Crypto Academy / Season 3 / Week 8 - Homework Post for professor @stream4u : Let's Open The CryptoGraphy
Hello everyone this is Monz from India hope you are doing great. So after going through a study for this homework I am here with my Homework .
Hope I will be able to match all the standards of the homework required.
1. Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Let's Understand what's Cryptography
Cryptography is made up of two Greek words which are "Kryptos", which means hidden and "Graphein" means to write . It is the study of secure communications we can say a technique to prevent the data from third party which is techniques that allow only the sender and intended recipient of a message to view its contents .
Cryptography uses the techniques such as microdots or merging for covering the obfuscation of information in images . Moreover in cryptography first message/data is encrypted which is converted from plain text to ciphertext. And for reading the message must be decrypted for which private key is required and data is encrypted using a secret key, and then both the encoded message and secret key are sent to the recipient .
Blockchain Cryptography
Blocks in blockchain are linked together using cryptography, moreover each block contains a cryptographic hash of previous block. Blockchain itself is secured by cryptography and it is impossible to alter the data once recorded in the block . We can consider cryptography as the backbone of blockchain because an integral part of the inner-workings of blockchain technology.
Blockchain Platform
Blockchain-based applications like centralised, decentralised, permissioned or permissionless blockchain are developed on blockchain platforms.
Number of blockchain platforms are increasing day by day with the increase in dApps because of The growth of dApp development is also another reason that the number of blockchain platforms is increasing day by day.
Below are some leading blockchain platforms :
•Hyperledger
•R3
•Ripple
•EOS
•Ethereum
•Steem
•Fantom
•EOS
•Neo
•Tezos
2. Explain the Public Key CryptoGraphy.
Public Key Cryptography can be defined as class of cryptographic protocols based on algorithms .
It relies on pair of keys to encrypt and decrypt data to protect it against unauthorized access or use. moreover cryptography requires two separate keys, one that is private or secret, and one that is public.
In Cryptography cryptographic code and the address is a hashes version of the public key that is used for depositing the fund.
Public key is generated by private key moreover digital signature can be verified using a public key which is with the use of user's private key digital signature is created.
When there exists agreement between the two parties for a transaction then both receiver and sender exchanges their public keys to each other which is just like exchanging the account numbers of bank.
Your the sender needs to create a digital signature with the use of his private key and then transfers the amount to the receiver and the receiver confirms using the sender's public key .
3. Explain the Private Key CryptoGraphy.
A private key, also known as a secret key is a cryptographic secret of any wallet. Private keys play an important role in symmetric and asymmetric cryptography and cryptocurrencies and At the time of creating wallet both private and keys are generated. Moreover private key is typically a long generated sequence of bits that cannot be easily guessed which one is helpful for the security purpose.
While sending the cryptocurrencies the use of the private key the software signs the transaction without any disclosure , moreover The receiver can only access the funds by decrypting using his private key. To generate the private keys encryption software is used . Private key securely retire keys after their useful lifetime is reached.
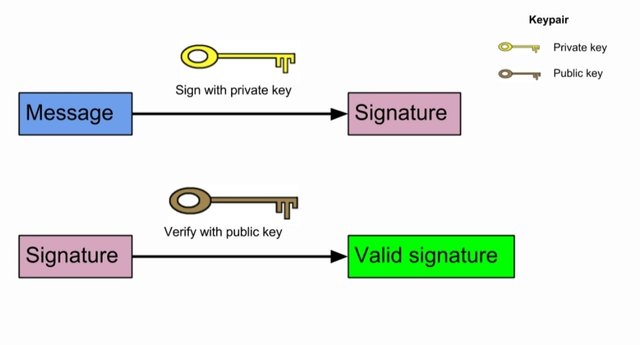
4. Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Digital Signatures CryptoGraphy
Signature binds a person to digital data it is a mathematical technique used to validate the authenticity of a message, or digital document. Digital signature provides the proof of identity and status of electronic documents or digital messages .
It works on public keys and digital signature and technology requires all parties trust that the individual creating the signature has kept the private key secret.
A transaction is digitally signed by creating the hash value of the data, it makes it secure .
Advantages and importance of digital signature cryptography
•security : based on digital certificates, digital signature offers a higher level of security compared to the paper contract.
•Legal validity and Authenticity of message : digital signature has got a legal validity and as the message is verified by using public key show assurety of authenticity of the message exists.
• Better time management : shining of digital contracts takes very less time which in turn is a time saving process.
• Easily accessible anywhere at any time:digital signature brings the advantage of easy access at anytime and anywhere.
Signing Of Transaction
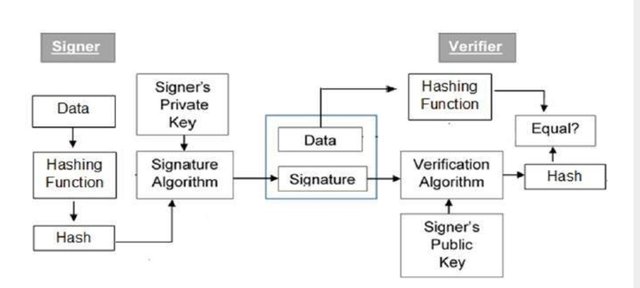
Let's now understand How digital signature is created and verified with the help of the diagram given below:
• Using a Hash function Hash of the data is created
• In the signature algorithm sender of the message digitally sign the message feeding hash value and signature key .
• Being attached to the data signature is sent to the verifier or receiver.
• Public key is entered into verification algorithm to verify the signature for receiving the output.
• To generate a hash value verifier uses the received data .
• The output value received by verification is compared with the hash value on the basis of which whether the signature is valid or invalid is decided.
Data hash of the data is created first and then signed to create a digital signature because the hash has a unique value.
5 .Explain what is Symmetric and Asymmetric cryptography?
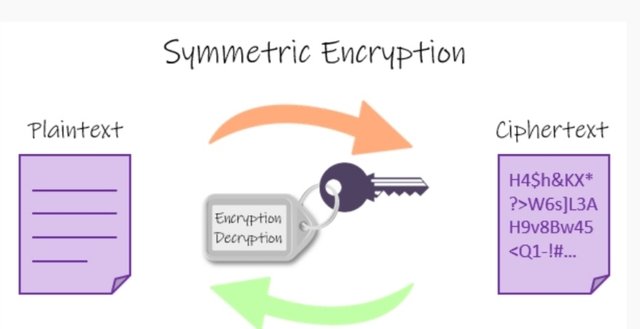
Symmetric Cryptography
In Symmetric Key of Cryptography secret key is used for both encryption and decryption . Due to the absence of private and public key same key is shared which was used to encrypt the data, with another party for data decryption which is also known as secret or private cryptography .
It's a two way process which comprises of two kinds of algorithms Block and Stream . Advanced Encryption Standard (AES) and the Data Encryption Standard (DES) are two common encryption algorithms. A single key is used by all the parties
involved in and aware of and can use to encrypt and decrypt data.
Symmetric keys consists of 128 or 256 bits long, a 128-bit long key has 34x10^37 possible combinations made for the security purpose so that the third party could not crack it.
Areas of usage of symmetric keys:
• Payment applications such as Bank purchases where information PII must be secured .
• validation performed for the ensurance of correct sender which appears to be.
• required for creation of random numbers and hashing .
Advantages and Disadvantages of Symmetric Cryptosystem
Advantages
Symmetric cryptosystem is more effective and no key is sent with the files, the chances of data decryption are zero. A symmetric cryptosystem employs password authentication to confirm the receiver’s existence.
Disadvantages
The main Disadvantage is it is not possible to have digital signatures that cannot be revoked .For a larger group, a large no of keys is required in symmetric cryptography which is another disadvantage of symmetric cryptography .
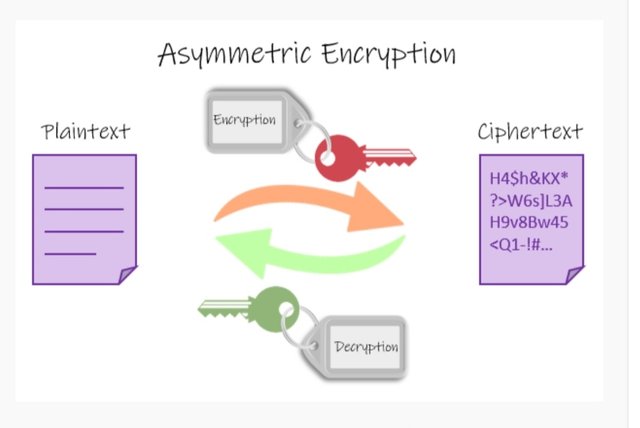
Asymmetric cryptography
Asymmetric cryptography helps to overcome the major distribution issues that arise due to the symmetric encryption process moreover Unlike symmetric cryptography, where a large no of keys are required Asymmetric cryptography is scalable .
Asymmetric cryptography uses two keys private and public key both are related to each other mathematically. The private key or secret key is only known to the key’s generator. The encryption and decryption procedures are automatic and locking and unlocking of messages are not needed by the users. Asymmetric cryptography helps in checking the the authenticity of data using digital signatures.
It is often used in the SSL/TSL cryptographic protocols, which provide encrypted connections between websites and browsers.
Let's take a small example and understand it in a better way.
•Suppose Rahul and Ram wants to share data with each other
• Both have their public and private key with each other and they will share their public key with each other.
• Now when Rahul wants to share any data with Ram he will encrypt data using the public key of Ram and send it to Ram .
•The encrypted data now only be decrypted using the private key of Ram because it is encrypted with the public key of Ram .
•This data only can be decrypted by Ram and even Rahul can't decrypt this data.
Advantages and Disadvantages of Asymmetric Cryptosystem
Advantages
In Asymmetric Cryptography there is no need to exchange keys eliminating the key distribution issue.
Moreover it provide digital signatures that can be revoke. Signing a message digitally is an acknowledgement of the message, the sender cannot reject it.
Disadvantages
The main disadvantage of asymmetric key is loss of a private key can be irreversible. When a private key is lost, all incoming messages cannot be decrypted and security breach is possible when an intruder obtains the person's private key .
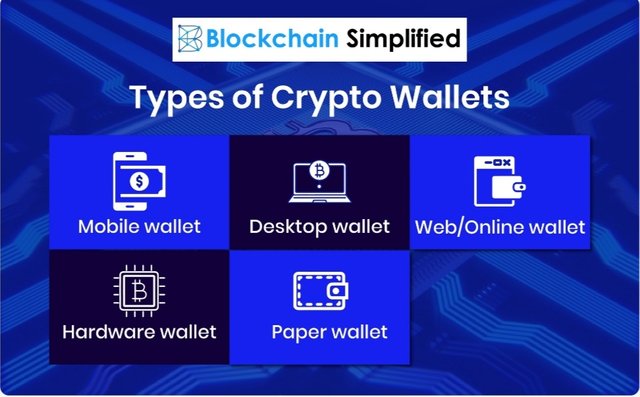
6. How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Blockchain wallet cryptography
Crypto wallets can be defined as type of software that stores private and public keys and can be accessed by their respective keys which is Private or Secret keys through which ownership of the digital assets can be proved. It is used to interact with blockchain network as it consists of an address that is similar to bank account no. Based on the pair of private and public keys an alphanumeric identifier called address is generated. This address specifies the location to which coins can be sent to the blockchain.
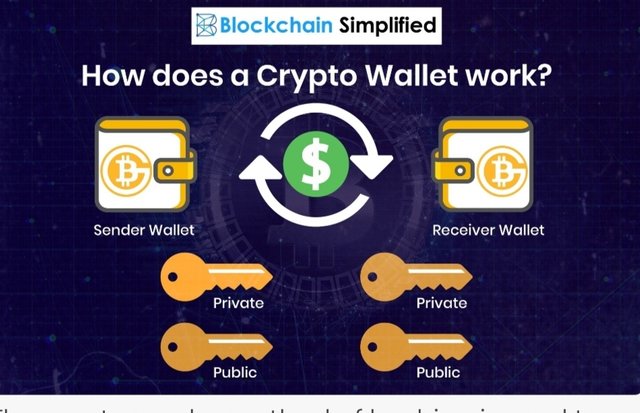
src
Crypto wallets consists of two types of keys which are:
•Public Key it is used to receive funds and with the help of public key of the wallets accounts can be identified on blockchain.
For example the public key I created for the task below
Public key-
04ca34237a3a3fa188528c77c4ccf8fdf53f3fb6987090e625b8edf8006a4bb7386468097a12d75287e780341cd655f106bd206b0a9a394d5d5b1c28de6fbc7664
•Private Key this key of the wallet is only used for signing the transactions and also proving the ownership of the wallet.
Example of Private key-
97100694419927737285063517232101188049315319360051624028696951002890809187139
The three major types of crypto wallets are Hardware, Software, and Paper wallets.
We will discuss each of the wallets in detail below.
Hardware wallets
Unlike software wallets, hardware wallets are
hardware devices that individually handle public
addresses and keys and store keys offline in
hardware devices like USB . Hardware wallets is a battery-less device and can be connected to PC and accessed by native desktop apps. They are more secure and user-friendly than paper wallets , moreover transaction through hardware wallet is as easy as an online wallet but more secure as it stores assets in offline mode, It cost up to 70-150 dollars, but is worth every single penny and they are compatible with different web interfaces and can store various currencies.
Most popular hardware wallets are Nano S and Trezor.
Software wallets
•Desktop Wallets Such wallets are downloaded on PC/laptop and are installable software packs available for operating systems. Desktop wallets are most secure way to store cryptocurrencies and the best method for cold storage and can be accessed only on that particular device .
•Mobile wallet Made for smartphones mobile wallets are easy to operate can be used anywhere. Moreover mobile wallets are quite convenient as it uses QR codes for transactions.They are suitable for daily operations but are vulnerable to malware infection and are comparatively smaller and faster than desktop wallets.
•Online wallets online wallets are a type of cloud wallet which can be accessed from any device and at any place . They are more secure and convenient than the mobile wallet and the desktop wallets . The clouds are hosted by third parties and the private keys are store online .
•Paper wallets paper wallets are physically printed QR coded form wallet and has the highest level of security . Paper wallets are print of private keys and public keys on the paper. They are not prone to hacks and funds can be transferred on the paper wallet by just transferring funds from the software wallet to the public address . A major flaw of Paper wallet is not being able to send partial funds but overall this wallet is good .
Recovery of keys is possible with the help of online or hot wallets whic provide facility to recover the key using seed phrase but in cold wallets without the proper backup recovery is not possible.
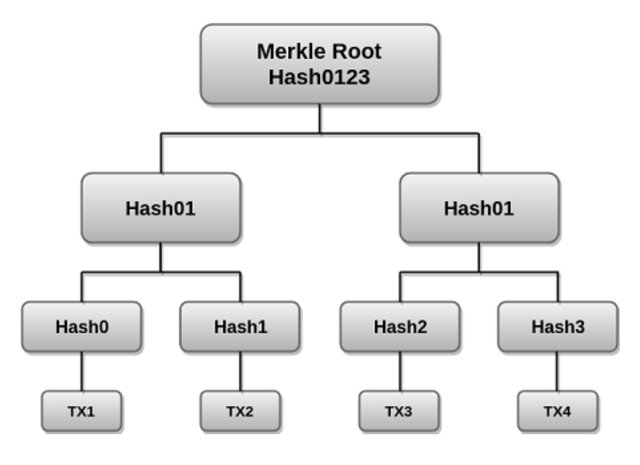
7. What is the Merkle trees and What its importance in blockchain?
Merkle Trees
Introduced by Ralph Merkle in 1979, Merkle tree is a fundamental part of blockchain technology. Moreover a process for verifying data that would allow computers to work much faster than before.
Merkle tree is a mathematical data structure composed of hashes of different blocks of data,
It is the backbone of blockchain and is used in the fundamental's of Bitcoin code . Merkle Tree is also known as Hash Tree ,arranged in a tree-like structure it is a structure of hashes of different blocks of data arranged . Markle Tree is generally a data structure tree in which every leaf node labelled with the hash of a data block, and leaf nodes are the lowest node in the tree.
In the image above you can see the Binary Merkle Tree. There are four transactions in a block: TX1, TX2, TX3, and TX4. Here one can observe a top hash which is the hash of the entire tree, known as the Root Hash, or the Merkle Root. Each of these is hashed at repeated intervals and stored in each leaf node.
Root hash is stored in block header and header gets has in the process of mining resulting in Hash 0, 1, 2, and 3. Consecutive pairs of leaf nodes are generally summarized in a parent node by hashing Hash0 and Hash1, resulting in Hash01, and separately hashing the Hash2 and Hash3, resulting in Hash23. The two hashes (Hash01 and Hash23) are then hashed again to produce the the Merkle Root or the Root Hash
Importance of Markle Tree in Blockchain
Integrity of the blockchain - After the creation of root hash if anything new is changed then call of the route hash will change and the block will become an invalidated . Hence this ensures the the integrity of blockchain .
Enables the quick verification of blockchain data-Markle Tree of that particular block need to be varified to verify any transaction in the blockchain and Markle Tree encodes the blockchain data in an efficient and secure manner.
It is also useful in distributed systems where same data should exist in multiple places moreover markle tree plays an important role in bitcoin and blockchain and they are also used to check inconsistencies.
8. Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
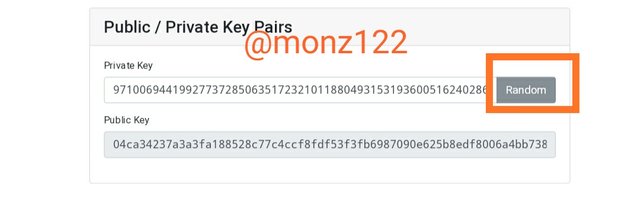
As we all know that asymmetric Cryptography requires 2 key that is public and private key and both the keys are related to each other. taking the help of the private key we can generate a public key. For every new private key there is a new public key because as the private key changes the public key also changes.
Let's understand practically with the image and the example given below
In the above image in the screenshot for any randomly generated private key a public key is generated.
Private key
97100694419927737285063517232101188049315319360051624028696951002890809187139
Public key
04ca34237a3a3fa188528c77c4ccf8fdf53f3fb6987090e625b8edf8006a4bb7386468097a12d75287e780341cd655f106bd206b0a9a394d5d5b1c28de6fbc7664
Whenever I click on a random private key is changed and at the same time a new public key is generated.
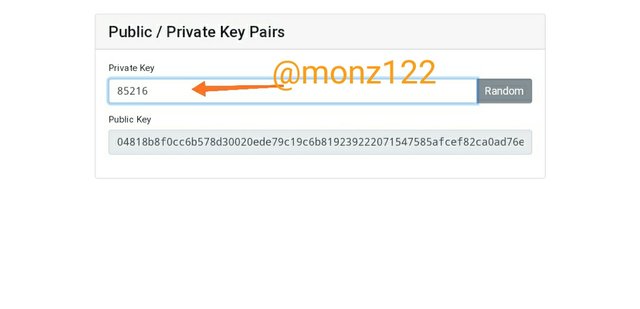
Now I entered another private key and the other key which is the public key changes
As you can see in the image when I changed the private the public key automatically changes.
As I entered private key as 85216 and new public key is generated.
Public key-
04818b8f0cc6b578d30020ede79c19c6b819239222071547585afcef82ca0ad76ee7212bc7b6067e0a695eebf233daf11cc341f299d945cd241112888afd76be11
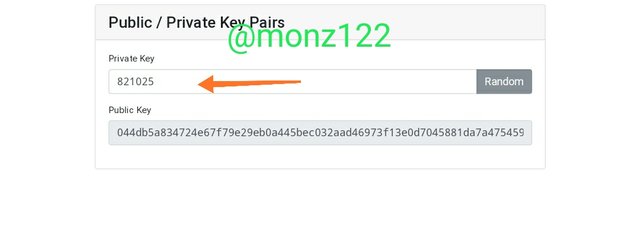
Again if I make a slight change by changing the private key to 821025 the public key automatically changes as you can see below
New Private key -821025
Public key-
044db5a834724e67f79e29eb0a445bec032aad46973f13e0d7045881da7a4754596adef826d44111e6243fdc3be5a4b980906e9f40e275602aa46d513dc76db836
So from the above practical experience it is clear that for every new private key there is a new public key related to it.
Signature
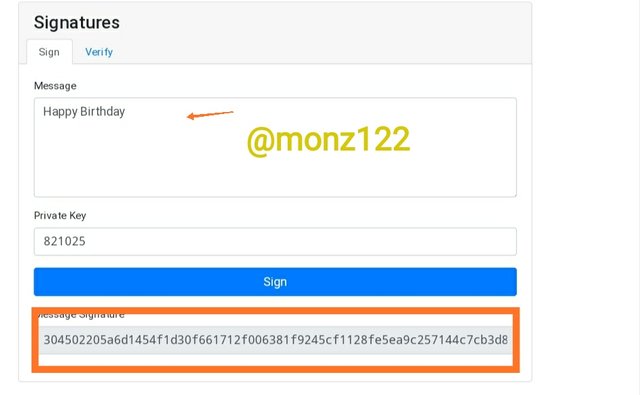
For this section, I will sign the message (Happy Birthday) with private key 821025 I entered manually. Clicked on the sign and the message was signed.
Message signature generated -
304502205a6d1454f1d30f661712f006381f9245cf1128fe5ea9c257144c7cb3d891f66d022100aa174c955a4c575cdafd172f29e39783e619e636ba074edd53feda440cff8d6b
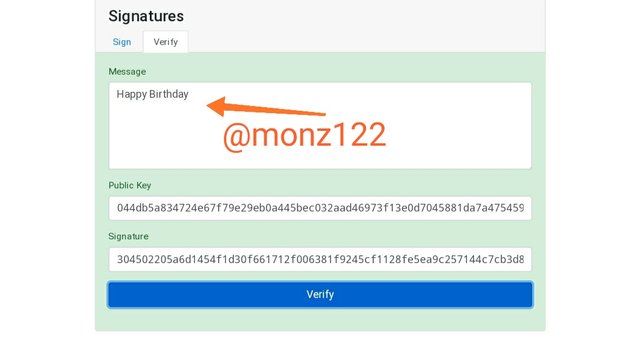
For verifying the message I entered the public key , which was generated by entering private key 821025, and the signature
Now , After entering all the required information clicked on verify, the block become green and the signature is verified.
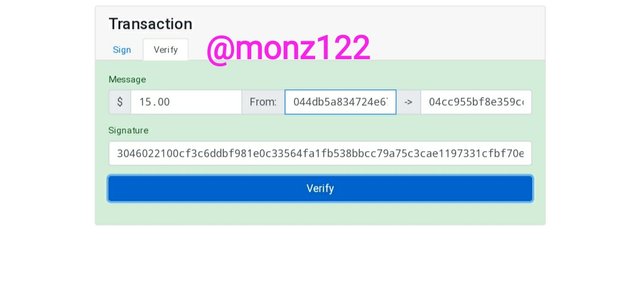
Transactions
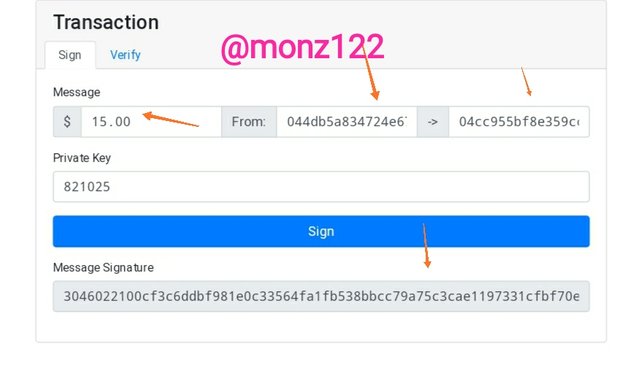
Now Here I will demonstrate a transaction of $15 from one wallet to another.
From wallet address/public key linked to private key 821025
044db5a834724e67f79e29eb0a445bec032aad46973f13e0d7045881da7a4754596adef826d44111e6243fdc3be5a4b980906e9f40e275602aa46d513dc76db836
To another wallet-
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Message Signature
3046022100cf3c6ddbf981e0c33564fa1fb538bbcc79a75c3cae1197331cfbf70e5cd3362e022100a40f917caaa1cbeedaa31d34650f7521db397e85b80b6e83817afe86afec290b
Let's verify the transaction
Now here we have successfully verified the signature as interface become green that shows the transaction is valid. It confirms that the message signature is generated using a private key linked to the public key from the message was sent.
Blockchain
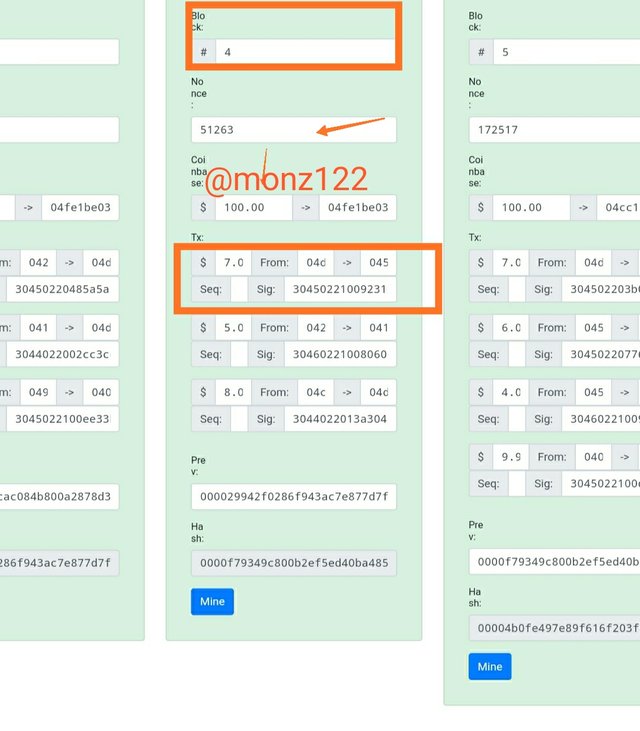
Here we will see how blockchain behaves by altering any transaction in any block. I will demonstrate on block #4.
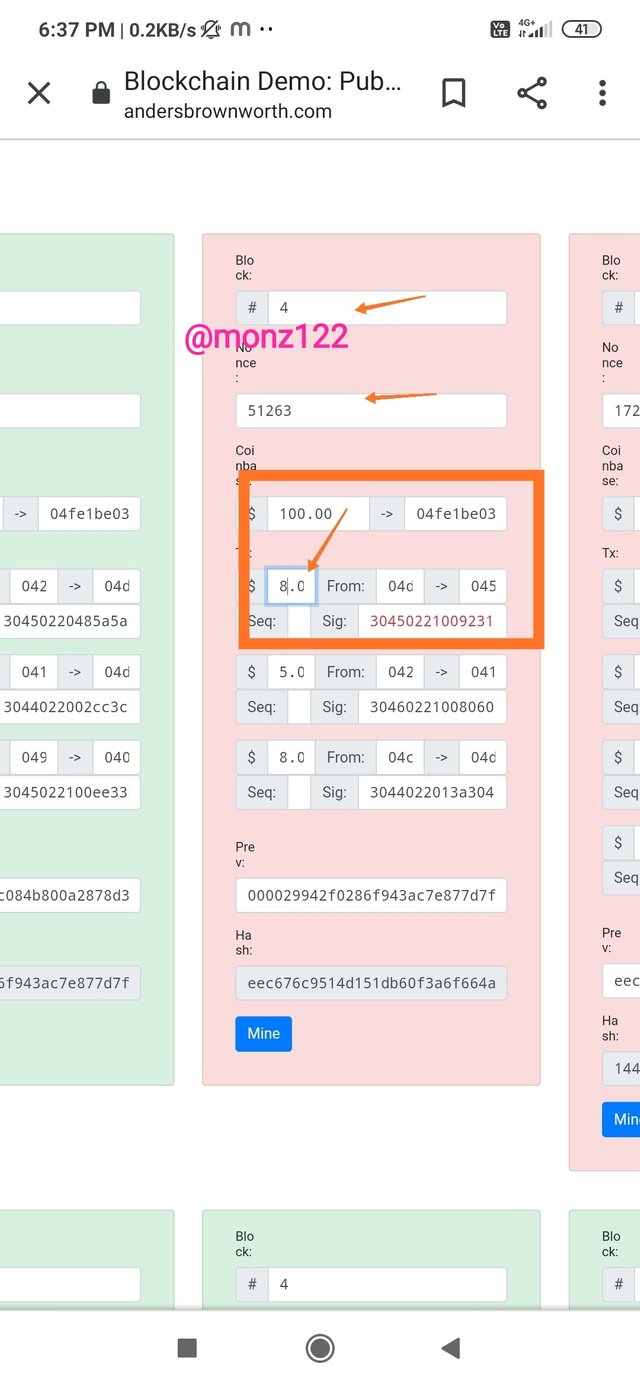
Now just by altering a transaction amount from 7 to 8, the transaction signature becomes invalid which makes the block invalid as well as all blocks after block #5 also become invalid as shown in the screenshot below.
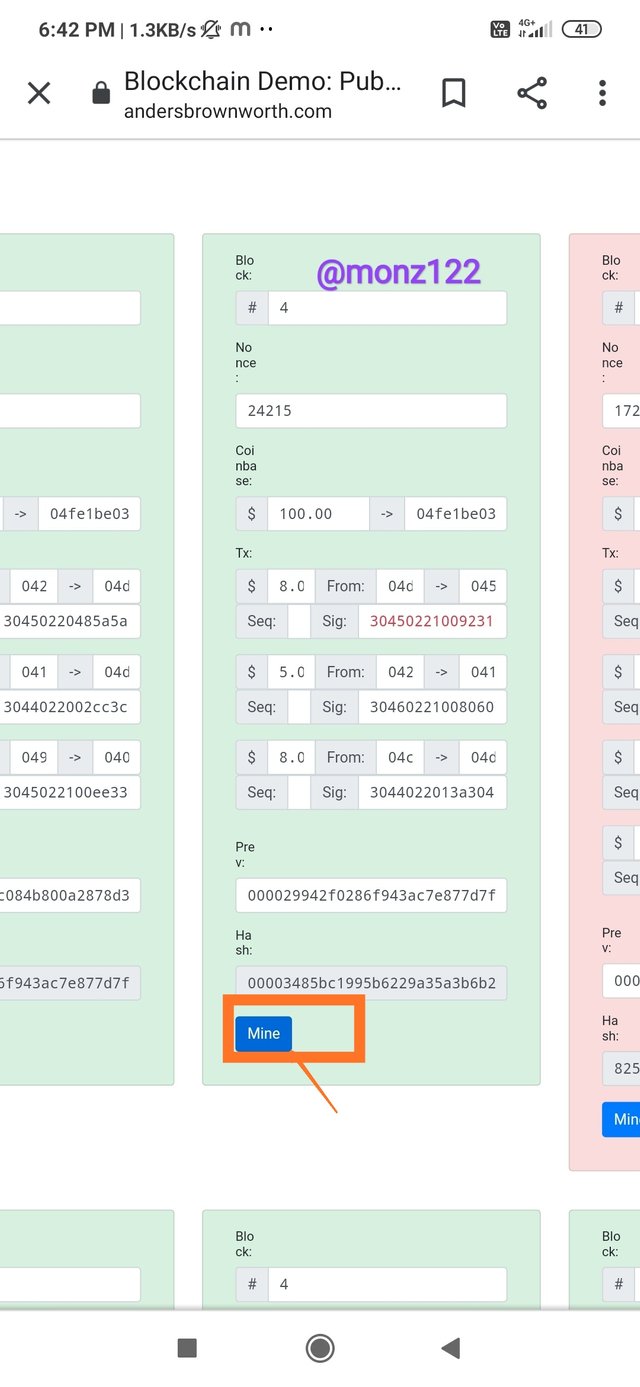
Just by clicking on mine the block becomes valid
Just as we click on mine, the block Nonce changes it becomes green and valid but still signature attached to the transaction which was altered is invalid. It shows that the transaction amount, signed by the private key related to the public key mention, is not correct. All blocks after #4 are still invalid and should be re-mined again .
Conclusion
coming to the conclusion of this chapter firstly I would like to thank our professor @stream4u for giving us this wonderful lecture through which we learnt many new things about the blockchain technology and cryptography.
Without cryptography blockchain would not have been secured like now and it plays an important role in the development of blockchain technology. Hacking with becomes difficult with with the help of cryptography which provide hashes and private and public keys which are in the hands of the sender and receiver which makes the wallets secure.
Moreover I came to know about the Hashes and its functions which I I knew very little earlier and with the help of this homework after doing the research now I came to understand about all the hashes and Nodes. I also came to know about the two forms of cryptography which is symmetric and asymmetric in which I came to know that symmetric Cryptography works only on private key but a symmetric Cryptography works both on public and private key.
I also came to know about the scalability of both the symmetric and asymmetric which is symmetric cannot be scaled and a symmetric can be scaled easily. Blockchain Cryptography plays an important role in in the development of blockchain technology moreover digital signature provides the security and surety and without it signing of messages transactions or document would have not been possible therefore we can say that cryptography is an important part of blockchain technology.
Cc
@stream4u
@steemitcryptoacademy