Grassroot Crypto Education (Vol.4) - Cryptography: Private-Key Encryption, Public-Key Encryption and Hash Functions|| assignment post by@madilyn02

Special greetings to everyone especially my dear friends, I hope you are all we and I wish you you all success.
Today I'm participating in the steemkids crypto education for children and I will be giving answers to the assigned tasks by the professor @fredquantum.
It would be nice if you continue reading and get to he end of this post. Provide a comment if you wish to...

Define Cryptography. Explain Private-Key Encryption, Public-Key Encryption, and Hash Functions. What is the distinctive difference between Private-Key Encryption and Public-Key Encryption? .
Cryptography
Cryptography is the study or practice of how to secure communication in such a way that only the people conversing can know what is said or can see the content of the communication.
In cryptography, only the people involved can unlock the information by using a cryptographic element such as the private key.

Private key Encryption
To encrypt means to convert a message to a coded one so that only the person it is sent to can access it.
Private key Encryption simply means using the private key to encrypt or code a message and when this happens, the outsiders will not have access to it.
The sender of the message pases the private key to the recipient so that he can be able to unlock the message from his destination.
This means that in private key Encryption, one key is involved which the sender sends to the receiver so that he can decrypt and read the message.
Public key Encryption
Unlike the private key Encryption, two keys are involved in this type of cryptography.
In public key Encryption, two keys are involved, one for encryption and the other for decryption.
The sender uses the public key to to encrypt the message while the recipient will use use the private key to decrypt the information and like the first type of cryptography, no outsider can get access to the message.
Hash functions
Hash function is any function that converts the data of the whole transaction into a fixed size values and these are what is called hash codes or hash values.
This process is irreversible, which means that data that has been stored about a crypto transaction cannot be changed or reversed. Each input produces a different output and because of this level of security, there is no way that fraud or fake transactions can be employed.

Difference between Private-Key Encryption and Public-Key Encryption
In private key decryption, one key, the private key, is involved in encrypting and decrypting the messages sent.
In public key Encryption, two keys are involved, public and private key, one for encrypting and the other for decrypting.

What happens to outsiders if a message is encrypted? Give a brief example. Visit https://andersbrownworth.com/blockchain/hash, enter two different inputs, and show your observation. (Screenshot required).
When a message is encrypted, only the person it is sent to can see what the content is about. The outsider might be present when the message was sent and might even see the message, but he is blinded to it so to speak and he cannot know what is contained in the content that is shared since he doesn't have the private key to decrypt the message.
Example of this:
David sends a message to Abigail in the presence of Kyle and Karen. Now the transaction is taking place between David and Abigail and Abigail is the recipient. She unlocks the encrypted message with the private key and reads what is in it.
Kyle and Karen, although being present were not able to see the message because they do not have access to the private key.
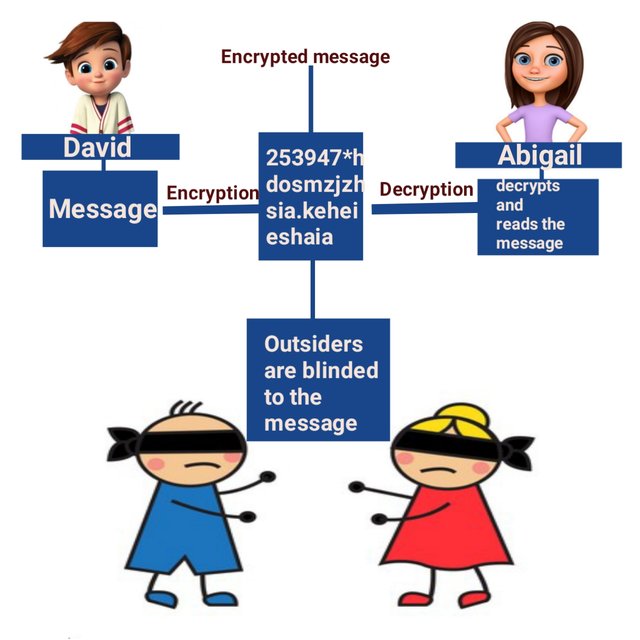 created on pixelab app
created on pixelab app
My observations from https://andersbrownworth.com/blockchain/hash after entering two inputs
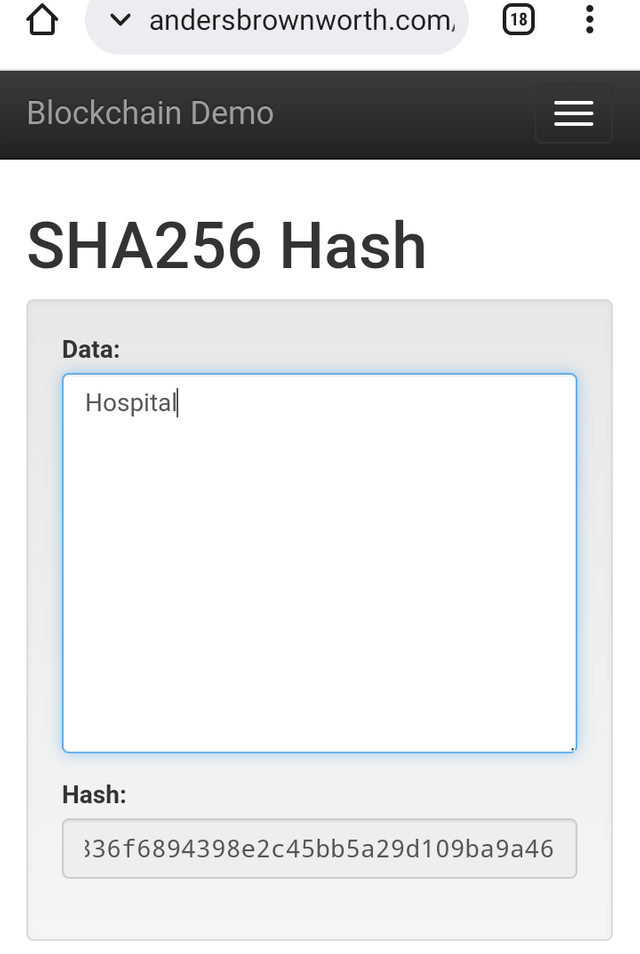
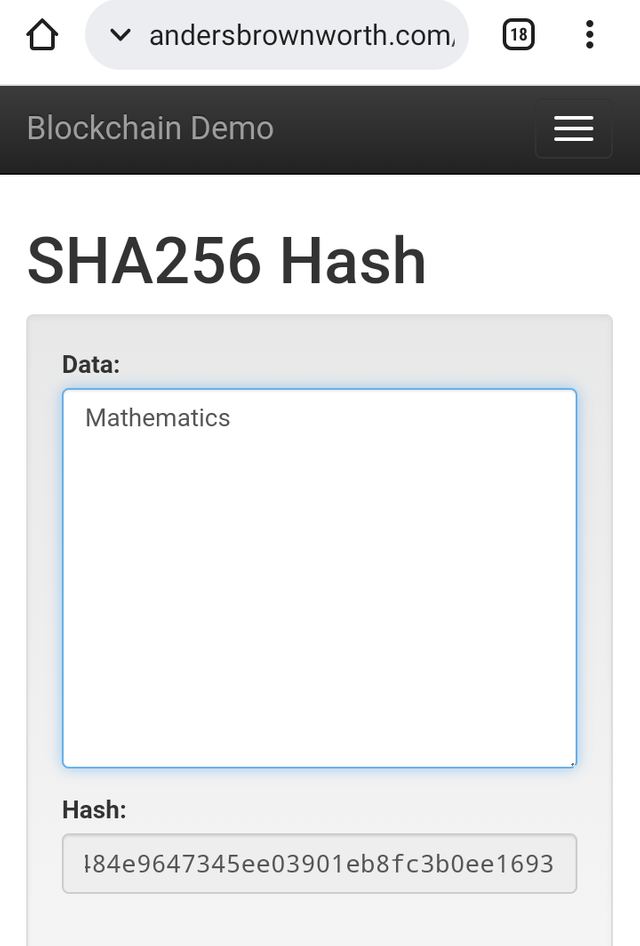
I inputed Hospital for the first one and then mathematics do the second one.
The screenshot below shows the result it gave:
 |  |
|---|
Hospital
97e9623661f2970acb41495153876df0836f6894398e2c45bb5a29d109ba9a46
Mathematics
cdba6dc33e22fb468026fce488b4a6dc484e9647345ee03901eb8fc3b0ee1693
I was able to observe that the two hash produced are different and it's just like the professor said, different inputs will have different hash.
Also both outcomes came with the same length from the result shown above.

Conclusion
I appreciate the professor @fredquantum for the nice and well explained lesson. I have learnt so much here and I promise to continue doing my best to improve everyday.
If you have read to this post to this level, I appreciate you so much.
I invite @chimeroselam, @bossj23, @ibtisamwaqas, @firyfaiz to participate in the crypto lesson assignment for this week.
Cc,
@steemkidss
@ngoenyi
@goodybest


You've written so well about this topic, it shows that you really understand it! Congratulations 🎉👏🎉 to you as you've scored 10/10. Continue learning and the sky will be your starting point.
Thank you ma'am for the encouragement, I'll keep doing my best 🤗
I'll certainly Join you
Alright 😊
Awesome content dear
Already posted. Thanks for the invite. Your editing is very rich thanks for participating
Ok dear, thank you too. I hope to read yours soon 😊
I'm happy you will thanks dear
Amazing dear I wish I could be like you.