Steem crypto academy:-: season 3 week 8:- home work post for professor @stream4u

1. Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Before discussing blockchain cryptography, let's understand what is cryptography.
So cryptography is composed of two Greek words:- Kryptos and Graphein. Which literally means combined:- writing hidden.
So in a nutshell, cryptography is a technology which enables the secure communications between two individuals. And it also prevents other people from accessing those messages and data.
In cryptography, first of all data is translated to machine language which is known as ciphertext and after this, it is sent to the destination where private key is required to decrypt this message that is translated from machine language to human language that can be read.
Blockchain cryptography:- Now we know that in any blockchain data is stored in blocks and by using the digital ledger it is shared across the nodes. And this all is done in such a way that it is impossible to alter the data stored in it after it is validated.
All these blocks are also connected with each other. And all the participants in the network has a private key which acts as a digital signature which is used to sign any transaction and then only it is initiated.
Any single change in the data will lead to change the hash and it will lead the blockchain to be inconsistent and make the whole blockchain invalid. It is something known as avalanche effect in which a small change is data lead to a big change.
Also this lead to make the digital signature invalid.
To make any changes in the data stored, anyone must have control over minimum 51% of the total computing power then only any change in data can be validated. But it is quite hard and literally impossible to do this.
Blockchain Platforms:- Now a days as more people are taking interest into blockchain this sector is growing day by day. Now a days there are a number of blockchain available which may be public, private, permissioned or permissionless blockchain and on this blockchain many dApps are coded.
Some of the popular blockchain Platforms are:-
- Ethereum
- Steem
- Ripple blockchain
- Binance chain
- EOS & many more.

2. What is Public Key Cryptography?
Public key cryptography is a part of asymmetric-keys cryptography in which two keys are used. One of it is known as public key and can be shared on network. And other one is private key which is a secret key.
Public key is important as it is hashed to produce the wallet address that is like the bank account number which is shared, which is used to receive funds. Public key is stored in digital certificate in a network as it is used for many purposes in a network.
Public key is generated from private key but for security purposes so that no one else can derive private key from public key, it's reverse engineering that is deriving private key from public key is impossible.
The use of private key is to sign the transaction but public key is required to verify the signature. This means public key is required to verify the signature by the private key.

3. What is Private Key Cryptography?
Private key cryptography is also a part of asymmetric cryptography. At the time when a wallet is created private key is generated and from this public key is generated. We have discussed this in the previous section.
Private key, as the name suggests is the private and should not be shared with anyone else. As it is the key of your wallet just like the key of a safe containing fund and whoever has the key is the owner in this case. If you give your key to anyone, he will be owner of the Wallet and can assess the funds in that wallet as those funds can only be accessed using the private key.
Private key is used to sign the transaction and only after this funds can be transferred to any other wallet. So anyone with your private key can access the funds and also can transfer those to any other wallet that's why private key should not be shared with anyone else.

4. Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Digital signature cryptography is also a product of asymmetric cryptography in which private key is required to sign the transaction to initiate it and then public key is required to validate this signature.
It is similar to that of in conventional financing system. In any bank when you try to transfer funds to anyone else's account, you need to sign the transaction. Similarly while using UPI which is a abbreviations for Unified payment interfacewhich is used for transferring funds online, also require the signature in the form of a 4 or 6 digit code. For more security purposes, sim with that number must be inserted in the phone to initiate the transactions..
Similarly in the crypto currency world, when anyone want to transfer the funds to any others wallet, it requires the signature using the private key and then only this transaction is initiated and is broadcasted to the network where miners use owner's public key to validate this signature and then the funds are deposited in the destined wallet and transaction is deemed to be completed.
Advantages of signature cryptography:-
There are many advantages of signature cryptography in the blockchain:-
Authenticity:- As signature of a person signed with private key can be verified with public key, the receiver can get to know that This message has been sent by the one who is claiming himself to be in this message.
For example if I send any person a message that lets have a drink together on behalf of anyone else, then receiver can easily, by using the public key of that person, get to know that this message is not sent by that personIntegrity:- this means it ensures that the message which is being sent to person A from person B is the same message which is receiving by person B and nothing has beed changed on the way. If the data has been changed then the hash value will be changed and the blockchain will become inconsistent.
.
For example, if I want to send a message to my friend @rishabh99946 that lets go on a walk on Monday at 4 am and the message is signed by me. And if anyone in the middle want to change the message to let's go on a walk on Sunday at 4 am he can't do that because this will change the hash.Non-repudiation:- This means than anyone with signed message can't claim that he hasn't done this. As the data is signed with private key which Should only be possessed by the owner. And if this is signed this means owner has done this and he can't claim he hasn't done this.
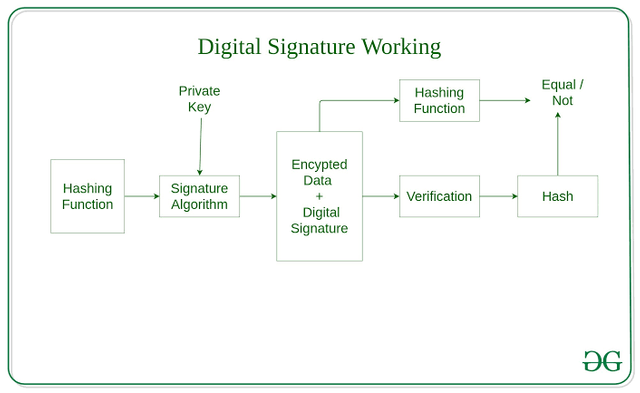
How digital signature works:-
First of all, the hash of data is created using the hash function and then this hash function is digitally signed with private key of the sender. And then this is called signature algorithm.
After this, this signature algorithm is combined with the signature and is sent for the verification.
Now in the verification process, the received data and signature is used to produce a hash function and then again the signature is verified with the public key of the sender. And both of these values are compared and on the basis of the comparison, signature is declared to be validated.

5. Explain what is Symmetric and Asymmetric cryptography?
Symmetric Cryptography:- Symmetric cryptography is the one where a single is used for the both purposes that is encryption and decryption of data. In this type of cryptography there is no private or public key rather than this a single key is used.
In this type of cryptography, initially key is used to decrypt the data that is to be sent and the text that is human readable is converted into the ciphertext or you can say machine language.
When this data is reached at the destined place, that very key is used to decrypt the data that to change the ciphertext to human readable language.
This type of cryptography is generally used within a organization where a bulk of data is transferred from a person to another person on regular basis. Because this type of cryptography is ideal for bulk of data.
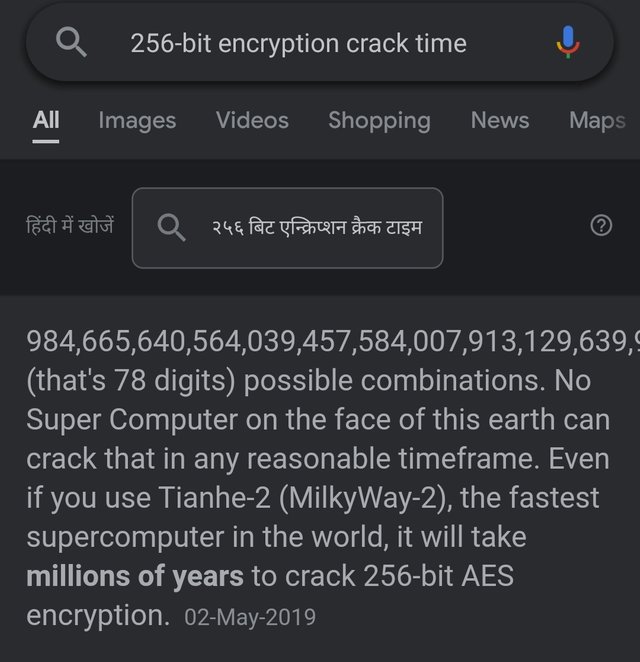
Usually the keys in symmetric cryptography are 128 ,192 and 255 bits long. And it requires a long time to crack the data. And there are millions of billion possible combinations to crack the data.
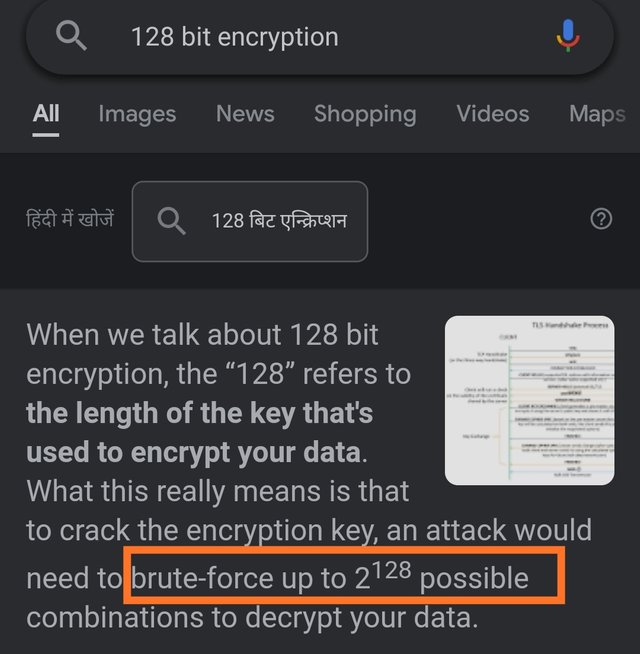
For example, there are 2^128 possible combinations to encrypt the 128 bits encrypted data and to encrypt the 256 bit encrypted data it will take a super computer million of years.
Some examples of symmetric cryptography are:- AES and DES which are the abbreviations for Advance encryption standard and data encryption standard respectively.
Types of Symmetric Cryptography Algorithms:-
There are two types of Symmetric Cryptography Algorithms this means that these are two methods of changing plain text that is human readable to the ciphertext.
- Block cipher
- Stream cipher
The main difference between the block cipher and stream cipher is that stream cipher takes only 1byte or 8 bits of plain text and then it is converted to the ciphertext thus is created only confusion but it have high complexity and at the same time it requires less time for encryption but as in this at a time only 8 bits are encrypted, reverse encryption is easy as compared to block cipher.
On the other hand, block cipher takes 64 or more than 64 bits at a time and encrypt it. Thus it creates diffusion in the encryption as well. And as at a time it encrypt 64 bits or more, reverse encryption is hard and more complex.
Asymmetric Cryptography:- In this type of y, two keys are used. One to encrypt the data before it is sent to the receiver that is called private key and other one is called public key that is required to decrypt the data to human readable language.
But this type of cryptography is not suitable for any organisation and is not as efficient as the symmetric cryptography where single key Is used.
How asymmetric cryptography works:-
First of all the data which is to be sent is encrypted with the public key of receiver. And when this data is encrypted now even the sender can't decrypt it. And this data when reaches the receiver then this data is decrypted with the private key of receiver and when a private key is entered, public key which is already entered validates the private key and if it is validated then the message decryptes.
In this way both public key and private keys are used
Now for example, I want to send a encrypted message to my friend @rishabh99946 then initially I have to encrypt the data that is a message, by using the public key of receiver that is Rishab99946 After the encryption of data, when this is received by the receiver, receiver (@rishabh99946) will use his private key to encrypt the data and the ciphertext will be translated into human readable language. As the data is encrypted with the public key of Rishab, now even I can't decrypt this data and the private key will only be possessed by the Rishab so only he can see the data.

6. How Blockchain Wallets Cryptography works
Crypto wallet is similar to the wallet we use on the daily basis with the difference that in regular wallet we contain the regular currency while in crypto wallet, crypto currency is contained.
But at the same time it can be differentiated from the Wallet as wallet only can contain currency can't transfer currency to another wallet.
Every Wallet has a address that is used to receive fund. It also has the private key and public key associated with it and are retrieved when wallet is created, and acts as the password of the wallet.
There are many types of wallet. Such as hot wallet and cold wallet
Let's take a brief about these.
In a nutshell we can say that hot wallet are the one which are connected with the internet and these types of wallet are Ideal for trading where a trader need to sell and buy funds from and to the wallet. But these types of wallet are more prone of getting hacked. Hot wallets are classified into exchange wallet which are usually connected with a exchange that helps in selling and buying asset easily and desktop wallpaper which are usually Installed on a desktop and online wallet which are cloud based Wallet and can be accessed from anywhere.
On the other hand cold wallet are the ones which are not connected with the internet and these types of Wallet are usually ideal for holding funds for a longer period of time and as these types of wallet are not connected with internet so these are less prone to get hacked.
But if the seed phrases that are used to get access to these wallet is lost, the key is lost In that case funds are lost permanently.
Now let's talk about the public key, private key and wallet address:-
Private key:- Private key is the key having fixed length of Alpha numeric words combination. It is used to access the funds inside a wallet and whoever has the private key is the owner of the funds inside the wallet.
Private key is also used for signing the transaction and it's initiation. It is somewhat similar to signing the papers in the conventional banks or like entering the password while using UPI.
An example of private key is E9873D79C6D87DC0FB6A5778633389_SAMPLE_PRIVATE_KEY_DO_NOT_IMPORT_F4453213303DA61F20BD67FC233AA33262
So you can see here many Alpha numeric words are used and it is quite hard to remember and copy the key.
Public key:- Public key is generated from private key and it is associated with a single private key. But it's reverse engineering is not possible that's why no one can retrieve private key from public key.
As the name suggests , this key is public and is used for many actions in the network. Its main purpose is to validate the authenticity of the signature. This means that private key is validated by the miners using the public key.
Crypto wallet address:- Wallet address is used to receive funds. It is having fixed length and is generated by hashing the public key. But as reverse of hashing is not possible yet, generating public key from Wallet address isn't possible.
It is similar to bank account number in the conventional banks where the bank account number is used to receive funds. And as these bank account number is unique similarly wallet address is unique and can't be same. And are used for receiving funds.

6. What is the Merkle Tree and its Importance?
Merkle tree:- Merkle tree is nothing but the data structure in a blockchain which consists the root at the top and branches and leaves at the bottom. So Merkle tree is a upside down tree in which root is at the top of the tree.
Merkle tree was Ralph Merkle and after its introduction it became a integral part of many blockchain as it helps in verify transaction easily and in a very secure way and also it increases the speed of verification.
In any blockchain data/transaction is recorded in blocks but in blocks transaction isn't recorded as a full but in the form of Hash which is a combination of Alpha numeric characters which is unique and have fixed length. But in a block there are many transaction and each transaction will have its own unique hash. And in this way we will have to keep the record of all hash of all transactions. And here Markel tree cane into play by which we can derive the hash of all the transaction at a time. And we know that in a blockchain, blocks are connected with each other with hash as every hash contains hash of previous block.
So the main purpose of Merkle tree is to derive the hash of the whole block from the hash of each transaction recorded in the block. And then blocks are interconnected with each other with this hash. And it reduces the time for verifying a transactions data.
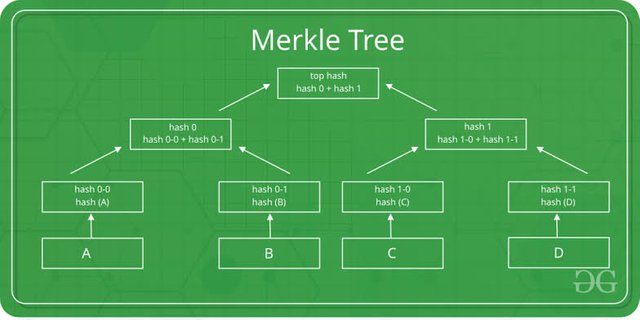
So let's assume there are 4 Transaction in a block and we have to calculate hash for the block.
For this first we have to calculate hash of A, B, C and D which is referred as H(A), H(B), H(C), H(D). And then we will calculate the hash of A and B and C and D together which js referred as H(A+B), H(C+D). And at last we will calculate the hash of A,B, C and D which is referred as H(A+B+C+D) and is called root hash which is at the top of the Merkle tree.
Importance of Merkle tree:- In a blockchain Merkle tree have many importance.
Immutable:- As we discussed that in root hash, it contains the hash of all the transactions in the block. And if any transaction is altered, root hash changes and in this way block become invalid. Thus it is not possible to alter the transaction/data in any block.
Verification:- Merkle tree make it easy to verify any transaction. If a transaction need to be verified, we will have to verify the Merkle tree containing that transaction and then to verify that perticular block is available In that Merkle tree and if that block is in the Merkle tree, this means that transaction is verified.
How verification is done:-
To verify that the tx6 is available in this block, first we have to check the hash of tx5, and then on the same side we will have to check the hash of tx7 and tx8 on the market branch. After this, on the other side on the higher Merkle tree check the hash of tx1, tx2, tx3, tx4 and at last check the hash of root that is tx1, tx2, tx3, tx4, tx5, tx6, tx7 and tx8. And if it matches then tx6 is available in the block
When the number of transaction in Markel tree is odd:-
In the above example we came to know how to create a Merkle tree when the number of transactions is even.
But can we make Merkle tree when there are odd number of transactions. The answer is yes. We can.
To make a Merkle tree of a block in which there are transactions in odd number, then we just repeat the hash of last transaction twice. But in reality the transaction doesn't get replicate just we duplicate it's hash to make a tree and in that block that transaction is present for only one number of time.
To see how Merkle tree is formed in this scenario or to gain more detail on Merkle tree you can refer to homework post of professor pelon53.
Importance of Merkle tree.
There are many importance of Merkle tree in any blockchain
It reduces the capacity to store data as in this only the root hash is stored and not hash of all transactions in any block is needed to be stored.
It enhances the security of a blockchain because it is impossible to alter any data as it will lead to change the hash of whole block. This is something called avalanche effect
It makes the computers work faster.

8. Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
In this section we will do the practicals related to the blockchain, keys and signature and we will see the results in their respective sections:-
Keys:-
As we have discussed earlier in this task that In assymetric Cryptography there are two keys that are public key and private key. These both keys are connected with each other.
Now In this Practical I will demonstrate how a public key is connected with the one private key only and for every private key , there is a unique public key.
For this I will take the help of andersbrownworth blockchain demo
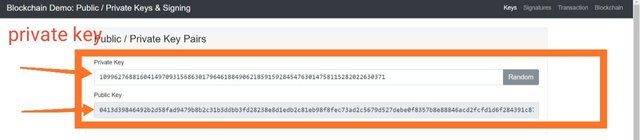
Private key:-109962768816041497093156863017964618849062185915928454763014758115282022630371
Public key:- 0413d39846492b2d58fad9479b8b2c31b3ddbb3fd28238e8d1edb2c81eb98f8fec73ad2c5679d527debe0f8357b8e88846acd2fcfd1d6f284391c87b184a0d52ba
Now as in the above screenshot you can see that there is a private key already generated and there is also a public key with it and this public key is associated with this Private key only. This means as soon as we will change this private key, the public key will get changed.
Now let's change the private key by clicking on random button beside the column of private key. This will generate a new private key randomly.
Let's see what happens next:-
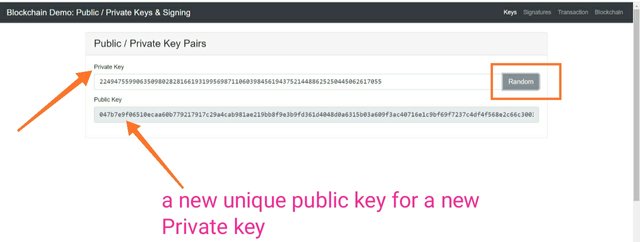
Private key:- 22494755990635098028281661931995698711060398456194375214488625250445062617055
Public key:- 047b7e9f06510ecaa60b779217917c29a4cab981ae219bb8f9e3b9fd361d4048d0a6315b03a609f3ac40716e1c9bf69f7237c4df4f568e2c66c3003e3db5f99e4d
So here you can see, as soon as the private key was changed, public key also got changed. This is now clear that the public key is associated with only one private key
Now let's take another scenario where I will select a new private key myself not by clicking on random. And let's see what happens with the public key.
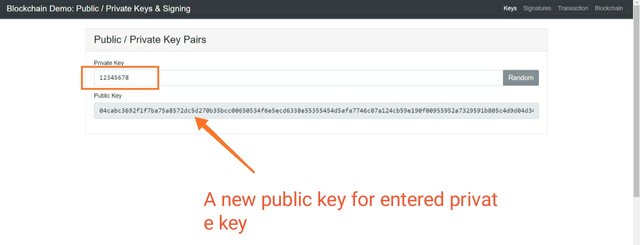
So here you can see, I entered a new private key as 12345678 and I got a new public key as 04cabc3692f1f7ba75a8572dc5d270b35bcc00650534f6e5ecd6338e55355454d5afa7746c07a124cb59e190f00955952a7329591b805c4d9d04d34abe8a803a74 which is also not matching with any other public key above.
Now I will use the private key 12345678 as my private key for signature in latter section
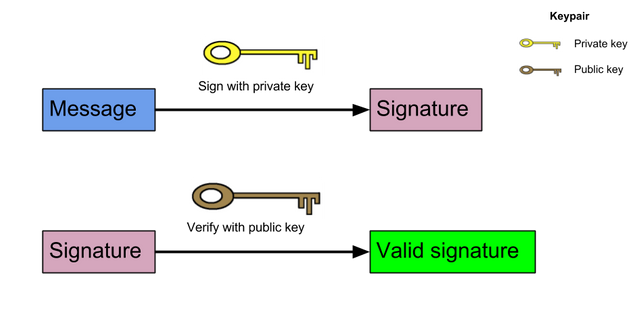
Signature
As we have discussed earlier that like the signature in any banking institutions, we also need to sign the transaction in the blockchain. Here we use our private key to sign the transaction and this generates the digital signature for that transaction.
Later that digital signature is decrypted using the public key by the miners where the transaction has to be validated. Once the private key and public key are matched the transaction is declared valid.
In in this section I will sign a message ENDGAME using my private key which is 12345678 and we will see how this message gets validated.
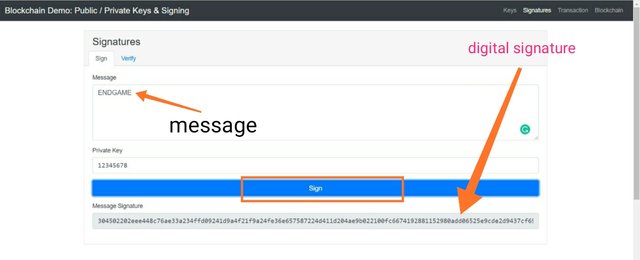
Digital signature:-304502202eee448c76ae33a234ffd09241d9a4f21f9a24fe36e657587224d411d204ae9b022100fc6674192881152980add06525e9cde2d9437cf693a27fa804008345f45e94fa
In the above screenshot, I entered the message as ENDGAME and now in this section we will see how signature works. .
So I have entered my private key which is 12345678 and has signed the transaction. Now it will generate a digital signature for this message. And this digital signature will be broadcasted to the network for validation.
Now we will see how this is validated by the miners. So now I will act as a miner.
Now to validate this signature, miner will use public key of the owner. And if the public key validates the private key this means that signature is valid.
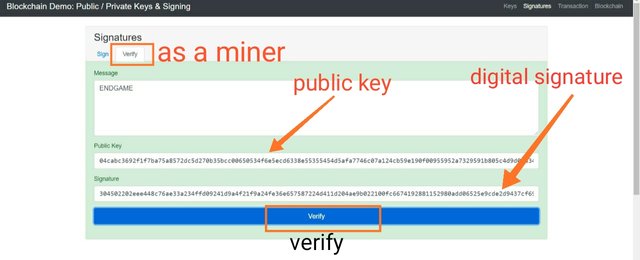
Public key:- 3045022100db88cc56190efe2a9e8565d57dd45aa8a82522a0d129d8ade786c461ac8fbbcb0220407629cee561c05fd829e90672d1deaaa081ff214e54f74aeb0db02f5eabc53a
Now digital signature will be used by the miner. Miner will enter the digital signature and public key of the owner. And after this, verify button will be tapped.
And if public key validates that the private key is associated with this, the signature will be verified.
And the background will be turned into greenish shade.
Now let's take another situation where the private key and public key doesn't match.
Now I have used the same digital signature with same message written. And now miner will use public key of the owner and will click on verify.
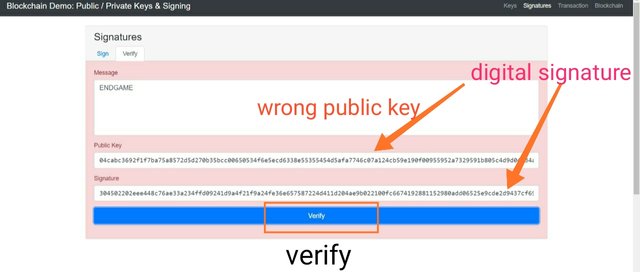
Wrong public key
To mismatch the private key and public key, I have entered a wrong public key which might be or might not be associated with any other private key but certainly isn't associated with this private key.
Now as soon as the verify button is tapped, as the private and public key doens't match, the background will be changed into reddish shade. And the signature verification will be failed.
Thus signature verification plays a crucial role in validating transaction. If the signature is verified, it is a valid transaction and if doesn't then it a invalid transaction.
Transaction
Transaction means sending asset from a address to another address. But transaction needs a valid sign from the sender and public key of sender should be Correct in order to validate the private key.
And if private key and public key are matched, transaction will be verified and transaction will be initiated.
Now let's have a look how this all things are done.
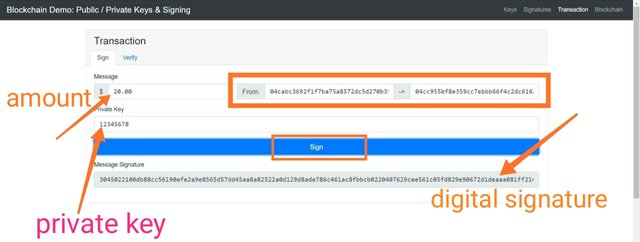
Digital signature:- 3045022100db88cc56190efe2a9e8565d57dd45aa8a82522a0d129d8ade786c461ac8fbbcb0220407629cee561c05fd829e90672d1deaaa081ff214e54f74aeb0db02f5eabc53a
First of all sender will enter the amount, sender and receiver's address and then the sender will sign that transaction using its private key which is 12345678 in my case. And this will generate a digital signature.
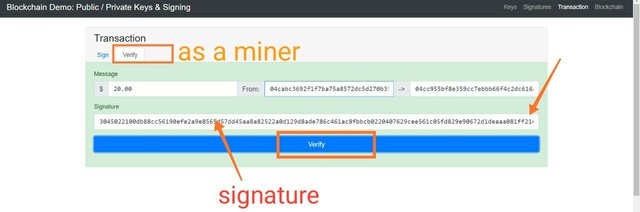
And now this digital signature will be used by the miners to validate the transaction. Now I will act as a miner to validate this transaction using the public key.
When the miner will click on the verify button, if the public key validates the private key this means signature is validated and the transaction is considered to be validated and it is initiated.
Here you can see after clicking on verify, the colour of background changed to greenish shade this means the transaction is valid.
Now let's take another case when the transaction is declared invalid when keys doesn't match.
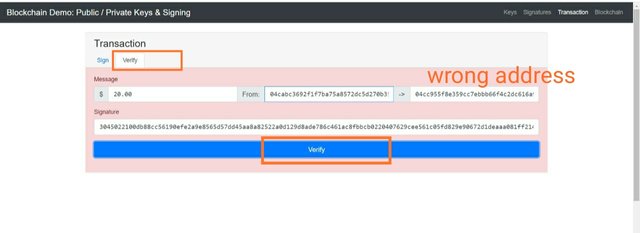
Now here in the receivers address, I have changed some digits and now it's a changed address.
When the digital signature will be verified.
When we click on verify, the background changes to reddish shade this means signature verification is failed and transaction is invalid.
Blockchain
As we know that data in blockchain is stored in blockchain and all the blocks in blockchain are connected with each other forming a blockchain. Every block has data, hash and hash of previous block. And these hash and previous block hash connects block with each other.
Every blockchain has 1st block having hash 00000000 that is known as genesis block.
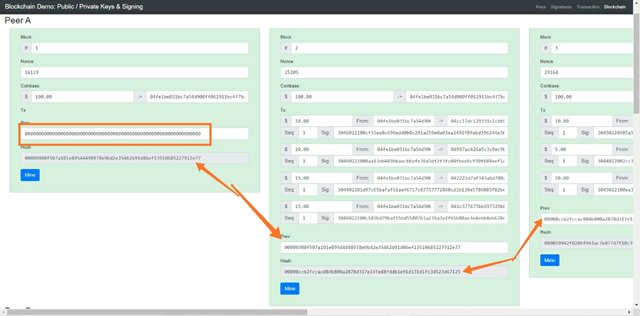
Now as you can see in the block 1 section, the hash of previous block is 000000 which is the hash of genesis block. Similarly block 2 has its own hash and it also has hash of its previous block which is the hash of block 1 and this joints these two blocks.
Similarly block 3 has its own hash and it is connected with block 2 as block 3 has previous hash which is the hash of block 2.
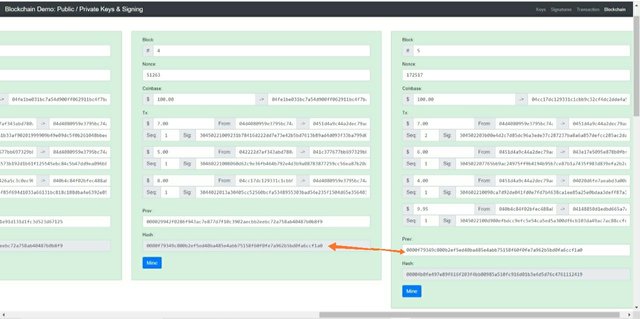
Similarly you can see in the above screenshot that block 4 and 5 are also connected with each other using the hash and previous block hash. And this connects all the blocks together and form the blockchain.
Along with hash, there are many data stored in a block such as amount, sender's address, receiver's address, and signature too.
Now as you can see all the blocks have greenish shade this means the blockchain is intact.
Now let's try to change data in a block and let's see the consequences.
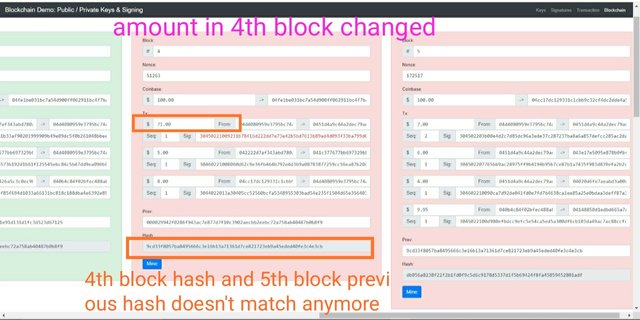
Now as you can see I have changed a transaction stored in block 4. I have changed the amount from 7 USD to 71 USD in a transaction.
Any chance in the transaction will lead to make the signature invalid and the hash of the block will be changed.
As the hash of block 4 will be changed now in the block 5, the previous block hash will not match with any other block thus these two blocks will now be invalid and the blockchain will break.
Now to make those block valid, we will have to mine those blocks again. Mining block will lead to change the hash and nonce of block 4 and 5 and thus these will be again make a perfect blockchain.
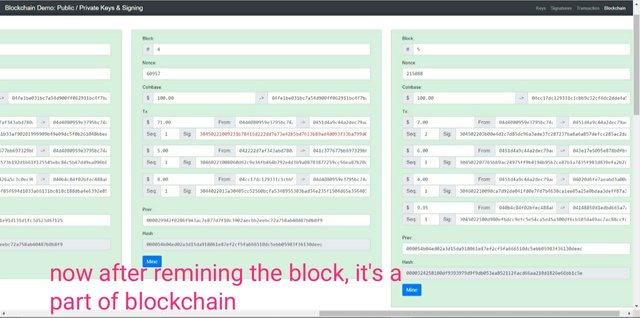
Now to mine blocks again, click on mine and then block 4 and 5 will have new nonce and new hash.
As you can see now the nonce of the block 4 and 5 has changed to 60957 and 215088 from 51263 and 172517 respectively.
Now as you can see that again the block are having greenish shade this means the blockchain is now perfect.

conclusion
So in a nutshell, we can conclude the whole homework, we discussed what is cryptography and how it is useful for any blockchain and how it keep the blockchain safe and establish secure connection between sender and receiver.
We also discuss type of cryptography that is symmetric in which only one key is needed for encryption and decryption and we also see pros and cons of this type of cryptography. And assymetric Cryptography in which public key is required to encrypt the data and private key that is associated with that public key is required to decrypt the data. This takes the encryption and decryption at a whole new level as no one can see your data without your private key.
We also discuss what is signature cryptography l, Wallet Cryptography and blockchain cryptography and we discussed all these in detail.
We also discuss how Wallet address, private key and public keys are associated with each other and with the one wallet only. And how public key is needed by the miners to validate the authenticity of the private key.
We also came to know why the wallet address, private key and public key of two different wallets can't be same and we also discuss the reason behind this
We learnt how private key is used to sign any transaction or data and how public key is required to authenticate that signature.
After this we discuss how Merkle tree is used to make computer work faster and how by using it blockchain uses less storage capacity to store the data of transactions in the block. And how it is useful for verifying any transaction is present in a block or not.
We also get to know how to make Merkle tree and I also referred a task from where you can se the whole detail about the Merkle tree.
And in the end, we practically demonstrate how the private key and public key are associated with each other and how these are required for signing any transaction and what happens when public key is wrong.
We also practically demonstrate how block and then blockchain Cryptography works. And what happens when the data inside a block is altered. And if it's not possible to alter then what can we do when we need to change that data that is by mining the blocks again.
So thats all from my side. Hope I was well understood.
In the end I would like to thank professor @stream4u for this amazing homework which enables me to see the working of a blockchain more closely.

Cc
@stream4u professor
.png)
.png)
.jpeg)