Botnet-a hacker's nuclear weapon
All of you have heard about the botnet more than once. But do you know what it is at all? What is it for? And how not to become a victim of it. If not, then be sure to read this article. In fact, a botnet is a kind of zombie network. It contains ordinary users who download all sorts of shit to their computer. More precisely, infected software that performs certain tasks without the owner's knowledge. You download some file you need, for example, kursach. And it really is there, but in addition to your computer is filled with malware. Which, of course, you don't know about. A botnet is a network of computers infected with the Backdoor behavior malware. Backdoors allow cybercriminals to remotely control infected machines (each individually, part of the computers included in the network, or the entire network as a whole) without the user's knowledge. Such programs are called bots.
Botnets have powerful computing resources, are a formidable cyberweapon, and are a good way to make money for attackers. At the same time, infected machines that are part of the network can be controlled by the botnet owner from anywhere: from another city, country, or even from another continent, and the organization of the Internet allows you to do this anonymously. A hacker can install such bots on the computers of millions of people around the world in a short time, naturally, without their demand. At the same time, the capabilities of the programs are very large. This can be the usual collection of personal information, conducting illegal activities, mining farms, stealing passwords. The owner of the computer can not guess anything until he turns off the Internet or does not lose money from the accounts
Who benefits from botnets?
In short, all computers that are on the same network and controlled by one person are serious weapons. The person who manages all this has the ability to really raise the dough. He can manage the entire process from anywhere in the world. The main thing is that there is an Internet and a computer, or rather, any device from which you can access the Internet. Today, botnets perform more serious tasks. For example, a person who sends spam from "infected" computers can earn up to 100-200 thousand euros per year. At the same time, it will not hit the hacker on the head, but the owner of the computer, because spam was sent from his device. For example, an account on or on the social network VKontakte may be banned for sending spam, and the user may not be aware of the situation and at the same time sincerely resent it.
Today, the botnet is very actively used for blackmail. All computers included in the network can be used for DDoS attacks on a specific site. Because of this attack, the site will crash and stop functioning. This can continue indefinitely until the victim pays a certain amount or gives out some information.
The owner of the Smartresponder mailing site, Maxim Higer , was forced to pay a considerable sum to a hacker from London, who used the latest technology to organize a DDoS attack on his site. While negotiations were going on between them, the Smartresponder site was unavailable for several days. Today, even well-protected government, banking, and other serious websites are often attacked.
Attackers often use the capabilities of botnets to anonymously access the Internet under someone else's IP to steal passwords and hack websites. At the same time, such powerful networks can be rented out to perform specific tasks.
The botnet is also often used for mining cryptocurrencies. To mine, you need to have a large number of computers to solve problems. And who but zombie users can help with this? Is my computer infected with a bot?
The answer to this question is not easy. The fact is that it is almost impossible to track the interference of bots in the daily work of the PC, since it does not affect the performance of the system in any way. Nevertheless, there are several signs by which you can determine that a bot is present in the system:
- unknown programs try to connect to the Internet, which is periodically reported by the firewall or antivirus software;
- internet traffic becomes very high, although you use the Network very sparingly;
— in the list of running system processes, new ones appear, masquerading as normal Windows processes (for example, a bot can have the name scvhost.exe – this name is very similar to the name of the Windows svchost system process.exe; it is quite difficult to notice the difference). Ways to infect a botnet
Прямой Direct hacking of the computer or local network by brute-force passwords to gain access on behalf of the administrator. Most often, such attacks are carried out specifically on the private networks of large companies for espionage. They require a lot of resources for hackers, so they are practically not used to hack ordinary users.
🔻 It is also easy to infect a computer if there is a hole or vulnerability in the software code. The scale can be astounding. For example, a hacker discovers a hole somewhere in Windows 10 and everyone who uses it is automatically at risk. Usually, when such vulnerabilities are identified, software developers react quite quickly and fix them with updates. So, always update your computer!
🔻 Infecting your computer with authorized access. This type of infection can be either targeted or random. Imagine that you gave your computer for repair. To save money, you chose the cheapest price and did not even make sure of the legality of the company. And asked the wizard to install a hacked program for you. Photoshop or some word. And he accidentally installed infected software along with these programs. But he doesn't even know about it, and neither do you. And also, if this is some novice basement hacker, he can specifically pour you infected software and hello, botnet. So, I recommend that you use the services of only proven masters.
🔻Infection connection via an infected USB flash drives. Everything is simple, put a flash drive, and on the computer the autorun of removable storage devices is not disabled, that is, there is a chance that the virus will easily penetrate your computer. The best way to combat this method of spreading the infection is to disable autorun for CD-and USB-media.
🔻 Infection by the user's input into error. Perhaps the most common way to infect computers around the world. Here, social engineering, intrusive advertising, spam mailings, in short, everything that can make an unlucky user install a virus on their own computer is used. Usually viruses go "in the load" to some useful program.
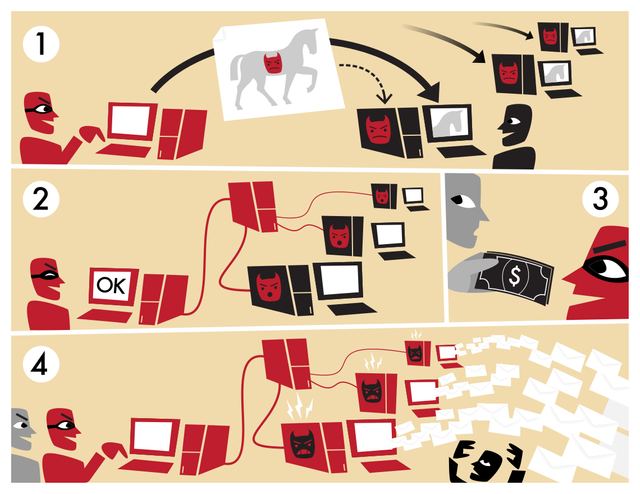
The use of botnets Botnets can be used by attackers to solve criminal tasks of various scales: from sending spam to attacks on state networks.Sending spam. This is the most common and one of the easiest ways to use botnets. According to expert estimates, currently more than 80% of spam is sent from zombie machines. Spam from botnets is not necessarily sent by the network owners. For a fee, spammers can rent a botnet.It is spammers who can appreciate the effectiveness of the botnet: according to our data, the average spammer earns 50-100 thousand dollars a year. Thousands of botnets allow spammers to send millions of emails from infected machines in a short time. In addition to ensuring the speed and scale of mailings, botnets solve another problem of spammers. Addresses from which spam is actively sent are often blacklisted by mail servers, and emails coming from them are blocked Another" bonus " of botnets is the ability to collect email addresses on infected machines. Stolen addresses are sold to spammers or used for sending spam by the botnet owners themselves. At the same time, the growing botnet allows you to get new and new addresses.
The kibershantazha. Botnets are also widely used for DDoS attacks (Distributed Denial of Service). During such an attack, a stream of false requests is created from bot-infected machines to the attacked server on the Network. As a result, the server becomes inaccessible to users due to overload. Attackers usually demand a ransom for stopping the attack.Today, many companies operate only via the Internet, and for them the unavailability of servers means a complete shutdown of business, which, of course, leads to financial losses. To quickly restore stability to their servers, such companies are more likely to comply with the demands of blackmailers than to turn to the police for help. This is exactly what cybercriminals are counting on, so DDoS attacks are becoming more and more common.
DDoS attacks can also be used as a means of political influence. In these cases, the servers of government agencies or government organizations are usually attacked. The danger of such attacks is also that they can be provocative: a cyber attack on the servers of one country can be carried out from the servers of another, and controlled from the territory of a third state.
Anonymous access to the Network. Attackers can access servers on the Network using zombie machines, and commit cybercrimes on behalf of infected machines – for example, hacking Anonymous access to the Network. Attackers can access servers on the Network using zombie machines and commit cybercrimes on behalf of infected machines – such as hacking websites or transferring stolen funds.
Selling and renting botnets. One of the options for illegal earnings with the help of botnets is based on renting out a botnet or selling a ready-made network. Creating botnets for sale is a separate area of the cybercrime business.
Phishing. The addresses of phishing pages can quickly get blacklisted. The botnet allows phishers to quickly change the address of a phishing page, using infected computers as proxy servers. This allows you to hide the real address of the phisher web server.
Theft of confidential data. This type of criminal activity, perhaps, will never cease to attract cybercriminals, and with the help of botnets, the catch in the form of various passwords (for accessing E-Mail, ICQ, FTP resources, web services) and other confidential user data increases thousands of times! A bot that infects computers on a zombie network can download other malicious software – such as a Trojan that steals passwords. In this case, all computers that are part of this zombie network will be infected with the Trojan program, and attackers will be able to get passwords from all infected machines. Stolen passwords are resold or used, in particular, for mass infection of web pages (for example, passwords for all found FTP accounts) in order to further spread the bot malware and expand the zombie network.
How not to fall into the clutches of a botnet?
In general, the prospect of becoming a victim of a botnet is not good. So, here are some ways to protect yourself from intrusion:
◾use a firewall and do not ignore its warnings;
не do not open suspicious email attachments or messages in social networks;
◾on various sites, carefully look at what buttons you click when downloading programs;
не do not fall for provocative ads that promise a big win after downloading and installing something;
◾use only updated software;
◾do not use autorun of flash drives and disks;
Always back up your most important data and store it outside of your computer.
Every year botnets develop and it becomes more and more difficult to detect them. Even anti-virus software often pass it by yourself. Therefore, you should not rely on them. Be careful when you download any garbage and do not forget to update the computer in time! Examples of well-known botnets
Mirai and Reaper According to a report published by Fortinet in August 2018, Mirai was one of the most active botnets. 2 years after its creation, the Mirai botnet has new features, such as the ability to turn infected devices into malicious proxy software complexes and mining devices. Botnets are often used for mining cryptocurrency. During mining, hackers can use the victim's computer hardware and electricity to mine bitcoins.Mirai is just the beginning. In the fall of 2017, Check Point engineers discovered a new botnet known as IoTroop and Reaper. It hacks devices on the Internet of Things even faster than Mirai. Mirai infected vulnerable devices that used default passwords and usernames. Reaper went further, hacking into about a dozen devices from different manufacturers through vulnerabilities — including devices from well-known companies such as D-Link,Netgear and Linksys. The Reaper botnet is also flexible, allowing hackers to easily update its code.Reaper was used in attacks on European banks last year.
Conclusion
Today, botnets are one of the main sources of illegal earnings on the Internet and a formidable weapon in the hands of intruders. It is not to be expected that cybercriminals will abandon such an effective tool, and security experts are anxiously looking to the future, waiting for further development of botnet technologies. The danger of botnets is compounded by the fact that their creation and use is becoming an increasingly simple task, which even schoolchildren
use the information only for legitimate purposes