Earlier Attempts at Cryptography

Own Image, Created by @gamsam with Image from Pixabay | Photographer: skeeze
We’ve talked about how the miners store the public copies of the bitcoin ledger; now imagine if the ledger was a .txt which you could just change or edit at will. Or imagine a group of miners deciding together to go edit or change a transaction in the past. There’s nothing stopping them unless there is cryptography involved.
What is Cryptography?
Cryptography is derived from a Greek word which translates to “secret writing”.
How then does it relate to bitcoin?
How does it help us secure the ledger and ensure the integrity of our transactions?
It is the basically the art and science of secure communication. You can think of it as a really challenging and fascinating word puzzle in games. It was developed in war and used for war and politics. It enables people to write a secret message and get it across to allies who only have the way of interpreting it. This way, even if the enemy were to intercept the message, the contents would and could not be revealed.
Ceaser Cipher
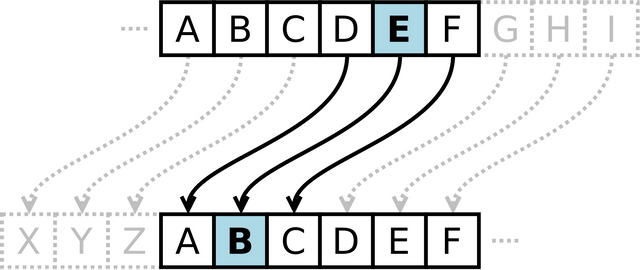
The action of a Caesar cipher is to replace each plaintext letter with a different one a fixed number of places down the alphabet. The cipher illustrated here uses a left shift of three, so that (for example) each occurrence of E in the plaintext becomes B in the ciphertext. By Matt_Crypto, Public Domain, Link
An example is the Caeser Cipher credited to Julius Ceaser. Letters were basically coded with other letters from left to right and when the message was delivered, you could decode it by translating it back to the original letters.

A construction of two rotating disks with a Caesar cipher can be used to encrypt or decrypt the code. By Hubert Berberich, Public Domain, Link
In the cipher shown below for example, “hello” becomes “vgttx” and only a person who has or understands the cipher can decode the message.

The cipher is not a very reliable and secure approach because if somebody just happens to find the cipher, he would posses the key to unlock all the secret messages. Also, another user can actually crack the patterns of a cipher and decode the whole message.
Enigma Machine

Military Enigma machine, model "Enigma I", used during the late 1930s and during the war; displayed at Museo scienza e tecnologia Milano, Italy. By Alessandro Nassiri CC BY-SA 4.0, Link
A few steps after that came the Enigma Machine. The Enigma Machine was an advanced form of cryptography that used the enigma code. The machine was used during the 2nd world war. This machine was portrayed in the movie “The Imitation Game”.

Enigma in use, 1943. By Bundesarchiv, Bild 183-2007-0705-502 / Walther / CC-BY-SA 3.0, CC BY-SA 3.0 de, Link
It is a much more complicated way of encrypting a message that used a much more complicated algorithm. It was developed by the Germans to use in WWII. The message was encrypted and broadcast over radio. The recipient will them plug it into their own Enigma Machine and the message would be decoded to German.
The Enigma was so hard to crack because it had different rotors and even the same letter would appear as different letter when encrypted. This made it very difficult to work backward from and break the patterns. Of course there are more sophisticated algorithms today, but back then this was a monumental effort to overcome.

Interesting history. Thanks for sharing