually means that your client is only able to take advantage of this methodology and also skill set of just two consultants.
Bug Bounty challenges:
Information security researchers have been paid on a per-vulnerability-uncovered foundation. Companies frequently end up becoming charged to repair problems not entirely consequential to their revenue or customers. This is described in greater detail in the subsequent section.
The Buglab Solution
Even the Buglab platform connects organizations who have information security needs, which is just about all them, with a community of certified cybersecurity penetration testers in a off-beat environment, where testers are rewarded whenever they find machine vulnerabilities, ranked by seriousness and possible impacts. It's done as a race against time. Significantly, finding exceptional vulnerabilities is ranked above only producing a set of topics.
Core Features of the Buglab Platform
The Buglab platform enables customers to either use the bulk of pentesters or select a verified group from a known company. Teams must involve no less than five pentesters.
- Public Contest
- Private Contest
- Selection Filters
- Triage System
- Reports
- Chat
- Fix Companion
- Client-Managed
- Mediation
- Leader-board
Defining Requirements
The set of likely usage cases is quite long. Scenarios may possibly consist of discovering malicious SQL injection, which routes database material to an individual hacker. A system could have authentication bypass vulnerabilities. Oily company information could possibly be unencrypted. File uploads may not be protected. User sessions might be susceptible to take over by malicious stuff. Perhaps the vulnerability is relatively straight forward: for instance, a company may have insufficient log in security. Even the Buglab strategy addresses both these and other vulnerabilities in a cheap manner to tackle cybercrime and its impact on customers' bottom lines
Real Time Reporting
The customer company staff follow the competition as it unfolds instantly to observe exactly the reported vulnerabilities and reduction recommendations. They have the means of communicating with the pentesters to follow up. The platform can also incorporate with other reporting programs at your company's discretion.
The Contest
A client signs up on the stage and information about itself, including its own products and services. Afterward, using a very simple and user-friendly interface, it subscribes to a contest contract, choosing rules.
Clients are able to customize the confidentiality1 of this contest, the kind of management they need, and also the contest cost, which depends upon the selected plan and also an optional incentive. When necessary, a Buglab team will connect to clients to help them establish up program parameters.
Contest Scoring
Up on the competition launch our community of pentesters that have enrolled with Buglab is notified. Our international cybersecurity pentesters then analyze, test, and report back to the vulnerabilities of a solution on the Buglab platform.
After the competition finishes, the role of Buglab is limited to vulnerability scoring and triage working with the Common Vulnerability Scoring System 3 (CVSS3) benchmark described in Vulnerability time stamp. Pentesters are compensated in accordance with their position at the competition.
Vulnerability Timestamp
Outcomes of penetration evaluation competitions are contingent on the Vulnerability time-stamp (VTS) that corresponds to the exact moment a vulnerability has been reported.
It had been necessary to prepare a ranking system so as to be able to reward the best researchers according to both their general score and time. A pentester's overall score for a competition is corresponding to the sum of each the scores they have received for discovering a vulnerability. The score for a vulnerability is based on objective and quantifiable standards, as a result of CVSS3.
For such cases, researchers gain CVSS3 scores depending on the speed where these could uncover the vulnerability. The first to get done so will receive full marks, and the Ones That follow will probably see that their rating decrease according to their position in time and also the Amount of all pentesters who have uncovered that Exact Same vulnerability
Fix Companion
At the Enterprise level, Buglab will verify that the fix was implemented. When confirmed as mended, a Buglab team of analysts may update the status consequently in the stage. A"fix" can be diminished by Buglab to allow the company a opportunity to address the vulnerability again. The Business will be booted up to five attempts to address the vulnerability issue
Through the entire length of the challenge businesses can talk with pentesters and get reports, they will have the ability to implement tips to remedy the vulnerabilities in real time. That is especially useful in the event the vulnerabilities and the associated fixes are time sensitive and painful. Organizations need wait before the end of the contest to implement a fix.
Service Levels
For a fixed price, Buglab will arrange insight evaluations done by pros pre-approved by our team. Highlights of these features with the three service levels are provided in the following table.
Vigilante Protocol
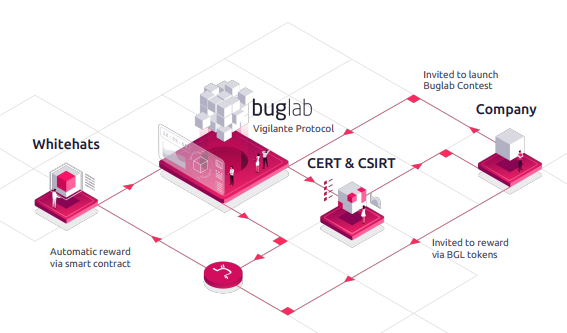
Our Vigilante Protocol Smart Contract enables communication of sensitive information in a private and secure manner through the applicable licensed federal government, namely computer security incident response teams (CSIRT), which are administered by most countries across the planet.
In addition to telling the company in question of a vulnerability, both CSIRT and Computer Emergency Response Teams (CERT) will have to triage and score it. In exchange, when the company marks a vulnerability as resolved, the answer teams will soon be rewarded in tokens that emerge of this Vigilante Protocol Reserve, as partnerships have been forged with Buglab.
Assigning Pentester Status
For a white hat to accomplish pentester status and also to be able to take part in the numerous challenges, they need to when signing up to your Buglab stage, meet two mandatory requirements, i.e. furnish ID plus one or more certificate. Country of residence is optional. The account is only approved once those conditions have been validated.
Yet another means to achieve pentester status is by acting under the Vigilante Protocol in order to prove one's abilities and willingness to take part within our preventative security application. Once they have collected a number of 20 points, in agreement with the CVSS3 grading system, they are going to have the ability receive the status and participate in the challenges.
The Buglab Token
Even the Buglab Token (BGL) will be introduced into incentivize penetration testing in the blockchain atmosphere. From the context of the Buglab adventure, token trade happens in the following situations:
● To reward competition winnersup to the top three in positions, or as customized with the client.
● To cover the expense of a competition, for example trade costs.
● To enable and tokenize"leaning" performance for white vases.
● To fund both VPR and BTR.
● To reward CERTs and CSIRTs to get triaging of both vulnerabilities and help build new partnerships.
Information Token Sale
- Symbol BGL
- Total Token Supply 425,000,000
- Token sale allocation 170,000,000
- Funding goal Equivalent of $20,000,000
- Public sale price Equivalent of $0.15
- Type ERC20
Bonus
- Pre-sale 25%
- Tier Public sale period Bonus %
- Tier 1 First 24H 20%
- Tier 2 Week 1 15%
- Tier 3 Week 2 10%
- Tier 4 Week 3 to end 0%
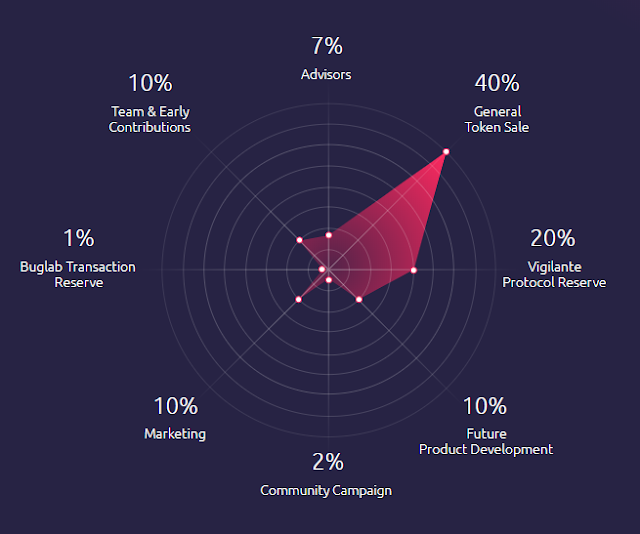
TOKEN DISTRIBUTION
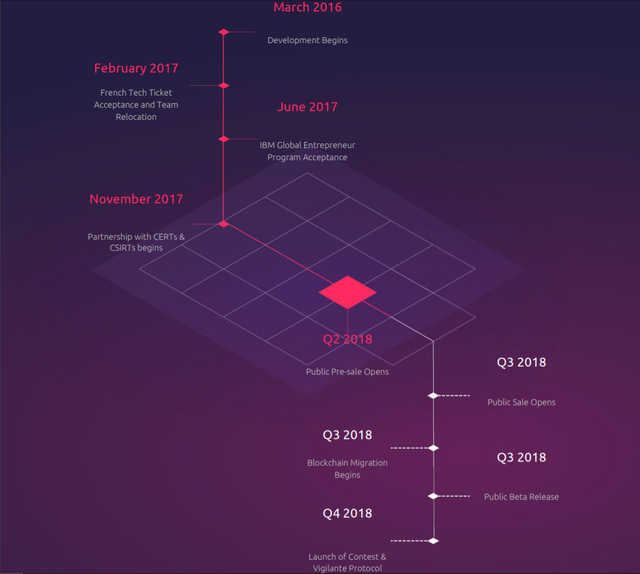
ROADMAP
Additional Information:
Website: https://buglab.io/
White paper: https://buglab.io/assets/docs/Buglab_WhitePaper.pdf
Twitter : https://twitter.com/joinbuglab
Telegram : https://t.me/buglab
Bounty Link : https://bitcointalk.org/index.php?topic=4446991
Bitcointalk Profile : https://bitcointalk.org/index.php?action=profile;u=1063830
My Username Bitcointalk: MN_Sidik
My ETH wallet address: 0x2016deDc02912bE50DbeD8e8093D1e3fF528bf54