Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u | Let's Open the Cryptography
Hello everyone,
In this post we are going to learn about Cryptography in depth as discussed by professor @stream4u in his lecture.
1. Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Blockchain Cryptography
Let us discuss both terms Blockchain and Crytography,
I hope everyone must heard of word Blockchain if you tries to know about cryptocurrency. Basically, Blockchain is technology on which crypto network works, it is technology which keeps the record behind the crypto network. It is a kind of database. For better understanding of Blockchain we first learn about database. Database is basically a collection of large amount of informations which is easily accessed and manipulated by a large number of user at once.
Blockchain is store house of this database. Blockchain mainly stores database in form of blocks which are linked together through chain network. When ever a new data comes it is chained into the previous block. This process of adding new block in blockchain goes on and on.
Cryptography
This word is made up from Greek language
Cryptography = kryptós(means, hidden/secret) + graphein(means, to write)
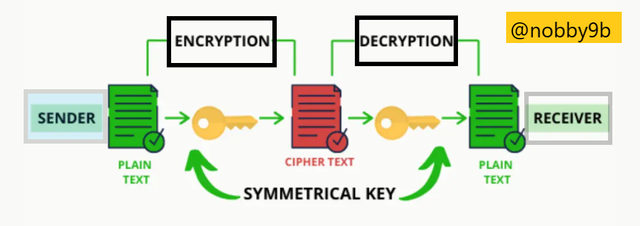
It is the technology which is used to secure communication between any two person who are using an third party. Using this technology only sender and receiver will know the message. This process is done by using encryption and decryption. First, message from sender is encrypted into some code and this message only be read when it is decrypted which requires private key.
The primary purpose of bringing cryptography to blockchains is to secure its participants, transactions. If we understand blockchain cryptography through example then radio communication of 2 army soldiers is an great example. This communication between two soldiers is highly secure and encrypted and only these two soldiers can know the information.
Similarly, Blockchain cryptography is used to secure its users and tranactions on blockchain. Cryptography in blockchain mainly use encryption key algorithm. In encryption key algorithm , keys ensure that nobody other than sender and receiver will able to read the message or information. The sender of message encrypt message with a key and receiver requires the same key to get message decrypted. Over the years many other tools emerged for cryptography in blockchain and some of them are hash functions, digital sigantures.
Blockchain Platform
Platforms which use blockchain techonolgy are known as blockchain platforms. Some of the examples are:
Ethereum
EOS
RIPPLE
FANTOM
and many more.
2. Explain the Public Key CryptoGraphy.
Public key is a part of the asymmetric key algorithm of cryptography. Public key is published such that it can be seen by everyone in the world. It is a public shared key made up of alphanumeric codes which are hashed and produce address for different crypto wallets deposits. The main algorithm used for generating publc key are :
Rivest-shamir-adleman
Elliptic curve crytography
Digital signature algo
Public key is string of alphabets and number, used to encrypt the plain message into coded form known as cipher. Public key has a unique private key which is used to decrypt the message which is encoded by public key.
Public key is a verification tools for digital signature done by user using private key. This verification is done before adding a new block.
Application of public key
Used to secure web server
For digital signs
For identity authentications
3. What is Private Key Cryptography?
It is another part of asymmetric key algorithm. Similar like public key it is a random alpha-numeric code generated from numers and alphabets. This key is secret and only known to the user. It is very important to keep this key private and secret to keep your assets safe into your wallet. Private key the meant for only user so it is advised to not share them with any other person.
Private key comes to use when you want to send your assets to some other person then you require your private key for that purpose. Private key is used to digital sign transactions which later requires public key for verification before adding transaction to block.
4. Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Digital signature concept coems into existence in 1976 by Martin Hellman and Whitfield Diffie.
Digital sign are very similar to the physical signs their main purpose is to verify originality of message. Digital signatures are used to verify digital message.
Digital signature is used in cryptograhy. They provides an extra layer of security to information sent by any third party. Digital signs adds user's signature to transaction using private key and broadcasts it into network. Afterwards, before adding transaction to block , the transaction is verified using the public key associated to the private key of same user.
The complete process of digital cryptography sign includes two process:
Signing the transaction : This is done by using user's private key before message is transmitted.
Verification : This is done by miners to verify the authenticity of transaction by using same user's public key.
Private key is used to sign the message for encryption and Public key is used to verify and decrypt the encoded message.
Application/Advantages of Digital Signatures
For authentication
Digital signed message can not be manipulated
Non - repudiation means user can not deny in later time if he signed message.
It is easy to sign a large amount of data at once.
5. Explain what is Symmetric and Asymmetric cryptography?
In today's cyber times, financial or payment data is very vulnerable, due to this user's personal details can be revealed. Due to these reasons, cryptography is very critical for securing user's personal data as transactions happens every minute of day. This is the main reason why cryptography is very important. The two main type of cryptography are :
Symmetric Cryptography
Asymmetric Cryptography
SYMMETRIC CRYPTOGRAPHY
Single key , Secret key , One key, Private key encryption are another names which are used for symmetric cryptography. This cryptography uses one single key which is shared to all parties which is used for encryption/decryption of data.
In symmetric cryptography we use a secret key which is used for encryption and decryption. This is exactly opposite to asymmetric cryptography, which use one key for encryption and other key is required for decryption. In symmetric cryptography, Data (message) which is transmitted can't be understood by somebody who do not hae the same secret key which is used during the encryption of the message.
Symmetric cryptography is widely used on internet today, it comprises of two algorithm : BLOCK & STREAM. The two main encryption algorithm are AES(Advanced Encryption Standard) and DES( Data Encryption Standard). These are type of encryption which are way faster than asymmetric encryption. Symmetric cryptography allows to use one secret key by sender as well as receiver.
Symmetric crypto graphy uses either Stream Encryption technique or Block encryption technique.
Stream Encryption
This technique does not store data and encrypt message word by word one at a time.
Block Encryption
This technique encrypt large bits as a single entity. This usually store data untill full message is encrypted. Mainly used block size is 64 bits. But, AES algorithm and some other algorithms might uses 128 bits block.
Purpose of symmetric cryptography
It is the older kind of encryption method but, this method is simple to use, quick, smoother than asymmetric method,which causes strain on network due to heavy data size and CPU usage.
Due to quickness and smoothness of symmetric encryption it is used for big volume data encryptions.
Uses of Symmetric cryptography
For payment applications
For hashing
For validation of sender of information
Advantage
It is more effective
It has password authentication for receiver
Decryption happens only when their is a key
Doing encryption is simple
Faster than asymeetric encryption
Disadvantages
Key must be sent to receiver to decrypt
It's digital sign can't revoked
For communication between different person different set of keys need to be created.
ASYMMETRIC CRYPTOGRAPHY
This cryptography is also known as public-key cryptography. Asymmetric cryptography encrypt/decrypt a information by using a pair of keys. One of these two keys is used as public key and another one is used as private key this helps in preventing unauthorised use of information. In asymmetric cryptography anyone can use public key to encrypt the message or information, which will be decrypted by receiver by using their private key.
These encryption/decryption are automatic processes user need not to use key to encrypt/decrypt data manually.
Advantage of asymmetric encryption is that it increase the security levels as user never supposed to share their private keys.
Purpose of Asymmetric Cryptography
It is mainly used to verify the digital signature on messages. Digital sign which uses this asymmetric cryptography may contains identification, transaction, origin proof os one who signs information. There are other application of asymmetric cryptography such as
Encrypted emails
Used in SSL(safe sockets layer) & TSL( transport layer security) cryptographic protocols.
Advantages of Asymmetric Cryptography
It removes key distribution issue.
Improve security because of using two keys and private keys are never supposed to exchange.
Provides message verification
Disadvantages
Lack of speed
Need more computer resource
When private is lost it can not be replaced.
6. How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Let us first learn about some basic terms involved.
Crypto Wallet
It is an online wallet that is used to store our crypto assets digitally. Each crypto wallet has two key public and private key which are required to access the wallet related work.
Crypto Wallets Private Key
This key is used to digitally sign the transaction. It is a code of random alphabets and numbers. Private key are very important as security of your asset is depends on that key.
Example of private key :
51496782014950762205574803739667833920476739905538591040584511261110595975154
Crypto Wallet Public Key
This is used by miners before adding new block of transactions for verification purposes. It verifies the authenticity of users private key. This key is also a alphanumeric code.
For example
0416d00553c33cdad9903c17902c1840dead811ece53442da7b401e5343bb9e52b84e5ff2e4bf8a9eb1399b5f02088cad0251d4be162411c24a38954a853d91d3e
Crypto wallet address are generated using the hash algorithm along with the keys. This combination of hash and key makes wallet address very secure. These address are used for sending/receiving crypto assets. These addresses can be shared in public because hash algorithm assures that our wallet address are safe and did not compromise with our private key.
Categories of Crypto wallet
Crypto wallets are mainly of two types :
1. Cold Wallet
These type of wallets are physical wallets and are not connected to the internet. These wallets are supposed to be more secure as they are not vunerable to online attacks.
Advatages of cold wallets
More secure as they does not require any kind of key, because your keys are held with third party.
Can not be easily hacked as they are not connected to internet.
Recovery of wallet is possible
Disadvantage of cold wallets
Need more time for access as you use it at suitable place and time.
May cost high price for offline wallet
They did not accept all crypto assets.
2.Hot Wallet
These are kind of wallets which are digitally present and are connected to the internet. As they wallets are connected to internet so they are vunerable to oline attacks.
Advantages of Hot wallets
Instant access to your wallet
User friendly and easy to use.
Low cost required for online wallets.
Disadvantages of hot wallets
Vunerable to online attacks
Depends on third party for key
Some of the sub-types of wallets
Hardware wallets
These wallets comes under cold wallet type. These are hardwares which are needed to store assets.
Desktop wallets
These are kind of software installed wallets in your computer. For example : Coinomi Wallet, Bitcoin core, ...etc
Mobile wallets
Wallets which are present in your mobile devices through applications installed. For example : Coinomi, Electrum, ...etc
Web wallets
These are kind of hot wallets which are connected to internet. These wallets easily access through any kind of browser. For example : Metamask wallet.
7. What is the Merkle trees and What its importance in blockchain?
Hash tree is another name of Merkle tree.
Merkle tree or Hash tree concept first discovered by Ralph Merkle in 1979. Basically, Merkle tree is a data tree in which leaf nodes are labelled as Data block Hash and non-leaf nodes are labelled as cryptographic hash of child nodes. Lowest node in Merkle tree is leaf node.
Merkle tree is one of the basic part of blockchain technology. Merkle tree is simply a data structure, made up of hashes of different blocks. Merkle tree or hash tree acts like a summary for collection of all tranactions that take place in blockchain. It provides secure verification of content in big data body. Bitcoin and Ethereum both uses Merekle Tree structure in their blockchain.
Working
Merkle tree is used to store all transactions data in block by generating digital fingerprint for all transactions. This will help users to verify the tranactions before inculding them to block.
Hash tree is generated by simultaneously calculation of hasing pair until single hash left which is known as Root Hash or Merkle root. Hash tree construction is a bottom-up approach. Each leaf has transactional data hash and non-leaf has hash of previous hash. It is a kind of binary tree and required leaf nodes as even number otherwise the last hash ducplicates itself to create even number of leaf nodes in tree.
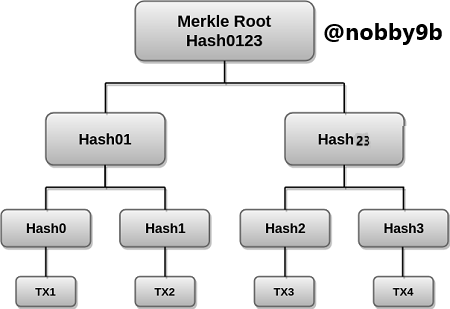
As you can see in the picture above the most basic example of merkle tree. It consists of 4 transaction blocks TX : 1,2,3,4 . There is hash at top HASH0123 which is hash of fulltree also known as merkle root. Everyone of these are constantly hashed resulting in Hash0 , Hash1, Hash2, Hash3. Also consecutive pairs of these hash are combined to make parent node. Hash0 combined with Hash1 to make Hash01. Simailarly, Hash2 is combined with Hash3 to make Hash23. These two hashes Hash01 and Hash23 are then combines to make Hash0123 which if root hash.
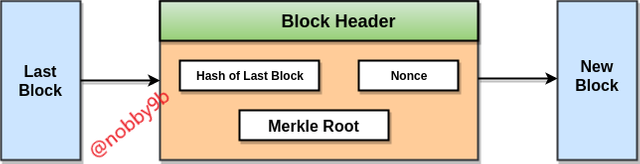
Root hash or merkle root is kept in block header. This block header is hashed during the mining process. Block header has three components : Merkle root , nonce, hash of last block. Due to presence of root hash in block header all transaction are secure and can't be changed.Merkle tree has great security levels, and if only one detail of transaction changes this change will cascade up the complete hash tree into merkle root, thereby invalidating the block. So, this is how merkle tree decides in a quick and simple way whether to add or not a transaction in block.
Benefits of Merkle tree
It provides good integrity levels.
It is easy and fast.
It is very efficient in storing data.
8. Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing, and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
In this question all the examples are take from
Keys
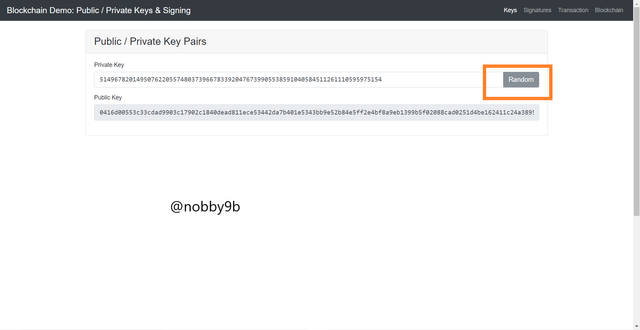
As we already discuss in first part of this homework task that asymmetric cryptography need two kind of key private key and public key. These keys are alphanumeric codes generated from random numbers and alphabets. Each and every private key has its own unique public key.
As you can see in the picture we can see a private key linked to a unique public key.
Private key :
51496782014950762205574803739667833920476739905538591040584511261110595975154
Public key :
0416d00553c33cdad9903c17902c1840dead811ece53442da7b401e5343bb9e52b84e5ff2e4bf8a9eb1399b5f02088cad0251d4be162411c24a38954a853d91d3e
This is a unique public key relate to above private key.
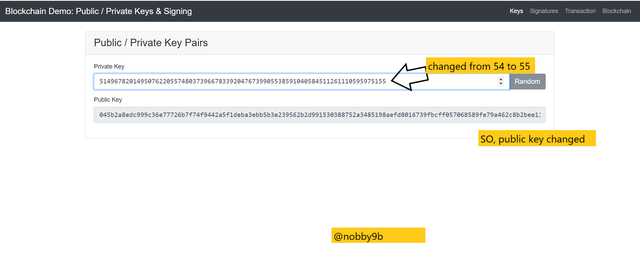
As we already know now that there is a unique public key realted to each private key. If we slightly change the private key then public key will also changed. Let us see
For example :
Private key :
51496782014950762205574803739667833920476739905538591040584511261110595975155
Public key
045b2a8edc999c36e77726b7f74f9442a5f1deba3ebb5b3e239562b2d991530388752a3485198aefd8016739fbcff057068589fe79a462c8b2bee115c4480e3fd2
Here, from previous private key I change the last digit from 54 to 55 and as you can see my public key is completely changed. This verifies that each private key has unique public key.
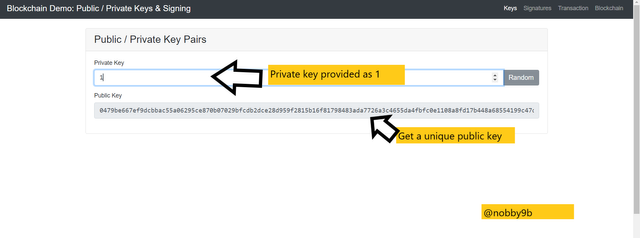
Now if we look at another example, we want to generate a public key to a private key that we provided. Here, I provided private key as 1 and we get a unique public key for that.
Private key :
1
Public key :
0479be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798483ada7726a3c4655da4fbfc0e1108a8fd17b448a68554199c47d08ffb10d4b8
All these examples verify that each and every private key has unique public key associated with it.
Signature
Signatures are used to provide authenticity to a transaction and it is generated with private key and hash of transaction.
Signature here is digital signature done to a transaction using user's private key, this sign is verified by miners before adding this to block by using user's public key.
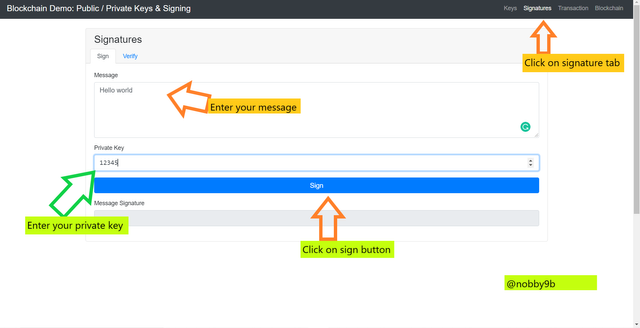
Procedure to done :
We go to website click
Now we have to select signature tab from top right corner.
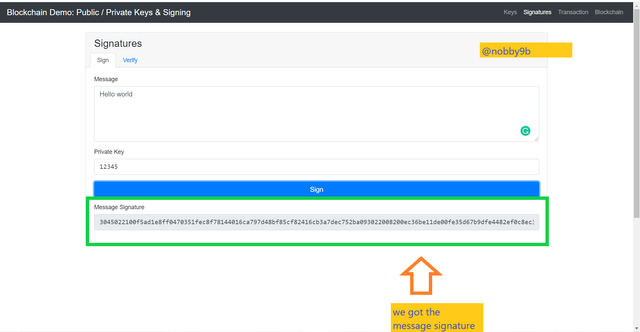
Now, we have to provide a message in message box, this message can be anything of your wish. I enter a message : Hello world
After entering message you have to you need to enter a private of your choice. I entered private key as : 12345
After all this done click on sign button to digital sign your message.
After clicking on sign button we get signature for transaction which has message : Hello world and private key : 12345
Sign:
3045022100f5ad1e8ff0470351fec8f78144016ca797d48bf85cf82416cb3a7dec752ba093022008200ec36be11de00fe35d67b9dfe4482ef0c8ec3b930d175db7fccc2ef43752
In this we can do digital signature to a transaction.
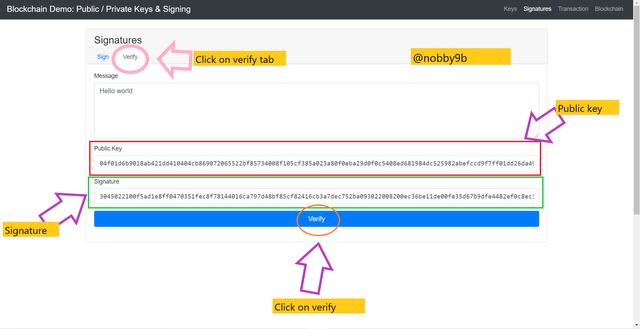
Verification
Now if we want to verify this digital sign then we click on verify option on signature tab of same website. This verification will authenticate the private key's digital sign. On verification tab we can see our message also our public key and signature.
The unique public key related to my private key 12345 is shared with miner who verify transactions. We need to click on verify option to complete the process of verification.
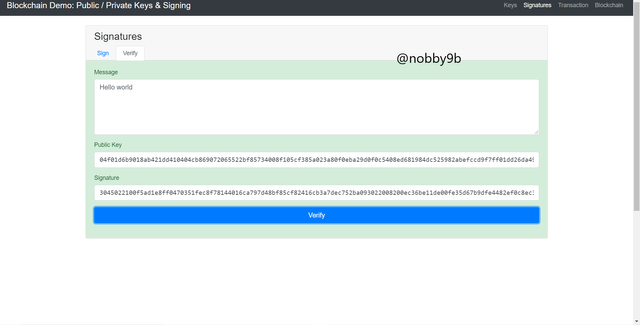
When we click on verify option, the colour of screen automatically turns into green that means signature added using our private is verified by the public key.
Transaction
Transaction is added to block after signing message with private key and verify it with public key.
Let see how it is done.
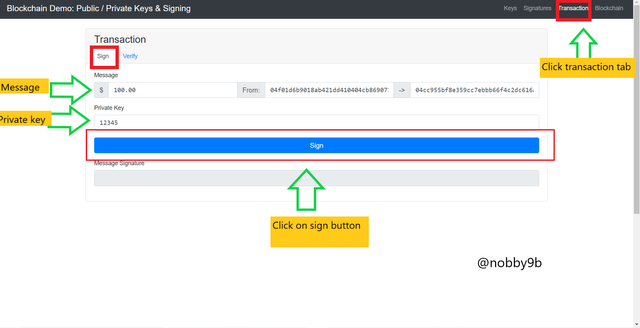
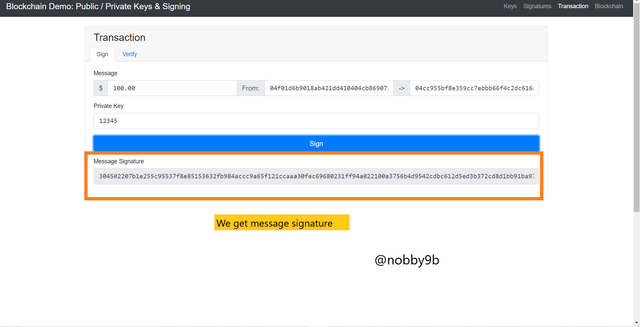
Go to click
Click on transtions tab. We can now see sign tab on screen where I provide input as $100 as amount that I am going to send. My private key is 12345 which already there and public key related to this private key is already shared with receiver.
Now we click on sign button below.
And get message signature :
304502207b1e255c95537f8e85153632fb984accc9a65f121ccaaa30fec69680231ff94a022100a3756b4d9542cdbc612d5ed3b372cd8d1bb91ba9760a25687686f349662e4a94
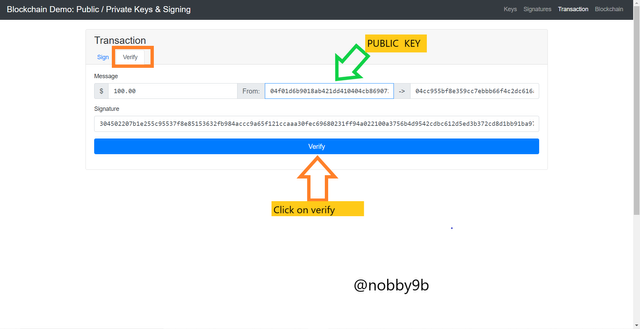
Verify
Now we are going to verify this sign. For that click on verify option in same transaction tab. Verification is done before adding new block.
Our public key linked with our private key is already shared with miner.
Public key :
04f01d6b9018ab421dd410404cb869072065522bf85734008f105cf385a023a80f0eba29d0f0c5408ed681984dc525982abefccd9f7ff01dd26da4999cf3f6a295
Now click on verify option.
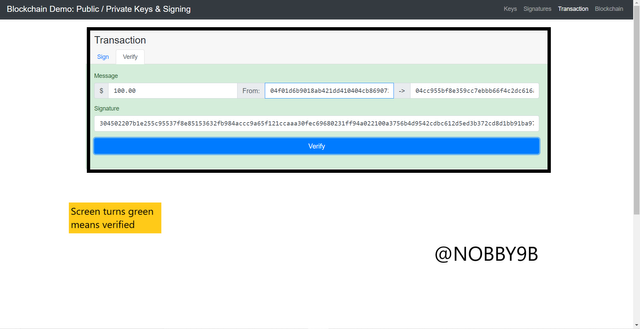
As you click on verify option screen will automatically turns into green means our transaction is verified succesfully.
Blockchain
This option will let us know how transactions will be stored in blocks wth hash created with cryptography.
Go to click
click on blockchain option.
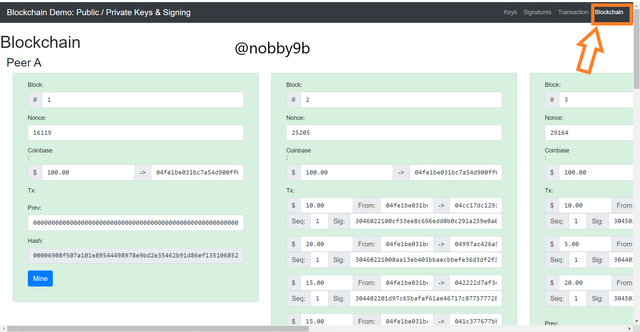
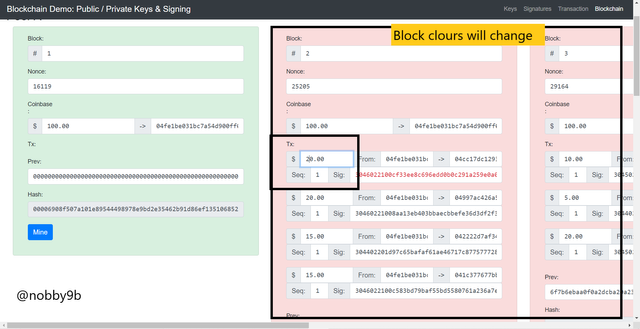
In above screen we can see all the verified block which are added. In each block we can see hash, block , nonce , and other transaction details. If we just slighlty change any of the block details than this will not verified. For example :
As you can see in above picture I tried to make a slight change.
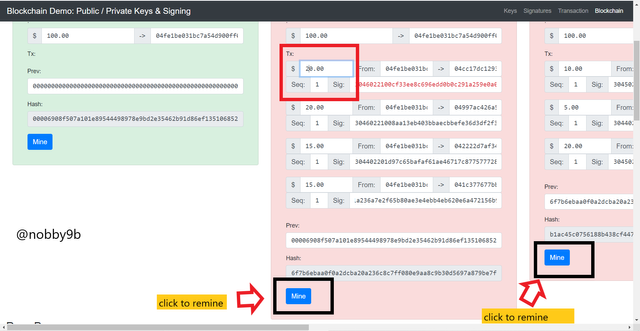
In block 2, I will change transaction 1 from $10 to $20 then screen will automatically turns red and thus invalidtaes the block. We can also see that block 3 which is after block 2 also turns red. This is mainly due to one reason, as we alreday discussed in merkel tree that block header consists of previous block hash, nonce, merkle root and all these are used to make new block. And soon as we change any details of block it will affect all the blocks that followed that block. Here when we change in block 2 it became invalid and due to this next block 3 become invalid as its formation depends on the block header which has previous block hash. Due to this we now need to remine these blocks with different nonce to validate.
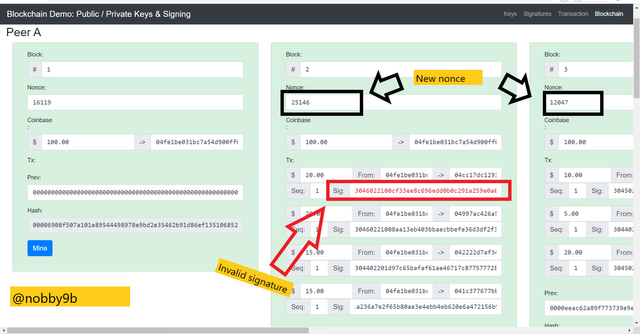
As you can see nonce of block 2 is 25205 and of block 3 is 29164. As soon as we click on mine button below than nonce of block 2 changes to 25146 and nonce of block 3 changes to 12047.
Here, we can also see that signature of block 2 is still not verified this is due to the difference between the key used now and keys used previously to sign the message.
So, we learn about detection of invalid transaction and how one block details changes another one.
Conclusion
Blockchain uses cryptography to be more secure and it is most important aspect for any blockchain. With the use of cryptography blockchains are so secure that even small change can be detected.
Cryptography is of two main types symmetric and asymmetric cryptography. In symmetric, we requires only one kind of key and in asymmetric cryptography, we need two keys one is private key which is used to sign the transaction and other key is a public key which is used to verify that sign done using private key. Only a unique public key is related to one private key.
With the help of cryptography, we can easily signs and verify the transaction. Hash algorithm plays an important role to make blockchain compact by making big data into single block. We also learn about the Merkle tree in this homework post. The main use of Merkle tree is to make blockchain fast and smooth. It consists of a root hash of block and other hash are made from that root hash.
At the end of post we learn about some praticals which are very helpful for better understaing to basic concept. We learn how different processes like digital sign, transaction, keys, blockchain works. We also learn how we verify transactions and digital signature. In the last we learn how to detect any minstake in a blockchain.
Thanks to professor @stream4u for such a great lecture. I learned a lot from this lecture.
.png)

I really love the remarks for the professor
Your really learned
Data input is a briskly growing sector in Pakistan. Information Transformation Services can meet a variety of Data Entry Services
competently and professionally. ITS will not only provide various data entry services to customers, but will also offer some creative and customized solutions to meet your needs.
Academic Master is a US based writing company that provides thousands of free essays to the students all over the World. If you want your essay written by a highly professional writers, then you are in a right place. We have hundreds of highly skilled writers working 24/7 to provide qualityessay writing services to the students all over the World.
You have been upvoted by @sapwood, a Country Representative from INDIA. We are voting with the Steemit Community Curator @steemcurator07 account to support the newcomers coming into Steemit.
Engagement is essential to foster a sense of community. Therefore we would request our members to visit each other's posts and make insightful comments.
Thank you