Crypto Academy / Season 3 / Week 8 / Homework Post for Professor@stream4u — Let's Open Cryptography


Introduction
Dear Steemians,
It is a wonderful time again in this academy. I hope your week has been good. Mine has been full of blessings. I am Taiwo Micheal and my username is @msquaretk. I am extremely glad to be submitting my homework post for Professor @stream4u in the CryptoAcademy Advance class. Prof has introduced us to the topic "Let's Open The CryptoGraphy", and he has dexterously explained the concepts of this topic in a unique way. In the homework section, he has posted some questions which I will be answering based on my own view in the next paragraphs.

Question 1
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
What is Blockchain Cryptography?
To fully understand blockchain cryptography, let's first understand the meaning of blockchain and cryptography.
Blockchain consist of two words, Block and chain. It is a decentralized or immutable ledger that store transactions or information in form of block and securely share or distribute this transactions across the network. The transaction data or the block which include data of transaction stored by blockchain are encrypted and are joined together by a chain. Hence, the word "Block + chain", Blockchain.
Cryptography is also called cryptology. It is a system of communication that enables the secrecy of information shared. This technique allow only the sender and receiver of information to view the message or the contents of the information. This means that nobody can have access to the information except the sender and the recipient. The sender uses the key and algorithm to encrypt the information sent and that ensures the information to be concealed. The receiver at his end, decrypt the information received and allows him to view the contents of the message.
Now let's now bring blockchain and cryptography together. Blockchain Cryptograph is a technique used to secure the information or transactions shared on the blockchain network. This allows the secrecy of the transactions shared across the entire blockchain network. Blockchain cryptograph also ensures high level of security on the blockchain network and thereby disallow the third party access to the blockchain data.
The main purpose of blockchain cryptography is encryption, decryption, keys and cipher.
Encryption is a system of changing information from one form to another with the aim of hiding it. Decryption on the other hand deals with technique employed to convert the encrypted message to understandable format. The algorithm used in achieving encryption and decryption is what is known as Cipher. Also, keys serves as means to obtain the cryptographic algorithm output.
There are two keys employed in cryptographic algorithm. They are symmetric Algorithm and Asymmetric algorithm. Symmetric algorithm involves the use of the same key for both encryption and decryption operations. This type often create problem for both sender and receiver and it is not employed in blockchain cryptography. The second type which is asymmetric algorithm is deeply employed in blockchain cryptography and it involves the use of different key for encryption and decryption operations. Public key is used for encryption while private key is employed for decryption operation.
Another noticable point to note about blockchain cryptograph is cryptographic hashing. It is also a cryptographic algorithm which takes huge or large amount of data input and convert it to a fixed but compressed output.
This function is used to verify data in blockchain.
Features of Blockchain Cryptography
Blockchain cryptography ensures security and safety of information shared on blockchain network.
Data sent cannot be altered and the sender cannot claim the information sent was not sent by him.
Information can be send anywhere without the linking of content of the information.
Data and space are managed through the use of cryptographic algorithm hashing and this in turn saves time and energy.
Some Blockchain Platforms are listed below;
• Ethererum blockchain
• Tezos Blockchain
• EOS blockchain
• Stellar Blockchain
• Binance chain
• Steem blockchain
• Tron blockchain
• Hyperledger Fabric blockchain
• Stellar blockchain
• Ripple blockhain
• Corda blockchain
• Openchain etc.

Question 2
Explain the Public Key CryptoGraphy.
Public key as it name implies is a key that can be shared to the the general public on blockchain for identification purposes. It is a key used for data encryption in blockchain cryptography. Additionally, public key is also used to encrypt message which ensures the security of information sent from sender to the receiver.
For instance, let's assume that I want to send a message to my Mummy, the only means I can send this message is to deliver it through my sister and I don't want my sister to know the content of the message, encryption of the message would be needed. The key that will turn the message from understandable format to non understandable format is known as pubic key.
Practical example of Public key
Text + public key = enciphered text
"The house is 100M Niara" + public key = A4Dqym8Xhyr
From the above example, the text "The house is 100M Niara" is added to a public key and then turned to non readable format "A4Dqym8Xhyr". The text was able to turn to non readable format by the help of public key. The ciphered text i.e the non readable format message can only be read by individual who has the private key that is directly related to the public key that is used to encrypt the message.
Also, public key is also use to check the authenticity and verify data signature. More so, public key also helps in the creation of public address by hashing which helps crypto users to receive fund to their wallets.
Let's see the example of a public key in a screenshot below

Key Features of Public Key Cryptography are;
• Public key helps in the generation of public address by hash function which in turns help crypto user to receive fund to their wallet.
• It helps in the verification of digital signature.
• Public key has a corresponding private key
• It can be shared to the public without jeopardizing the corresponding private key

Question 3
Explain the Private Key CryptoGraphy.
Private Key Cryptography is a form of security that put crypto users in total control of their asset or fund in their wallets. It consists of alphanumeric characters. Unlike public key which can be published to the public, private key is personal to users, it must not be published to the public. Otherwise, the owner lose total control over his funds or assets in his wallets.
Private key Cryptography is used to confirm transaction before it go through the intended path to which the transaction is sent. Let's take a look at Steemit Private key for more understanding. For steem blockchain, the keys are segmented into three part; Private posting key which is use to login to steemit platform and to do some tasks such as commenting, posting, voting etc. ; Private memo key, which is used to decrypt memo on the blockchain and Private active key, which is use majorly for wallet operation such as confirmation of transaction, confrimation of powering up etc.
Additionally, private key are generated at the creation of wallet. Also, private key is used to sign transaction. Without private key, transaction cannot be signed.
Below is an example of private key.

Key features of Private Key Cryptography
• It is used to sign transaction.
• It is a secret key that must not be shared or published to the public.
• It gives security to asset or fund in the wallet.

Question 4
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Cryptography Digital signatures is another important unique of cryptography blockchain. In any matter that involves money, before a transaction is processed, signature must be attached as a confirmation that the person who want to do the transaction willingly release it. In the traditional system, this signature is affix by handwritten method, stamp or thumb print etc.
Similarly, in blockchain cryptography, this concept is used and it is called cryptography digital signature.Just as signature is used on legal document for certification and as a mean of identity, so also digital signature is used in blockchain primarily to affirm or confirm the authenticity of data, transaction or messages before it is sent. In this case, the digital signature tie, chain or attach a person to the data sent.
Furthermore, digital signature is the mathematical processes attached to data and the private key of the person who is to sign the documents. That is, private keys are used to sign a transaction. This help the receiver to ascertain the sender of the message or transaction. Then the receiver the use the public key to verify the data.
Point to note
Private key is used for signing while public key is use for verification.
Singing Of Transaction/Message?
Electronic data in Cryptography blockchain require authentication of data which is achieve through signing which is called digital signature. Private key is employed in the signing of transaction or messages. I.e, the transaction or message is affixed with signature by the help of private key.
When this is done, the transaction of message is then sent to the pool for the verifier to verify the authenticity of the transaction or message. The private key is not shared to the public however the public key is shared to the public. The verifier or the blockchain miner then use the public key that that correspond to the private key to verify the transaction sent.
There are two things to note in adding signature to transaction or message. They are;
- signing and
- verification.
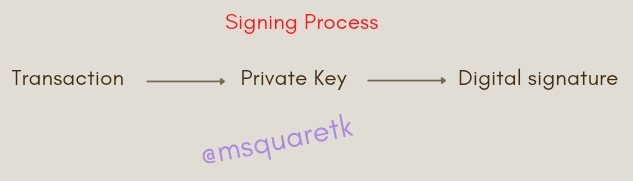
Let's see the signing process in a diagram created on canva app below
The above picture shows the steps in the signing of transaction. The transaction is signed with the use of private key which in turns gives digital signature. Then the transaction is sent to the blockchain for verification.
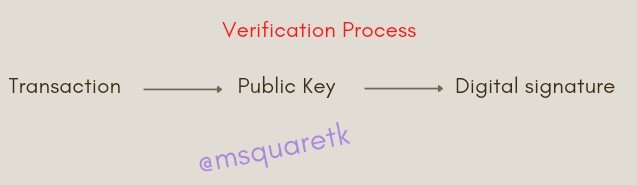
Let's see the next picture for verification procedure
The above diagram shows what happens in the verification phase of digital signature. The transaction is located by the blockchain miners in the pool. The miners use the public key corresponding to the private key of the sender that initiated the transaction to verify the transaction. At the successful verification of the transaction, it is then added a block.

Question 5
Explain what is Symmetric and Asymmetric cryptography?
What is Symmetric Cryptography?

In Blockchain cryptohraphy the data or information sent are kept secured from the unauthorized party. That is, the information can be accessed only by the sender and receiver of the message. The technique use for this process is achieved through encryption and decryption of the information or message sent. To operation of encryption and decryption is accomplished through the use of keys.
In symmetric cryptography a key is used for both encryption and decryption processes. In this type of cryptography a sender use a key to encrypt a message to a non readable format before sending it to the receiver. The receiver of the message at his end then use the same key which the sender used to do encryption to decrypt the message received. This system allows both party to share common secret key. Therefore, the same key that is used to encrypt a message is used to decrypt it. Hence the word symmetric.
Although symmetric cryptography is faster than asymmetric cryptography because of the uncomplicated algorithm being used, the main drawback of this type of cryptography is that all parties involved have to share the same secret key to do encryption and decryption processes. This poses a risk on the the secret key because there will be maximum usage of a single key which may further cause the linkage of the secret key to the unauthorized party.
There are two classes of symmetric cryptography, classical and modern cryptography. Classical cryptography is further divided into Transposition and Substitution. In transposition encryption, the position of the text are shifted during the encryption process. In substitution method of classical cryptography, the unit of the plaintext are replaced with a fixed designed system.
Modern cryptography is also of two types which are stream and block. Stream type of modern cryptography encrypt information by bit at a time. While the block type in the opposite of stream. This type encrypt information by block instead of a single bit in stream type.
What is Asymmetric Cryptography?
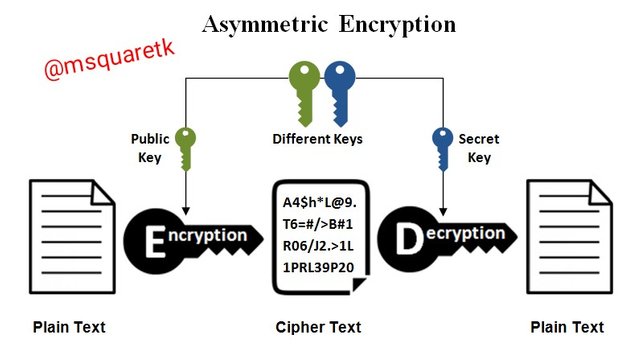
Asymmetric cryptography unlike symmetric cryptography uses different keys for encryption and decryption of information. The keys that are employed in this type of cryptography are public key and private key. The public key can be published for all but the private key is kept secret by the person who generated the keys.
The information may be encrypted with the use of public key or private key and the private key or public is used to decrypt the information. If the information is encrypted with the sender private key, the decryption will be done with the sender public key. However for a receiver to use his private key to decrypt a message, the sender must have used the receiver public key to encrypt the message.
Although the keys use for for both encryption and decryption are different but they are related to each other. And this helps the information that is encrypted with a key to be able to undergo decryption with another key but related one.
Unlike symmetric cryptography, asymmetric cryptography is enhanced with high level of security because the parties involved do not exchange private key for encryption and decryption of information. And this implies that the risk of attack in small compared to symmetric type.

Question 6
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets
Blockchain wallets cryptography is another key note in blokchain cryptography. This involved the use of cryptography technique to secure blockchain wallet. In blockchain cryptography wallet, there three things to note. They are: wallet address, private key, and public key. These three key things listed above are related and unique to cryptography wallet and are used in different forms. We would be discussing each of them in the next paragraphs.
Let's first introduce cryptography wallet. Cryptography wallet is a device that is used to securely store public and private key. It enables users to keep and recover their digital asset.
Wallet Address
To fully understand wallet address, let's look at the screenshot below

The image above is a typical example of what happen in crypto wallet address. The picture is a key box lock. The box can only be accessed by anyone with the key code. That means anybody without the key to the box cannot have access to what is in the box. The blockchain wallet address also function the same way. It is like a box that is secured with key in which crypto funds are kept. The security of the wallet with the use of key put the asset owner in full control of his fund.
Wallet address is like traditional account number which consist of alphanumeric character that enables the owner to send and receive crypto asset.
Below is the screenshot showing example of a wallet address.
It should be noted that wallet address can be share to public, of course it is send to people who want to transfer fund to owner wallet address. Additionally, just as there are no users with same account number in traditional banking system so also no wallet address is the same in decentralized blockchain. This then put each user in control of his wallet because no one can collect their wallet address.
Private Key
At the successful creation of blockchain wallet, a private key associated to this wallet is generated. The private key is made up of alphanumeric character which is a function used to maintain high level of security to user's fund. You remember the illustration of a box above? Private key can be liken to the code that is used to open the box. As no one can open it except the owner of the box, which then give him the right of ownership. Likewise, the private key is used to access blockchain wallet. It is a secret key that gives security to the wallet address.
Private key like the illustrated code inform of key that is used to open a box, also put the owner of wallet address in full control over his fund in his wallet. More so, the private key is used to confirm and to add digital signature to the transaction before releasing it to the pool for verification by the miners.
The screenshot below shows how private key look like.
Public Key
Public key like private key is also a combination of series of letters and numbers. This key is related to private key. When the transaction has been initiated by the sender and then signed the transaction with his private key, it will be send to the blockchain pool. The miners then look for a public key corresponding to the private key of the sender to verify the transaction before it is added to a new block. In short, public key is use to verify the originality or authenticity of the transaction.
The screenshot below shows an example of public key.

Types of Crypto Wallets
There are various types of crypto wallets. Crypto wallets can be divided into software, hardware and paper wallet. Another division of crypto wallet are cold and hot wallet.
Software wallet as it name implies is a wallet storage that is designed to be stored on the computer hard drive. Many of this type of are connected to the internet.
Hardware wallet on the other hand is a wallet that store the private key to a wallet in a hardware. The reason for this storage devices is to keep the key secured and this enables it to be less funnerable to the attack. Unlike software wallet, hardware wallet is physical and it is store in a secure place.
Paper wallet is another means of storing private key in blockchain. It is an offline way of storing key. It is an old method of storing key, as such, it is no more widely used to store key.
Hot Wallet: As mentioned earlier, another classification of crypto wallet are hot and cold wallet. **Hot wallet is a wallet that is connected to the internet. I.e the private key in this type is save over the internet. Example of hot wallet is my steem wallet address. The transfer of fund from my steemit account to my Binance steem spot wallet is know has hot wallet because the wallets are connected to the internet. Some software wallet are example of this wallet since they are connected to the internet.
Pros of Hot wallet
• The transaction done via Hot wallet is easy and faster compared to the one done on cold wallet.
• It is associated with convienent transaction.
• Since hot wallet is stored over the internet, it is enables ease of accessibility.
• Setting up a hot wallet is simple compared to a cold wallet.
Cons of Hot wallet
• It is less secured compare to the cold mode of storage.
• Users don't have access to their private key on hot wallet provided by centralized exchange and this does not put them in total control of their assets.
Cold wallet on the other hand is not connected to the internet. Unlike hot wallet, cold wallet employed the use of offline technique as a medium of storage for to store keys. Cold wallet is associated with low risk of internet hacking since the keys are kept secure offline. Hardware and paper wallet are example of cold wallet since the two are stored offline.
Pros of Cold Wallet
• It offers high security since it is store offline.
• It can be carried around.
Cons of Cold Wallet
• It is not easy to set up compared to hot wallet
• Cold wallet storage is costly.

Question 7
What is the Merkle trees and What its importance in blockchain?
Understanding Merkle Trees
Merkle tree is a technique that is used in the field of computer science to solve the problem of large and cumbersome data. The same concept is employed in blockchain. But what exactly the merkle tree came to solve in blockchain? What is it work?
In blockchain transactions or data are verified by miners before added to a new block. It is the block that saves series of transactions in blockchain. There will be hundred of thousand of blocks as there are many transactions present each day. For example, in bitcoin, halving occurs at every 210,000 block mined. And bitcoin has experience three halving since it inception. The third halving occurred in 2020 which means as at today 21 of August, 2021, we have more than 630,000 blocks present in bitcoin. And averagely there are about 2,500 transactions in a block.
You can imagine the number of transactions that are performed on blockchain per second noting the large number of audience. The transactions are very numerous and as such the data are very large and cumbersome which in turns consume space and energy. Locating each transaction or data can be very tiring and time consuming. Hence Merkle tree is used to solve this problem.
Merkle tree is a strategy or approach used in blockchain to arrange and organize large amount of information, transaction or data that need verification and authentication to ensure to error free of data verification and efficiency.
Operational Principle of Merkle Tree
Merkle tree employed the method of hash function to perform it operation. Hash function is an algorithm that takes in input to produce special result which is called output.
Let's view a picture below to explain the operation of Merkle tree.
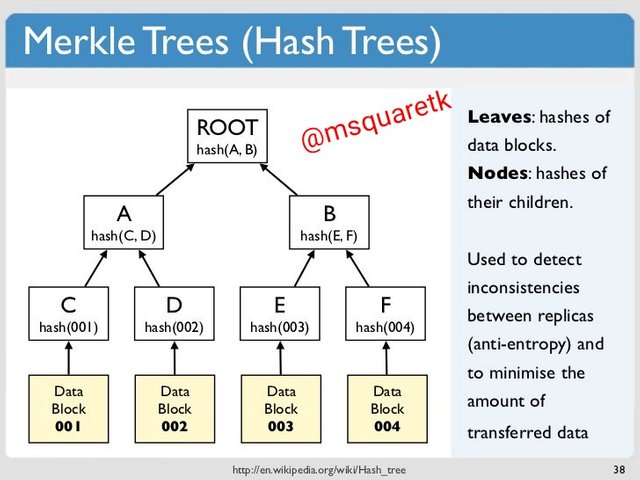
Merkle tree achieve its operation by first pairing data into two. The tree arrangement at the bottom of the picture in the yellow box are called block. Each block contains series of transaction. To understand pairing of data, let's assume that there are a total of 144 data in the block 001 of the picture above.
The merkle tree will first pair the 144 data to give 72 pair and this pair will undergo hashing to form new code, which is the hash 001 in box C in the picture. After this is done, the merkle tree would repeat the process. The 72 pairs will also be subjected to further pairing to become 36 pairs and then follow by hashing to form a new code entirely. This pair is then part of hash A in the picture uploaded above. The process continue until the merkle tree get a single code for all the data present. The single code is which is called Merkle root.
The C, D, E and F in the picture are the hashes of block 001, block 002, block 003 and block 004 respectively. These hashes are called leaves. The A and B in the picture are the hashes of C,D and E,F respectively. A and B are called nodes. The nodes A and B are further hashed to become the Root hash or Merkle root which is the final output of Merkle tree. The merkle root in the picture is the single code result gotten from the combination of the four hashes. This therefore ensure easy verification of transactions or data.
Importance of Merkle Tree in Blockchain
• Verification of blockchain data or transactions are made simple with the use of Merkle tree.
• Merkle tree reduces memory and space data consumes by converting thousands of data into a single unique Merkle root.
• It helps the Information to be compressed to a considerable size or length on the blockchain network.
• Blockchain miners work are simplified since they don't need to download a whole lot of data to verify the transaction.

Question 8
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
For this task I will be using the blockchain demo: Public/Private Keys & Signing developed by a man called Anders Brownworth.
• To access this website, go to Ander's website.
• Clicking this above website, the home page of Ander's website will appear as displayed in the screenshot below.
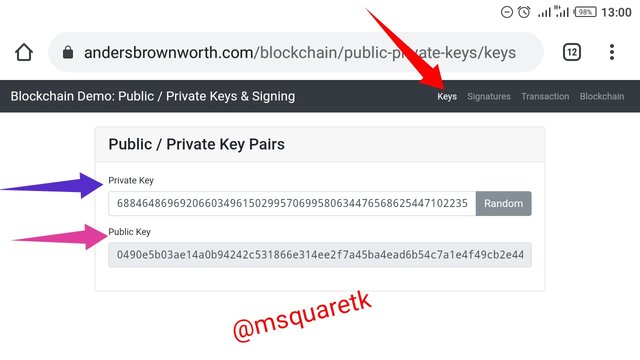
The picture above shows the home page of Blockchain Demo by Anders Brownworth. From the image above we can see some features at the top of the page. The features are key, transaction, **signing and blockchain. We will be exploring and explaining this features one after the other in this demo blockchain.
Keys
As mentioned earlier, keys are of two kind in blockchain. The private key and the public key. The public key is use to encrypt data which can be share to the public while the private key is a secret key that put crypto user in control of their fund. Both private and public ket are unique in their own. Although they are different but the are related to each other.
• Clicking the key as indicated by the red arrow in the screenshot above, two keys, private key and public key are generated as seen in the image above. They are pasted below
1st Private key: 68846486969206603496150299570699580634476568625447102235218653047148298430983
1st Public key: 0490e5b03ae14a0b94242c531866e314ee2f7a45ba4ead6b54c7a1e4f49cb2e44efa075c1965736eba9962899f34f17c3094ddff59e1ceb6ce695675f7a82a3c6f
• As mentioned earlier, private key and public key are related to each other, let's try to click random in the screenshot above to generate another one to see what happens.

• Clicking the random button from the above picture generated new private and public key. The private key is indicated by the blue arrow and the public key is indicated by a purple arrow in the screenshot. The "random button" which generated the keys is indicated by a black box. The private and public generated are pasted below;
2nd Private key :
69813127921202238914696772222630594677263837802459700563650486175742931332300
2nd Public key : 0417649c2706da97b91235236bf1186aa4368a33db61f4ca573454a4cc9c4235dbbfc108b37a5d9fdda405bb9231eed8db71715c1494b9bfccf35dbc446835a475
From this, we note that the 2nd private and 2nd public keys generated are totally different from the 1st private and public keys above. This then signifies that each public key is unique to it private key.
Let's us see another example about key generation for more understanding
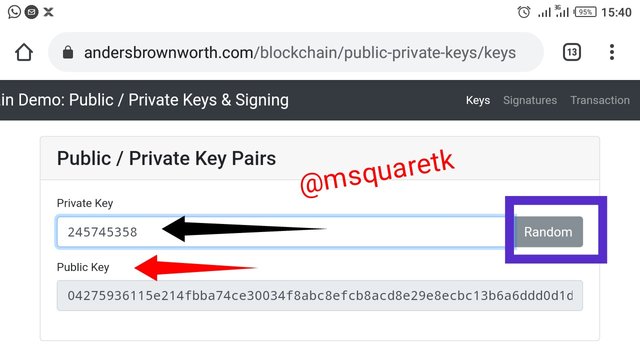
To further testify that the two keys are unique and related to each other, I altered the private key as seen from the screenshot above by imputing 245745358. This private key then generated new public key for me. The new private and public key are pasted below.
3rd Private Key: 245745358
3rd Public Key: 04275936115e214fbba74ce30034f8abc8efcb8acd8e29e8ecbc13b6a6ddd0d1d13a7c3180ab2aca8b2d36e0d67a7274b0c9b30395e553b8036315035f6c116d02
The second Feature we will be talking about is signature
Signature
Signature involve confirming the message that is about to be sent with private key. While the receiver at his own end verify the message using the corresponding public key.
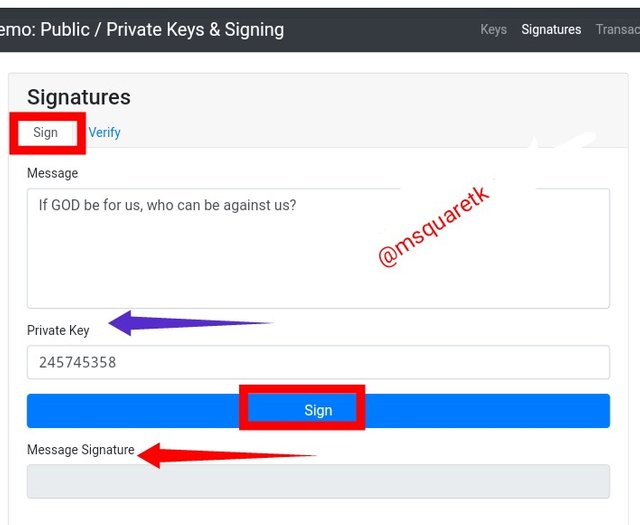
The screenshot above shows the signing process.
• To do the signing In the blockchain demo platform, click the signature at the top of the page.
• Then the page will appear before you. There are two key feature in this page, the sign and verify. The sign is the place where the sender will initiate the message and verify it with his private key. Verify page is where the receiver will verify the message. For this demo practice, I will be acting as both the sender and of the message.
• As seen from the screenshot above, I clicked sign, the the sign page appear. It consist message box, the private key: 245745358, as indicated by the blue arrow, the **message signature, as indicated by red arrow which has no value yet; and the sign button
• I put my message which is "If God be for us, who can be against us?".
• Next, I then clicked the button sign
Then let' see the next screenshot to check what happened thereafter.
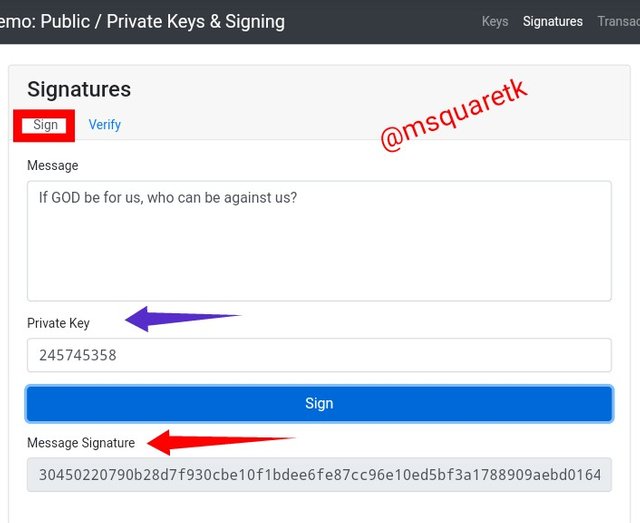
• From the above screenshot, we see that at the clicking of sign, message signature appeared. The message signature as seen from the picture is:**
30450220790b28d7f930cbe10f1bdee6fe87cc96e10ed5bf3a1788909aebd0164ac6f4e4a022100afc468c872a312d7eba9538422f074640641d5e85f5d6c39aabca750ff96cb7b
This is then the signature of the message.
• Now let's click the verify to go to verification page.
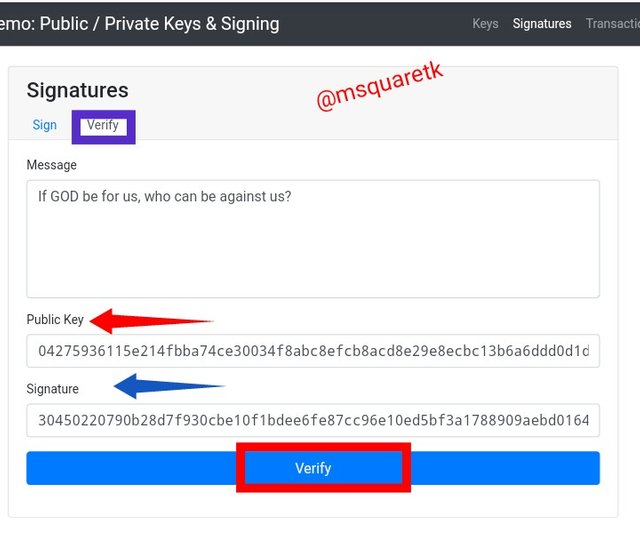
• The picture above is the verify page of the signature feature.
• It contains the message, the public key and the message signature.
• Upon receiving this message the receiver then verify the message with the public key.
• I will act as receiver also in this case. I then verified the message with the public key:
04275936115e214fbba74ce30034f8abc8efcb8acd8e29e8ecbc13b6a6ddd0d1d13a7c3180ab2aca8b2d36e0d67a7274b0c9b30395e553b8036315035f6c116d02 by clicking the verify button.
Then guess what? Let's see the next image to see the next magic
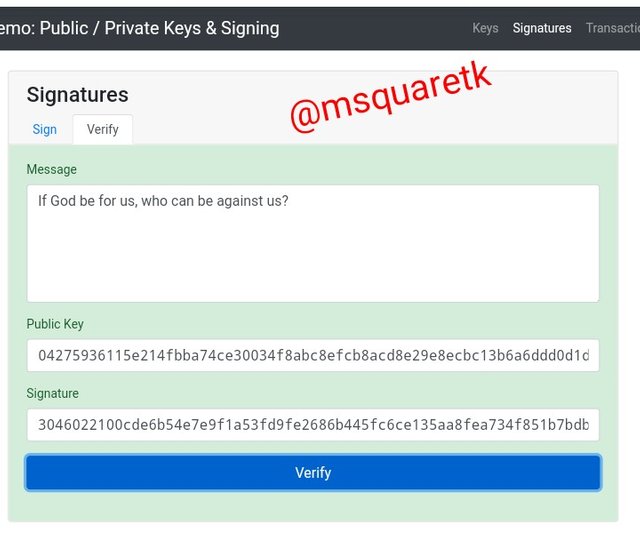
As seen from the image above, the message body changed from white to green. This validate the authenticity of the message received.
The next feature is Transaction feature.
Transaction
Transaction in this case involves the sending of fund from owner wallet to another wallet by using private key to sign the transaction and as such the message signature is generated.
To do transaction, click transaction from the top of the home page. Then the transaction page will appear for you.
Let's see the screenshot below.
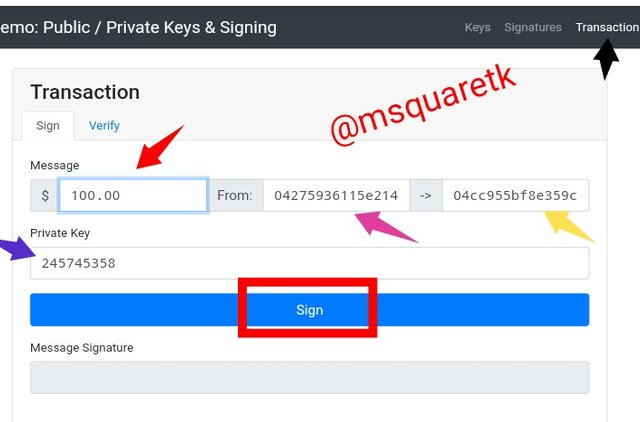
The screenshot above shows the transaction page of the blockchain demo in used. This page contain the message which is the amount a sender is willing to send. In this case I put $100 as seen in the screenshot. It also contains the wallet address of the sender, which in my own case is: 04275936115e214fbba74ce30034f8abc8efcb8acd8e29e8ecbc13b6a6ddd0d1d13a7c3180ab2aca8b2d36e0d67a7274b0c9b30395e553b8036315035f6c116d02. Also the wallet address of the receiver is seen beside the sender's address. The address of the receiver is: 04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74. The transaction is then initiated with the private key by clicking the button sign . The private key used for this transaction is 245745358. The last thing in that page is message signature which is not attributed with any value yet.
Let's see what happen when I clicked sign button.

• As seen from the image above, when sign button was clicked, the transaction was signed and the message signature appeared. Message signaturefor this transaction is:
304402201cdea13dd4ae9d325ba258d211d66919dd445dc09d5b3ce4f6b3bae6e81e8bfc0220497db5fc75a028721d122cb0491077bb58f1a82c88c0ae7ab8249aef3bf1b427
Then for verification, let's switch to verify.
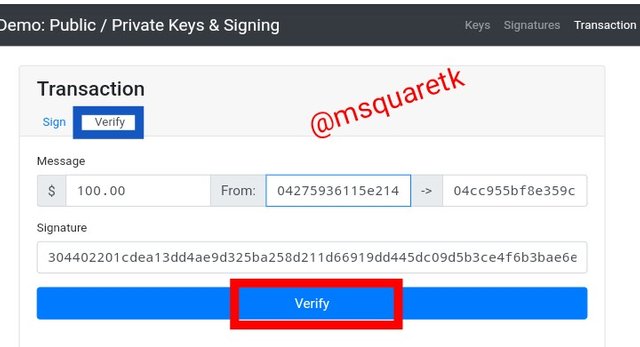
The picture above shows the verification process of the transaction. Then i clicked the verified button as indicated by the red box in the screenshot.
Now let's see what happened in the next screenshot below.
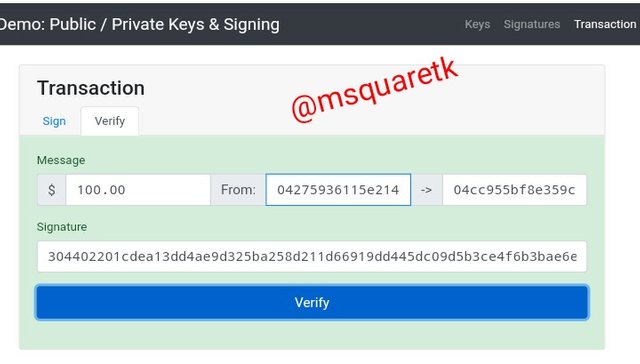
The blockchain color change to green at the click of verify button. This shows the validity of the transaction.
The last feature I will be discussing in this question is blockchain
Blockchain.
In this section, the details of transactions are recorded block by block. I will be explaining some transactions in this part.
• To view blockchain transactions, click blockchain from the top of the page.
• Then blockchain page will appear for you.
Let's check the screenshot below tosee how this feature looks like.
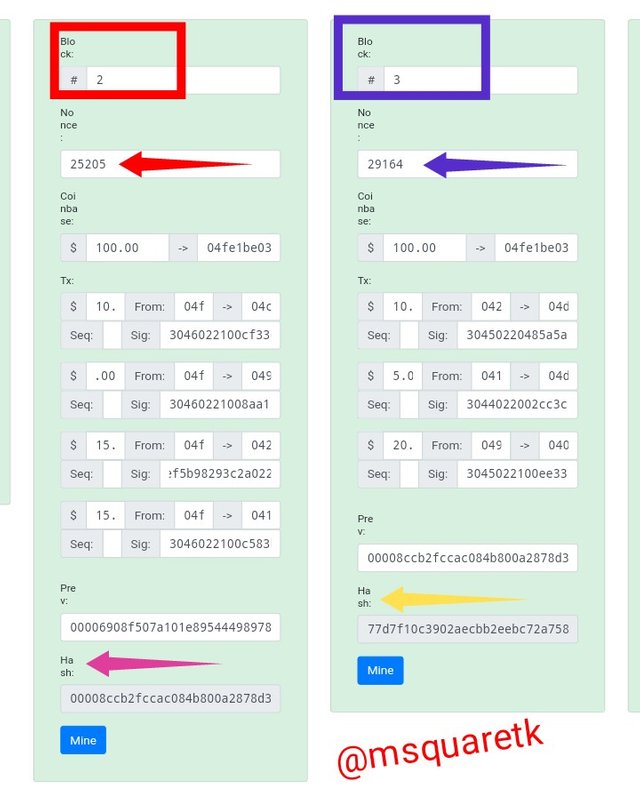
There are many blocks recorded in blockchain. For this exercise I will be using information contained in block 2 and 3.
• From the image above, block 2 is indicated by a red box and block 3 is indicated by a blue box.
• The total number of Nonce in block 2 is 25205 and that of block 3 is 29164
• Each block has it own hash. The hash present in block 2 is indicated by a purple arrow in the screenshot above. And the hash of block 3 is indicated by a yellow arrow.
• Then each block contains series of transaction as seen in the screenshot.
The information shows that the blocks are valid. Blockchain is a chain of blocks. Therefore, any alteration to either of the two block will render the two blocks invalid because the are joined by chain.
Let's confirm the validity of the statement I said in the previous parahraph by changing the number of Nonce in block 2.
I changed the number of Nonce in block 2 from 25205 to 2345. Then check what happenes in the screenshot below
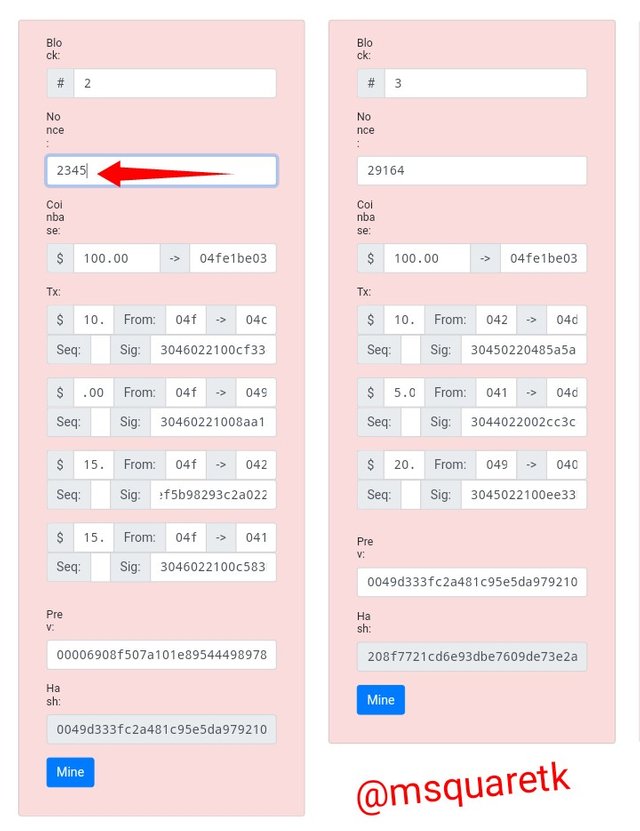
• From the above screenshot we can see that the changes made to the Nonce render both block 1 and block 2 invalid.
• How then can we correct this? We can correct this by re-mining the block to again.
• We then clear the Nonce in both block and mine the block two.
The picture below shows that the Nonce input for both blocks has been cleared.
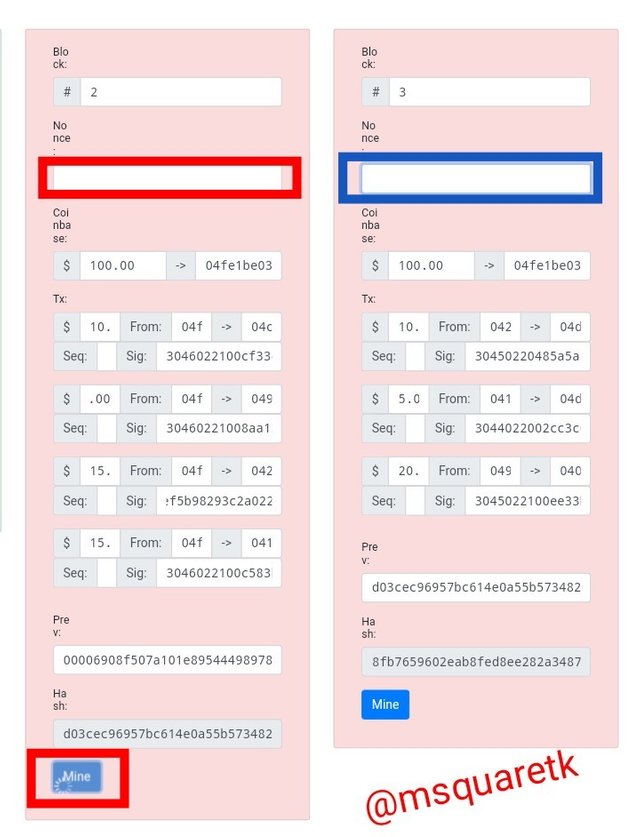
• After clearing the Nonce value for both block, I then clicked on mine in block two. It rotates for a while.
• Then the two block came back with valid response.
Let's see the screenshot below to check this.
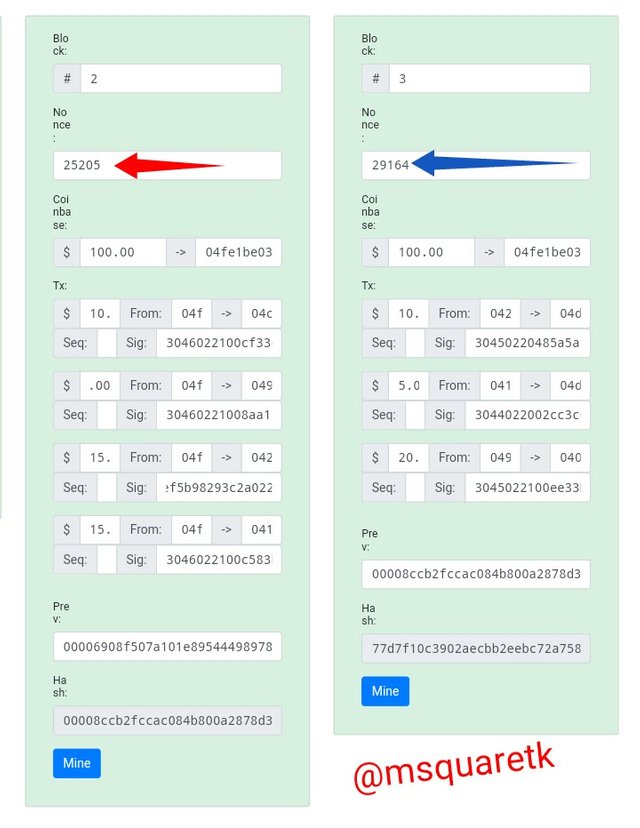
At the successful mining of block 2, the two blocks then become valid because they are chain together.

Question 9
Conclusion
One of the greatest threat to our society is the issue of security and confidentiality. More fund are released on quarterly and yearly basis to cater for this problem. This problem is not only occurring in the society but also happening to individual through the use of some traditional system such as bank and financial institution.
This issue is dealt with in blockchain with the use of cryptography. Cryptography has been the first topic to reckon with when it comes to secrecy of information, data or transaction. Cryptography helps in maintaining high level of secrecy. The parties involved could be certained that the information shared is highly kept and secured from unathorized party.
This technique employed by blockchain make it highly secured as there cannot be alteration or modification of the information shared. Additionally, cryptography also helps in the verification of information which is a great strength in validating the authenticity of data or transaction. More so, the symmetry and asymmetry type of cryptography also make blockchain secured through the encryption and decryption processes which is a great method employed in hiding information to ensure secrecy.
Another thing to note is is the use of Merkle tree cryptography employed in blockchain to solve the cumbersomeness of data stored in blockchain. This technique has also help in the management of space consume by data which is of great advantage in crypto space. It is then therefore of no doubt that blockchain is the future of financial system not only because it put users in control of their funds in their wallets but also maintains high level of security and confidentiality.
Special thanks to Professor @stream4u for opening us up to this great topic in the world of crypto. I have learnt whole lot about crytography and it techniques as employes in blockchain throught his presentation and of course through solid research, especially the Demo blockchain pratical aspect of this course.
Thank you for reading
Written by @msquaretk
Cc:- @stream4u
Thank you, Prof. @stream4u. I hope to participate in your next class