Crypto Academy / Season 3 / Week 4- Homework Post for Professor @pelon53 - Topic: Root Hash And Merkle Tree.
Information is power, they say. The right information falling into the wrong hands is actually a big risk. Therefore, sensitive informations should be transmitted in a secured manner such that only the sender and the receiver can be able to understand the message sent.
One of the most secured ways of transferring information from one node (sender) to another node (receiver) within a network is through the use of Hash. When input texts are hashed, they generate a set of codes containing both alphabets and numbers. This alphanumeric character codes are called the Hash of that input, and they are always unique to the input text that generated it.
Due to the uniqueness of the hash to the input text that is attached to it, when the right hash algorithm is applied to the hash, the reciever (who shares a unique key with the sender that decodes the hash) can be able to extract the information attached to the hash by the sender.
Although the hashing of informations makes the blockchain more secured, the information can become so bulky, and if miners must know the details of each of them before they verify a transaction, it's going to take ages. This can be avoided if all the hashes in a block can be classified into one hash (the root hash), therefore, verifying the root hash is the same as every hash in the block. When hashes are arranged in this manner, it is refered to as Merkel Tree.
In today's lecture, professor @pelon53 while teaching on the topic "Root Hash And Merkle Tree" has explained to us how the hash of several transactions can be represented in one hash called the root hash. Below is my response to the assignment he gave after the class.
Question 1: EXPLAIN IN DETAIL THE HASH RATE.
Mining of cryptocurrencies in the crypto eosystem requires solving of hash functions algorthims. These calculations are carried out by high-powered super computers computers. High-powered computers are not all the same, some of them solve complex algorithm faster than others. This means that they of different power rating. These power rating of these computers used in mined is obtained by measuring their hash rate.
Hash rate (or hash power) is defined as the speed at which the high power computer solve hashes at a specificed period. Hash rate is a measure of the efficiency and the productivity of the machine used for mining.
Hash rate of a machine is determined by calculating the number of hashes the machine can calculate within a second.
Hash rate = number of hashes solved / time
The S.I unit for hash rate is hour/second. Sometimes prefixes such as Mega (M), Giga (G), Tera (T), Peta (P), and Exa (E) are included in the S.I unit.
To better illustrate what hash rate means, I will be giving an example. Let's assume that a high powered computer is able to calculate 500,000 hashes within 0.5 second. Using the hash formula above,
Hash rate = 500000 / 0.5 second = 1,000,000h/s = 1Mh/s
Apart from the computer used in mining the cryptocurrency, hash rate is also affected by the cryptocurrency being mined. Different currencies don't have the same mining rate. When the same high powered computer is used to mine them, at the same time, you will realize that one will have a higher hash rate than the other.
Note:- Although using computers with high hash rates enables the miner to verify transactions faster, it actually increases the cost of mining. The reason for this is that high hash rate processing computers consumes much electricity, and the higher the systems hash rate, the more energy it consumes.
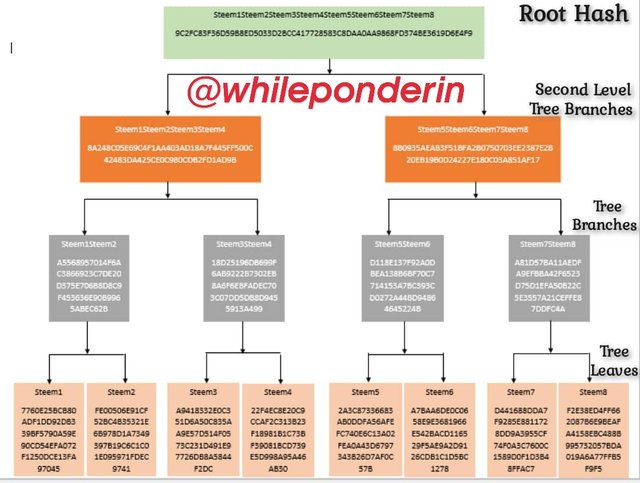
Question 2a: MAKE THE FOLLOWING MERKLE TREE: TRANSACTION (TREE LEAVES): Steem1; Steem2; Steem3; STEEM4; Steem5; Steem6; Steem7; Steem8.
To create the Merkle tree, first, I have to generate the hash for all the leaves (Steem 1 to 8). To do so, I will use SHA-256
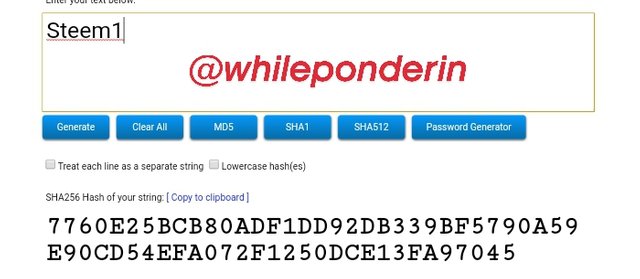
Steem1:
Hash: 7760E25BCB80ADF1DD92DB339BF5790A59E90CD54EFA072F1250DCE13FA97045
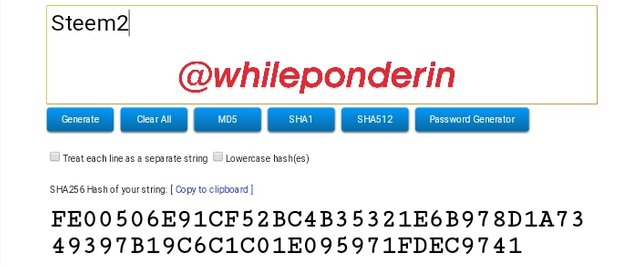
Steem2:
Hash:
FE00506E91CF52BC4B35321E6B978D1A7349397B19C6C1C01E095971FDEC9741
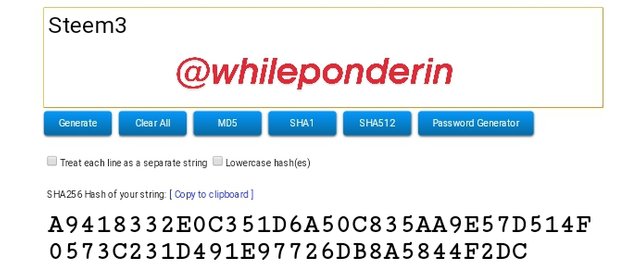
Steem3:
Hash:
A9418332E0C351D6A50C835AA9E57D514F0573C231D491E97726DB8A5844F2DC
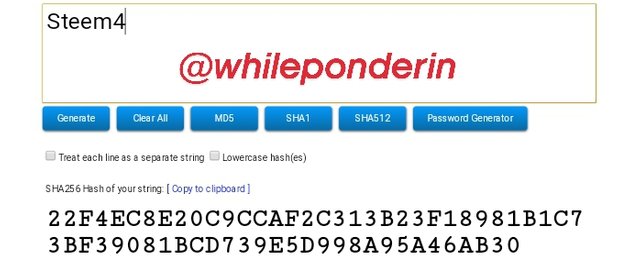
Steem4:
Hash:
22F4EC8E20C9CCAF2C313B23F18981B1C73BF39081BCD739E5D998A95A46AB30
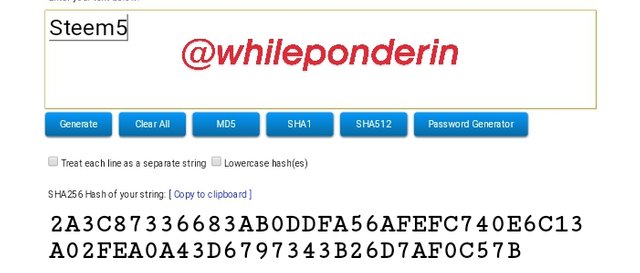
Steem5:
Hash:
2A3C87336683AB0DDFA56AFEFC740E6C13A02FEA0A43D6797343B26D7AF0C57B
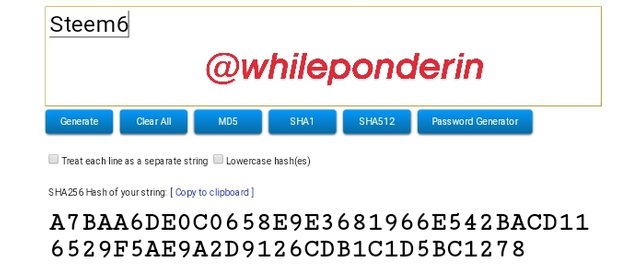
Steem6:
Hash:
A7BAA6DE0C0658E9E3681966E542BACD116529F5AE9A2D9126CDB1C1D5BC1278
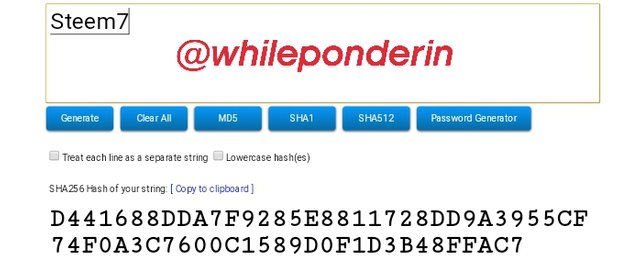
Steem7:
Hash:
D441688DDA7F9285E8811728DD9A3955CF74F0A3C7600C1589D0F1D3B48FFAC7
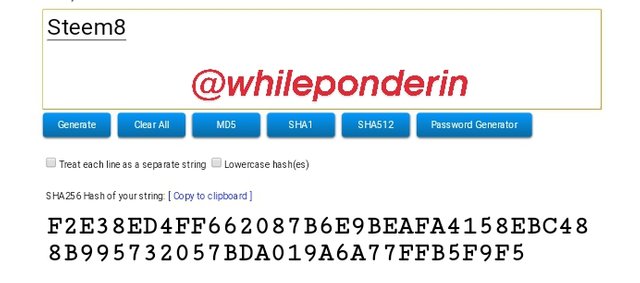
Steem8:
Hash:
F2E38ED4FF662087B6E9BEAFA4158EBC488B995732057BDA019A6A77FFB5F9F5
After creating the hashes for the leaves, the next step is to generate the branches. Below are the branches and their hash.
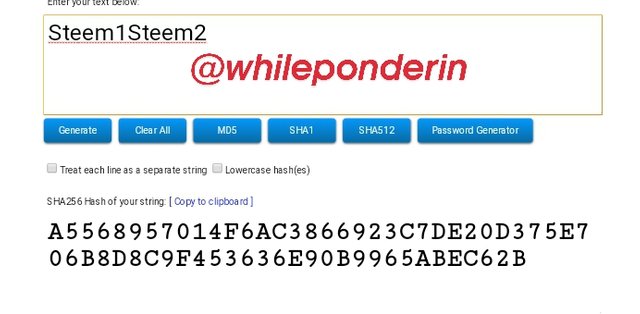
Steem1Steem2:
Hash:
A5568957014F6AC3866923C7DE20D375E706B8D8C9F453636E90B9965ABEC62B
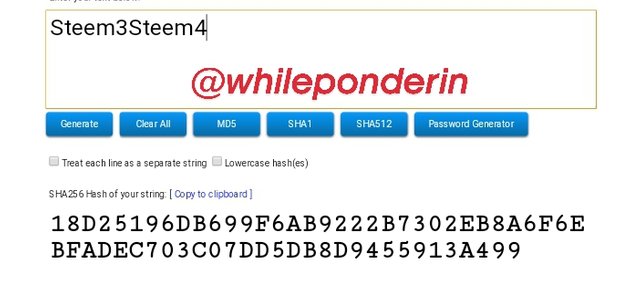
Steem3Steem4:
Hash:
18D25196DB699F6AB9222B7302EB8A6F6EBFADEC703C07DD5DB8D9455913A499
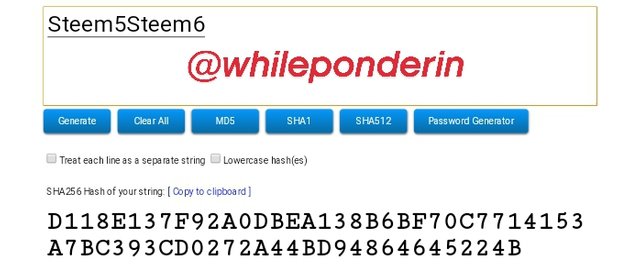
Steem5Steem6:
Hash:
D118E137F92A0DBEA138B6BF70C7714153A7BC393CD0272A44BD94864645224B
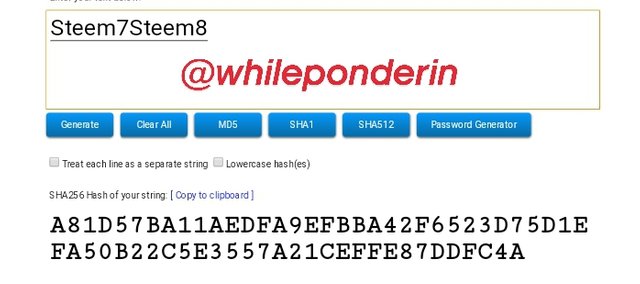
Steem7Steem8:
Hash:
A81D57BA11AEDFA9EFBBA42F6523D75D1EFA50B22C5E3557A21CEFFE87DDFC4A
Since the branches are still up to four, we go a step further by using them to generate second level branches, so as to reduces the branches to two. They are:
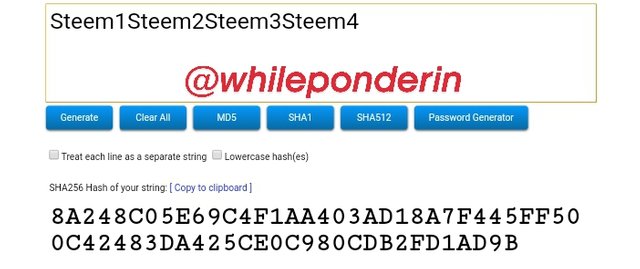
Steem1Steem2Steem3Steem4:
Hash:
8A248C05E69C4F1AA403AD18A7F445FF500C42483DA425CE0C980CDB2FD1AD9B
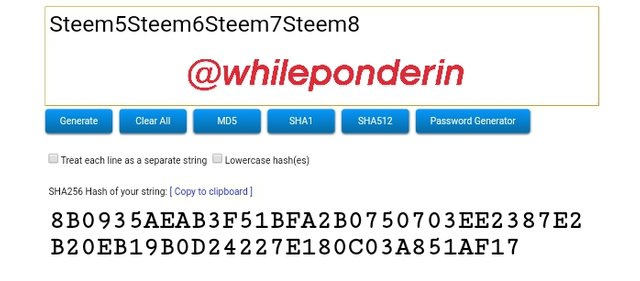
Steem5Steem6Steem7Steem8:
Hash:
8B0935AEAB3F51BFA2B0750703EE2387E2B20EB19B0D24227E180C03A851AF17
After creating the second level branches, the next step is to generate the root hash.
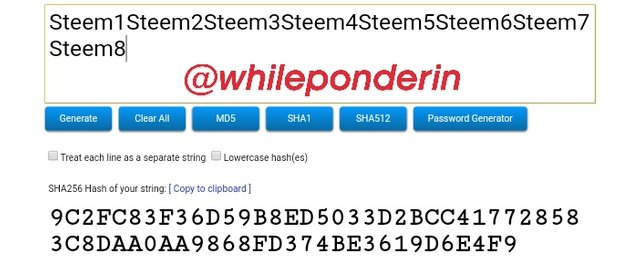
Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8:
Hash:
9C2FC83F36D59B8ED5033D2BCC417728583C8DAA0AA9868FD374BE3619D6E4F9
Finally create the Merkle tree for all the inputs and their respective hashes.
Question 2b: TELL THE STEPS TO FOLLOW TO VERIFY IF Steem6 IS INCLUDED IN THE MERKLE TREE.
In other to verify Steem6, the miner is required to have know the Hash of Steem5,
Hash of Steem7Steem8 and the Hash of Steem1Steem2Steem3Steem4. Based on the already known data, these are the steps I took in verify if Steem6 is included in the merkle tree.
Step 1:
First, using SHA-256, I generated the hash for Steem6.
Step 2:
Since I already know what the hash of Steem5 is, I will use it, along with hash of Steem6 I generated in Step 1 to calculate the hash for Steem5Steem6.
Step 3:
Since I already know what the hash of Steem7Steem8 is, I will use I will use it, along with hash of Steem5Steem6 I generated in Step 2 to calculate the hash of Steem5Steem6Steem7Steem8.
Step 4:
Since I already know what the hash of Steem1Steem2Steem3Steem4 is, I will use I will use it, along with hash of Steem5Steem6Steem7Steem8 I generated in Step 3 to calculate the hash of Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8
This hash of Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8 is referred to as the Merkle root hash.
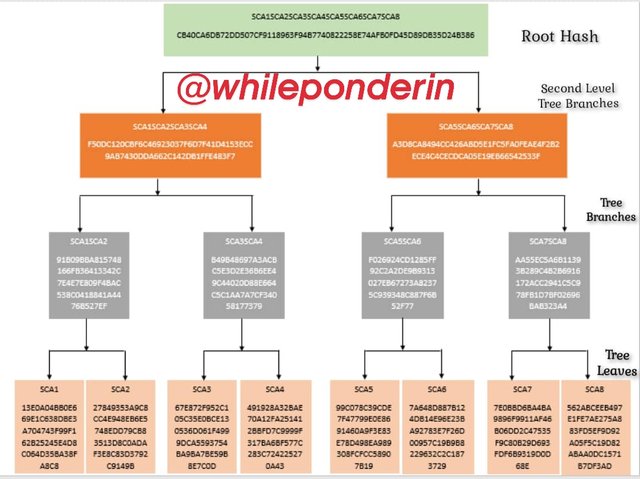
Question 3: USING THE SHA-256; YOU MUST PLACE EACH COMPLETE HASH IN THE MERKLE TREE. TRANSACTION (TREE LEAVES): SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8. Explain each step
To create the Merkle tree, first, I have to generate the hash for all the leaves (SCA1 to 8). To do so, I will use this SHA-256
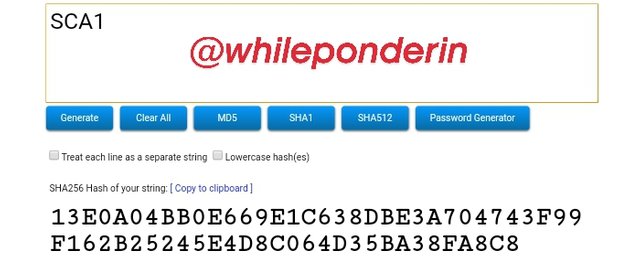
SCA1:
Hash:
13E0A04BB0E669E1C638DBE3A704743F99F162B25245E4D8C064D35BA38FA8C8
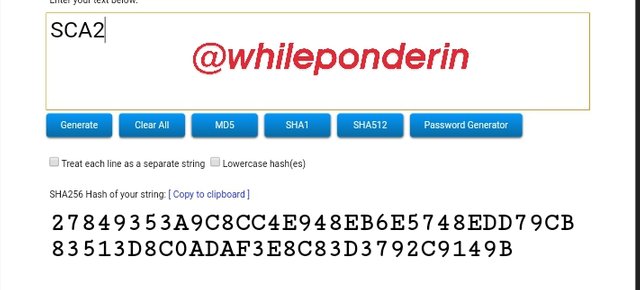
SCA2:
Hash:
27849353A9C8CC4E948EB6E5748EDD79CB83513D8C0ADAF3E8C83D3792C9149B
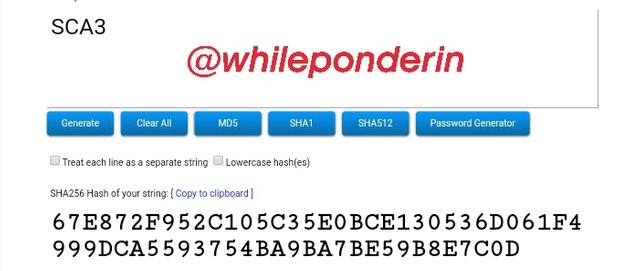
SCA3:
Hash:
67E872F952C105C35E0BCE130536D061F4999DCA5593754BA9BA7BE59B8E7C0D
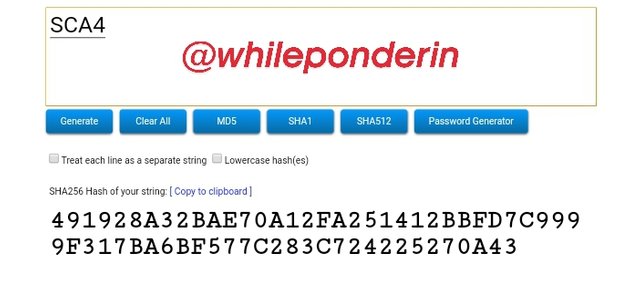
SCA4:
Hash:
491928A32BAE70A12FA251412BBFD7C9999F317BA6BF577C283C724225270A43
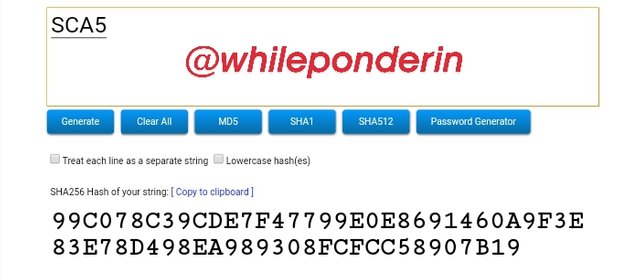
SCA5:
Hash:
99C078C39CDE7F47799E0E8691460A9F3E83E78D498EA989308FCFCC58907B19
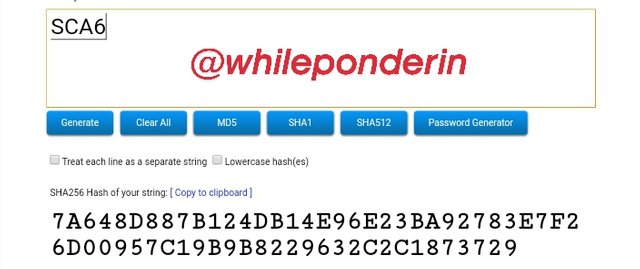
SCA6:
Hash:
7A648D887B124DB14E96E23BA92783E7F26D00957C19B9B8229632C2C1873729
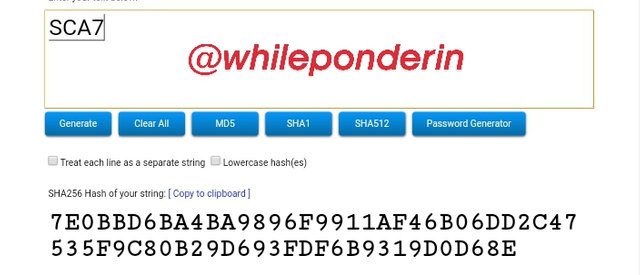
SCA7:
Hash:
7E0BBD6BA4BA9896F9911AF46B06DD2C47535F9C80B29D693FDF6B9319D0D68E
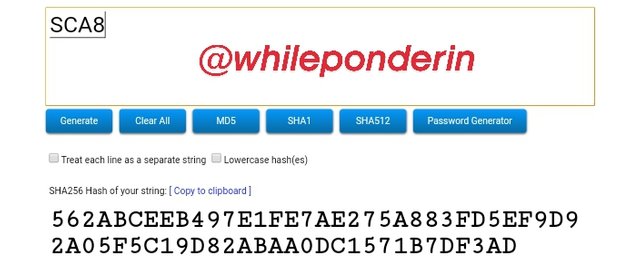
SCA8:
Hash:
562ABCEEB497E1FE7AE275A883FD5EF9D92A05F5C19D82ABAA0DC1571B7DF3AD
After creating the hashes for the leaves, the next step is to generate the branches. Below are the branches and their hash.
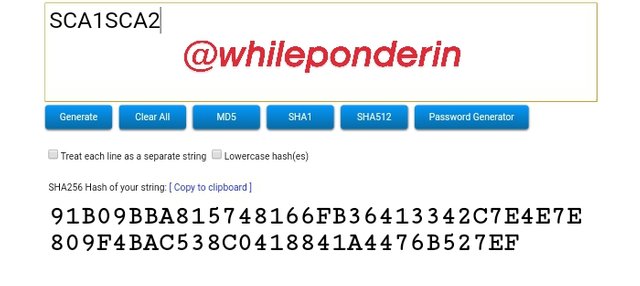
SCA1SCA2:
Hash:
91B09BBA815748166FB36413342C7E4E7E809F4BAC538C0418841A4476B527EF
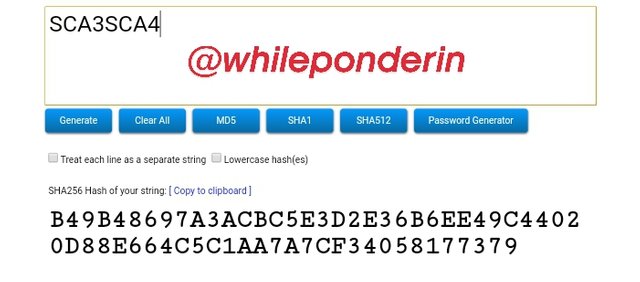
SCA3SCA4:
Hash:
B49B48697A3ACBC5E3D2E36B6EE49C44020D88E664C5C1AA7A7CF34058177379
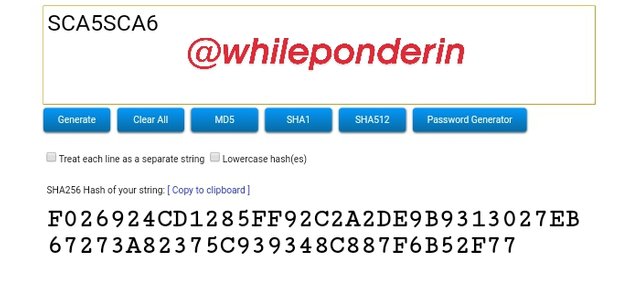
SCA5SCA6:
Hash:
F026924CD1285FF92C2A2DE9B9313027EB67273A82375C939348C887F6B52F77
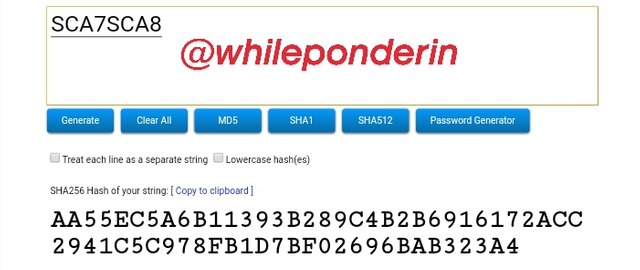
SCA7SCA8:
Hash:
AA55EC5A6B11393B289C4B2B6916172ACC2941C5C978FB1D7BF02696BAB323A4
Since the branches are still up to four, we go a step further by using them to generate second level branches, so as to reduces the branches to two. They are:
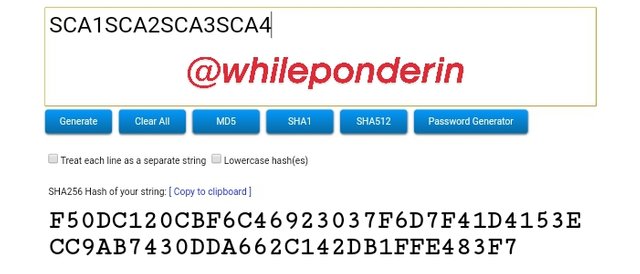
SCA1SCA2SCA3SCA4:
Hash:
F50DC120CBF6C46923037F6D7F41D4153ECC9AB7430DDA662C142DB1FFE483F7
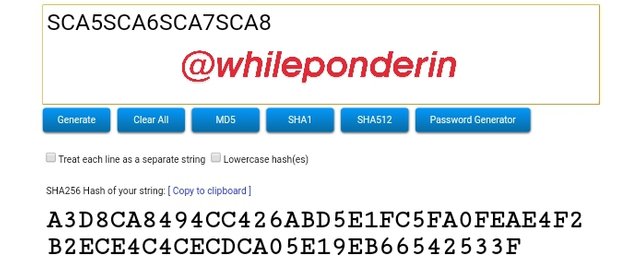
SCA5SCA6SCA7SCA8:
Hash:
A3D8CA8494CC426ABD5E1FC5FA0FEAE4F2B2ECE4C4CECDCA05E19EB66542533F
After creating the second level branches, the next step is to generate the root hash.
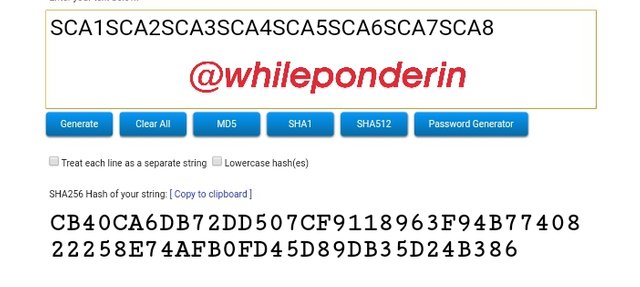
SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA8:
Hash:
CB40CA6DB72DD507CF9118963F94B7740822258E74AFB0FD45D89DB35D24B386
Finally create the Merkle tree for all the inputs and their respective hashes.
Question 4: IF THE NUMBER OF LEAVES ON THE TREE IS ODD, WHAT SHOULD YOU DO? EXPLAIN.
Based on design, the Merkel tree is considered complete if it's leaves and branches are even. This is because it takes two leaves to form a branch, and two branches to form a second-level branch or the root hash.
Assuming that the number of leaves that is required to make a tree is odd, why drawing the tree, it's advisable to take out one of the leaves and keep it aside for the mean time.
After that, using the even number leaves, draw a Merkle Tree and produce the root hash for that even number of leaves.
After forming the root hash for that even number of leaves, we will create another root hash, using the first root Hash from the even numbers as one of the branches, and that odd leaf that we kept aside. Together, these two branches will produce the final and the main root hash for the Merkle Tree
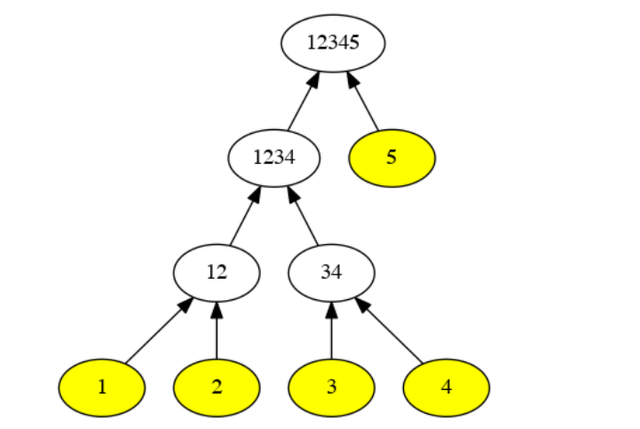
For instance, let's consider a tree that has 5 leaves: 1,2,3,4, and 5. 5 is an odd number. Therefore, to draw the tree, we will keep the 5 leave aside and draw the Merkle Tree for leaves 1,2,3, and 4. When we do, we will obtain a root hash of 1234.
Then, using the root hash 1234 as one branch, and the 5 leaf as the other branch, we will obtain the final root hash of 12345. This is shown in the image below.
One can arguably say that hashing is one of the central pillars of the blockchain technology. Apart from the security it gives to the platform, miner tend to receive reward each time they verify hash values by solving complex math problems.
These problems are too complex for humans, but with they aid of high-powered computers, these algorithms can be calculated in less than a second. Each transaction data has a hash, and in a block there are various transactions. Arranging these data in a Merkle Tree, helps make transaction process faster.
Although it's a fact that the faster the computer is in calculating hashes, the more blocks the Miner gets to mine in a day, it's worth noting that computers with higher hash rate consume so much energy, therefore increasing the cost of mining.
Thank you professor @pelon53 for this amazing lesson.
PS: Check out article How to Reset Battery Light: (Causes & Solution) by steadymechanic


Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Pregunta 1, bien contestada, aunque se puede profundizar un poc más.
Pregunta2, todos los hash coincidieron, muy bien.
Pregunta 3, Los hash coincidieron. La pregunta 3b, está mal. La hoja impar no se rechaza, sino que se duplica. Si es 7, sería 7 y 7. Y se comienza a hacer el Árbol de Merkle.
Recomendaciones:
Investigar más a fondo para dar respuestas acertadas y mejorar la calificación.
Es necesario justificar el texto.
Calificación: 8.3
Thank you Professor @pelon53