Steemit Crypto Academy Season 2 || Privacy Coins || For Professor @levycore || Done By @preshdan
Am grateful to be a part of this week's lecture presented by Professor @levycore and I must commend the explicit work done on this lecture.
This week's homework task focuses on Privacy Coins
Homework assignments
Create an article for this week's homework with content that covers the following:
1 Choose a Privacy Coin and perform a detailed fundamental analysis of the coin.
2 Describe the steps in creating a wallet for the Privacy Coin of your choice. (Screenshot required)
3 Provide an explanation of the reason you chose the Privacy Coin. (List the advantages and disadvantages)
4 Conclusion.
Before I start attempting the questions, lets take a brief look at:
Brief Background of Private Coin
Privacy coins are coins of cryptocurrency which take Bitcoin’s privacy, anonymity to the next level. Each transacton made with Bitcoin is technically anonymous since there are no names involved. Alternatively, the record of each payment is made with a user’s public key, which is an arbitrary combination of numbers and letters. Nevertheless, there is possibility to figure out the owner of a particular public key owing to the fact that a name and bank account is necessary to make a transfer of Bitcoin into traditional currency. Because every transaction on Bitcoin is usually recorded on a public database, someone's entire payment history is absolutely trackable once the public key is known. Payments with privacy coins are actually and completely private and confidential.
Privacy coins have one function in common, though there are various methods employed by privacy coins - privacy coins makes use of convoluted mathematical equation to assure that every transaction is verified properly by the entire without making a public record of the involved parties and how much they spent. By so doing, privacy coin acquire the possession of decentralization of a typical cryptocurrency during the same time allowing users to remain anonymous.
Monero, Zcash, and Dash are the three most popular privacy coin
Question1
Choose a Privacy Coin and perform a detailed fundamental analysis of the coin.
I will be discussing Zcash
Zcash came into existence in 2016 through Zooko Wilcox-O’Hearn with a team of experienced and skilled cryptographers and scientists with the aim of providing users with the utility of Bitcoin at the same time presenting them with the ability to beshield their privacy.
Zcash is able to compete in the increasingly crowded market with the help of its team's science-based approach that has a determined concentrated attention on decentralization and privacy. In order to assist in protecting the privacy of the users and at the same time making sure that the system is not being cheated nor stealing committed, Zcash makes use of custom-built zero-knowledge-proof known as zk-SNARK.
At the first launch of Zcash, the value of coin was driven over $5,000 by a combination of low supply and hype, this being above 6 Bitcoins at the moment. Up to 2020, Zcash founders receives 20% of all mined Zcash as "founders reward" with the pact of donating 10% of the reward to Zcach non-profit foundation which is designed for the purpose of serving the interest of all users of Zcash.
Owing to Zcash use of open-source, it is quite impossible for the Zcash company to exercise influence or dictate the neha behaviour of any aspect of the cryptocurrency beyond the provision of updates to the software responsible for the Blockchain. This guarantees that that Zcash is really decentralized.
Zcash allows users the capability to participate in two categories of transactions. The first being an open transaction, that works basically the same way as a Bitcoin transaction. Options of storing or sending currency from a protected address is available to users, this lets users conceal the metadata behind their transaction thereby maintaining control over their privacy.
The shields are manufactured with the use of zk-SNARKs (which is the acronym for Zero-Knowledge Succinct Non-Interactive Argument of Knowledges). It is an absorbing form of zero-knowledge cryptography that allow a party (the prover) to prove to another party (the verifier) possession of data (such as secret key) without ever disclosing the information or having direct interaction with each other. This implies that instead of carrying out direct validation of the sender and receiving addresses, Zcash is designed and constructed with the ability to validate a transaction without disclosing any of the underlying information.
For every shielded transfer, the value of the input adds to the output values.
The sender is given the authority to spend by they possess the private spending key of the input notes.
The input notes private spending keys are linked cryptographically to a signature over the entire transaction, such that the is not modifiable by a party who lacks the knowledge of these private keys.
A shielded transaction is also has the capability of verifying that a user has enough ZEC so as to to process transactions by making use of “commitments” and a nullifier that have a similar relationship.
A unique identifier called "rho" which is used in verifying payments is given to all these commitments. Any time a shielded transaction is spent, a nullifier is published by the sender which happens to be the rho’s hash from an unused commitment. This makes provision of a zero-knowledge way to show that they are authorized to transact.
The team responsible for ZEC emphatically upholds a claim that their blockchain is indded independent and decentralized, in spite of accusations that it is a corporate coin.
The launch of Zcash as a coin met with a mass of hype which resulted in the cryptocurrency having a value of more than ***6 Bitcoins (over $5,000)**** on the day of launch. It wasn't quite long when this speculation died down and ever since ZEC has been growing at organic rate.
The initial launch face some controversy. Zcash was created with the use a “Parameter generation ceremony” which involves 6 individuals that each created a detached portion of the eventual “master passkey” needed for Zcash to work. These keys were portrayed as toxic waste.
How Zcash Master Keys Work
A master key authoritatively calls for all 6 shards. This demands a lot of trust in the 6 individuals that took part and the ceremony has been depicted as little more than security theatre.
Should the passkeys in one way or the other leak or the involved individuals colluded then it is theoretically feasible for somebody to procure the master passkey, which would provide them with the ability to make their own ZEC.
In spite of the potential problems, it is worthy of note that only a single participator needs to have successfully damage all traces of their shard beyond use in order to make certain that the ceremony was a success.
So for someone to acquire access to the master key, it would demand all six participants to either interfere with honesty or be compromised.
Zcash is mined in same way as most other cryptocurrencies. Banks or governments are centralized institutions responsible for printing money, alternatively, Zcash and as well as other cryptocurrencies undergo a decentralized approach. ZEC is manufactured by its community by means of mining. The tenet of the fundamental technology behind Zcash is similar to the technology behind Bitcoin. The both coins are mined by means of making use of computer power to solve algorithms.
The blockchain is made sexure by means of a consensus mechanism known as Proof-of-Work (PoW).
A miner makes use of their computers in order to solve convoluted equations. An addition of a new block is made to the blockchain as soon as the equation is solved and the miner gets rewarded with ZEC.
There are two purposes that this reward system serves: The first purpose is encouraging miners to devote computing power so as to have transactions completed on the Zcash blockchain.
The second is to control or direct according to rule, principle, or law; the manufacturing of new ZEC, which is then divided into portions and dispense by the miners.
Question 2
Describe the steps in creating a wallet for the Privacy Coin of your choice. (Screenshot required)
As taught by Professor @levycore, privacy coins has their individual wallet so do Zcash. The steps involved in creating Zcash wallet is as follows:
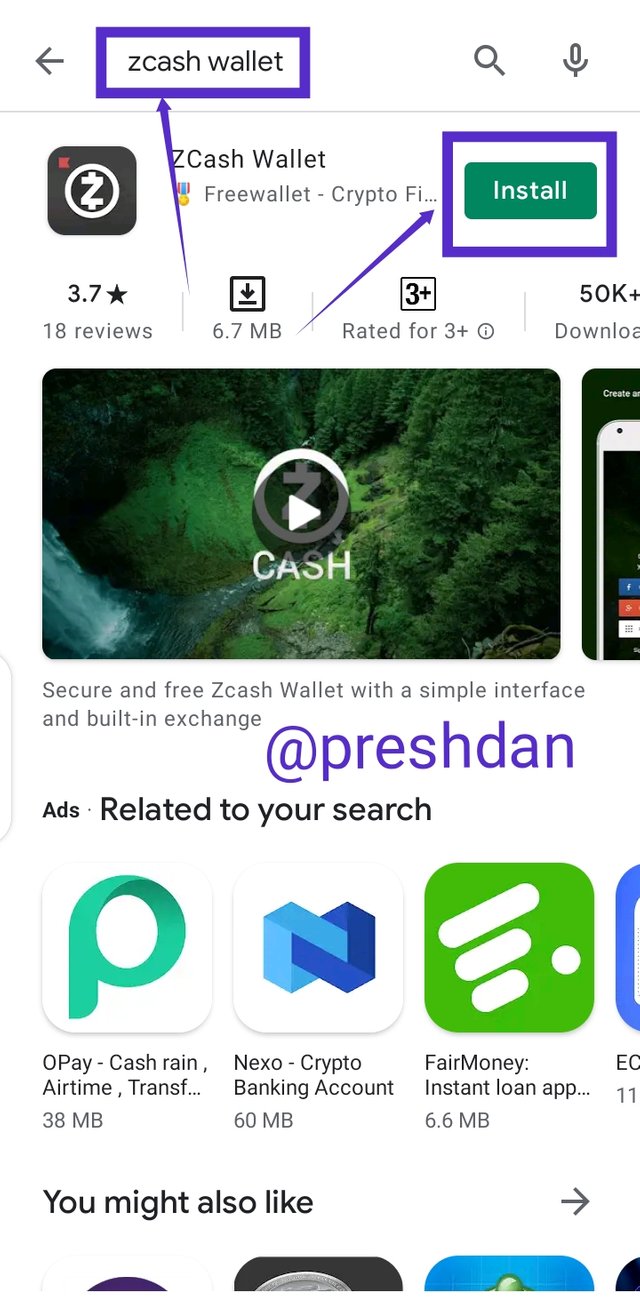
From your playstore app, search for Zcash wallet and select "Install".
The installation process is initiated after clicking install. At the end of the installation, click "Open"
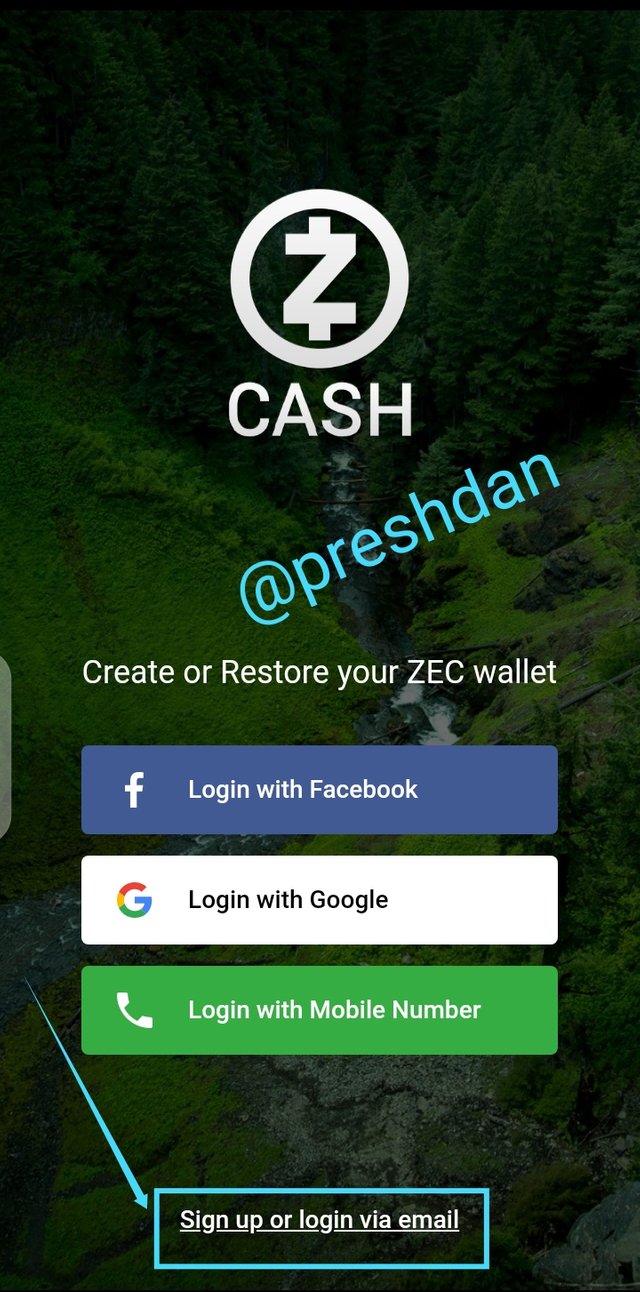
When the Zcash wallet app is open, as a new wallet holder select "Sign up or login via e-mail"
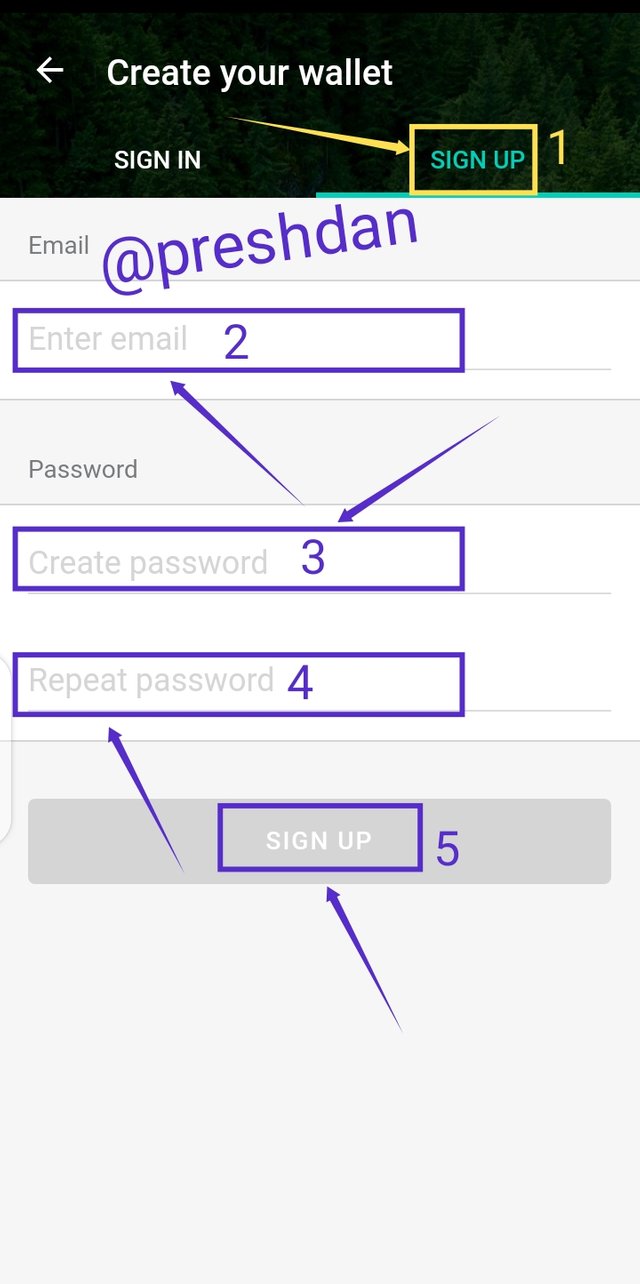
Selecting sign up or login via e-mail ushers you to another interface where as a new user, 1. you select "Sign Up", 2. Input your email, 3. Create a wallet password, 4. Re-enter your password and 5. Click "Sign Up"
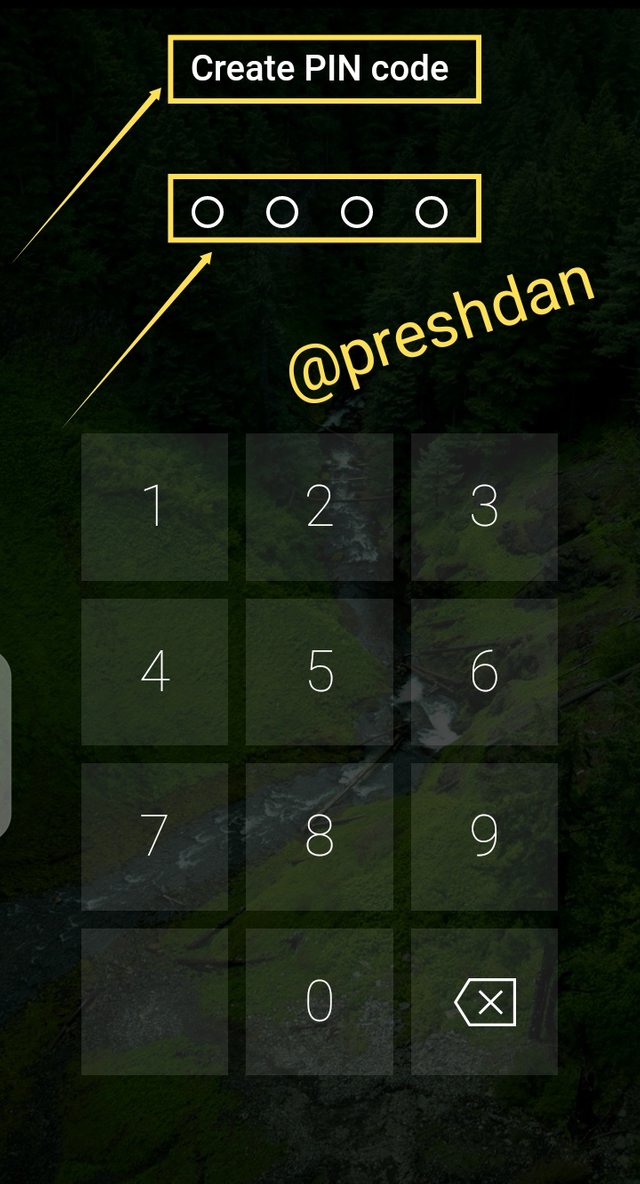
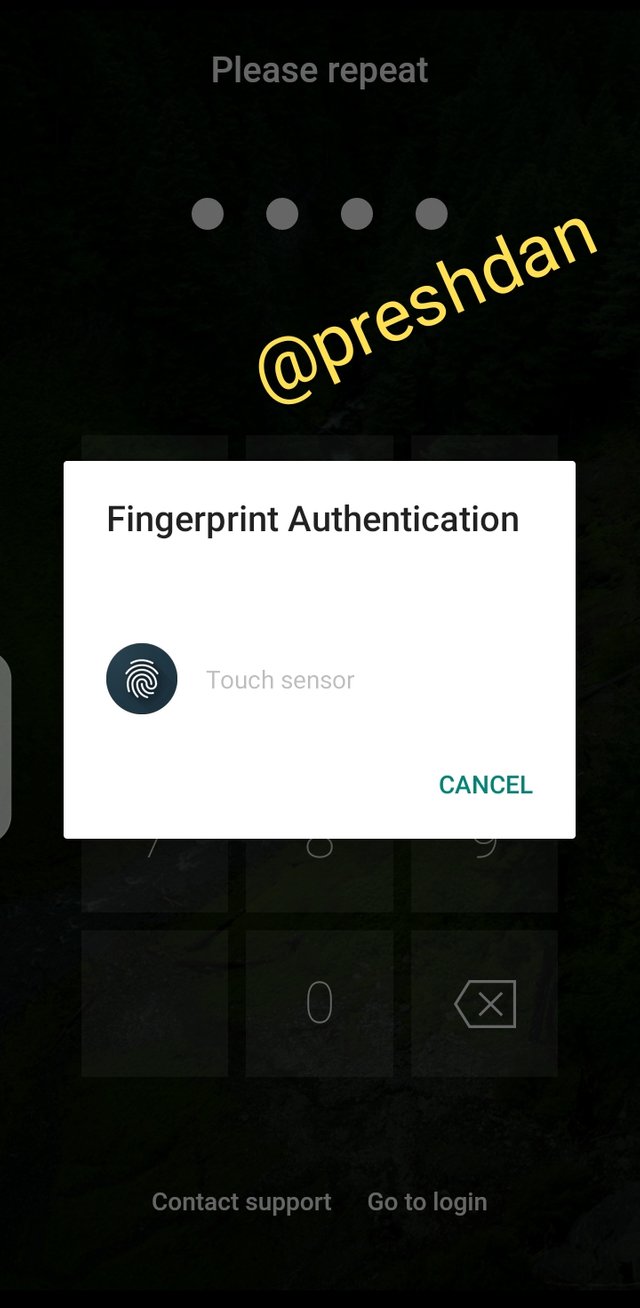
Once the above details are provided, the next step is to create a 4-digit wallet pin code followed by a fingerprint authentication
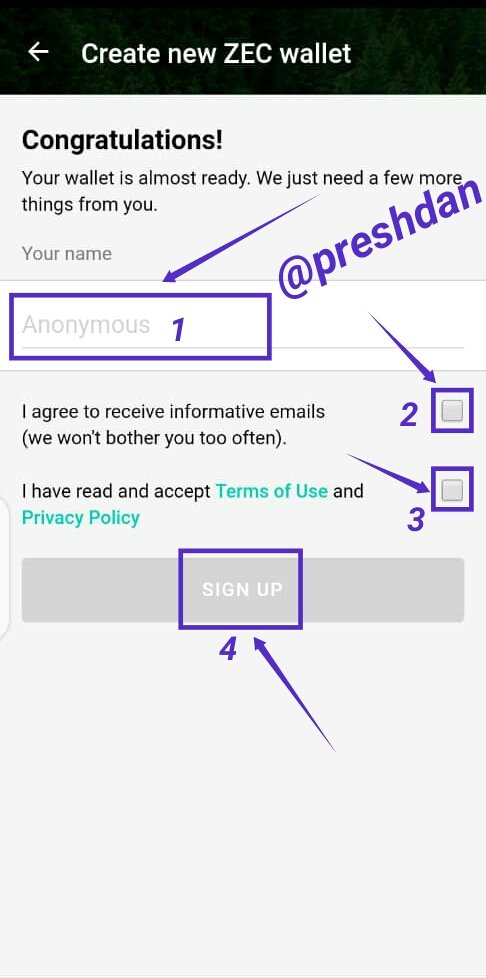
The next step after the fingerprint authentication is done is: 1. Input your (which I anonymous), 2. Agree to receive informative emails, 3. Accept terms of use and privacy policy then 4. Click Sign Up and the wallet is ready for use.
1
2

3
4
5
6
Question 3.
Provide an explanation of the reason you chose the Privacy Coin. (List the advantages and disadvantages)
The following are reasons why I chose Zcash:
The flexible alternative to shield transaction and conceal the sender's and receiver's identity on the blockchain is one of Zcash's structure or make-up. This does not only practically protect user's anonymity but as well blocks malevolent actors from aiming at addresses that have high currency volume. This indeed is advantageous for enterprises to protect informations of confidential nature regarding business transactions and employee payrolls as well. This is dissimilar to transparent cryptocurrencies such as Bitcoin which have evey information available for view on the their public ledger.
Zcash ability to hide the quantity amount in a shielded transaction, it is less susceptible to a timing attack. Timing attack occurs when a hacker takes advantage knowledge of when a new coin is “minted” and in an effective manner spend the coin before the user can.
Security bugs have so far not been found in Zcash protocols, and Zcash has not recorded any network downtime or security ruptures.
The zero-knowledge security layer can be used in verifying any relation without revealing inputs or divulgating information, and could possess implications for coded security transmissions together with other possible applications.
Zcash has proved, optional privacy structure which is not presently native to bitcoin or many other cryptocurrencies.
It carriesnout world-class, cutting-edge cryptographic privacy technology known as zero-knowledge proofs (ZKPs).
It is also known for it's above-average network effects which includes exchange listings, liquidity, as well as name brand recognition.
Zcash has vigorous, reputable team and advisors including Zooko Wilcox, Gavin Andresen, Nathan Wilcox and Vitalik Buterin.
Zcash's high inflation as well as founder’s reward in each block depreciate the asset and also dissuade long-term holders.
The zK-SNARK privacy technology is not singular to ZEC and can also be put to use by other cryptocurrencies such as Ethereum.
In the course of project creation, ZCash experienced a Trusted Setup ceremony which is a potential security hole and is debatably antithetical to the notion of a trustless money.
A centralized business, Electric Coin Company, runs the project.
While privacy is a much-desired structure or make-up in the virtual world, it is accompanied by the perils of a considerable great size of criminal elements. Cryptocurrency operators have to push away numerous hacking attempts by malevolent participants. Also law enforcement agencies and regulators are more likely to scrutinize people with large transactions. Zcach goes a long way mitigate these conditions owing to it's privacy level.
This is my entry Professor @levycore, thanks for reading through
Cc:
@xkool2

Hi @preshdan, Thank you for taking my class in the 8th week.
You are using a photo that is not copyright-free and the source you have posted is incorrect, please review the rules and guidelines before creating an assignment.
Thanks prof for pointing out that unintentional error. I have edited the post, please kindly review it, best regards.