Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u (Let's Open The CryptoGraphy)
Hello All...
This week has entered the 8th week of season 3, I am very happy to be joining professor @stream4u class. This is a very interesting class, ok I will try to do the homework given this week
.jpg) Background from canva
Background from canva

1.) Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Blockchain cryptography is a system contained in a blockchain network that plays an important role in securing users' data. as for the cryptographic work system, hiding the inputted information data by changing the data to make a unique algorithm so that the inputted information cannot be understood, aims to prevent information from being hacked. After the information has been inputted, it cannot be changed again. only the parties involved in the processing of the data know the meaning of the inputted information.
Cryptography can be said to be one solution to overcoming one's privacy in sending data to the intended party, because if someone sends very confidential personal data via email then the data is very easy to hack like the incident experienced by Warren Buffett which can be solved by the government which is a very private company personal data. so the cryptography contained in the blockchain is an excellent innovation in maintaining the privacy of one's data.
so the process of sending the data involves encrypting and decrypting messages so someone who sends data makes information encrypted so that the information becomes a unique mathematical algorithm that cannot be read back in meaning. and if the data has reached the recipient, the information in the form of a unique algorithm becomes the original information that is inputted initially, which is usually called decryption, so that receiving and sending can know the meaning of the information sent.
Here are some names that are the platforms of the blockchain:
- Ethereum Blockchain
- Tezos Blockchain
- EOS Blockchain
- TRON Blockchain
- Stellar Blockchain
- Steem Blockchain

2.) Explain the Public Key CryptoGraphy.
A public key is a key that is shared on a blockchain network and is in the form of a unique algorithm that cannot be understood by anyone. Public keys are needed in verifying transactions carried out by senders and recipients, so when they want to make transactions in the blockchain network, the recipient and sender can provide their public key. This is very useful for the parties involved (sender and recipient) in conducting transactions.
The public key is also closely related to the private key, because the sender's public key is needed to verify the transaction, so after being received by the recipient and signed using the private key, the sender's public key is needed to complete the transaction process.

3.) Explain the Private Key CryptoGraphy.
The Private Key is a key that is very confidential by the owner because it is closely related to the owner's wallet, this key is obtained when creating the wallet for the first time, the private key is needed for every transaction that occurs in the owner's wallet, if someone can access the private key it will be very dangerous to funds stored in the owner's wallet, therefore the private key is strictly confidential.
so when the sender wants to make a transaction to the recipient, the most important thing for the transaction process to run is to use the sender's private key, and so the recipient can access transactions received from the sender, the recipient also needs his own private key to access the transaction.

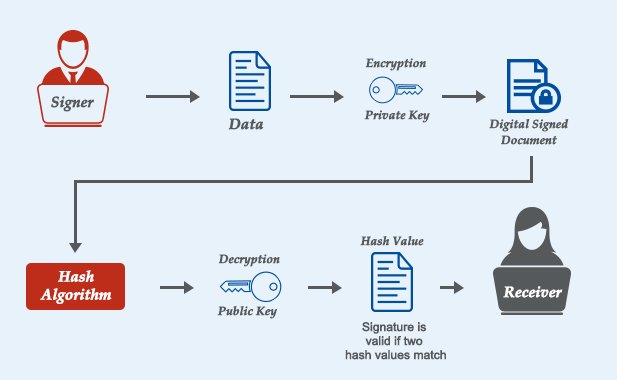
4.) Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
In processing every transaction, of course, a signature is needed to certify a transaction such as document administration, digital signatures also have almost the same function as the signatures that we usually sign on hardcopy. Digital signatures are needed in every transaction in cryptography. so digital signatures are needed to verify the authenticity of messages from every transaction made.
With a digital signature, the security in transactions that occur in cryptography will be increasingly maintained, because, with a digital signature, parties other than those involved in the transaction process cannot know the transaction. After all, in the transaction process that occurs the sender requires private keys to make a signature. digital and broadcast to the network and processed by miners, then when the transaction has entered the network the recipient needs the sender's public key to be able to accept the transaction.
Digital Signature Process
The digital signature process involves 2 functions involving the sender and receiver, namely:
Sign
This process involves the sender's private key to be able to generate a digital signature before the transaction enters the network.Verification
The verification process involves digital signatures and public keys to be verified by miners against the authenticity of the transaction so that they can overcome hacking transactions against the network.
So it can be said that digital signatures are interconnected with private keys and public keys, in the process of encrypting data on the network it requires a private key and when you want to decrypt data on the network it takes a public key.

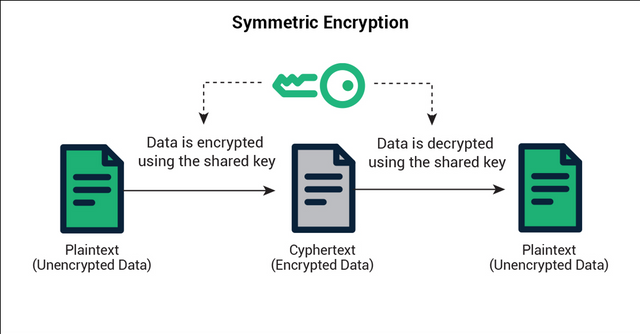
5.) Explain what is Symmetric and Asymmetric cryptography?
Symmetric Cryptography
Symmetric cryptography is a type that uses only one secret key in the encryption and description process. so in the process of sending data in a transaction, the sender uses a secret key to encrypt the data into a mathematical algorithm that can only be read by a computer, and when the recipient wants to decrypt the data into readable text with the consent of the sender, the recipient also uses the same secret key. it only involves one key, unlike asymmetric cryptography.
Although the symmetric cryptography method is an older encryption method compared to asymmetric cryptography which involves two keys (public and private) symmetric cryptography also has several advantages such as being easy to use and faster because the data size is not too large, this can help senders and recipients in streamlining time in transaction processing.
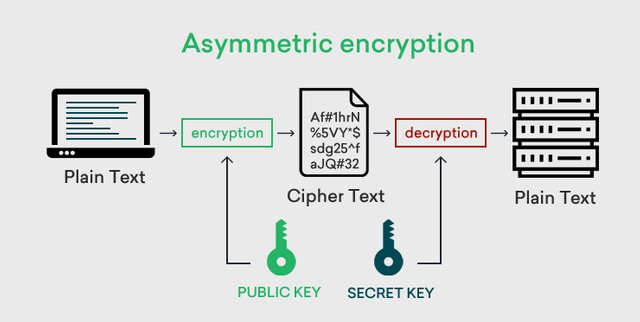
Asymmetric Cryptography
Asymmetric cryptography is a type that is used in the process of encryption and description of data using a pair of keys, namely the public key and the private key. a system like this can be said to have a very good level of security without fear of being known to parties who are not involved in it because the pair of keys is related to the decryption and encryption of data in the network. so the sender uses the receiver's public key to encrypt the data in the transaction process, then the receiver uses his private key to decrypt the data.
Asymmetric cryptography has advantages in the field of security in the level of confidentiality of the data. the parties involved also do not need to share their private keys. because that can be shared only with the public key. so that a system like this really helps the sender and recipient in carrying out every transaction without fear of being known by other parties. and the private key will also be safe because it does not need to be shared with other parties or parties involved. However, this system does not have a speed level like symmetric cryptography because the data is large and certainly requires a lot of computer resources.

6.) How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Crypto wallet is a platform used by crypto holders to store crypto assets owned and used to transact with other users. crypto wallets have almost the same function as conventional banks which we usually store and make transactions, conventional banks make transactions using the recipient's account number while crypto wallets using the recipient's wallet address.
Blockchain wallet cryptography has a very good working mechanism in the field of security because it uses several functions such as private keys and public keys. The private key is needed to prove ownership of the wallet owner's assets, while the public key is used to verify the transactions that occurred.
Crypto wallets that are on the blockchain can be said to be very safe in storing the owner's digital assets. As for the working system in processing crypto wallet transactions, the sender must use their private key to sign the transaction before sending their crypto assets. so the sender needs the recipient's wallet address to send the asset, once the transaction takes place the sender's public key is needed to verify the transaction so that the transaction will be secure and cannot be hacked by malicious users.
- Cold Wallet
A cold wallet is a wallet for storing the crypto assets of its users without being connected to the internet network. This type of wallet is considered very safe from hacking because this wallet does not use the internet network, so online hacking is not possible. So, this type of wallet is very suitable for users to store large amounts of assets.
- Hot Wallet
Hot wallets are the opposite of cold wallets, namely wallets that are used to store and transact using the internet network. This type of wallet is very good for storing digital assets and can make it easier to make transactions online, because it is done online this wallet has several advantages such as being easy to use and cheap in terms of costs. however, these wallets are not suitable for storing large amounts of assets because they are vulnerable to online hacking.

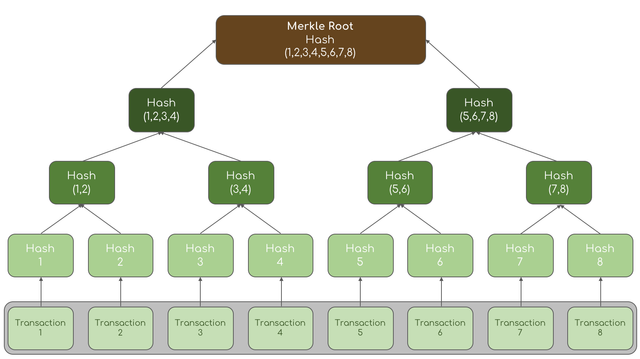
7.) What are the Merkle trees and What its importance in blockchain?
Merkle Tree is a hash structure that has a structure from leaf to root hash. It is called a Merkle tree because its structure is shaped like a tree. As for the Merkle tree structure, from the bottom, it is called the leaf, and the one in the middle is called the branch and the one at the top is the root. while the Merkle tree contains data in the form of hashes for each different transaction that is connected in each structure. so the system works by pairing each hash block with another block so that it reaches its peak, namely the root hash.
In a Merkle tree, every transaction is a hash whose word character length remains the same and can only be understood by a computer, so in a Merkle tree, all the information that has been inputted will become a root hash which is interconnected with the hash that is in the structure below it so that all information will become one hash, Of course, all of this can make the block validation process easier.
so we can see from the structure of the image above that the lowest one is called dau, there is hash 1 to hash 8, funds when paired between leaves, will form branches like hash 1 + Hash 2, producing hash (1,2) which is the branch until so on, if the number of leaves is odd then it can duplicate the last leaf that does not have a partner such as duplicating Hash 7 + hash 7. after forming a branch, the combined structure until it reaches the top will produce a root hash that is a hash (1,2,3,4,5,6,7,8,).
Importance of Merkle Tree in Blockchain
Merkle trees are interconnected with each other to increase security in changing transaction data in one block.
Highly structured Merkle tree can save time in the block validation process on the blockchain network
The Merkle tree can also reduce the amount of data storage
The Merkle tree can also reduce the amount of energy used because it has been structured to reach the root hash to track transactions more effectively and efficiently.

8.) Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical.
first, let's visit Blockchain Demo. And let's visit the features in it one by one.
Key
as we all know, cryptography has a private key and a public key that are interconnected, while the key is in the form of a unique algorithm that cannot be read, because it is in the form of letters and numbers at random. let's see an example like the image below.
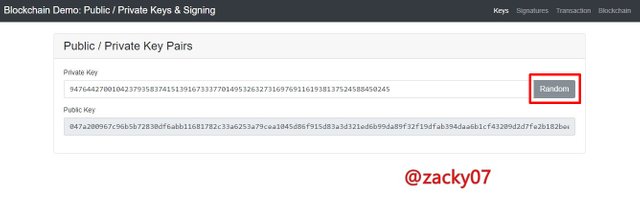
Private Key :
9476442700104237935837415139167333770149532632731697691161938137524588450245
Public Key :
047a200967c96b5b72830df6abb11681782c33a6253a79cea1045d86f915d83a3d321ed6b99da89f32f19dfab394daa6b1cf43209d2d7fe2b182beecd69d529e05
we can see from the picture above that the private key has a unique public key, and both keys are in incomprehensible language.
let's try changing the private key:
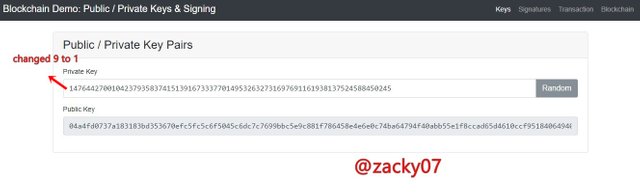
Private Key :
1476442700104237935837415139167333770149532632731697691161938137524588450245
Public Key :
04a4fd0737a183183bd353670efc5fc5c6f5045c6dc7c7699bbc5e9c881f786458e4e6e0c74ba64794f40abb55e1f8ccad65d4610ccf9518406494027a02228435
From the picture above I try to change the initial number of the private key from 9 to 1 so that it produces a different public key. From the above experiment, different privacy keys can't produce the same public key.
Let's try to generate the private key manually.
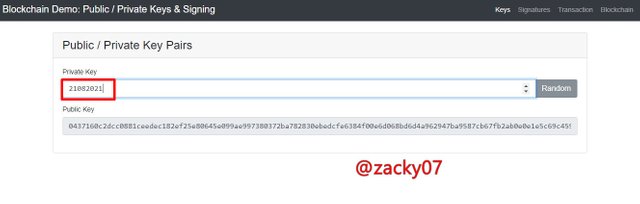
Private Key :
21082021
Public Key :
0437160c2dcc0881ceedec182ef25e80645e099ae997380372ba782830ebedcfe6384f00e6d068bd6d4a962947ba9587cb67fb2ab0e0e1e5c69c459f5f71c4374e
We can see from the picture above by trying to change the private key manually and generate a different public key as well. from some of the experiments above we can know that the private key has a public key that is related and not the same despite the small differences given.
Signature
The signature is proof of authenticity in the transaction that occurs, in the transaction process the private key is needed to sign the data, and the public key is needed for the process of validating the authenticity of the private key. let's see an example image below.
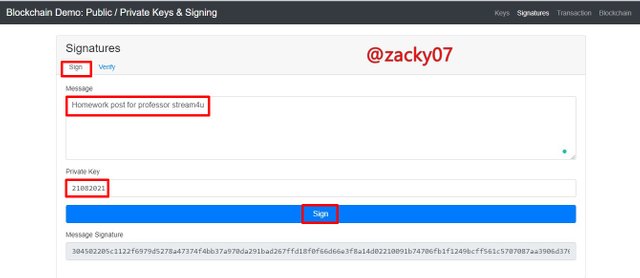
Message
Homework post for professor stream4u
Private Key
21082021
Message Signature
304502205c1122f6979d5278a47374f4bb37a970da291bad267ffd18f0f66d66e3f8a14d02210091b74706fb1f1249bcff561c5707087aa3906d3761c573416d6b61386d0ed6ff
Now let's try to verify the signature by using a valid public key with a private key as shown below.
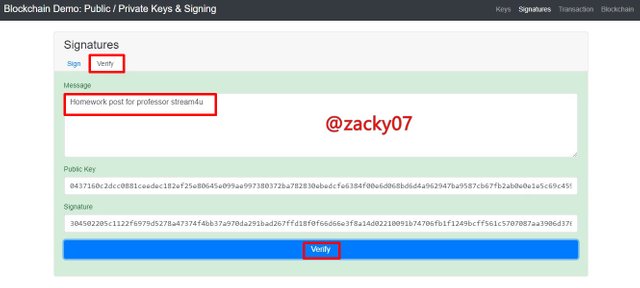
From the picture above, after pressing the "verify" button, the green background color will appear, this indicates a valid transaction. This is all because the public and private keys are interconnected.
Transaction
The transaction process occurs involving the public key and private key as well as a signature. This process occurs when a transaction is signed with the private key and verified using the public key. let's look at the example below
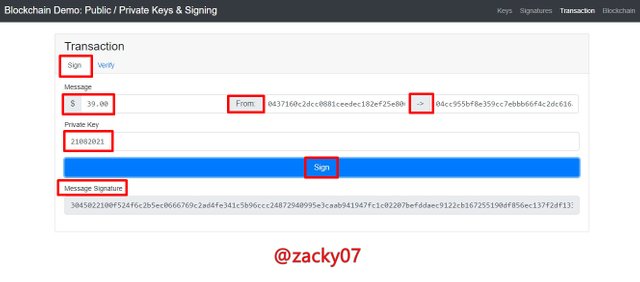
From the data above I tried to enter a $36 message and other transaction details as follows
From
0437160c2dcc0881ceedec182ef25e80645e099ae997380372ba782830ebedcfe6384f00e6d068bd6d4a962947ba9587cb67fb2ab0e0e1e5c69c459f5f71c4374e
To
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Private Keys
21082021
after being signed using the private key it generates a Message Signature.
Message Signature
3045022100f524f6c2b5ec0666769c2ad4fe341c5b96ccc24872940995e3caab941947fc1c02207befddaec9122cb16725190df856ec137f2df1333d058a0d5720d9dfce6acf7
After that let's try to verify the message, as shown below.
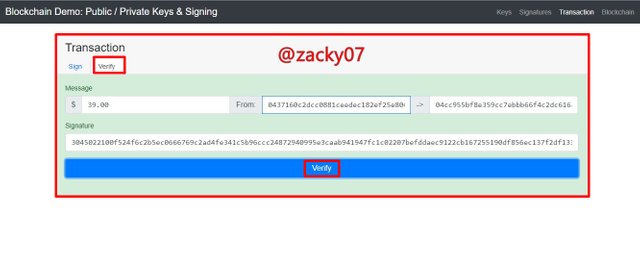
from the picture above, we can see that after the public key has been given and pressing the verify background button it turns green, this indicates the transaction that has occurred is valid
Blockchain
Blockchain is a place to store every transaction in a block that is interconnected with other blocks, if a block changes it will affect other blocks, let's see the picture below.
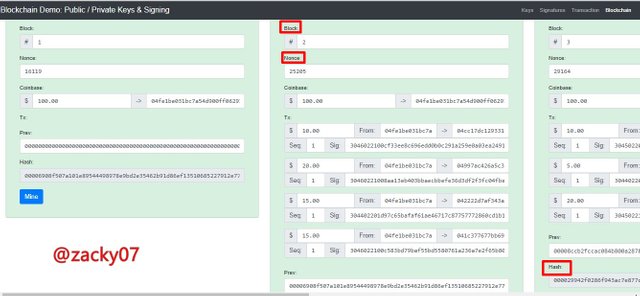
We can see from the picture above that the block is still green which indicates the block is still valid. The picture above also provides information about blocks, nonces, hashes, and others, and each block is interconnected with other blocks.
let's see if the block changes slightly, I tried to change the number of transactions in block 2 from $10 to $15 and we can see the block has changed its background color as shown below.
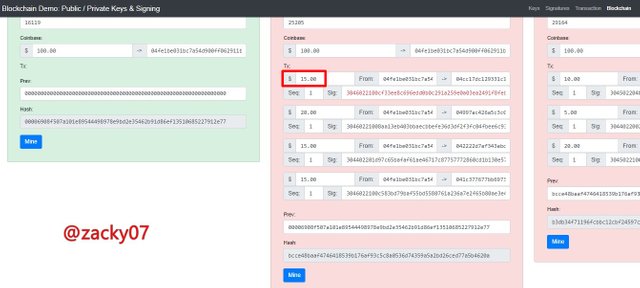
from the picture above, we can see that the block has changed color to red, this indicates that the block has received an error and is invalid. This also coincides with the next block if one block has a problem it will cause the next block to have problems too because each block is interconnected. so to make the block valid we need to fix the block by pressing "mine" on each block and will get a different nonce. like the picture below.
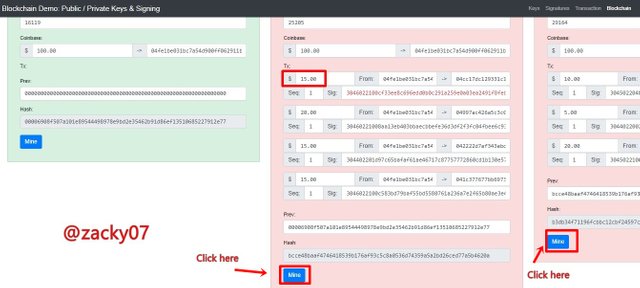
from the picture above we can see the initial nonce from block 2 is 25205 and block 3 is 29164 and after I press "mine" the nonce changes as shown below
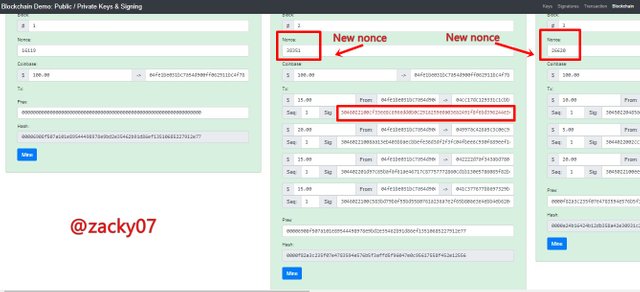
from the image above the nonce in block 2 has changed from 25205 to 38351 and the nonce in block 3 has changed from 29164 to 26620 and the background has turned green which indicates the block is valid, but the signature on block 2 has not been verified, this indicates a mismatch between the private key and the public key so that the signature cannot be verified.

9.) Conclusion
Cryptography on the blockchain network is very helpful to provide a level of security on the blockchain network. This technology can be said to be very good at anticipating parties who are not involved in the transaction process so that it can anticipate the hacking of users' personal data. This technology can be said to be able to change the information that has been inputted into a unique algorithm that is only understood by computers.
In the process of data encryption and decryption, a private key and a public key are needed so that parties who do not have the key in the transaction process cannot find out and hack the transactions that occur, so users on the blockchain network will feel safe in processing transactions.