Steemit Crypto Academy Season 5 Beginners' Course Homework for Task 4

Write the definition of blockchain. And how our data on Blockchain is protected from hackers. ? And write details about Data, Hash and Previous Hash tag and explain through screenshot.

Write the definition of blockchain

In a long time, people offered faith in transactions, intermediaries, or financial companies; it was impossible to know, and in general impossible to know, who the other party interested in the transaction was, thus we were forced to employ third-party services.
The world financial system collapsed in 2008, and a person known only by the pseudonym Satoshi Nakamoto proposed a protocol for creating a new direct electronic payment system between the parties, using a cryptocurrency called Bitcoin and a new technology called Blockchain, eliminating the need for a third party.
Because all cryptocurrencies require transactions to be transmitted through an information network and stored in the blockchain, the first Blockchain was created in tandem with the first cryptocurrency, Bitcoin. All cryptocurrencies require the use of a Blockchain to function.
A Blockchain can be defined as a network of distributed information, which functions as an accounting ledger that stores chronological records. It is said to be distributed because several copies of the updated information are replicated, and they are found in different nodes, or computers. Blockchain is a compound word that means "blockchain" in Spanish.

A Blockchain's Components

| Components | Description |
|---|---|
| Node: | This can be a home computer, a laptop, or a supercomputer, and it represents a computer on the network. |
| Standard Protocol: | It is a piece of computer software that facilitates communication across all nodes in a network; the most well-known example is SMPT, which is also used to send and receive e-mail. |
| A Point-to-Point Network (P2P): | P2P stands for peer-to-peer, and it refers to a collection of computers connected to the same network. |
| Decentralized system: | Because it lacks a centralised entity, blockchain is controlled by all of the components that make it up, all of whom are on the same level of hierarchy. |

There are various kinds of Blockchain

| Types | Description |
|---|---|
| Public Blockchain: | This sort of blockchain is also known as a distributed ledger technology (DLT). Anyone can join without permission, and there is no need for permission or authorization; it is open. |
| Private Blockchain: | This sort of blockchain is also known as a distributed ledger technology (DLT). I'm familiar with permission since it's the polar opposite of a public Blockchain; it requires permission and must be permitted to join; it's a closed Blockchain. |
| Hybrid Blockchain: | Parts of the two blockchains discussed above are combined in this type of blockchain. |

How is our data on the Blockchain protected from hackers?

A Blockchain is a distributed ledger that is entirely open to everybody, there is no way to prevent someone from attempting to change a block of the blockchain.
Because the block chain is copied to all of the nodes that make up the network, the fact that a blockchain is a distributed network lends it some security. This means that each of the network's nodes, which can number in the thousands or even millions, receives an exact copy of the previous transaction or block. To accept a new transaction or block, first the information contained in the block chain in each node is verified, until all nodes approve or disapprove it through a system consensus. If it is approved, then this transaction or block becomes part of the block chain and can no longer be modified.
When a block is added to the block chain, a code is added that identifies it indisputably; this code is known as Hash, which is a form of fingerprint; when a block is added to the block chain, a code is added that identifies it unequivocally. It is formed using a mathematical procedure, which requires multiple arguments in order to generate the hash, including transaction data, the previous block's hash, and the answer to an unknown, which is obtained by a process known as mining or proof of work.
The mechanism of a Blockchain is called proof of work, which reinterprets the creation of new blocks; in the case of Bitcoin, it takes 10 minutes to calculate the required proof of work and add a new block to the chain; this mechanism makes it very difficult for them to change the blocks, because if they change one, they must calculate the proof of work for all subsequent blocks.

Write details about Data, Hash and Previous Hash tag and explain via screenshot

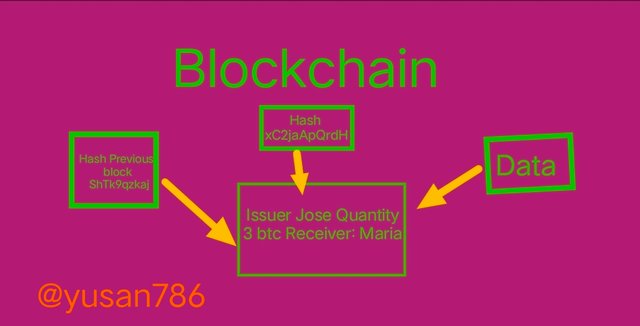
Every block contains the following information: data, block hash, and previous block hash.
Data: is a block contains varies according on the type of Blockchain; for example, the Bitcoin block chain stores transaction details including the issuer, receiver, and coin amount.
Hash: is similar to a fingerprint in that it uniquely identifies a block and all of its content. Once a block is produced, its hash is computed, and if something inside the block is changed, the hash changes as well. Using the hash, we can determine if a block has been edited.
The previous block's hash: The hash is what keeps a block chain safe; if you edit a block, the hash changes, rendering the next block and all subsequent blocks invalid.

Conclusions

The Blockchain is a distributed network,so each node has an exact copy of the block chain. It also uses the Cryptography technique, which generates a hash to identify a block and also works with the hash of the previous block to create the chain, and finally the proof of work, which is an unknown that must be deciphered and has the function of delaying tampering. With all of these security measures in place, it's unlikely, if not impossible, for someone to successfully tamper with a block.

Thanks you Prof . @shemul21
Mention
Prof . @shemul21