Steemit Crypto Academy, Season 3: Week 2 || Hash and Cryptography.
After reading the content posted by professor @pelon53 I understood more about the usefulness of both HASH AND CRYPTOGRAPHY and I was able to give back base on my understanding what the professor taught in my own words.

Explain what does the resistance to collision mean? And what does resistance to preimage mean?
HASH
Hash is a function that mathematically convert a block that has smaller or larger amount of information which is summarized in a single hash, hash helps to keep track of transaction saved on the blockchain technology hence, hash are not to be underrated as they are of great use to the block chain technology in other words, hash are fixed alphanumeric characters that are unique and unrepeatable, they are very safe, irreversible, efficient and they are of fixed length.
Hash functions works like taking input of words regardless of the file size or length and convert all into a single hash as an output of fixed length, such act like security, checking the integrity of messages or data, authentication of information are importance of cryptography with the help of hash function.
Hash function has been in existence since 1961 after which numerous cryptographic hash functions were created like MD2 in 1989 until the existence of the MDs to MD5, but in those years security wasn't so important hence, the creation of European RIPE project was born in 1992 where various version like RIPRMD- 160, RIPRMD- 256 and RIPRMD- 320 are currently used and the cryptographic function are very secure.
In this era, the SHA which is known as the (secure hash algorithm) is one of the most used series of hash function created in 1993 by the NSA which are SHA-0 and SHA-1 and others but the SHA-256 is the cryptographic hash function used in Bitcoin blockchain technology and it is one of the most used hash function, regardless of the input size in the case of SHA-256, the hash function output is also a fixed length with 64 alphanumeric characters either small or large input file the characters will always be 64, properties of hash function are collision resistance or resistance to collision, resistance to preimage and second preimage resistance but for this homework i will be explaining according to the professor @pelon53 question, which brings us to what,
RESISTANCE TO COLLISION
Collision is when two things collides but in the case of hash function, collision can only occur when two different input generate the same output. Resistance to collision is like, not allowing the production of same output of two different input, it is almost impossible to avoid collision whereas there is a very low chance that collision can occur in resistance to collision that is if the chances was given.
In other words, finding two input that generate the same output in resistant to collision has a very low chance but there is no resistance to collision or hash function without collision but in the case of SHA-256 which is a very strong hash function, collision hasn't been seen or recorded in this hash function.
Resistance to collision is a hash function where two different input could slightly produce the same output if the chances are given. however, two different input should produce two different hash.
RESISTANCE TO PREIMAGE
Preimage resistance is defined as the hash property where assigned data that produce a hash can slightly possibly be found but with a low possibility, it is not 100% impossible to map out the ascribed data that produced a hash, as we can see cases where an attacker can guess the what the input is by observing the output
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
Using tronscan to verify the hash of the last block and the hash of that transaction.
Click on this tronscan https://tronscan.org/#/
- Click on the three parallel lines at the top right corner
- Click on blockchain
- click on blocks
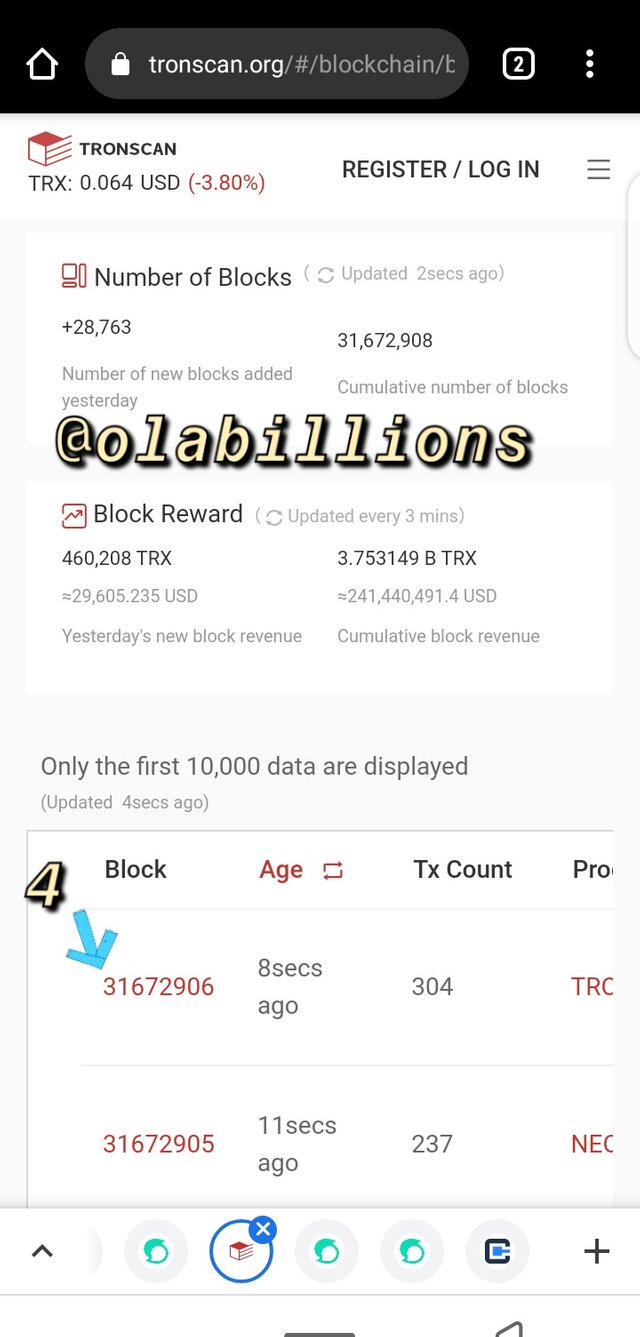
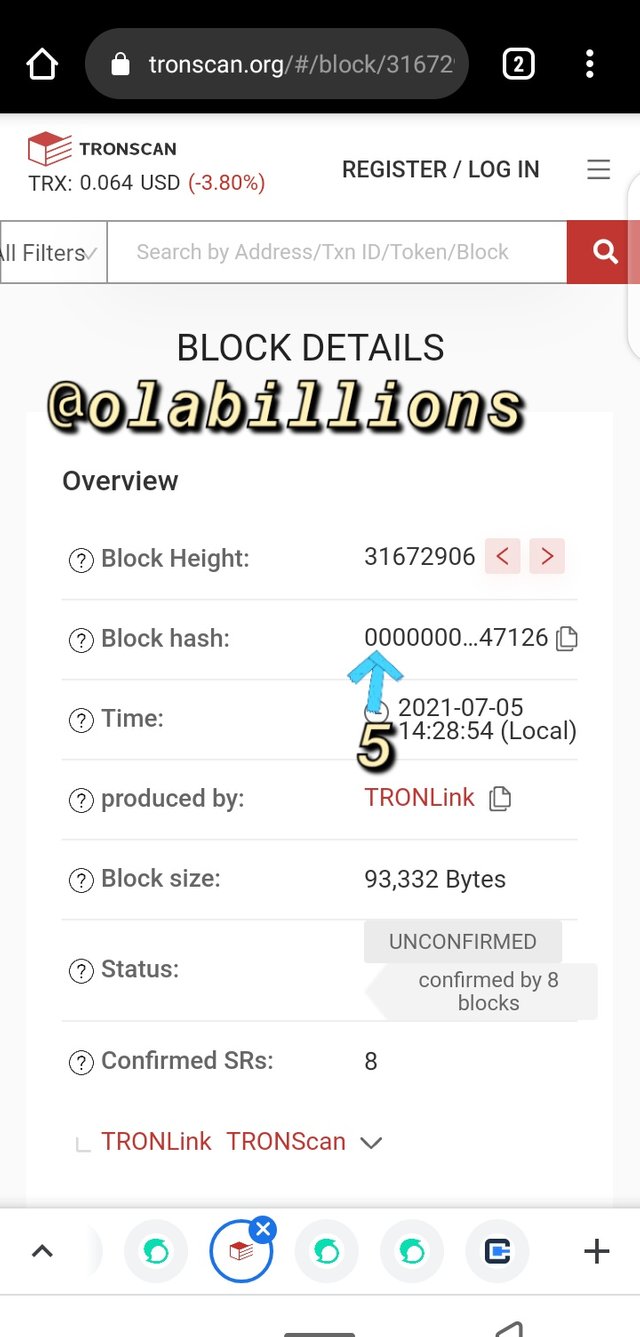
- In this page you see numerous tron blocks due to the number of fast ongoing transaction, as at the time of viewing the last block height was #31672906 and the block hash was 0000000001e34a4ac8d73593108fb96e04aae7d32416b50ad95fa5bda2447126
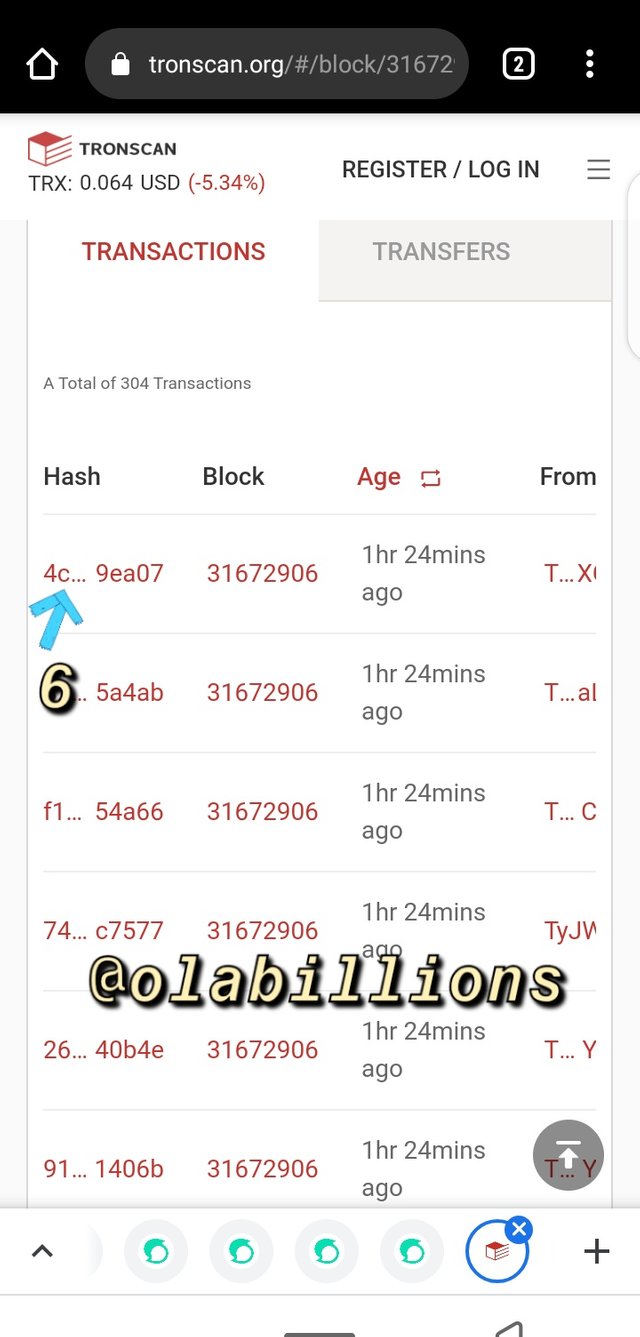
- So to verify the hash of the transaction, scroll down, then you see transaction,
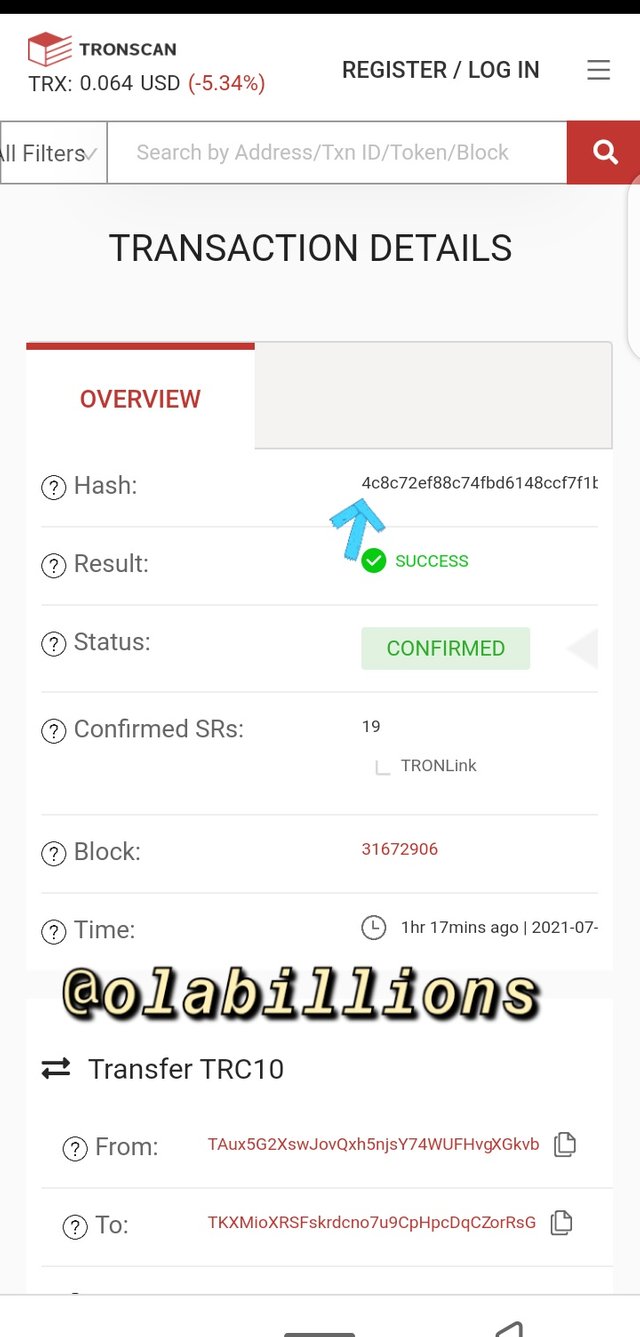
- Click on the block height and it will review the hash of the transaction.
4c8c72ef88c74fbd6148ccf7f1bc5c671d34030fe080d5fb693e91ed4749ea07
This link will direct you to the aforementioned detail of the block transaction.
https://tronscan.org/#/block/31672906
Using etherscan to verify the hash of the last block and the hash of that transaction.
Click on etherscan website https://etherscan.io/
- click on the three parallel lines at top right corner
- Click blockchain
- Click view block
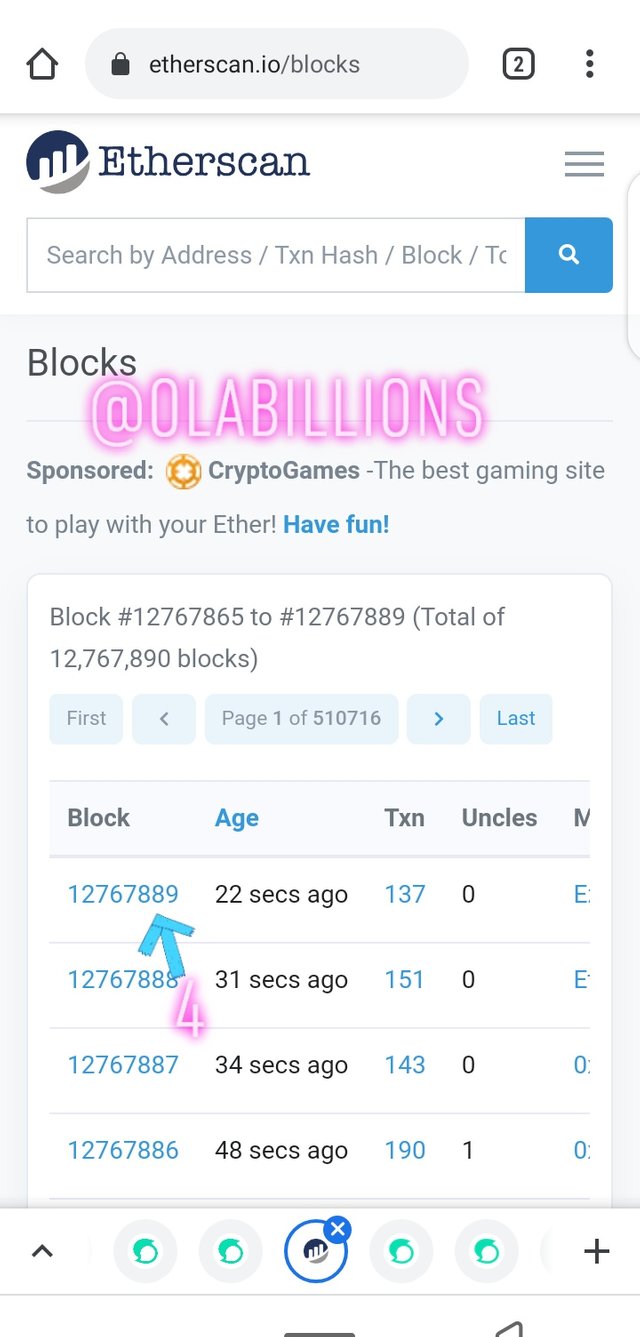
- Then the latest block will be seen which is #12767889 then click on the block height and scroll down to view the hash of the block
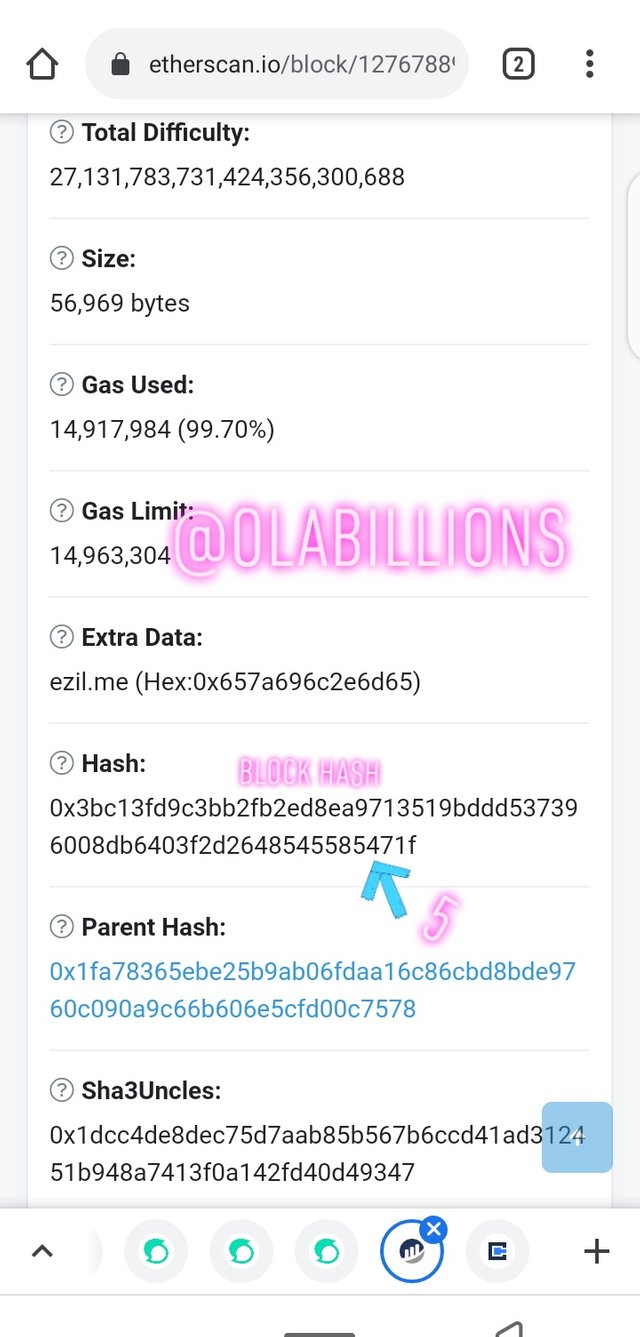
Block hash
0x3bc13fd9c3bb2fb2ed8ea9713519bddd537396008db6403f2d2648545585471f
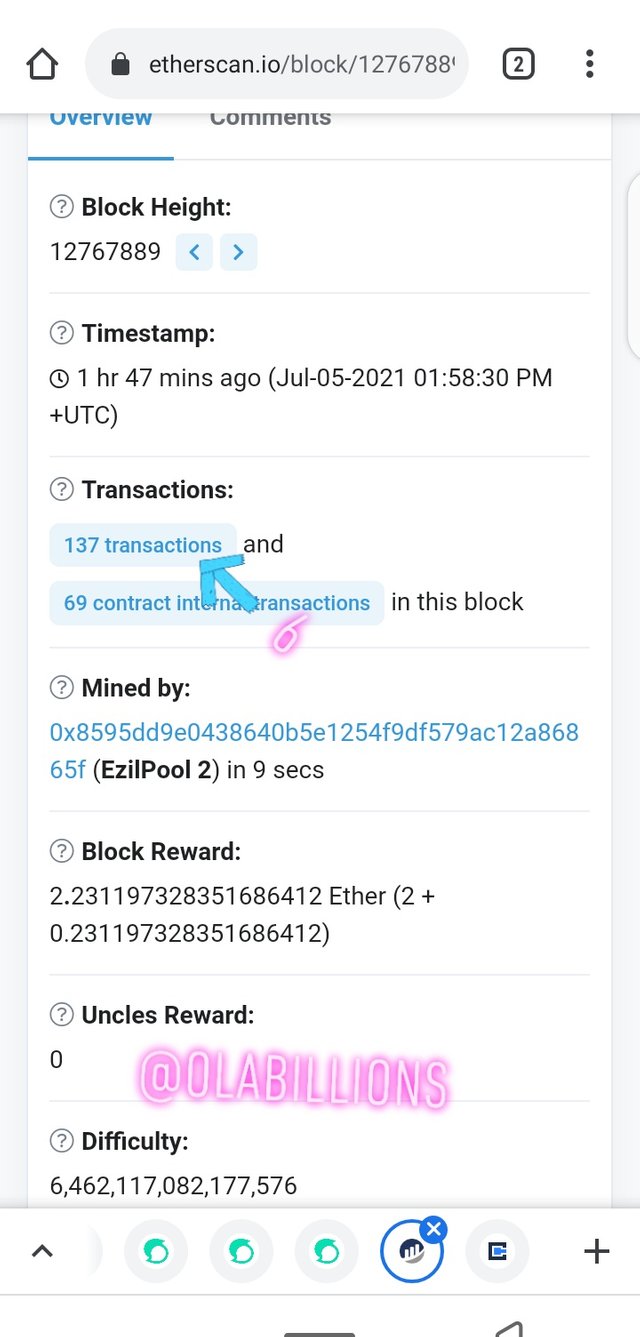
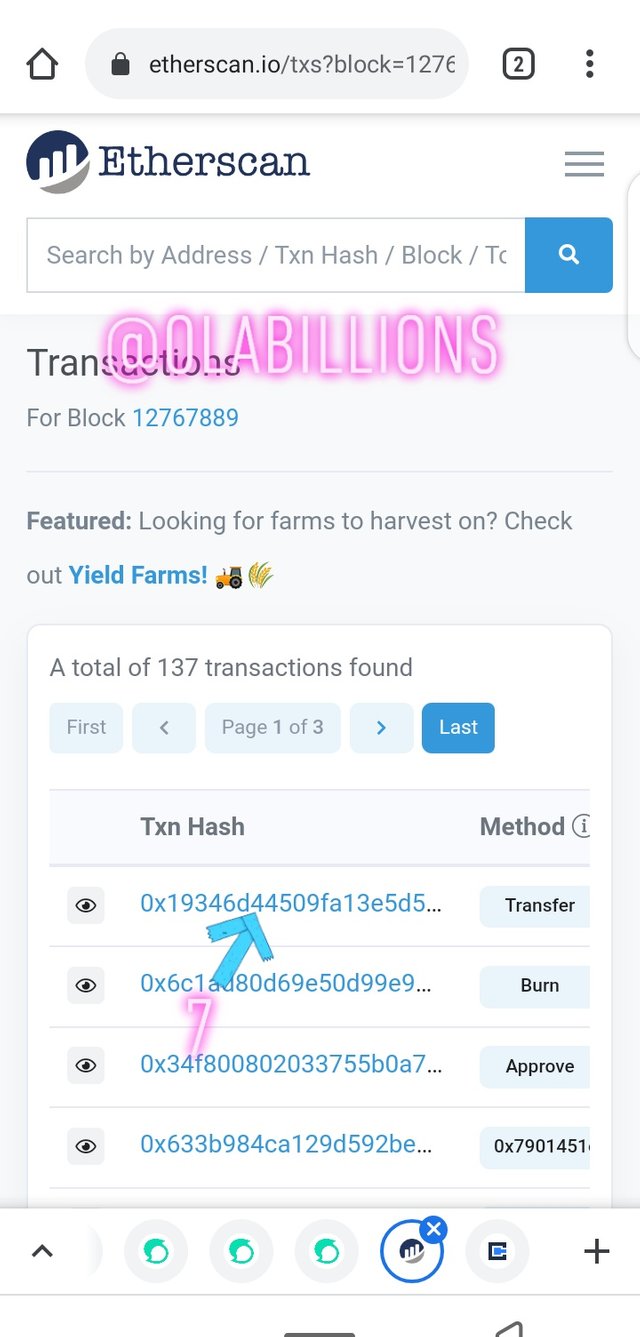
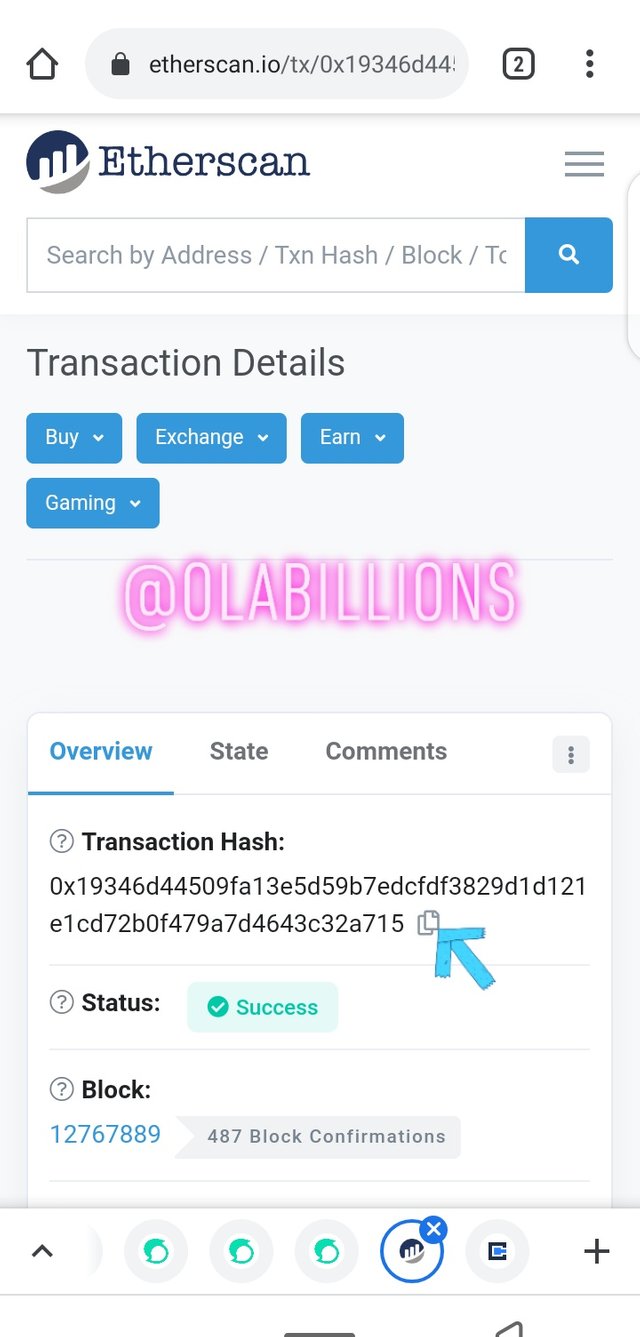
Scroll back up click on transaction, there you can see the number of transactions in the block so I click on the last transaction as asked by the professor.
To verify the hash of the transaction click on transaction and the details of the transaction will be seen.
Hash of the transaction
0x19346d44509fa13e5d59b7edcfdf3829d1d121e1cd72b0f479a7d4643c32a715
https://etherscan.io/block/12767889
Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
To simply generate the hash of the following words (CryptoAcademy and cryptoacademy) using the SHA-256.
The link used is as follows
https://passwordsgenerator.net/sha256-hash-generator/Put the first word(CryptoAcademy) in the space and generate the hash
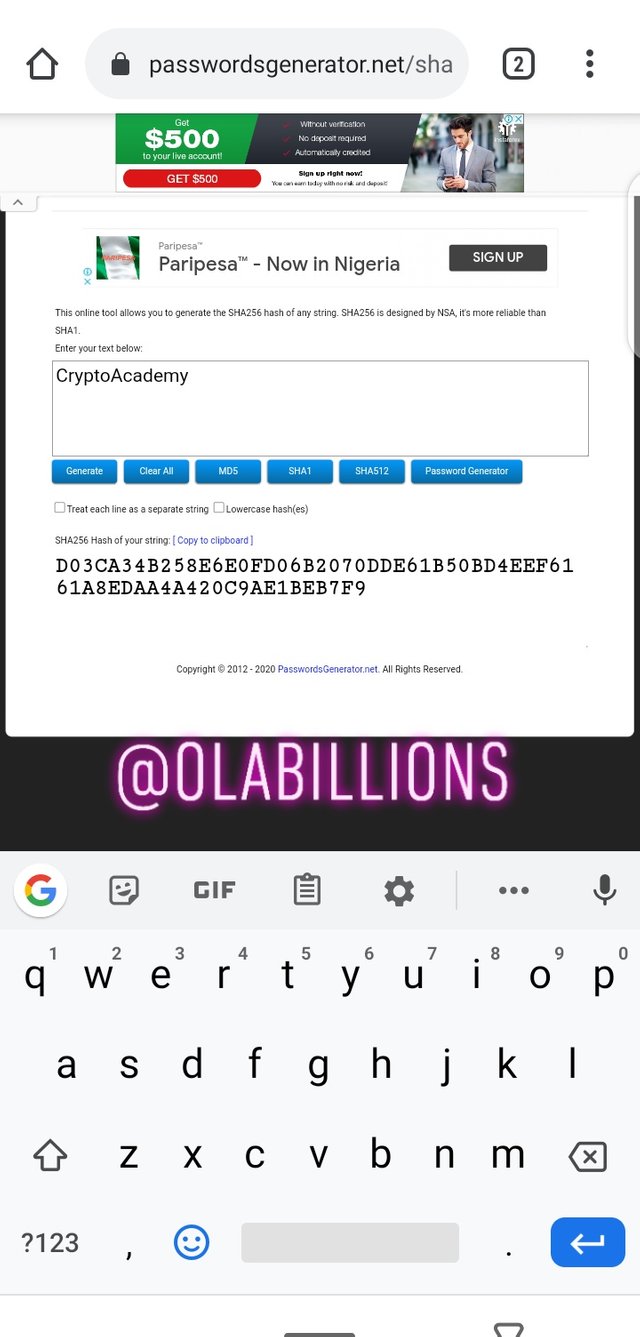
- The hash generated for the first word (CrytoAcademy) is
D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
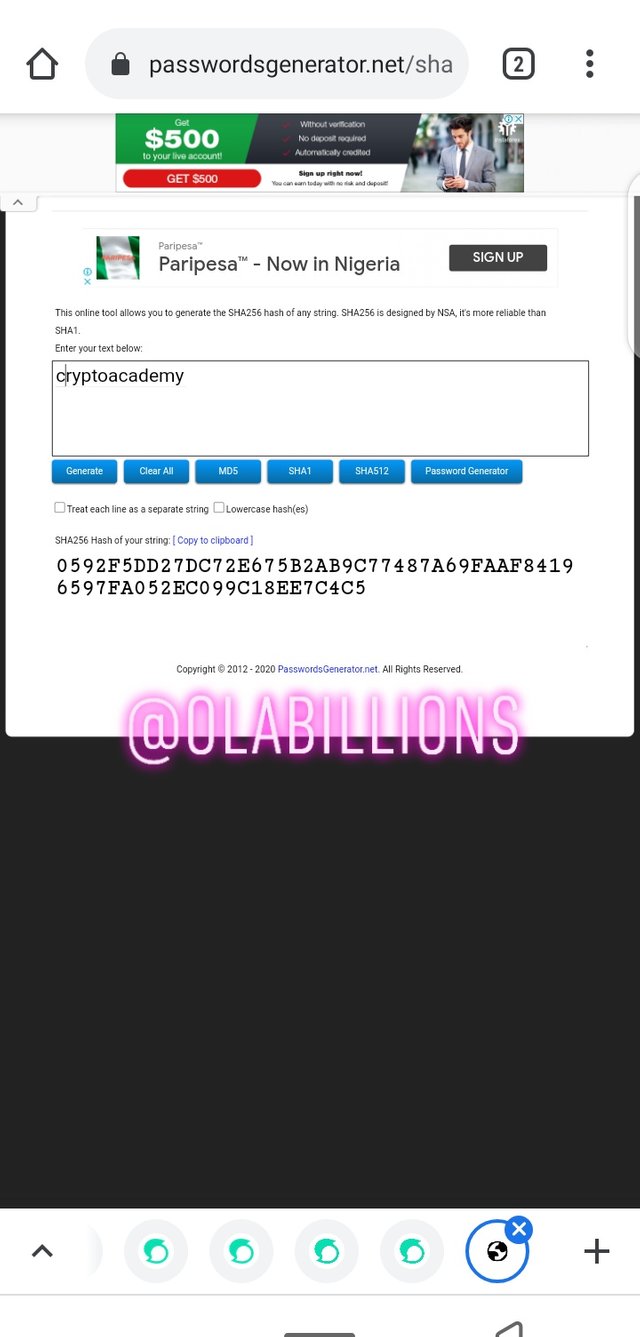
Put the second word(cryptoacademy) in the space and immediately the hash is generated
The hash generated for the second word (cryptoacademy) is
0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
In the practical shown above you can see that the generated hash are different even though they are the same words but the input a different,
The first word which is CryptoAcademy has an uppercase of C and A which makes it generate a different hash.
While in the case of the second word crypto academy the input is of lower case which brings the result of a different hash.
One of the basic function of hash property which is resistance to collision is something that was experimented above words can be similar but a little difference in words will equallly generate a different hash, it is impossible to map two imputs that will give us the same output in other words different words can give the same result.
In your own words explain the difference between hash and cryptography.
To avoid repetition the explanation of hash as been given before the first question.
CRYPTOGRAPHY
The alteration of information for beneficiary reasons or harmful purpose without authorization is prevented by cryptography, preserving data and information are the basic aim of cryptography, it uses security pattern and keys to safeguard data. Cryptography is one of the foundation of block chain messages or data can only be interpreted by users with the key hider the sender or the receiver.
Cryptography can be used to encrypt a group of data, messages or file using a key, this key must only be known by the sender and the receiver. In a case whereby this key is leaked to a third-party, hence the encrypt information or data can be decrypted therefore it is advisable to ensure the key will be of long length so that the decryption will be difficult.
In some cases, cryptography uses a public and a private key, the public key can be distributed among users in need of it but the private key should not be disclosed. note, both the private and public key at different so by safeguarding the private key, data encrypted cannot be compromised and can only be read by the person with the private key. This cryptography has a very good security and also each pair of keys are so unique, cryptography in this form can be known as asymmetric cryptography
The use of decrypting message very fast and quickly is known as symmetric cryptography and the asymmetric cryptography which is very secure, both advantages unite to form a hybrid cryptography in the sense that the encryption and decryption of files or messages in this form will need speed and security.
| HASH | CRYPTOGRAPHY |
|---|---|
| Hash code has a fixed length | cryptography codes present different length with the increase in information |
| Hash data cannot be retrieved | cryptographic data can be retrieved by a second party with the key |
| The use of keys are not required in hash | keys are required in cryptography, in some cases private key and public key and required |
| All ash and no cryptography | all cryptographic hash functions |
CONCLUSION

Hash has brought ease to the blockchain technology, hash function is unique and unrepeatable, in the sense that, two input cannot produce the same hash output, a slight change in an input will generate a different hash output.
Fixed length is another characteristics of hash function no matter the file size of input the hash output will always be fixed, the irreversibility is another characteristic whereby a hash output cannot be converted to he data that originated it. Cryptography encrypt data and safeguard information from users that has no authorisation to open the file, cryptography is very essential with the use of keys, keys are used to generate information in cryptography and also to keep data or file secured. In cryptography keys are to be kept saved because if revealed, the key can be used to decrypt information.
Both hash and cryptography are both useful in the world of blockchain technology and cryptocurrency as they both encode data and safeguard information.

.
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Buen trabajo, bien explicado, felicitaciones.
Recomendaciones:
Mejorar la presentación, hay momentos que no hay una buena secuencia. Mezclas los captures de pantalla con el texto.Calificación: 9.0
Hello @olabillions, your post has been supported by @ngoenyi, the country representative for Nigeria. Keep sharing original and quality contents.