Crypto Academy Season 3 | Advanced course : Let's Open The CryptoGraphy | For Professor @stream4u

Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
Let's say that John has a friend let's pretend like John and his friend are on different sides of the world. John has an important message to send his friend but because John is on the other side of the world he can't just hand his friend this message. Let's pretend like this message that John has has some secret information that he only wants his friend to know about and nobody else. If John sends his letter to the friend around the world there's going to be a whole bunch of people that will be handling this letter. So, there's a risk that as John sends this letter somewhere along the way the letter may be intercepted by somebody other than John's friend. If this message falls into the hands of the malicious person, that person may read the confidential message sometimes. That fellow will keep the letter or he could take note of that useful information his selfish interest. Then, continue to pass the letter on to John friend. How can John and his friend be sure that nobody in between has uncovered the secret message. That is where cryptographic come in.
One thing John could do is he could use cryptography to encrypt the message. That way if somebody in the middle got the message, they would be unable to understand its contents. So, when John first writes the letter he writes it in English because that's the language he speaks so if Paul wrote his letter in English, Spanish, Chinese. We would consider that this message is written in plaintext. So, if the message is written in plaintext that means it's very easy for anybody who speaks that language to understand its contents. So, what John needs to do is he needs to encrypt his message before he sends it.
What does it mean to encrypt a message, let's assume that John's secret message is the word fun he does not want anybody other than his friend to read this secret message. Anybody that speaks English can read the letters F U N and understand that John is trying to send the message fun to his friend. In order for John to encrypt the plaintext fun he converts the letters fun and two numbers. Then, once his message is in form of numbers he can use a key to secure the values of this number. We can think of the key as mathematical operations that we can perform on the numerical value of John's message. After applying the key to this numerical value, we end up with a new numerical value which is known as ciphertext. Now, if Paul puts his ciphertext in an envelope and sends the envelope to his friend John won't have to worry about somebody in the middle discovering the secret message if somebody in the middle discovers the message they won't be able to decrypt the message without a proper key. Now, if the message continues to John friend, John's friend will need a way to decrypt the message and recover the original plaintext. In order to convert the cipher text into plaintext John's friend needs to decrypt the ciphertext. In order to decrypt the ciphertext the friend will need a decryption key, using the decryption key the friend will be able to convert the ciphertext into the numerical value corresponding to the plaintext. Once John's friend has the plaintext value, he can transform it back into the original message. Now that the numerical value is converted back to the English language, the friend has retrieved the original plaintext that was sent in John's message. That is how cryptography works
We have blockchain platform such as:
EOS
Stellar
Ripple
Qourum
Zcash
You can derive a public key from that random number. A public key can always be derived from a private key, if you lose your public key you can always regenerate it or recalculate it from your private key but you can't go the other way without the private key, you can't generate that from a public key. So, no one can find out your private key by only looking at your public key. Now, public key is also known as addressing cryptocurrency. So, if you have a Bitcoin address or a fear address or a JC, ERC 20 address, that is a public key.
Private and public keys are used for data signing. let's have a look at an example of how that works.
Let say we've got a private key at 1 2 3 4. This can then be used to generate a public key. In this simplified version, all we're doing is doubling the number. So the algorithm we're going to use for this to sign data is to double the private key and then add on the length of the message. So, we get numbers we can then send this transaction to the other person. That person has a method or a function to verify this data. He knows that the person had the private key that derive this public key send this message.
In cryptocurrency, we use this to sign transactions
When funds come into your public key address, we can then create a transaction which is just data. We sign that with the algorithm and we send that off to the nodes in the network. Nodes verify it before they write the data to the block. If the majority of nodes agree that the data verifies and the block is completed with that transaction. Then, the funds are transferred and the blockchain continues.
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
The idea is that, i have a document or a message or something that i want to send you and i want to prove that it was me that sent it. So to do that i'm going to use my private key to sign a digital signature.
Basically, what you're going to do on your end is verify that signature and verify that it was actually me but encrypted it. That's the idea. So, when we perform this process what we tend to think of is the person that's doing the signing and the person that's doing the verification.
So we have the signer and we have the verifier. We've got some document or message. This document is not currently encrypted and we're going to send it over to the verifier. This right as part of our conversation right. Now the problem with that is there could be someone in the middle changing this document or forging it. This could be a fake document. We don't know that it's come from me. This is over the internet.
If we had an encrypted connection where we knew we had we each had a key that would help but we've still got the issue of how do you do this when you establish the key and during the initial handshake and things like this
Digital signatures form a big part of these kind of systems because at the beginning at least you're going to have to prove one of the identities at least.
So, what the signer is going to do is create a digital signature. So, they're going to take the document and we'll just simplify for a minute and then we'll build up a little bit of of sort of information. In a while right and they're going to encrypt it with their private key. They're the only ones that could have done that because they only they're the only ones that have the private key. Then send the signature over to the verifier right over the internet and the verifier can perform this verification process.
So, they can say what if we take this signature and we decrypt it with the public key. what if we do take this and we decrypt it with the public key because remember they reverse one another and then we can sort of work out whether the document and the signature match because if it was the original document that was encrypted using a private key that original document is going to pop back out again. Then we can verify that that's actually taken place.
Explain what is Symmetric and Asymmetric cryptography?
Symmetric Cryptography
Symmetric encryption is where we have one secret key as applied to a plaintext for normal original text to create the scrambled up ciphertext. So, there are got two parties in this communication. We have receiver and the sender's trying to send plaintext to receiver. I've got a key of two. This means receive also needs to have the key of two. They need to know the secret key. So, the idea is this key is kept secret just between these two people. everyone else shouldn't have access to his key. So, the same key was doing the hard work essentially and this means both the sender and receiver need to have this key.
Asymmetric Cryptography
Asymmetric encryption use two different keys. One of these key is public key, which is available to absolutely everyone who wants it. Then, you have a second secret private key, which only one party knows about. The fact we've got a pair and we have this asymmetry is because if you encrypt the data using a public key it can only be decrypted by the other key. For private key and the same applies to every way around. Data encrypted by the private key could only be decrypted by the public key.
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
We have the Bitcoin address which is labeled as share and you have a private key which is labeled as secret. The relationship is that the Bitcoin address is based on a public key which you can share with anybody while the private key is secret because the private key is what enables you to spend any bitcoins that are sent to the Bitcoin address. That is a relationship between the public keys and the private keys in Bitcoin.
We have three main different categories of wallets. We have a hardware wallet in cryptocurrencysoftware wallets for mobile and desktop, and paper wallets. I'm going to talk about what those three kinds are.
Hardware Wallet
A hardware wallet is an example of a wallet that lives within its own hardware space seem as a very secure wallet. So, whereas atomic decks is an application a piece of software that sits on your desktop. A hardware wallet is some code that sits on a physical device that's separate from whatever your main digital device may be. This example we're talking about Trezor. Which is one of the really great hardware wallet options out there. It's usually secured with a pin and its own password on top of your normal cryptographic security that you have for your public and private keys. This means that if somebody gets a hold of your laptop or you pick up a piece of malware that's seeking your wallet or anything that's associated with keys that it can't find a software wallet on your day-to-day use machine. So, it's a very very secure wallet in that sense.
Paper Wallet
A paper wallet is something that you end up storing a printed piece that you store your seed codes and maybe even a QR code that's associated with your private keys. This is a he idea here is that you have a completely offline method that is basically digital proof for having to be able to interact with. So, if you want to store some coins for a very long period of time, you don't want to mess with them, you don't want them to be online at all, you don't even like want to necessarily associate your saved keys in a digital format. Then a paper wallet is your choice for that.
Software Wallet
Software wallets are pretty much what their name implies, they are a wallet that is built out of a software application whose goal is to be able to give you direct power over your keys for your coins.
What is the Merkle trees and What its importance in blockchain?
.png)
Another way of calling a Merkel tree is what's know as hash tree. It's actually tree composed of hashes. A cryptographic hash is a digital fingerprint of a certain amount of data. You take a very extensive amount of data and narrow it all down to a single cryptographic hash. A Merkel tree is actually a structure built of all the hashes combined.
The first step of forming the Merkel tree is to perform a hash, on each of the transactions. We put each transaction through a hash function to get the transaction hash or the transaction ID which is useful in itself for identifying a transaction. We take our transaction IDs or our transaction hashes that we've created and then we put them into pairs and we perform a hash on that pair of hashes. Then once we've paired them up and hash them we pair them up again and hash them again and we keep doing this until all of the transactions just meet at a single hash. This single hash is called the merkel root to the root of the entire Merkel tree.
Importance of Merkel in blockchain
Merkel is very important to the blockchain because it easy find if any transactions are tampered with, uses very few resources to check any fraudulent action, and easy to add new transactions to the block.
This allows for simple payment verification, and the new nodes need not download the whole blockchain but only the block headers of the longest chain. Merkle trees help the block to unchangeable and also help to maintain the integrity of the blockchain
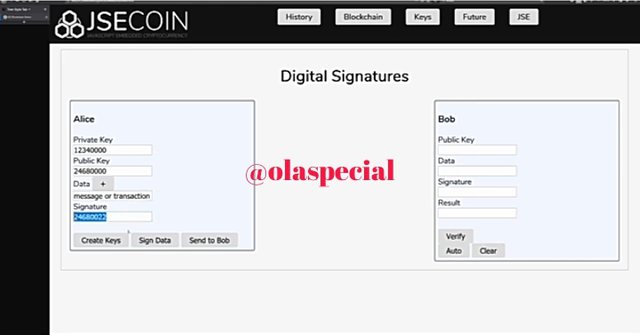
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical.
Any number could be your private key. You can just type in any random number for your private key. The more you add numbers to your private key, the more it generates a new public key. As the word imply, it means you can share the public key with anyone. You don't have anything to be afraid of because the private key can't be generated with the public key.
We have a private key of 12340000. Then we use to generate our public key. The argorithm going to use is double our private and add the lenght of the message.
So, our private key is 12340000 and we generate our public key from it which is 24680000. The add the length of the message which give 24680022.
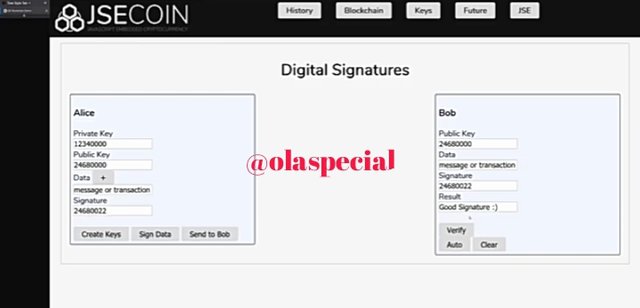
The person on the other end verify it by calculating the public and the data. If the person verify the signature and it is a good signature. Then the person will know that the person that have the private that derive the public key.
Cryptography method has been in used from the past to secure information. The symmetric cryptography is a good method to secure a message of it is not very good enough due to the fact that you have use the same key to secure your message. If you have to send it through the internet, it is not secure because ease might find a method to steal. But the best way to deliver the key is through face physical contact and that is a huge disadvantage because the person be living in the other side of the world. Asymmetric cryptography is the best method because both parties will have their separate keys. Hardware wallet, software wallet and paper wallet are good but paper wallet is better because it is completely offine