Crypto Academy Season 3 Week 8 - Homework Post for @stream4u CryptoGraphy
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
The blockchain is currently one of the most innovative application models that have the ability to integrate consensus mechanisms, distribute the storage of data, transmit peer-to-peer and other computing technologies. It gives a well-secured platform for decentralized exchange of information which is a core aspect of blockchain technology hence, creating attention to blockchain cryptography.
The security blockchain gives users information and the transaction data adds to its popularity.
Basically, cryptography simply refers to secrets. It ensures that there is either complete or partially complete anonymity in a blockchain.
How it works
Cryptography focuses primarily on ensuring that there is utmost security for users and their transaction data. It safeguards the blockchain against double-spending and centralization. It also helps to secure different transactions occurring in the network and provides applications capable of transferring digital tokens and assets. Cryptography makes use of advanced mathematical codes to store and transmit data values in a very secure way.
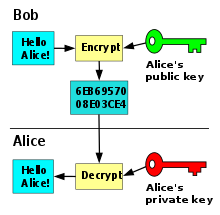
Consequently, it makes sure that only participants who the transaction is intended for can have access to it, read and process the transaction and verify its authenticity. Summarily, cryptography serves as a method for transmitting secure messages between two or more users. The sender uses a specific kind of key and algorithm to encrypt a message before sending it out. On the other hand, the receiver uses decryption to get the original message.
Benefits of cryptography
- Cryptography prevents the double-spending of cryptocurrency
- It ensures the security of both users and their transaction data
- It is used for the verification of cryptocurrency transactions
- There is the anonymity of transactions carried out and participants of the blockchain.
Blockchain Platforms
Stellar: this is distributed blockchain-based ledger used in the transmission of cryptocurrencies and fiat. It has a set of safety properties to ensure the security of transactions and users.
EOS: it is a blockchain platform founded by a private company. Its users do not need to make micropayments to perform transactions on the platform. It has a governance system that validates transactions and it also offers a fully-featured authentication platform to the participants where they are given varying permission levels.
Monera: this is a blockchain that ensures the anonymity of the users by integrating the use of blockchain cryptography.
Explain the Public Key CryptoGraphy.
Public key cryptography is also known as asymmetric cryptography is a kind of cryptographic protocol based on algorithms. It uses a set of keys to decrypt and encrypt data thereby protecting it against access from unauthorized users. This key is used to encrypt a message and then send it to the receiver and is gotten from certification authorities.
A public key is a number that is generated mathematically, giving it more security and nearly impossible to hack. This is what a public key looks like: 82b1egcfc12a11dfc5161abaa8169469fe1601d531
Using the public key can be quite challenging and one of the most common challenges is speed as it is quite slow.
It is also very susceptible to attacks through compromised certification authorities. Cybercriminals can impersonate anyone by simply taking a public key certificate from an authority that is compromised. This now gives them the opportunity to link a public key to another user’s name. in spite of these challenges, it is still beneficial as it provides high data security and remains the most secure protocol.
Public key cryptography demands that each user be responsible for the protection of their respective private keys. Robust authentication is also possible as the sender can combine a message with a private key to make a short digital signature on the intended message. Public key cryptography has three major benefits which are authenticity, non-repudiation, and confidentiality.
Explain the Private Key CryptoGraphy.
A private key also known as symmetric key or secret key is cryptography used with an algorithm to decrypt and encrypt data. It is usually shared with parties or participants authorized to decrypt data or transactions. This key is actually long and mathematically generated that cannot be guessed. This is what it looks like: 04tt350d29213775158a608b51e3eE898e507fe47f2d2e8c674de
Its length and complexity determine how easy an attacker can hack the key. The private key is used by encryption software to generate new private keys which must be stored securely whether offline or online. It can be protected with a password, hashed, or encrypted.
More so, it is also used to decrypt and encrypt data which requires that the key be shared. It can also be used in public-key cryptography for encryption and digital signatures. The benefits of private keys can be said to be speed, fast rate of the transaction, cipher and it is the best for encryption.
Just like in traditional bank transactions where a person’s handwritten signature is required, the same goes in cryptocurrency as a digital signature is required.
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
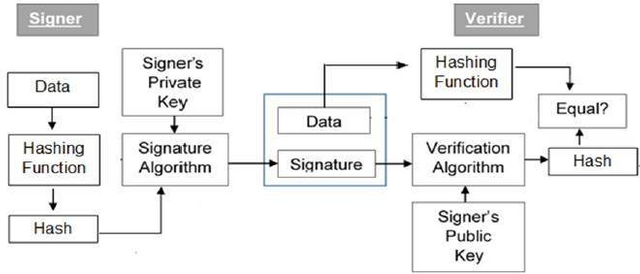
Digital signatures are the public key required for the authentication of a message. It binds a person to the digital data and can be verified by the recipient or a third party. It is a cryptographic value that is calculated from the data and a secret key that only the signer knows. It is worthy to note that the signer cannot repudiate signing the data in the future because the digital signature was created using his private key.
Different pairs of keys are used for encryption/decryption and signing/verifying. The signer feeds data to the hash function, generates hash data which is then fed to the signature algorithm to produce the digital signature on the selected hash.
Some of the importance of digital signatures are as follows:
- It shows the authenticity of a message because the digital signature can only be created by the sender who has a secret private key.
- It increases data integrity especially in case a hacker has access to the data and modifies it, the hash of the modified data will not match with that of the verification algorithm and the recipient can safely deny the message.
- There is non-repudiation and the receiver can always present data and the digital signature as evidence to a third party in case of any dispute.
- Signing a transaction involves providing proof of the digital signature you have created. This is possible because there is a relationship between you and your secret private key.
Explain what is Symmetric and Asymmetric cryptography?
Stymmetric cryptography
Symmetric cryptography is also known as secret-key cryptography. It uses a single shared secret to share encrypted data between parties. You make use of the same key to encrypt and decrypt the data. The sender encrypts the data with a password, which the recipient must know in order to access the data.
Advantages of symmetric cryptography
- It is a very effective cryptosystem and a message can only be decrypted by a device with a hidden key.
- It uses password authentication to confirm a receiver’s existence.
- It prevents breaches in widespread messages
- It is very simple to implement and works at a very fast rate.
Disadvantages of symmetric cryptography
- The secret key must be sent to the receiver before the final message is sent
- It is impossible to have digital signatures that cannot be revoked.
- There is no validation and the message’s origin cannot be assured.
- For messages between different parties, a new shared key must be created and this can be very challenging.
Asymmetric cryptography
Asymmetric cryptography is literally the second form of cryptography. It can be used in a large community where data are exchanged between different partners frequently. Each user has two keys namely; public key and private key. They are both mathematically related and are called the key pair. Whilst the public key can be made available to anyone, the private key is kept secret and is used to perform operations. Take, for instance, data encrypted with a private key will be decrypted with a public key and vice versa. This key is often used to exchange the secret key used for preparing symmetric cryptography to encrypt data.
Advantages of asymmetric key cryptography
- It has improved security because the private keys are never shared.
- Provides digital signatures that can be revoked.
- The usage of digital signatures adds to the authenticity and validation of the message.
Disadvantages of asymmetric cryptography
- It is relatively slow
- Losing a private key is irreversible; all incoming messages cannot be decrypted if the private key is lost.
- It consumes more computer resources
- It requires the authentication of public keys
Differences between symmetric key cryptography and Asymmetric key cryptography
| Symmetric key cryptography | Asymmetric key cryptography |
|---|---|
| For data encryption and decryption, just one key is used | Two different keys are used for encryption and decryption of data which are the public and private keys. |
| The encryption can be completed easily because it is a straightforward procedure | It is a time consuming and relatively complex procedure |
| It is also known as secret-key cryptography or private key cryptography | It is also known as public-key cryptography or conventional cryptography system. |
| It uses a few fewer resources than asymmetric key cipher uses | It uses more resources than symmetric key cryptography |
| It is commonly used where there is a massive transmission of data | It is mainly used where there is a small amount in the transmission of data |
| It is easily compromised because it is the secret key is shared | It is more reliable because the private key is not shared |
| It is an old technique | It is a relatively new technique |
| Examples include RC4, AES, 3DES, etc. | Examples include RSA, Diffie-Hellman, ECC, etc. |
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
A blockchain wallet is a kind of cryptocurrency wallet that allows easy exchange of funds and lets users manage different kinds of cryptocurrency. Transactions are cryptographed, hence makes them secure. A blockchain wallet can be accessed from any web device including mobile devices. Both privacy of users and transactions are maintained and it provides features that make transfer and exchange of funds between different parties safe and secure.
There are three important features needed in a blockchain wallet and they are; address, public key, and private key. They are all required for a user to make a complete transaction on the blockchain
An address is generated in every wallet and the user uses it to receive payment. Note that the address can be shared with anyone and can be accessed to make payments. Addresses are generated from a private key and the public key is simultaneously generated from the corresponding private key. The private key grants the user ownership over his cryptocurrency fund and he uses it to sign any transaction. Overall, a blockchain wallet helps a user to store these private keys automatically and aids in completing any transaction. The keys are generated automatically and give the user total access and control of his wallet. A recovery key is usually is used to easily reset his blockchain wallet.
Blockchain wallets are easy to use and highly secure. They are barrier-free and transactions are instant across different locations. There is a low transaction fee and it allows transactions across multiple cryptocurrencies.
Types of crypto wallets
There are different kinds of wallets available and they are as follows;
Desktop wallet: This type of wallet can only be downloaded on a single laptop or computer and accessed from there.
Mobile wallet: a mobile wallet is similar to a desktop wallet in that it is downloaded directly to a mobile phone and lets you spend your coins in actual stores.
Paper wallet: this is kind of an underrated crypto wallet. All is needed is to have to print your private and public keys on a piece and paper and that secures the funds.
Hardware wallet: this is a physical device that is used solely for storing private and public keys. It is usually not connected to the internet unless transfers need to be made. It is usually difficult to be hacked because the private pin is entered directly on the device.
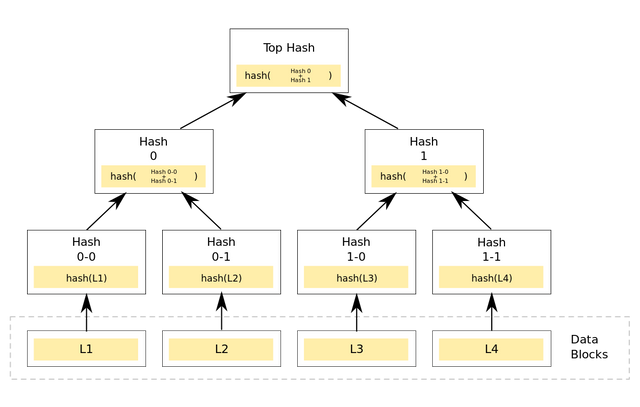
What is the Merkle trees and What its importance in blockchain?
Merkle tree began in 1979 when Ralph Merkle unknowingly created a major component of blockchain by writing a paper titled “a certified digital signature”. Merkle trees have the ability to take a large number of transaction IDs and run them through a mathematical process that results in a Merkle root which is a 64-character code. The Merkle root is important because it instructs any computer to verify a transaction that took place, quickly and accurately. The Merkle tree divides all data inputs into pairs, and this applies to all blockchain transaction IDs.
Importance of Merkle tree on blockchain
- Only a small amount of information is transmitted across networks by the required proof and management.
- It provides a medium to prove the integrity and validity of data and reduces the amount of memory needed to do this.
- It uses simplified payment verification which is a way of verifying the transactions done in a block without requiring to download an entire block.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
Looking at the top right of the page, one can see four basic elements which are key, signature, transaction, and blockchain.
I will go to the blockchain demo website through Blockchain Demo
Key
There are both public and private keys on the blockchain demo. It is worthy to note that the private key is not to be shared with any third party but should be used by the user alone. More so, private keys are used to generate public keys as we have already established.
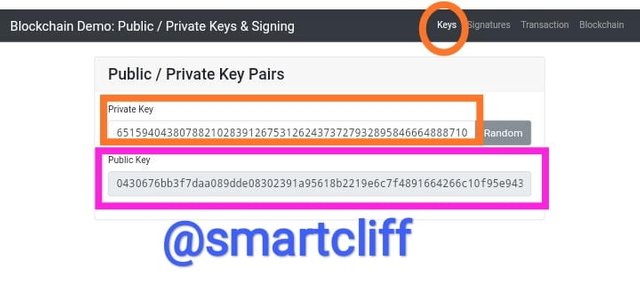
Private key
65159404380788210283912675312624373727932895846664888710515407533992935886308
Public key
0430676bb3f7daa089dde08302391a95618b2219e6c7f4891664266c10f95e9439ea3c18d384bb9945ea40dd915c53e5978243a0486768a59dd31ec86ff0dd5625
The screenshot above is an example of public and private keys in the blockchain and it is seen that these keys are made up of alphanumeric long digits.
I will be altering the private key to get a new public key. It will be seen that for every alteration, a new public key is created.
In the screenshot below, I used 5 as my private key and it created a new public key for me.
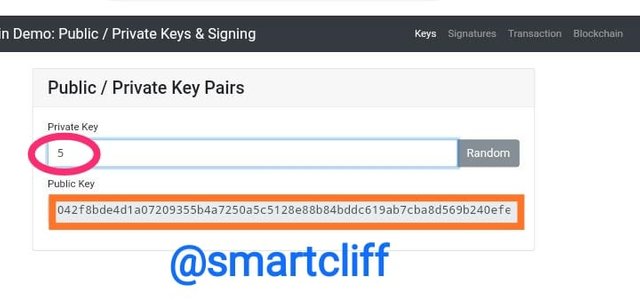
Private key
5
Public key
042f8bde4d1a07209355b4a7250a5c5128e88b84bddc619ab7cba8d569b240efe4d8ac222636e5e3d6d4dba9dda6c9c426f788271bab0d6840dca87d3aa6ac62d6
Next, I will use 7 as my private key and you will notice the change in the public key.
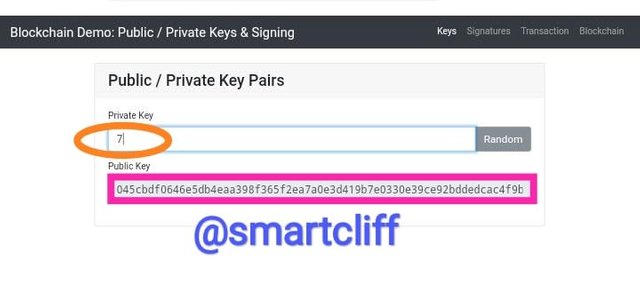
Private key
7
Public key
045cbdf0646e5db4eaa398f365f2ea7a0e3d419b7e0330e39ce92bddedcac4f9bc6aebca40ba255960a3178d6d861a54dba813d0b813fde7b5a5082628087264da
From this practical, it has shown that any number can be used as a private key and a new public key will always be generated. This is why the private key should not be shared and the public key can be seen by just anyone.
Functionality of keys
Private key is used to create public keys. They are generated on the block and used for signing transactions. The public key on the other hand is used to validate transactions carried out on the block.
Signatures
A transaction is signed or verified using a private key and public key. In my practical below, I tried all the options in signing. I created a random private key by clicking on the random option which generated a valid private and public key.
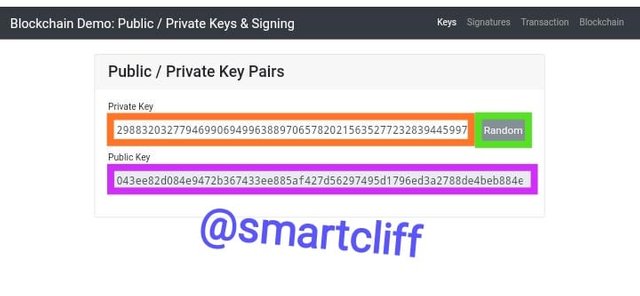
Random private key
29883203277946990694996388970657820215635277232839445997166228681731211872161
Random public key
043ee82d084e9472b367433ee885af427d56297495d1796ed3a2788de4beb884e962b5a0fbef95cfd9642e028243113226fb0fe29fefddba5d7c9d7fe85c3029cc
Next, I will click on the signature and input my message as signing
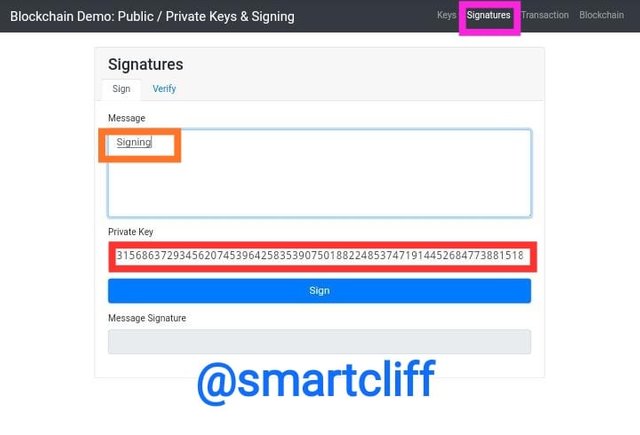
The number below is the private key that was generated and it can only be used to verify or sign the message I have imputed.
Private key
31568637293456207453964258353907501882248537471914452684773881518591579697046
Next, I will click on sign and a message signature will be generated.
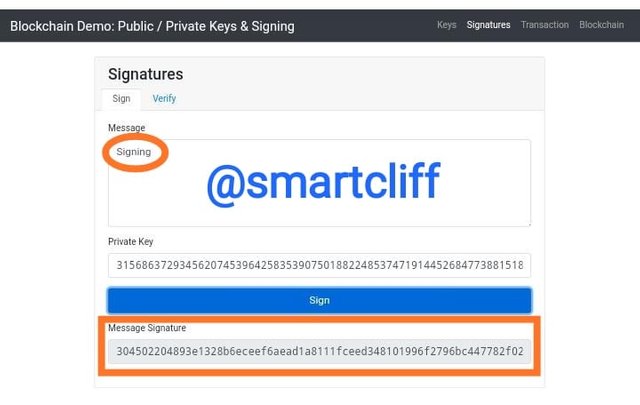
Message signature
304502204893e1328b6eceef6aead1a8111fceed348101996f2796bc447782f0214a28bb022100de6046b15e8b95051cef2bb046a39fb0afad518d186c6377ea1fa069c6041293
Again, I clicked on verify and a public key was generated.
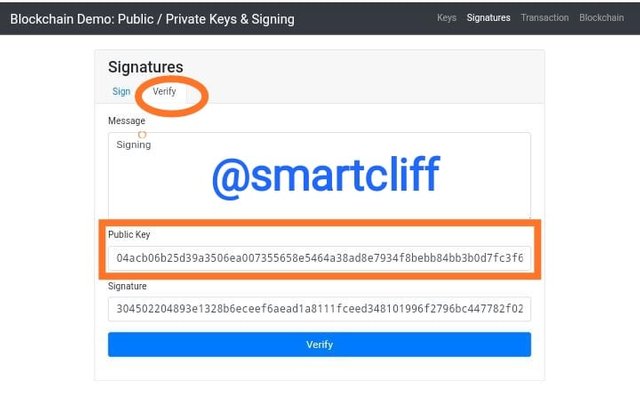
Public key
04acb06b25d39a3506ea007355658e5464a38ad8e7934f8bebb84bb3b0d7fc3f655980c91ee5039a03fbf8083ff1eed324c4b3be8e6ed14d1c91c3de35634ba57b
The public key that I generated from the private key above will now be used to verify my signature and ensure that my message is public and can be seen by other users.
When I clicked on verify, my dashboard turned green which actually means that the message has been successfully sent.
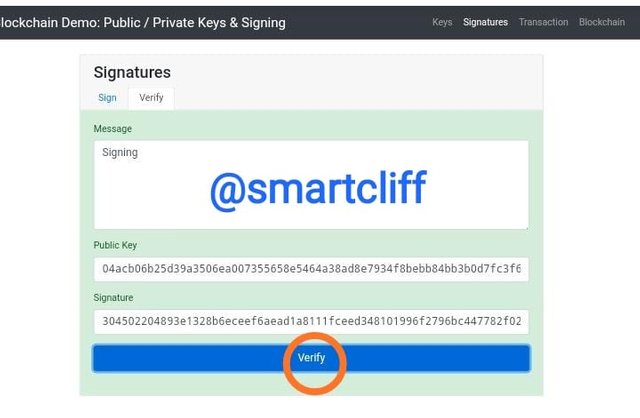
Functionality of signature
Signature is used to show ownership of a signed and verified transaction. It works simultaneously with the private and public keys.
Transaction
This option is where transactions are completed using a private key.
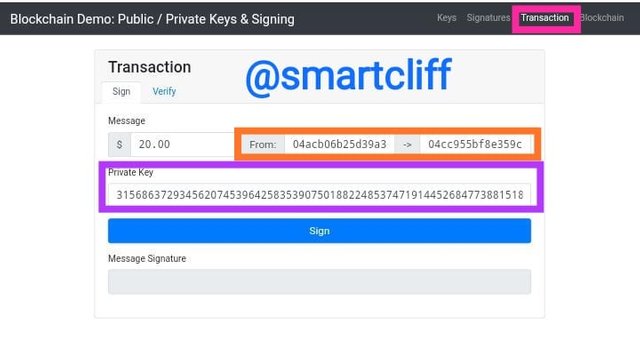
From 04acb06b25d39a3506ea007355658e5464a38ad8e7934f8bebb84bb3b0d7fc3f655980c91ee5039a03fbf8083ff1eed324c4b3be8e6ed14d1c91c3de35634ba57b
To
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Private key
31568637293456207453964258353907501882248537471914452684773881518591579697046
For a transaction to go through, there must be two addresses; one for the receiver and one for the sender. A certain amount of money is also required to complete the transaction and, in this case, $20 was used.
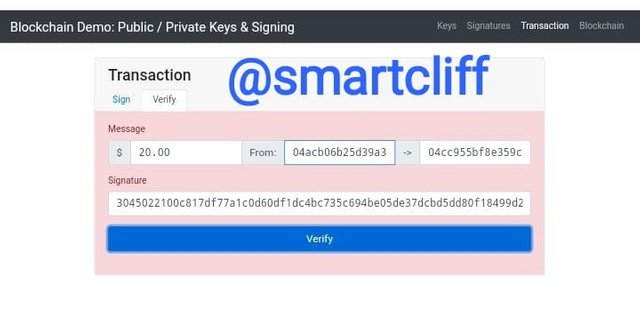
Message signature
3045022100c817df77a1c0d60df1dc4bc735c694be05de37dcbd5dd80f18499d2c36da6f64022040d6c804d0b27dc538ea7ba4e2dd8c5cd5a298a455929f989f829166533f4f2d
A message signature was generated when I clicked on the sign above.
Thereafter, I click on verify. This will generate a signature which can be used to send messages.
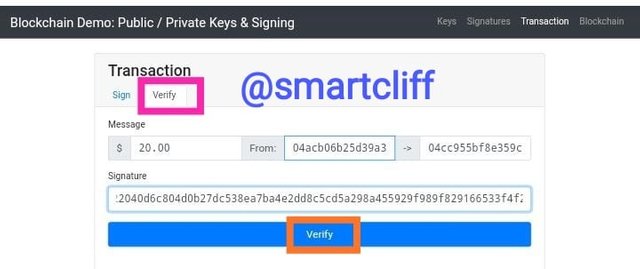
Signature
3045022100c817df77a1c0d60df1dc4bc735c694be05de37dcbd5dd80f18499d2c36da6f64022040d6c804d0b27dc538ea7ba4e2dd8c5cd5a298a455929f989f829166533f4f2d
The green colour shown means that the transaction is completed and successfully sent to the recipient.
Functionality of transactions
It is used in the completion of a block’s transaction.
Blockchain
This is the landing page.
Hash
00006908f507a101e89544498978e9bd2e35462b91d86ef13510685227912e77
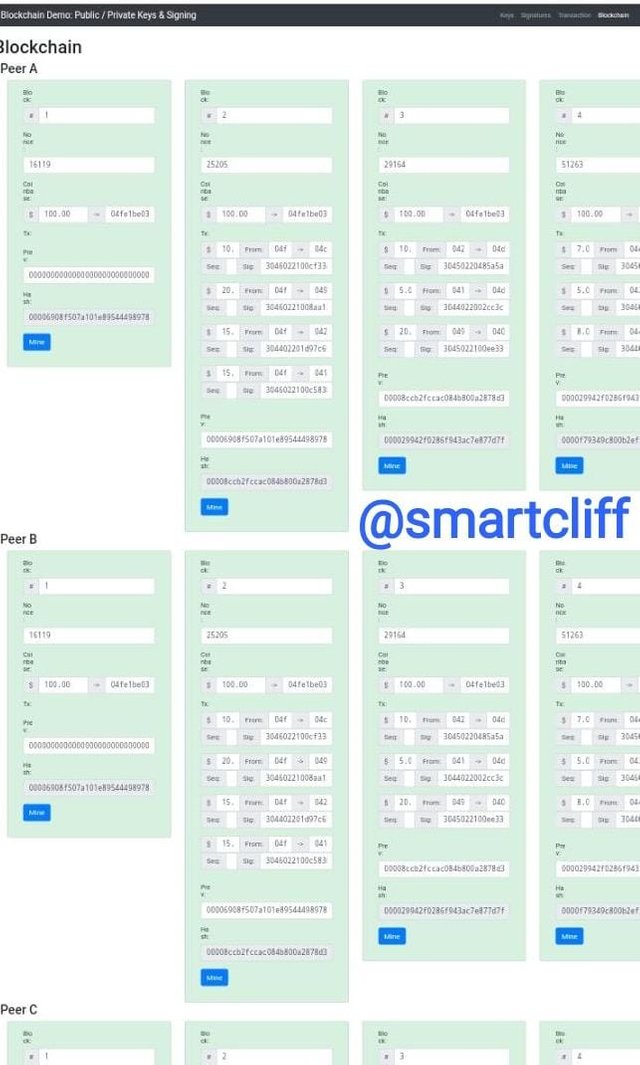
It can be seen that there are different peers and each peer has various blocks.
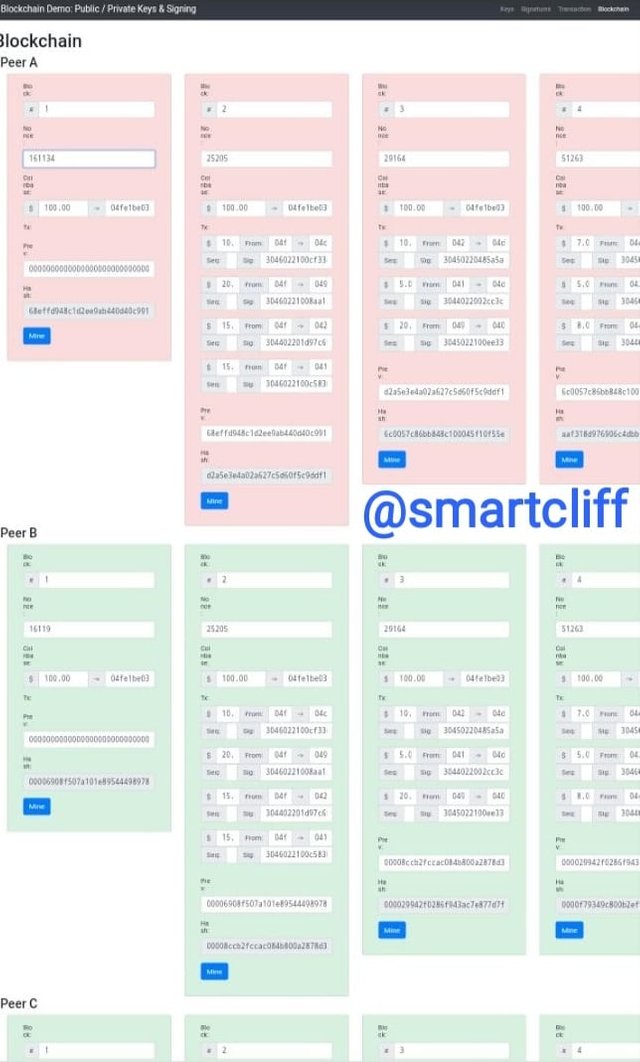
I changed the number on the first block and it showed red meaning that there is an issue and other numbers in different blocks were changed.
Functionality of blockchain in blockchain demo
It is used for recording transactions.
Conclusion. (The overall understanding of CryptoGraphy)
Blockchain cryptography is essential in blockchain technology as it plays a vital role in security and privacy. Transactions can be undertaken in an anonymous and safe way. The private key is never to be shared or disclosed to a third party because a user’s account can be hacked through it while the public key can be shared as the name goes. A blockchain address is essential for sending and receiving transactions and overall, I can say that blockchain cryptography makes blockchain an amazing experience especially for its anonymity.

You've got a free upvote from witness fuli.
Peace & Love!
Amigo muy buen resume que placer volverte a visitar un abrazo.
Yer thanks with all pleasures,can i get your email address? And i hope you read email.