SIZ Approved Course | Lecture 02 | Types of cyber attarcks @wiltord
Before we start click hereto see my previous course about cyber attacks to understand what are cyber attacks
also all my images i used in these post coe from thesesource
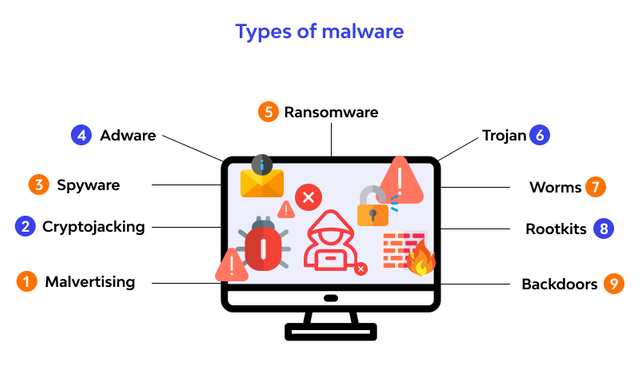
. Malware
Malware is a kind of utilization that can play out an assortment of malignant errands. A few strains of malware are intended to make relentless admittance to an organization, some are intended to keep an eye on the client to get qualifications or other important information, while some are essentially intended to cause interruption.
A few types of malware are intended to blackmail the casualty here and there. Maybe the most remarkable type of malware is Ransomware – a program intended to scramble the casualty's documents and afterward request that they pay a payment to get the decoding key.
. Phishing
A Phishing assault is the place where the assailant attempts to fool a clueless casualty into giving over important data, like passwords, Mastercard subtleties, protected innovation, etc.
Phishing assaults frequently show up as an email claiming to be from an authentic association, like your bank, the assessment division, or another confided in substance.
Phishing is presumably the most well-known type of digital assault, generally on the grounds that it is not difficult to do, and shockingly successful.
. Man-in-the-center assault (MITM)
A man-in-the-center assault (MITM) is the place where an aggressor catches the correspondence between two gatherings trying to keep an eye on the people in question, take individual data or certifications, or maybe modify the discussion somehow or another.
MITM assaults are more uncommon these days as most email and talk frameworks utilize start to finish encryption which keeps outsiders from messing with the information that is sent across the organization, whether or not the organization is secure or not.
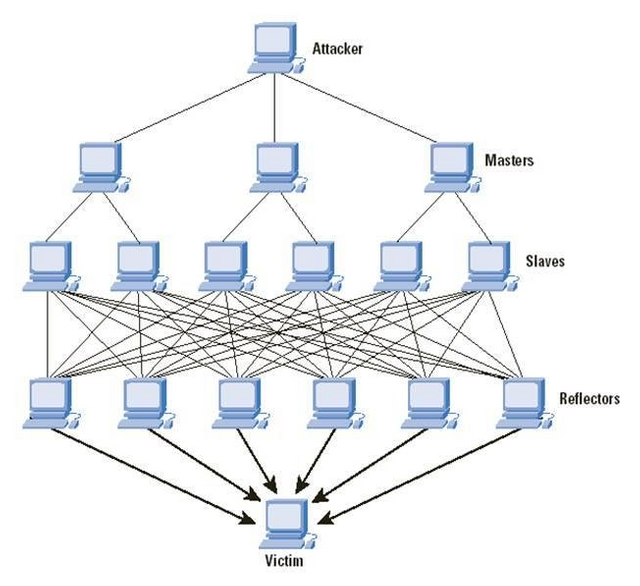
. Distributed Denial-of-Service (DDoS) attack
A DDoS assault is the place where an assailant basically floods an objective worker with traffic trying to upset, and maybe in any event, cut down the objective. Notwithstanding, not at all like conventional refusal of-administration assaults, which most modern firewalls can recognize and react to, a DDoS assault can use various compromised gadgets to besiege the objective with traffic.
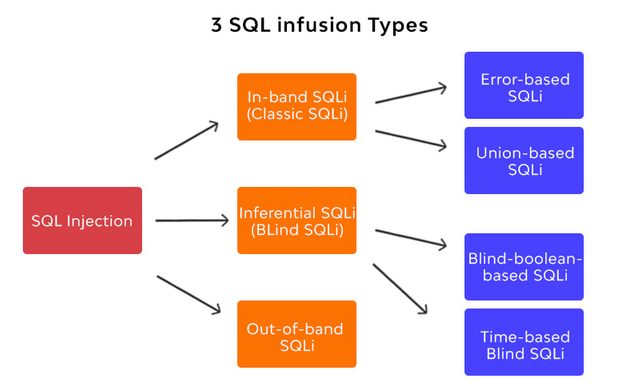
. SQL infusion
SQL infusion is a kind of assault which is explicit to SQL information bases. SQL information bases utilizes SQL explanations to question the information, and these assertions are ordinarily executed through a HTML structure on a page. In the event that the information base consents have not been set as expected, the aggressor might have the option to take advantage of the HTML structure to execute inquiries that will make, read, change or erase the information put away in the data set.
On the off chance that you like this, you'll love this:
Forestall, Detect and Recover from a Ransomware Attack
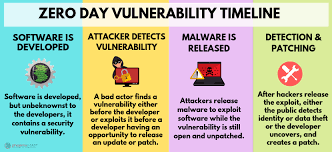
. Zero-day exploit
A zero-day exploit is the place where digital lawbreakers learn of a weakness that has been found in certain generally utilized programming applications and working frameworks, and afterward target associations who are utilizing that product to take advantage of the weakness before a fix opens up.
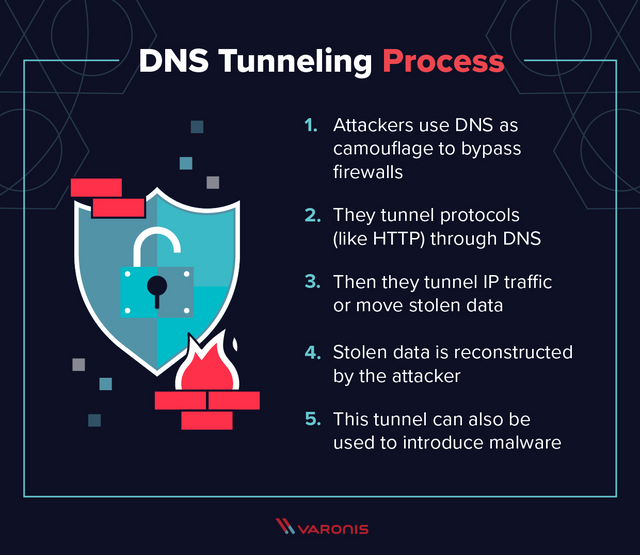
. DNS Tunneling
DNS burrowing is a complex assault vector that is intended to furnish aggressors with diligent admittance to a given objective. Since numerous associations neglect to screen DNS traffic for malevolent movement, aggressors can embed or "burrow" malware into DNS inquiries (DNS demands sent from the customer to the worker). The malware is utilized to make a steady correspondence channel that most firewalls can't distinguish.
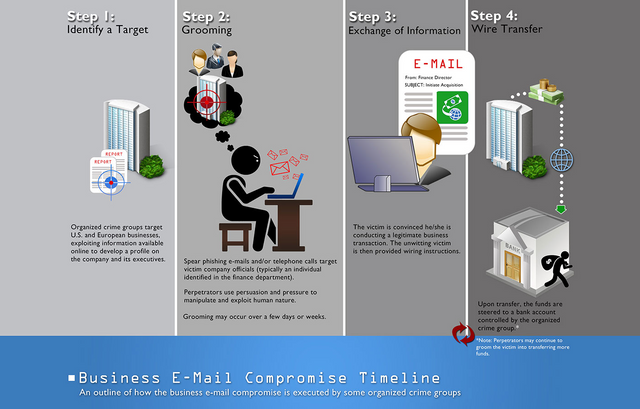
. Business Email Compromise (BEC)
A BEC assault is the place where the assailant targets explicit people, generally a worker who can approve monetary exchanges, to fool them into moving cash into a record constrained by the aggressor.
BEC assaults as a rule include arranging and examination to be successful. For instance, any data about the objective association's chiefs, workers, clients, colleagues and potential colleagues, will assist the aggressor with persuading the representative into giving over the assets.
BEC assaults are perhaps the most monetarily harming form of digital assault.
. Cryptojacking
Cryptojacking is the place where digital lawbreakers compromise a client's PC or gadget and use it to mine cryptographic forms of money, like Bitcoin. Cryptojacking isn't too known as other assault vectors, nonetheless, it shouldn't be belittled.
Associations don't have incredible perceivability with regards to this sort of assault, which implies that a programmer could be utilizing important organization assets to mine a digital money without the association having any information on it.
Obviously, filtering assets from an organization network is definitely less hazardous than taking important information.
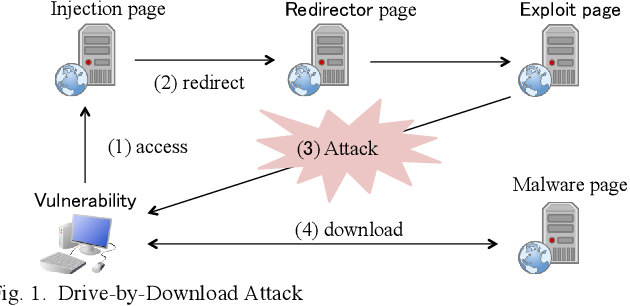
- Drive-by Attack
A 'drive-by-download' assault is the place where a clueless casualty visits a site which thusly taints their gadget with malware. The site being referred to could be one that is straightforwardly constrained by the assailant, or one that has been compromised.
At times, the malware is served in content like flags and promotions. Nowadays exploit units are accessible which permit amateur programmers to effectively arrangement pernicious sites or appropriate noxious substance through different means.
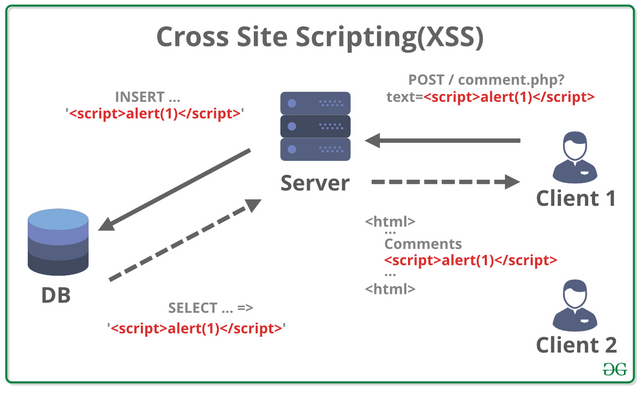
. Cross-site prearranging (XSS) assaults
Cross-site prearranging assaults are very like SQL infusion assaults, despite the fact that as opposed to separating information from a data set, they are commonly used to taint different clients who visit the site. A basic model would be the remarks area on a site page.
On the off chance that the client input isn't sifted before the remark is distributed, an aggressor can distribute a pernicious content that is stowed away in the page. At the point when a client visits this page, the content will execute and either contaminate their gadget, or be utilized to take treats or maybe even be utilized to extricate the client's qualifications.
Then again, they may simply divert the client to a pernicious site.
. password Attack
A secret word assault, as you might have effectively speculated, is a sort of digital assault where an assailant attempts to theory, or "break" a client's secret key. There are various strategies for breaking a client's secret key, albeit a clarification of these various methods is past the extent of this article.
Nonetheless, a few models incorporate the Brute-Force assault, Dictionary assault, Rainbow Table assault, Credential Stuffing, Password Spraying and the Keylogger assault. What's more, obviously, assailants will frequently attempt to utilize Phishing methods to get a client's secret key.
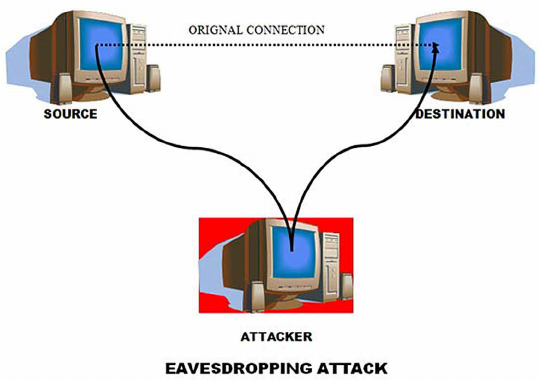
.Eavesdropping attack
Some of the time alluded to as "sneaking around" or "sniffing", a listening in assault is the place where the assailant searches for unstable organization correspondences to catch and access information that is being sent across the organization. This is one reason why workers are approached to utilize a VPN while getting to the organization network from an unstable public Wi-Fi area of interest.
. Simulated intelligence Powered Attacks
The utilization of Artificial Intelligence to dispatch refined digital assaults is an overwhelming possibility, as we don't yet have a clue what such assaults will be prepared to do. The most prominent AI-fueled assault we've seen to-date elaborate the utilization of AI-controlled botnets which utilized slave machines to play out an immense DDoS assault.
Nonetheless, we're probably going to see significantly more refined assault vectors to come.
Simulated intelligence fueled programming can realize what sorts of approaches work best and adjust their assault strategies in like manner. They can utilize insight feeds to rapidly recognize programming weaknesses, just as sweep frameworks themselves for possible weaknesses. Man-made intelligence produced text, sound and video will be utilized to imitate organization chiefs, which can be utilized to dispatch extremely persuading Phishing assaults. In contrast to people, AI-fueled assaults can work nonstop. They are quick, proficient, moderate and versatile.
. IoT-Based Attacks
As it right now stands, IoT gadgets are by and large less secure than most present day working frameworks, and programmers are quick to take advantage of their weaknesses. Likewise with AI, the web of-things is as yet a generally new idea, thus we are yet to perceive what techniques digital crooks will use to take advantage of IoT gadgets, and to what in particular finishes.
Maybe programmers will target clinical gadgets, security frameworks, shrewd thermometers, or maybe they will try to think twice about gadgets to dispatch enormous scope DDoS assaults. I surmise we will discover in the years to come.
i believe with this one can have an idea of what are the types of cyber attarcks thanks
my next course is about steemit security next week
I Really Specially Thank the SIZ Admin and Steem Infinity Zone Team.
@cryptokraze
@vvarishayy
@suboohi
@qasimwaqar
@arie.steem