Grassroot Crypto Education (Vol.4) - Cryptography: Private-Key Encryption, Public-Key Encryption by @bossj23 || 10% payout to steemkidss || club5050
Hello Steemians. I still owe my special thanks to @fredquantum for enlightening verified kids in this special community. You have made it possible for me especially to be interested in crypto Education. Knowledge of crypto is basic and intrinsic that's why you made this provision possible in this social media platform. Last week I learnt a lot about market capitalization and the rank of some crypto assets in the capital market. I also learnt how to calculate market capitalization of a Crypto asset using current price and circulating supply. This week's lecture is more about cryptography and I'll try my best to explain it in ways that even a layman will understand. The keywords in this topic are;
- Cryptography
- Encryption
- Key
- Decryption
- Hash Functions
- Hashing etc.
I'll define Cryptography, list and explain the types of cryptography, the differences between the two important types of cryptography and hash functions..
Define Cryptography
Cryptography is simply the process of using secret keys or codes to secure communication techniques which prevents an unintender from viewing or deciphering messages passed from the intended sender to the intended recipient. These cryptographic functions are used to protect sensitive and confidential information from an unintender. Cryptography involves the process of converting an ordinary message or information to an unintelligible or gibberish text known as Cipher text. It involves encrypting and decrypting data between persons in the presence of outsiders or unintenders who are blinded to whatsoever messages the sender sends to the receiver because they don't have keys necessary to decrypt the message. In summary, cryptography is the use of coding, algorithm or techniques to protect confidential information and techniques in communication from unauthorized access. The sender encrypts a confidential/sensitive information he wants only the recipient to decipher or see with the secret key that can only be unlocked and deciphered by the recipient. Cryptography is aimed at authenticity, confidentiality, and integrity in the crypto ecosystem.
Example: @bossj23 and @vonne can communicate in the presence of @madilyn02 and @fortwis09 without the latter having details to information or the conversation. They are blinded to what @bossj23 and @vonne are discussing. Cryptography is synonymous withencryption which I'll spotlight in the next question.
N/b: Cipher text are series of random numbers and letters that humans find unintelligible or uneasy to decipher.
Extensively Explain Private-Key encryption, Public key encryption and Hash functions.
Basically, these are types of cryptography but one may ask why encryption is used instead of cryptography. It's easy. Cryptography is synonymous with encryption and generally **Encryption is the process of changing an ordinary message into cipher text or code language that cannot be understood by humans if not decrypted using public or private key. Other terms Worthy of spotlight in this are;
- Decryption
- Key and
- Private key
Decryption is the process of decoding the encoded message or changing the message which appears as a cipher text back to its original form in human readable words.
Key is usually strings of letters or numbers stored in a file which when processed through crytographing can decode and encode encrypted data.
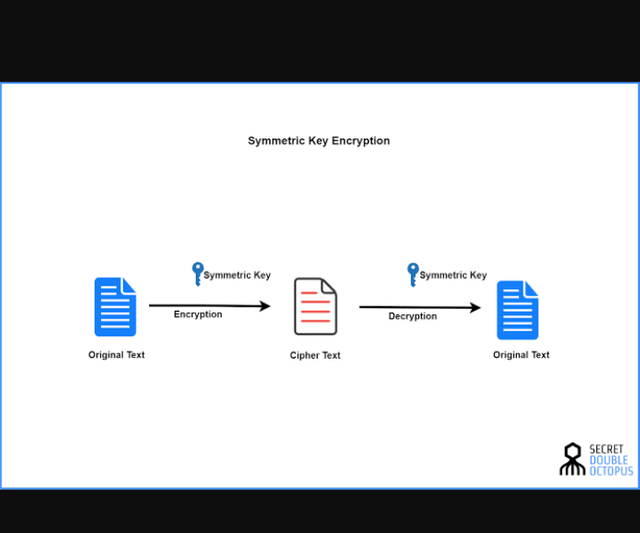
Private key Encryption
is also known as symmetric encryption. This is a type of cryptography where a secret, single private key is used to encrypt and decrypt data. It is usually a long generated sequence of bits that cannot be guessed easily or deciphered. It is only one key that is used in encryption and decryption. The sender sends a message in code or algorithm using the private key to a recipient and also shares this key to the recipient so that he will be able to decrypt, decipher and read the messages in its ordinary form. The sender sends this message in a way that won't be leaked or viewed by outsiders.
Illustrate: @bossj23 sends an encrypted message "The transactions were carried out successfully" to @vonne using a private key. And this message is encrypted as "Taha1tara1nasa1cata34nasawa2ra2ca1rara321da45tasa5caca2sasafa4lalaya" so that @madilyn and @fortwis09 who are outsiders won't be able to decipher the coded message because they don't have the private key.
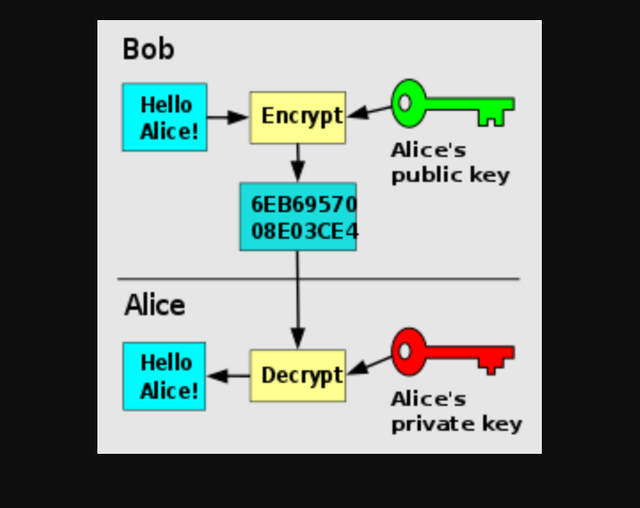
Public Key Encryption
Public key encryption also known as assymetric encryption is a type of cryptography where two keys are used; the public and private key. The same keys are not used in this kind of encryption. The sender of the message in this case uses a public key to encrypt the message and send it to the receiver who uses not the public key but a private key to decrypt the encoded message.
Hash functions
Hashing: is a process of converting a given key into another value.
Hash function is a function made up of mathematical algorithms. They are widely employed in cryptocurrency and it is a one-way algorithm s that cannot be reversed if data is stored about a cryptocurrency transaction. I. e the original data cannot be recovered through any form of alteration. It maps inputs of variable lengths to return outputs of fixed length which cannot be altered. It is used to validate the integrity of some inputs.
Simply Differentiate between Private key Encryption and public key encryption.
Private-key encryption uses only a single key for encryption and decryption while public key uses different keys for encryption and decryption. Private-key encryption uses only one private key while public-key encryption uses public key to encrypt and private key by receivers to decrypt.
A private key is much more faster than a public key.
Private keys and known only to the sender receiver and anyone else while public key can be viewed by everyone.
What would happen to outsiders if a message is encrypted. Give a brief example .
if messages are encrypted into an intelligible or gibberish text, outsider cannot decipher or view it. they are blinded as to having access to it since they cannot see it as a cipher text which is very hard to understand.
Example: Two persons i.e the sender and receiver are involved in communication and the sender encrypts a message using a private key and sends the private key to the receiver to be able to decipher the message. To outsiders, it is a cipher text they are seeing and not the main message because it has been encrypted with a key.
Visit https://andersbrownworth.com/blockchain/hash
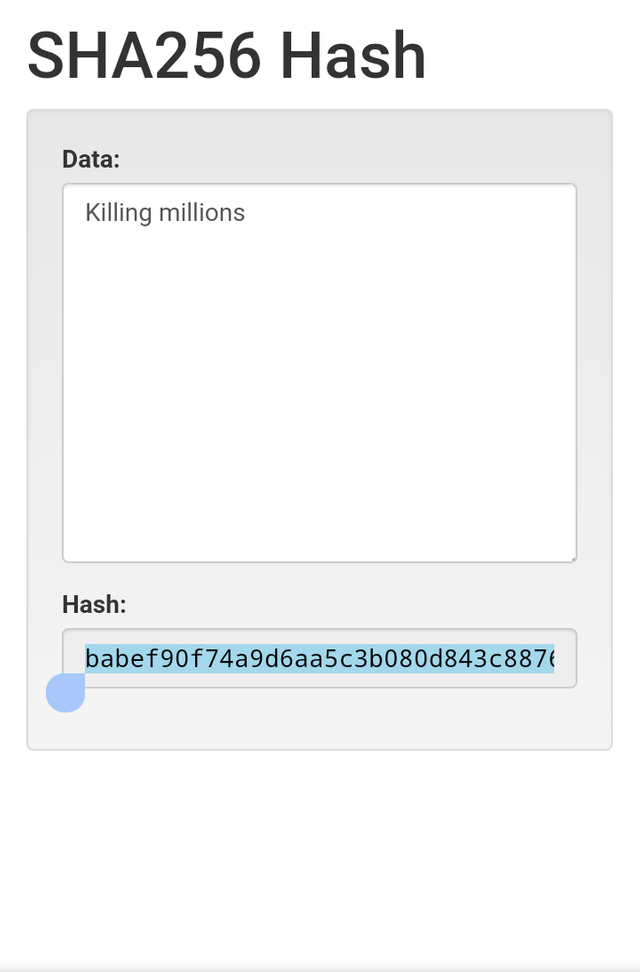
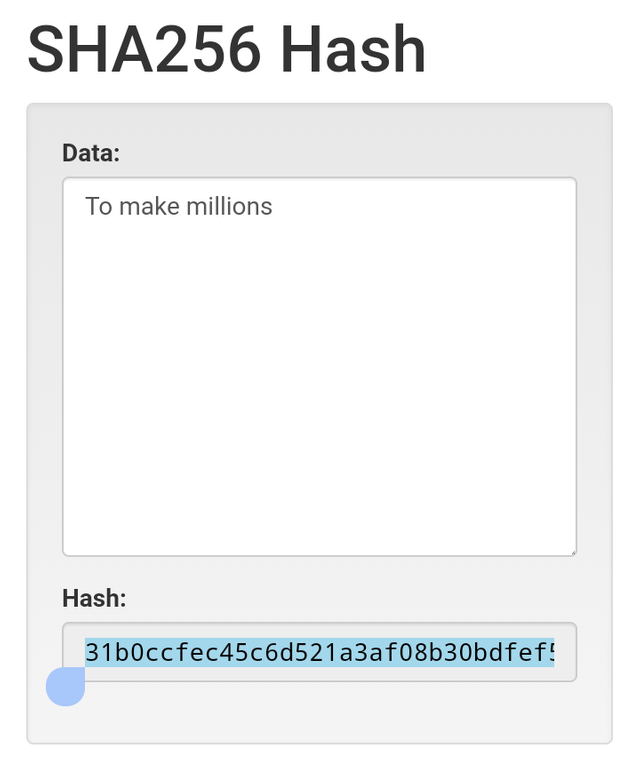
Enter two different inputs and show your observation.[Screenshot required]
When I typed the words "Killing Millions" the hash generated was babef90f74a9d6aa5c3b080d843c88766b93b1f5e97f3ade2d8f47550d32542b
But when I type to make millions, this hash is generated as 31b0ccfec45c6d521a3af08b30bdfef5694d78291f6de035da2cd9e6e392a08f
This is to show that different inputs create different hash thereby making each of them unique from the other.
Conclusion
I have really learnt a lot from cryptography. Cryptography is a way of securing confidential from unauthorised access in the crypto ecosystem especially during communication or transactions.


Wow,our celeb for the month is really doing well.
Hola @jefej23 felicidades has logrado captar mi atención con este contenido tan extraordinario y útil para todos. Se aprende mucho al leer publicaciones como éstas. Estas haciendo un hermoso trabajo, sigue así. Bendiciones para ti.