Grassroot Crypto Education (Vol.4) - Cryptography: Private-Key Encryption, Public-Key Encryption and Hash Functions | 10% payout to @steemkidss by @chimeoselam
Greetings beautiful friends in #steemkids community.
Here is another week of our crypto grassroots education by our prof @fredquantum
It's my delight to share in the.vume four of the classes on cryptography and it's elements.
Homework Task

1 (a). What Is Cryptography
This is the type of communication in which the interaction is based only between the sender and the recipient. It is a secured communication that hides the conversation or message (data) to be shared among only the sender and the receiver without the knowledge of others.
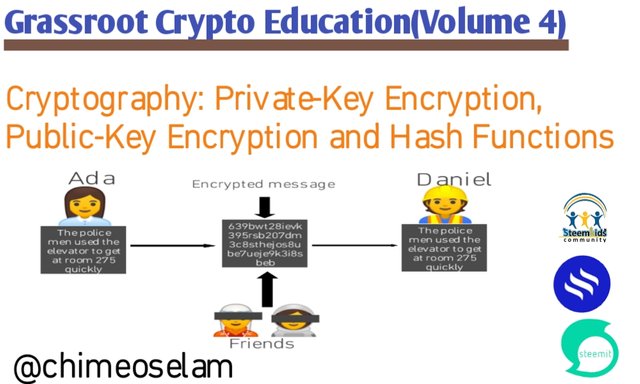
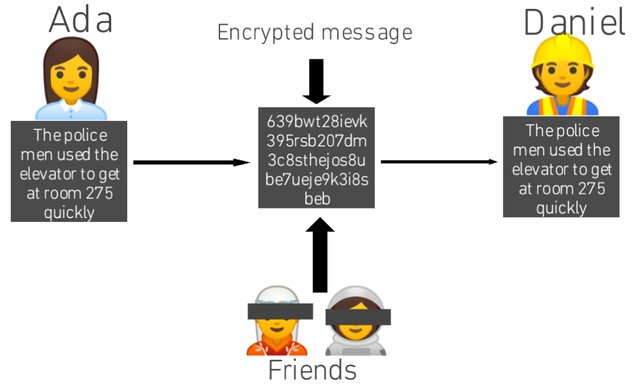
Fir instance, Ada was sitting with her friends and sent a message to Daniel without her friends seeing the content if the conversation.
Cryptography is subdivided into 3 types which are ; private-key, public-key and hash function encryption.

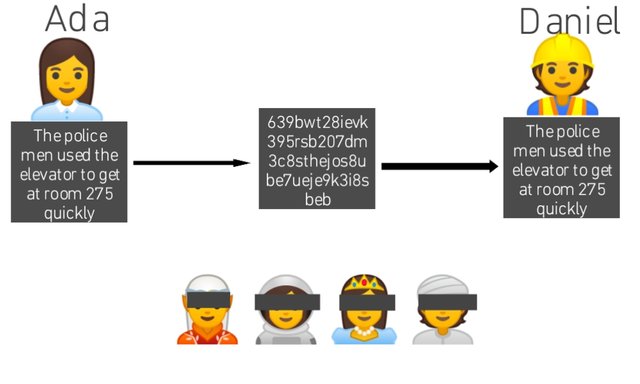
1 (b). What Is Private-key Encryption
Private-key Encryption can be defined as the use of private-key to Encrypt or decrypt a Data. It is the coding of an information and changing it from the original form (plaintext) to a mixture of letters and numbers and also requires the private-key before decription (that is uncoding.
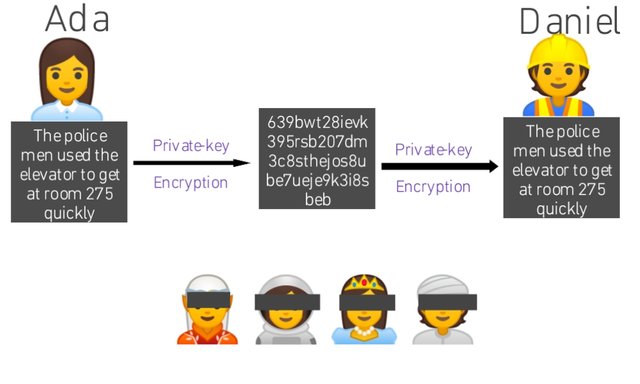

1 (c). What Is Public-key Encryption
This is the use of two separate keys to Encrypt and decrypt an information so as to hide it from others. Here, Ada uses a Public-key encrypt an information in the presence of her friends and sends it to Daniel, and Daniel uses a Private-key to decrypt it.
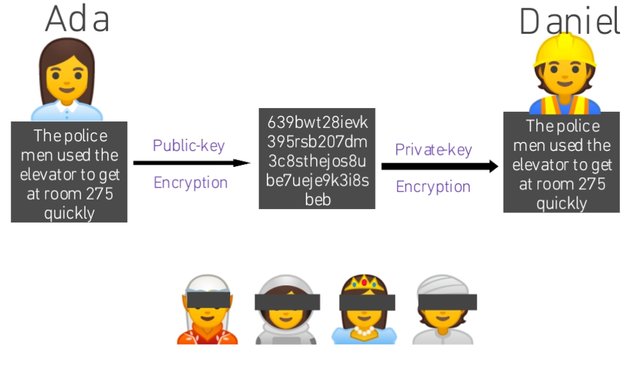

1 (d). Differences Between Private-key Encryption And Public-key Encryption
The differences Between Private-key Encryption And Public-key Encryption are:
In private-key encryption, the same private-key is used to encrypt and decrypt an information.
In public-key encryption, the public-key is used to encrypt by the sender but the reciever uses the private-key to decrypt as seen in the illustrations above.

2 (a). What happens to outsiders if a message is encrypted? Give a brief example?
When a message is encrypted the outsiders or people that are not associated in the conversation does not see the message that is sent. Only the sender and the receiver sees the message.
2 (b). Screenshot of Different inputs And Observations
The following are some examples of my inputs and the observations I found out
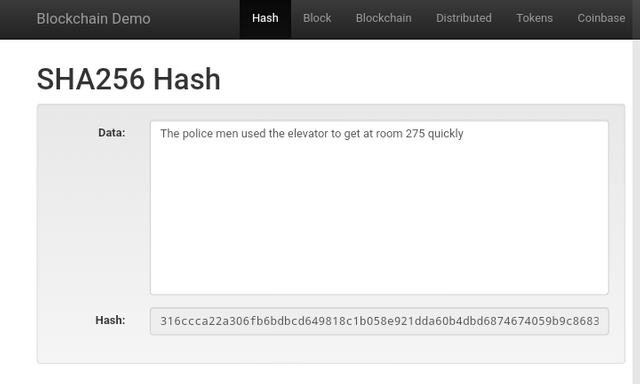
For the screenshot on the left, it has an input "the Police men used the elevator to get at room 275 quickly" and it has the encryption e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 which is different from the second input on the right.
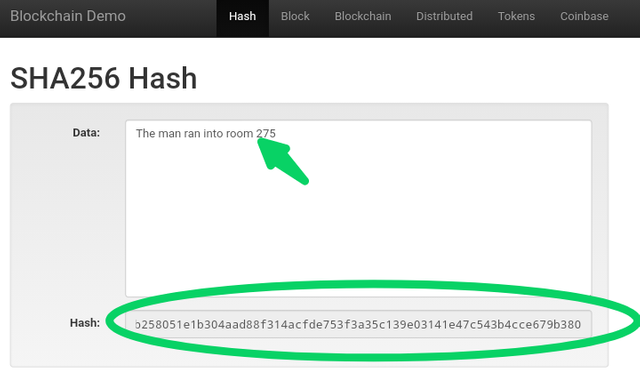
The screenshot on the right has an input "the man ran into room 275 whith an Encryption b258051e1b304aad88f314acfde753f3a35c139e03141e47c543b4cce679b380, which is also different from the first one.
According to our prof @fredquantum, there are 64 alphanumerics and the encryption can never be the same. The sample above also proves it to be true.

Conclusion
The class is very interesting class. Learning from the Grassroot is very exciting. I'll like @bossj23, @chiomzy810 and @fortwis09 to also be a part of this lesson for there are so much benefits.
Cc;
@steemkidss
@ngoenyi
@fredquantum
@ijelady
@mariajruizb
@madilyn02
📝
Introductory Post
thank you😁
.jpeg)
Thank you for the invite but am no longer among the kids..Am a member dear.
Oh my! You have graduated. Congratulations 💥 dear
New year brings new updates. Thanks for being here for me. Many hugs💗
Thanks dear
You are welcome. I'll miss you o among our kids here
Tell: 09130529277
Keep up the learning it will help you now and in the future
Yes mom
I'll our earnest efforts
Amazing participation
Thank you dear
Hi dear, I knew it that you will make a beautiful writeup as you always do. You have explained these things in detail and shown your understanding of the lecture. Kudos to you.
Thank you for being part of steemkids Community and for delegating your steempower. Will you consider increasing your delegation..? That will be very nice and that will mean that the amount of delegation reward will be increased. Think about it...🤔...🤗.
I wish you success and many blessings...🌹
Thank you very much
I have considered it. Planning towards it. It's about time
Thanks for the kind support
Hola cariño, felicidades por esta publicación, muchas gracias por participar en las actividades de la comunidad y contribuir con ella. Te deseo mucho éxito, me encanta ver que aprendes mucho con estos temas de cryptografía.
Thank you very much ma
You are putting smiles on my face