Crypto Academy / Season 3 / Week 2 - Homework Post for @pelon53

Hash
A hash is a mathematical function tht encodes data input of any size into alphanumeric characters of a fixed length. Hashed data are of fixed length and cannot be reversed to obtain the original data.
The irreversible and unique nature of the hash function makes it very secure. Because of this high security, hash is used in blockchain technology.

Resistance to Collision
Hash functions are very unique. This means that each hash is entirely different from another. But there are situations when different data would produce the same hash. This is known as collision.
Resistance to collision is an attribute of the hash function that ensures that more than one data do not have the same hash output.
That is; p ≠ q, H(p) ≠ H(q)
where p and q are two distinct inputs, and H is the hash function.
All hash functions are prone to collision. A low possibility of collision implies a greater resistance to collision. One of the reasons why the SHA-256 is most commonly used is because of its great resistance to collision.
Resistance to Collision is also known as Second-Preimage Resistance.

Resistance to Preimage
Resistance to preimage entails the difficulty or impossibility of finding the input for a specific hash output.
- Given an output "q",
- resistance to preimage makes it difficult to find a value, "p",
- for which p = H(q);
- where "H" is the hash functions.
The property of hash functions that make them irreversible gives rise to resistance of preimage.
Resistance to preimage can be compromised using brute-force attack, which involves randomly guessing the passwords or keys by examining the outputs.

Verifying Hash on Etherscan
Etherscan is the blockchain explorer of the Ethereum network.
Block
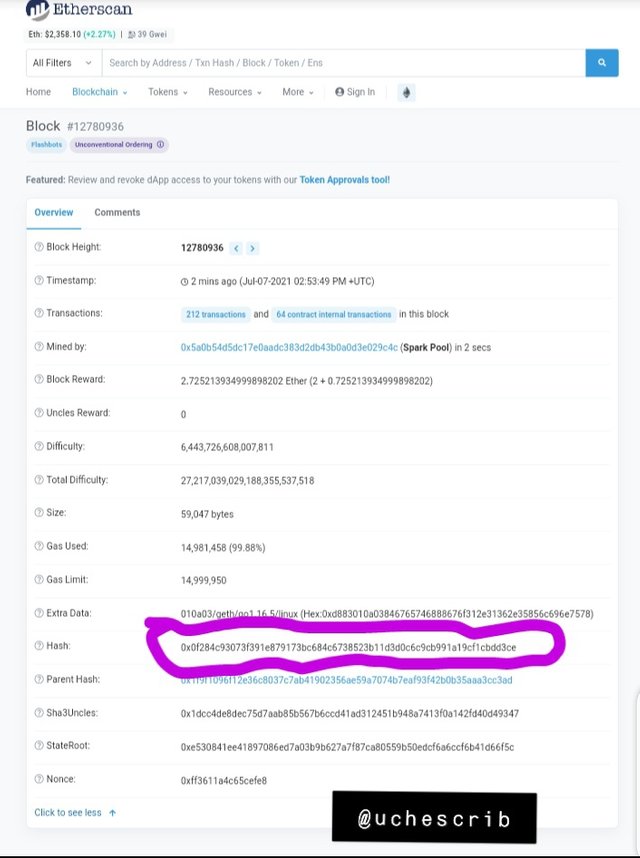
The image above shows some data on the last block as of the time of writing. It's hash is 0x0f284c93073f391e879173bc684c6738523b11d3d0c6c9cb991a19cf1cbdd3ce.
Transaction
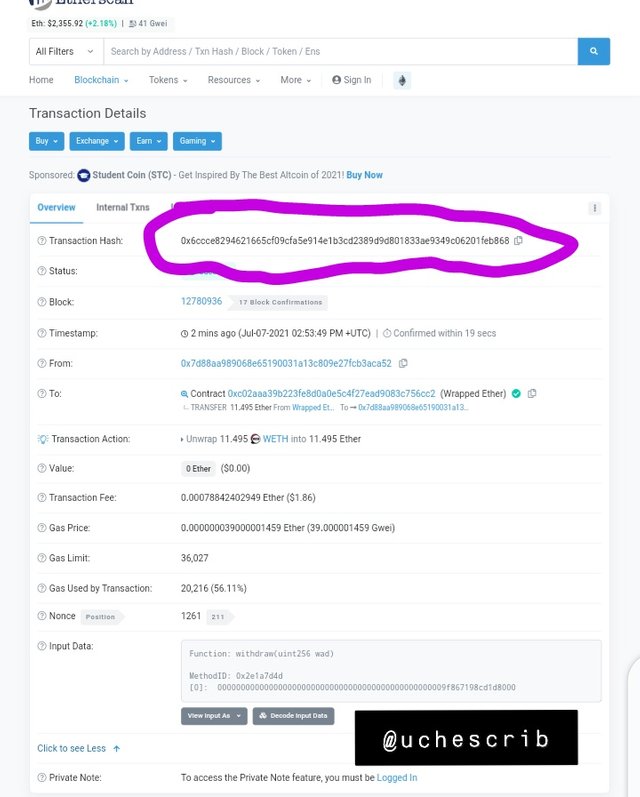
The image above gives details of the last transaction on the Ethereum blockchain as of the time of writing. Its hash value is Ox6ccce8294621665cf09cfa5e914e1b3cd2389d9d801833ae9349c06201.

Verifying Hash on Tronscan
Tronscan is the blockchain explorer of the the Tron network.
Block
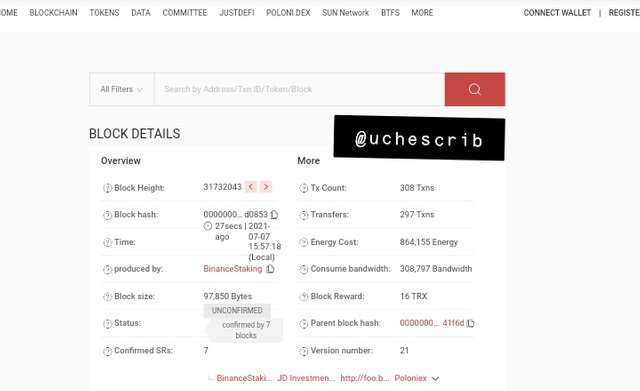
The image above gives data on the last block on the Tron blockchain as of the time of writing. Its hash value is 0000000001e4314b1fef38e814a128f1f5cf3437259d15773370cf70460d0853.
Transaction
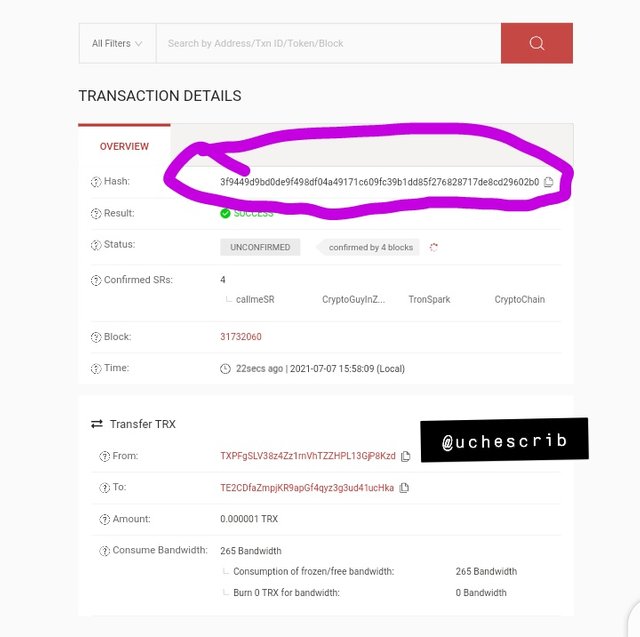
The image above gives data on the last transaction on the Tron blockchain as of the time of writing. It has a hash value of 3f9449d9bd0de9f498df04a49171c609fc39b1dd85f276828717de8cd29602b0.

Generating Hash using SHA-256
This task requires that I use this site here
I inputed the word "CryptoAcademy" and it generated a hash with the value D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9.
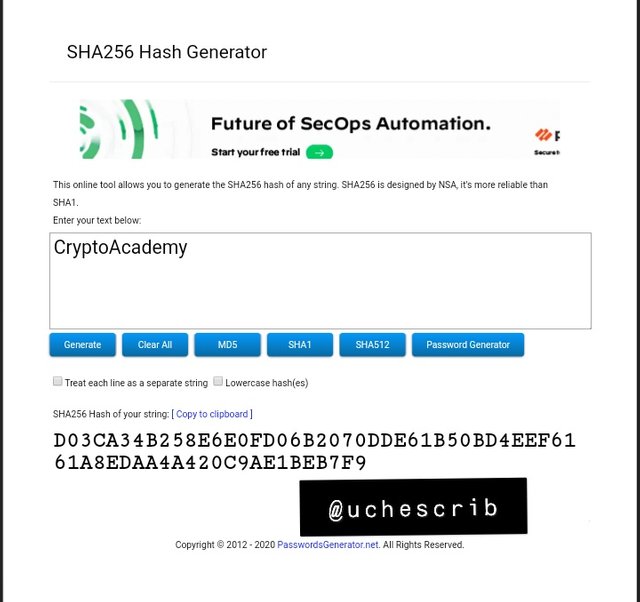
For the second task, I inputed the word "cryptoacademy". It generated a hash with the value 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5.
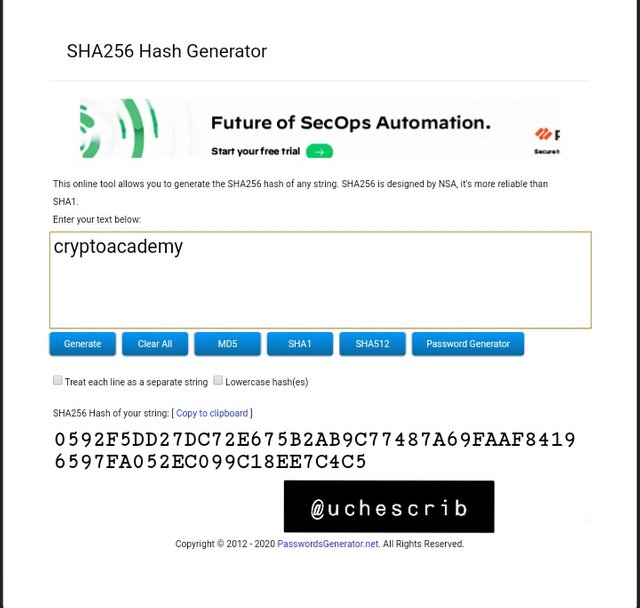
Observation
I observed that the two inputs generated different hashes. Although the words are the same, the characters that make up the words are different. The uppercase and lowercase case letters made a difference in the hash value. This shows that the hash function has a resistance to collision.

Differences Between Hash and Cryptography
By definition, a hash is cryptographic function that encrypts a set of data strings by generating a combination of alphanumeric characters from each character from the data string.
On the other hand, cryptography is the method of encoding data or information, such that only parties involved can gain access to the contents of the encryption with the use of keys.
The differences between these two terms are as follows:
| Hash | Cryptography |
|---|---|
| Each hash algorithm has their individual fixed size and character length irrespective of the data length or size. Example: SHA-512 generates 128 characters while SHA-256 generates 64 characters | Size of encryption depends on the size of information |
| Hashed data cannot be reversed | Encrypted data can be retrieved |
| Keys have no function in hashing | Private and/or public keys are provided for decrypting data |

Conclusion
Hashing is a method of ensuring security of data and information. With this lesson, I have gained knowledge on hashing and it's functions. I have understood the concepts of collision and preimage in hashing.
I'll like to make this note to all my readers. Hashing is a form of cryptography. Cryptography simply involves methods of securing computational data. Hashing is one of these methods.
Special thanks to @pelon53.
El la pregunta 2 no coincide el número de bloque con el hash de la transacción encontrada. Son bloques diferentes y debe ser el mismo bloque. En tronsacan uno es 31732043 y el otro 31732060.
Buen trabajo, sigue adelante.
Recomendaciones:
Debes explicar más como ingresas a la página de tronscan y etherscan. Las respuestas deben ser fáciles de comprender.
Calificación: 8.6