Cybersecurity: Definition, Types and How to identify Cyberthreats (Club5050)
Introduction
One of the major challenges that accompanied information and communication technology is Internet fraud and hack. It has been a major and long lasting problem to a lot of users. While some completely shied away from anything concerning Internet because of fear of hacked or defrauded, majority of individuals didn't because of its diverse opportunity it has to offer.
What is CYBERSECURITY?
.jpeg)
Its is the safeguarding of computer devices, put in place by tech companies, from relevant information being stolen,disclosed or destroyed. It is also put in place to avoid interruption when using these computer devices. Cybersecurity is so important to the modern technological world as it can help wage against war and political damages.
Since the conception of the use Internet, threats to them was birthed alongside and it has been constantly changing throughout the years. These threats comes in different forms that if one is not careful about it, he or she would be a victim of being scammed or hacked, whatever the intention of the fraudsters or scammers might be.
Cybersecurity can also be known and called Computer Security or Information Technology Security, a protection system put in place to safeguard out devices or internet usage and information. Before explaining the types of cyber security, let's define the terms Cyber and Security
Cyber is a word that characterizes the era of computers, information technology, and virtual reality. Security on the other hand is defined as the position of being free from danger or threats. Therefore cybersecurity is the state of being free from computer threats and damages.
.jpeg)
Types of Cybersecurity
There are different ways by which one can safeguard his or her system from attacks some of which are;.
- Critical infrastructure security.
- Application security
- Network security.
- Cloud security.
- Internet of Things (IoT) security
How to identify Cyberthreats
There are various ways one can identify Cyberthreats that tend to destroy our devices once installed. These threats includes the following incase one comes across any of these threats.
- Malware
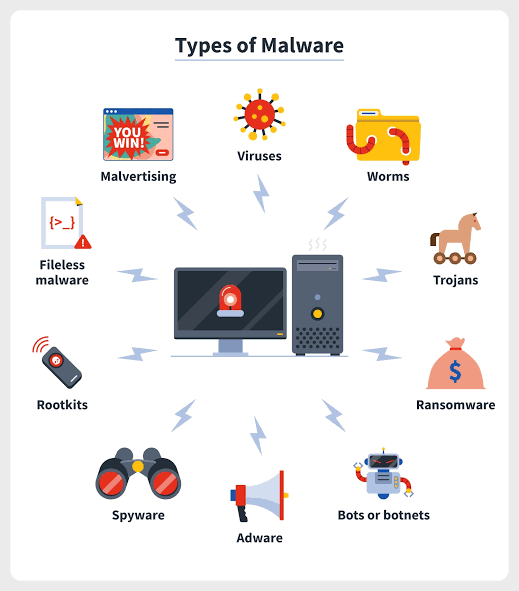
This is dubious software that comes in form of spyware, ransomware, viruses and worms. This threat is activated once the account holder or user clicks on the link or attachment. It usually comes like a bait to the user who might not know what he or she is clicking on. Example is when one is asked to click on a link to redirect to to claim a prize that the user doesn't know of. It may be out of curiosity but at times these individuals tend to click on these links and thereby installing a dangerous software into the system which can be copying and storing your data every step of the way. It can also render the device useless and prevent it from accessing other secure websites which easily detects the influence of the malware on devices.
- Phishing
Since our emails are gradually becoming a public address, some scammers go as far as sending emails to various addresses with the intention of installing a software that will gradually installs the data in the email. The trick behind this is to get the user to supply relevant information to them without knowing in the form of replying a relevant body or organisation. Fake addresses of these institutions or organisations are created a imitated in such a way that if one doesn't look closely and happens to be in desperate need of getting a response from the said institution, he or she might reply blindly, thereby causing an attack on its device.
- Denial of Service
DoS as abbreviated is also a category of cyber threat that crowds an computer internet connection so that it doesn't function or loads appropriately again. A typical example of this is called Botnets. This can be used to launch an attack on the computer system and infect it in such a way that it's almost impossible to trace the origin of attack.
- Password Attacks
Haven almost been a victim of this, the strategy of the hackers is to trick you into sending them important information such as OTP - One TIme Password. They won't make it known that they're trying to change your password and the tech company might want to send a confirmation code which these cyber attackers would ask for. They would trick you into believing that they're the ones trying to stop the hacker from hacking, however, they are the ones trying to get in and once they succeed, the account or email or device is completely hijacked and controlled by th
Conclusion
Cybersecurity is an important aspect of our technology usage if we want to guarantee safety of our devices and search history. It's important to know and be alert at all times to detect any form of cyber threat. The best method of avoiding this is to totally ignore the link, email or text. As long as you don't click it for any reason whatsoever, the safety of your device is assured.
Thank you for reading.
Cyber thefts keep coming up with new ideas of how to trick people to disclose their secret cyber security information to them. We just have to be up-to-minute with every new update about cyber security.
Thanks for sharing
Your post has been supported by @jimah1k using @steemcurator07 account.
Thank you for making a post in the #Science/ #Computing/ #Technology category. We appreciate the work you have put into this post.
We have analyzed your post and come up with the following conclusion:
Follow @steemitblog for all the latest update and Keep creating qualityful contents on Steemit!