Datawallet! ICO и идея проекта.

Interactive environments are vulnerable from a data security perspective. An example of interactive environments is any of the systems with communication capabilities, such as e-mail, computer networks, the Internet.
E-mail is any kind of communication used by computers and modems. The most unprotected places in e-mail include the outgoing mail item of the sender and the recipient's mailbox. Each of the e-mail software packages allows you to archive incoming and outgoing messages to any other address, which can lead to abuse by intruders.

E-mail while ensuring the forwarding of messages can bring significant harm to the recipient of messages. To prevent undesirable consequences, you should use other methods of security, including:
• You can not immediately start programs received by e-mail, especially attachments. It is necessary to save the file on disk, check it with an antivirus program and only then run it;
• It is forbidden to inform your password and personal data, even if the sender offers something very tempting to the addressee;
• when opening received MS Office files (in Word, Excel), it should be possible not to use macros;
• It is important to try to use proven, as well as newer versions of email programs.
One of the important problems for Internet users is the problem of data security in the network itself. Connecting the user to the resources is done through the provider. To protect information from hooligan elements, unskilled users and criminals on the Internet, a system of permissions or access control. Each data file (or other computer resources) has a set of attributes, which reported that the file anyone can view, but changing it is entitled to only the owner.
Another problem is that no one except the owner cannot browse the file, despite the fact that the visible names of these information resources. Typically, a user seeks in some way to protect your information, but you must remember that system administrators can overcome the protection system. In this case, come to the aid of various methods of information encryption using keys developed by the user.
One of the problems with working on the Internet is to restrict access to some categories of users to information resources (children and students). This can be done with the help of special software products – firewalls (Net Nanny, Surf Watch, Cyber Patrol). They are based on the principle of filtering on key words fixed list of field services of the WWW in which there is unwanted material. Programs of the same type, leading recording sessions, the Internet and deny access to certain network locations, may be installed in office and other agencies to prevent the phenomenon of workers spending time in personal interests.
Internet system where many users have their own Web servers, contains advertising or reference information on Web pages. Competitors can spoil of the contents. In order to avoid problems in such situations, you can regularly view Web pages. Upon detecting corruption of information you need to restore it using the pre-prepared copies of files. It is important to keep in mind that to ensure the security of information on servers owe providers, which systematically scan the log and update the software if it found problems in defense.
And now appeared good solution all this problems - Datawallet!

Datawallet provides users with a self-sovereign wallet that puts them in charge of their data, and allows them to monetize as well as utilize an asset that is rightfully theirs. It empowers developers to leverage a completely new data universe to build the most advanced applications ever. And it provides companies with insights that will boost their operations on a never before seen scale.
How is work
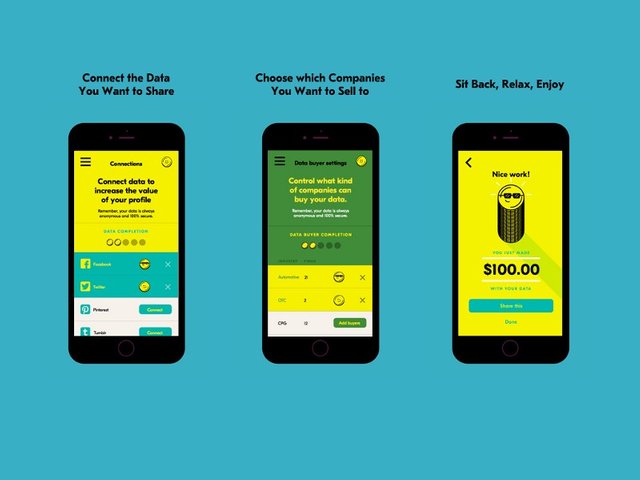
Three easy steps:
Connect the data you feel comfortable sharing. This can be data from Facebook, Twitter, Instagram and Pinterest, with more platforms to be added in the coming months.
Select your Data Buyers. You can choose from more than 19 types of Data Buyers to sell your data to — from marketing agencies to producers of household appliances to banks.
Enjoy! Sit back and relax, while we take care of all the work. Whenever a company uses your data, you’ll get paid.
Datawallet provides users with a self-sovereign wallet that belongs to them and only them. It empowers them to unlock the financial and utility value of an asset that is rightfully theirs.
Datawallet leverages blockchain technology to deliver an uncompromisingly transparent personal data marketplace. Blockchain technology obviates the need for data providers to trust Datawallet or other third parties through the two pillars of the Datawallet 2.0 marketplace—encryption everywhere (EE) and the smart encrypted data contracts (SEDC).
Token Sale Summary
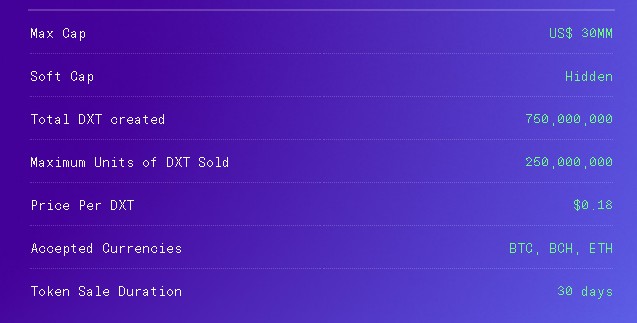
Data Exchange Token
DXT serves as the primary medium of exchange within Datawallet’s closed economy, enabling two primary behaviors:
Earning Tokens
Users earn token through expressively sharing their data with select companies.Spending Tokens
Users can utilize their tokens in order to use pay for AI driven services in the Datawallet App Store.
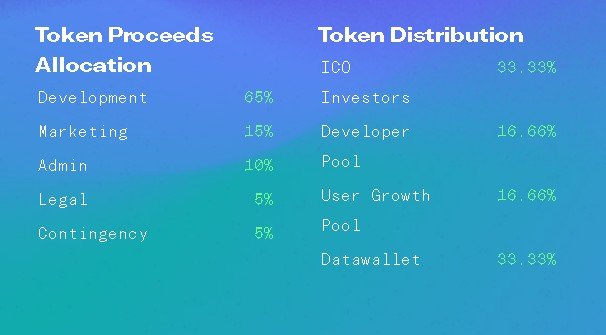
You will get paid $1-$50 each time your data is sold. The amount depends on three things:
The amount of data you connect. The more data you link to your DataWallet profile, the more value it will have.
The amount of data that Data Buyers purchase. The more companies you allow to buy your data, the higher the likelihood that you’ll make a sale.
Some luck. How much you make will depend, to an extent, on what the Data Buyers are looking for, and how unique or relevant your data is to them.
Whitepapper https://tokensale.datawallet.com/pdf/datawallet_whitepaper.pdf
Bitcointalk https://bitcointalk.org/index.php?topic=2385841.0
Twitter https://twitter.com/DataWalletHQ
My bitcointalk url https://bitcointalk.org/index.php?action=profile;u=1184171