Understanding the Mimblewimble Protocol
On the blockchain network which is very much public and transparent, users are eligible to see every transaction carried out on the blockchain, the addresses, amount sent, the timestamp of the transaction and other vital information. This reveal certain information and one might want to keep them private that leads us to the mimblewimble protocol.
What is the Mimblewimble Protocol? |
|---|
Mimblewimble protocol sounds like a funny word. If you notice, it is a term used in Harry potter movie as the name is extracted from it. The term isn't an English word that is valid but it has come to form a notable block chain which came into existence in the year 2016 of which credit is traced to Tom Elvis Jedusor.
This person or group of persons is anonymous and released its white paper that year. This is the scope. Mimblewimble protocol is actually a blockchain protocol designed for effective storage of transactions data that comes with enhanced scalability and improved privacy.
Unlike the blockchain protocols used in earlier times, mimblewimble comes with a storage of data that is referring to an extent that only uses involved in the transaction can see the data of that transaction. In these earliest blockchains, scalability was a problem and we can see how bitcoin second layer network has dealt with that for the lightning network whereby redundant transactions are eliminated from on-chain and off chain to increase speed as well as improve scalability.
As such, the exchange transactions on the lightning network are almost fee less since - are not present rather the nodes involved are responsible for transaction validation. Mimblewimble deals exclusively with privacy and scalability issues in such a way that transaction data is hidden from outsiders and redundant transactions are eliminated from the chain.
Data stored on this protocol can be downloaded easily and very fine but the data of the transactions remain completely hidden, only the users involved in this protocol or in the transaction can actually see the details. And this brings about privacy on the member window protocol such that users can maintain this anonymity of transactions placed without exposing the addresses to outsiders. Let's take a look into how cryptographic protocols can be utilised in mimblewimble.
Cryptographic protocols can be utilised in mimblewimble. |
|---|
The main cryptographic protocol utilised in this number window protocol is there Elliptic curve cryptography and it operate on the concept of discrete logarithm to assign private keys to every transactions placed.
Log2(64)=6
Log2(128)=7
The logarithm above chose to multiply itself six times to give the required output of 64 as shown in the first expression. The 64 in brackets is as a result of the two which multiplies itself six times. The second expression shows to multiply itself 7 times to give 128 which tends to be the output. In this way, numerous and complete discrete logarithms are performed to assign private keys to transactions on the protocol plotted on the Elliptic curve cryptography.
The operation of the discrete logarithm is beyond normal logarithm expressions shown above. The discrete logarithm is more complex to ensure anonymity of transactions on mimblewimble. Other existing cryptographic protocols used in mimblewimble our confidential transactions, CoinJoin and the likes of them.
What is this CoinJoin all About? |
|---|
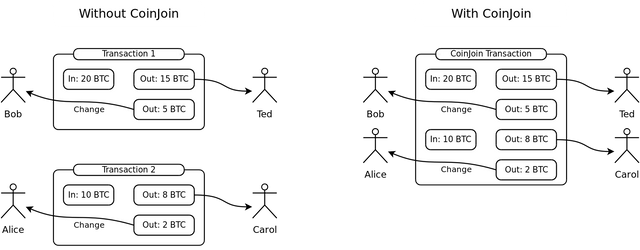
The coin join is a cryptographic protocol utilised in the Bitcoin network whereby different senders from different parts agree to sign a smart contract in such a way that the output of the transaction is equal and there's a quality in the senders addresses. In the process of doing so, it becomes extremely hard for outsiders to detect which transaction belongs to a sender or the other ensuring anonymity of transactions.
From the image above, the part labelled 1 shows UTXO transaction from Bob having the input in 20 BTC, with 2 outputs, 15 BTC is for Fred and 5 BTC changed routed back to Bob's wallet. Likewise Alice's case, having the input to be 10 BTC, with two outputs of which 5 would be sent to Carol and 5 routed back to Alice's wallet and in such case, it is very easy to know who sends a transaction. In the part labelled 2, this uses signed to perform coinjoin in the way that it becomes hard for outsiders to know which sender or account is sending an amount.
In conclusion, the mimblewimble protocol has ensured anonymity of transactions compared to other block chains which has its transactions transparent to outsiders both the name of the sender, the address and amount. So for those who love their transactions to be private can use this protocol. How does this protocol work? Check my next post
Disclaimer :Any financial and crypto market information provided in this post was written for informational purposes only and does not constitute 100% investment advice. It's just basic knowledge every crypto trader or investor should have

https://twitter.com/bossj23Mod/status/1730646435857568030?t=TB9jKQXjDxL-9xIIol24iQ&s=19
Wow nice article bro.
Thanks bro
Dear @bossj23 ,
We appreciate your active participation and contributions to our community. To ensure a positive environment for all members, we have implemented a set of guidelines to maintain respectful and constructive discussions while upholding community guidelines.
This is an interesting post on mimblewimble protocol that you have shared, keep sharing quality post in the community
Now Engage, Connect, and Inspire Each Other to Reach New heights.
Thank You.
Thanks for verifying my post