Crypto Academy Season 3 Week 8 – Homework post for @stream4u.|| Cryptography.
Am glad to be part of this week's lecture,this season has really been amazing. I will also like to appreciate Prof@stream4u for this well delivered lecture. Here is my entry below.
Explain the blockchain CryptoGraphy and mention few names which are the blockchain platforms?
Examples of blockchain platforms with cryptograpghy algorithm.
- EOS BLOCKCHAIN
- ETHEREUM BLOCKCHAIN
- HIVE BLOCKCHAIN
- TRON BLOCKCHAIN
- QOURUM BLOCKCHAIN
Public key Cryptography
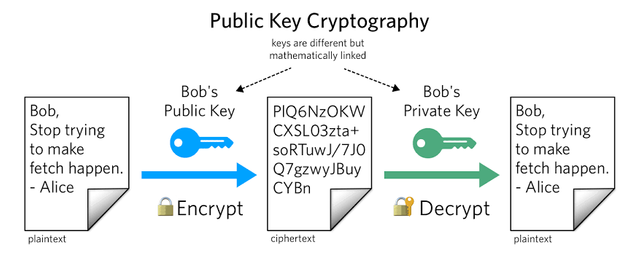
For example.
Weakness.
- communication becomes incomplete without the private key to decrypt, this also affect the algorithm and makes it vunerable
- public key can be vunerable to what we call middle man attack which is of the assumption that the key can be disrupted and modified by a third party and this can lead to loss of the encrypted information
Private key Cryptograghy
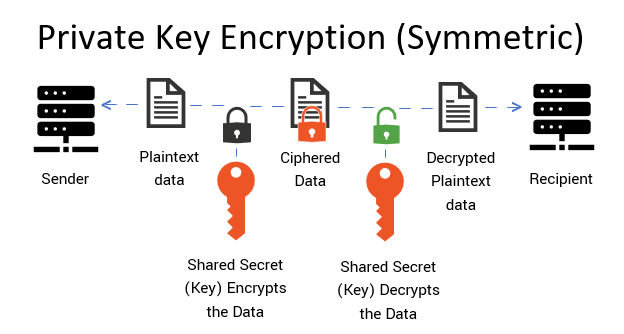
For example.
Weakness
- Key must be subjected to continual updating to avoid been hacked, stolen or leaked
- The loss of the key also means the loss of the encrypted message because the same key is used to encrypt and decrypt
Explain the Digital signature Cryptography and what is signing of Transaction/message?
Signing Process
Explain what is Symmetrical and Asymmetrical cryptography?
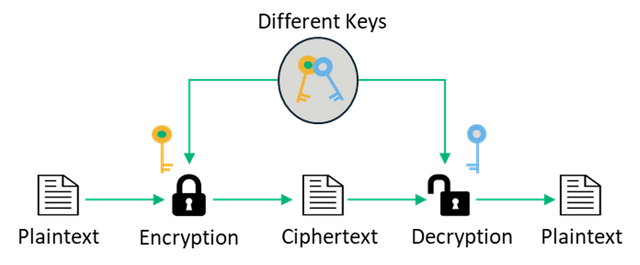
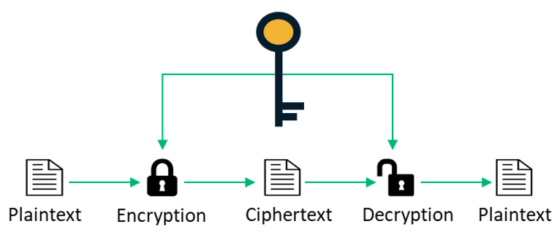
Differences
| Features | Symmetrical | Asymmetric |
|---|---|---|
| Key | only one key is needed for both encryption and decryption of message | Two different keys are needed,one for encrypting and the other for decrypting. |
| Complexity | The encryption process is simple and fast | It’s complex and complicated and the process is slow |
| Length of Key | Length is usually aroud 128/256 bits | Length is usually between 2048 bits as recommended |
| Usage | it is used to send large volume of information/or transaction | it is used to carry out smaller transaction |
How blockchain wallet cryptography works and explain the available types of crypto wallets?
Cold wallet
Hot wallet.
Other types of wallet includes
Online or web wallet
This types of wallet operate only on web and allows users to keep their cryptos on web, although it not a very good place to store cryptos according to experts and so its not advisable to keep all your crypto in a web wallet
Mobile wallets
These are the type of wallet that are supported by mobile phone, these wallets are downloaded and installed on ones mobile phone, you can store your cryptos in the downloaded app and even transact using your mobile phone.
Desktop wallet
Desktop wallet are wallet that is operated on a desktop, according to my research it’s a more secured way of storing your cryptocurrencies when compared with the mobile or web wallet and that is because its an offline kind of wallet which is characterized by it high level of security.
What is merkle trees and What its importance in blockchain?
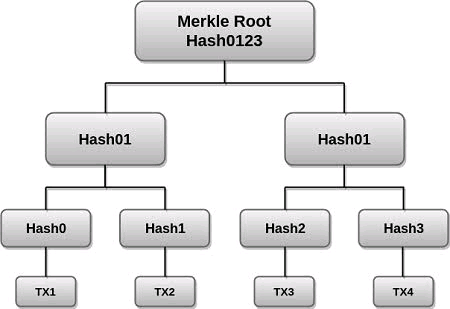
Markle tree structure
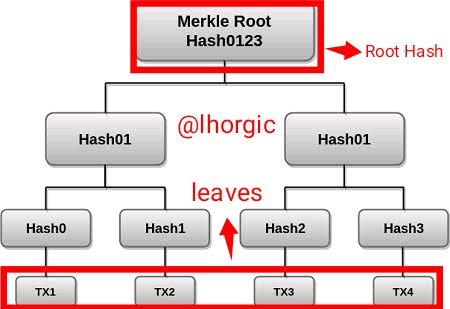
The last transaction is spotted from the level below and it's called the leaf level. The transaction in the level below is then tied to what we call the parent hash above which in turn is tied to the level above and it continues like that till we get to the single one at the uppermost part of the tree called "Root Hash". This root Hash contains the information from the bottom to the top and can be used to trace the remaining transaction.
Importance of markle tree.
- It helps organize block/hashes in an orderly manner.
- It allows for easy payment verification of a particular hash/block without the stress of going through whole block.
- It helps preserve blockchain integrity and immutability.
- It helps to quickly locate transaction on the blockchain especially when it is tampered with or exposed to threat.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private keys & Signing and then explain the functionality of key, signature, transaction, blockchain with proper screenshot of your practical. (Do study well for this topic)
My Task
Key Section(Private/public)
Step 1: I click on the menu with the three parallel lines and clicked "Key"
Step 2: I was shown an interface where with a private and public key paired with each other.
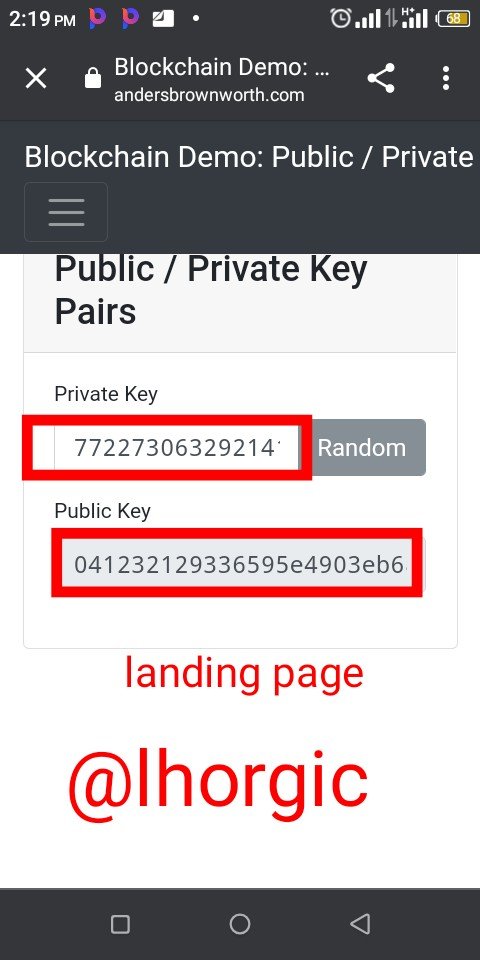
My aim in this section is to explore how the private key plays a vital role in generating a public key which it is paired with and can function with.
Step 3: I inputed 4 as my private key.
Result: it generated for me a private key which is seen below
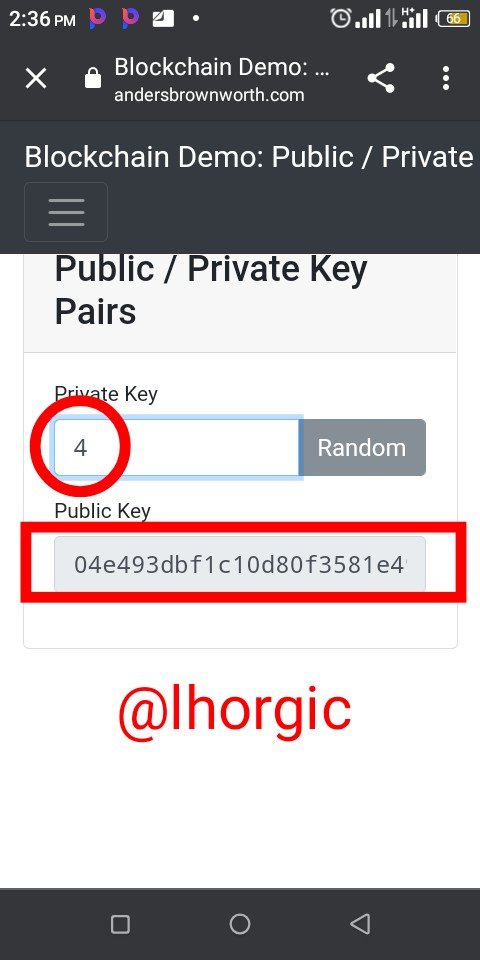
04e493dbf1c10d80f3581e4904930b1404cc6c13900ee0758474fa94abe8c4cd1351ed993ea0d455b75642e2098ea51448d967ae33bfbdfe40cfe97bdc47739922
I went further in my exploration to understand the process better then I inputed 5 as my private key.
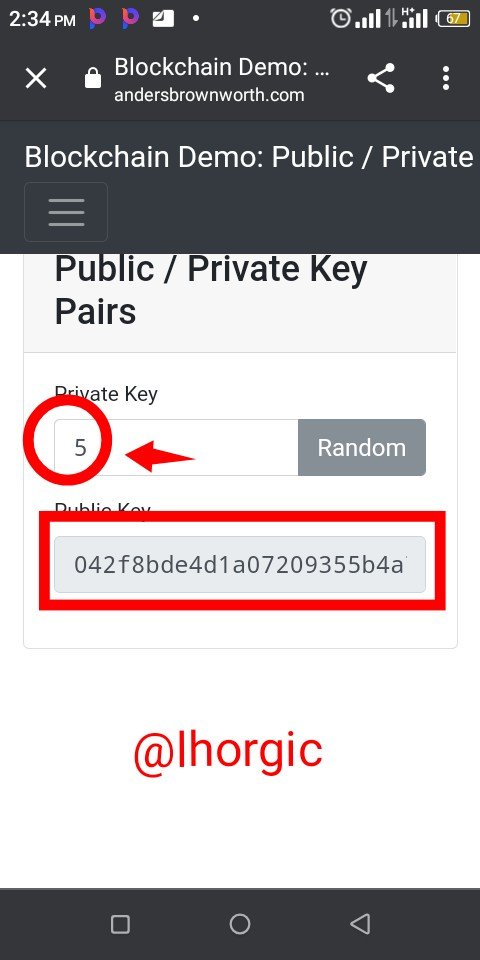
Result: a public key was generated for this likewise which is seen below
042f8bde4d1a07209355b4a7250a5c5128e88b84bddc619ab7cba8d569b240efe4d8ac222636e5e3d6d4dba9dda6c9c426f788271bab0d6840dca87d3aa6ac62d6
Functionality.
In my observation I discovered that the private key I inputed actually generated for me the public key needed to carry out transaction.
Signature section.
To demonstrate my understanding in this section,I will like to maintain the private key "4"
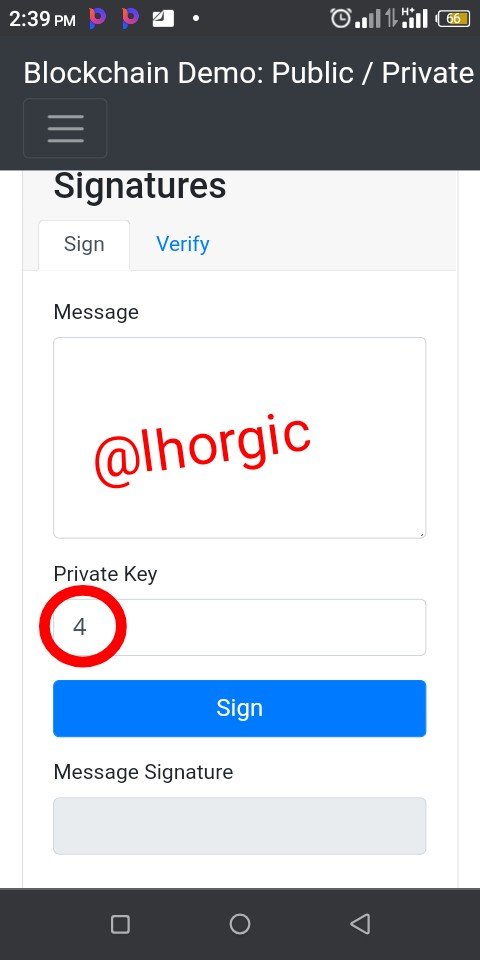
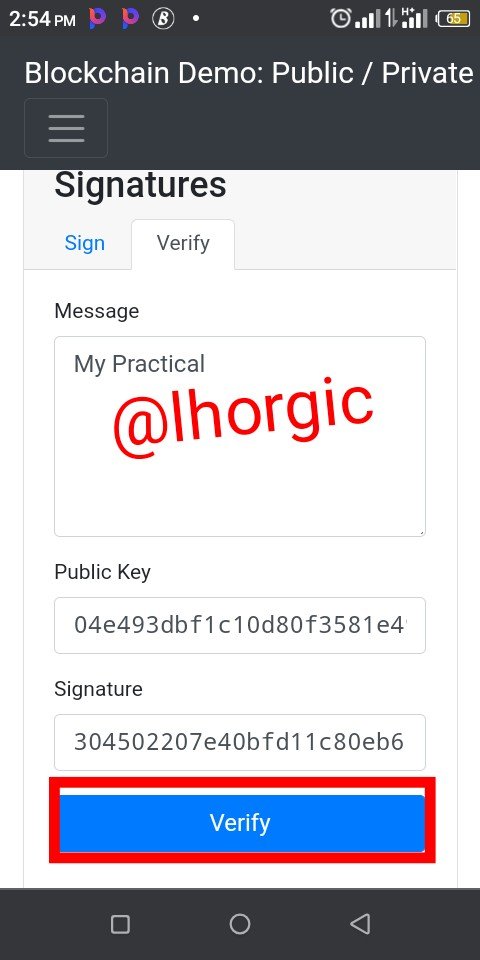
Step 1: I entered my message which is "My Practical"
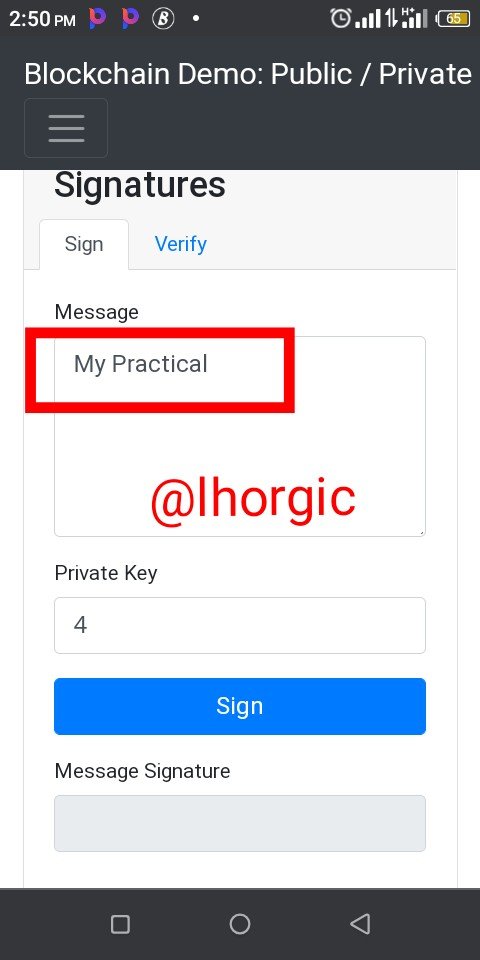
Step 2: I then clicked on "sign". This is possible because of my private key which is already inputed.
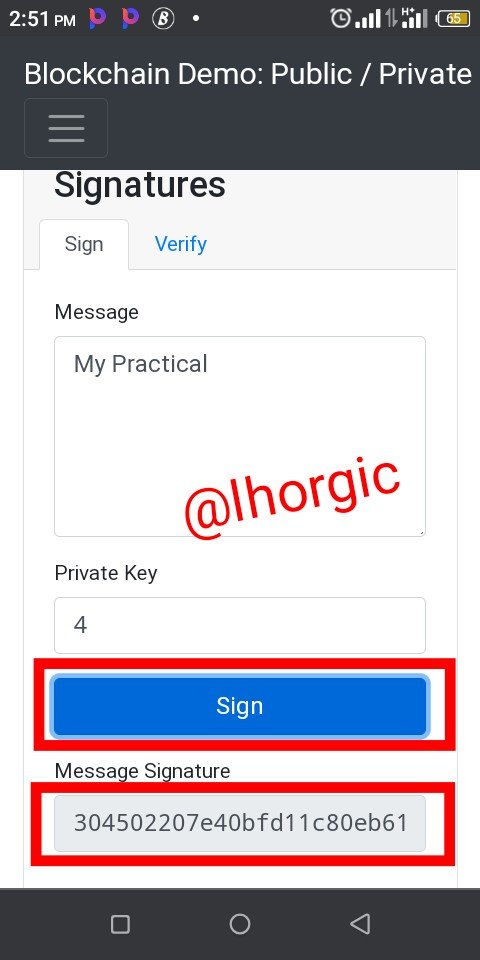
Step 3: My message signature hash was generated
304502207e40bfd11c80eb615ea7dc9361596a60537c16d48dd26bfc35a0b46f7b3e3ff1022100e8a82d713217f88c86daf4a09bd67e8850c04b11574b211484a1ae75af7a056f
Step 4: I clicked on "verify" and this helped me generate my public key instantly
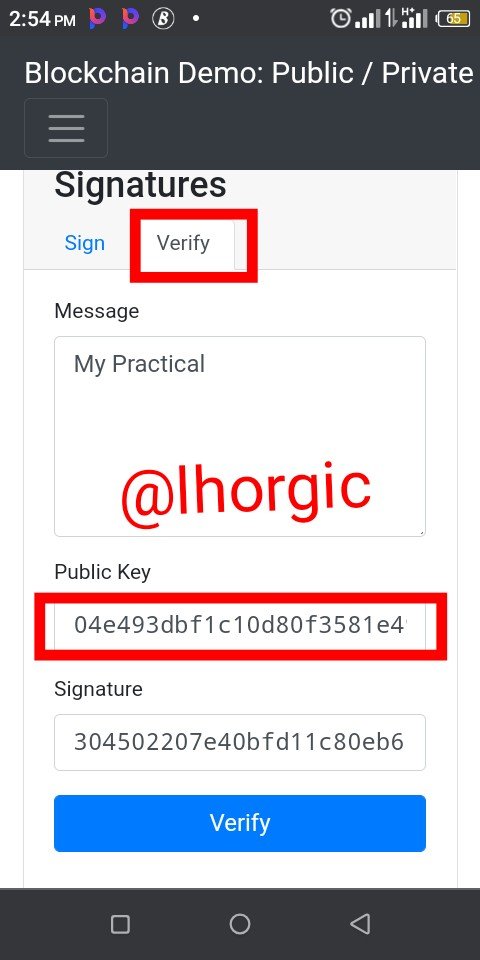
04e493dbf1c10d80f3581e4904930b1404cc6c13900ee0758474fa94abe8c4cd1351ed993ea0d455b75642e2098ea51448d967ae33bfbdfe40cfe97bdc47739922
Step 5: I finally clicked on "verify" and the transaction came out successful,I knew this because it was confirmed with the green interface.
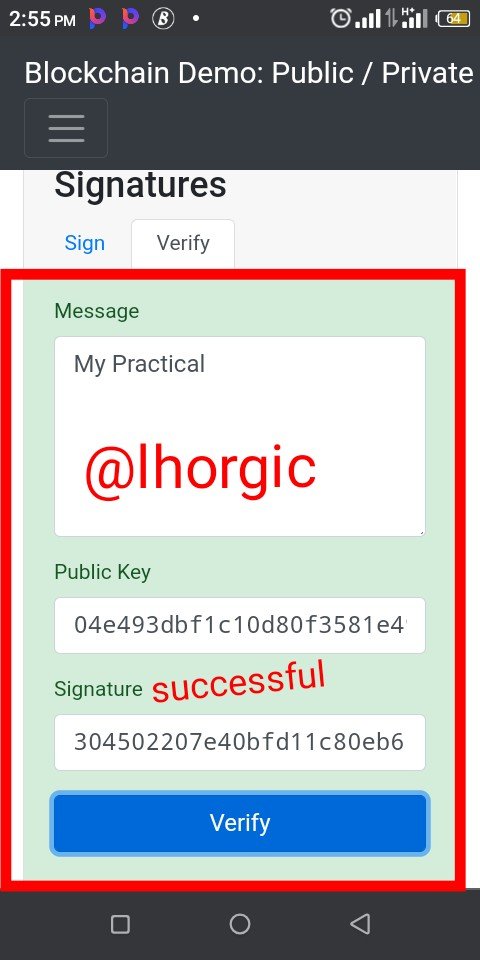
Note: Red colour gotten in the course of transaction means wrong/unsuccessful transaction while the green means successful transaction.
Functionality
- The private key enabled me to "sign",therefore it is used to sign a transaction.
- Signing with my private key led to the generation of my message signature
- Signing a transaction validate the transaction by the sender.
Transaction Section
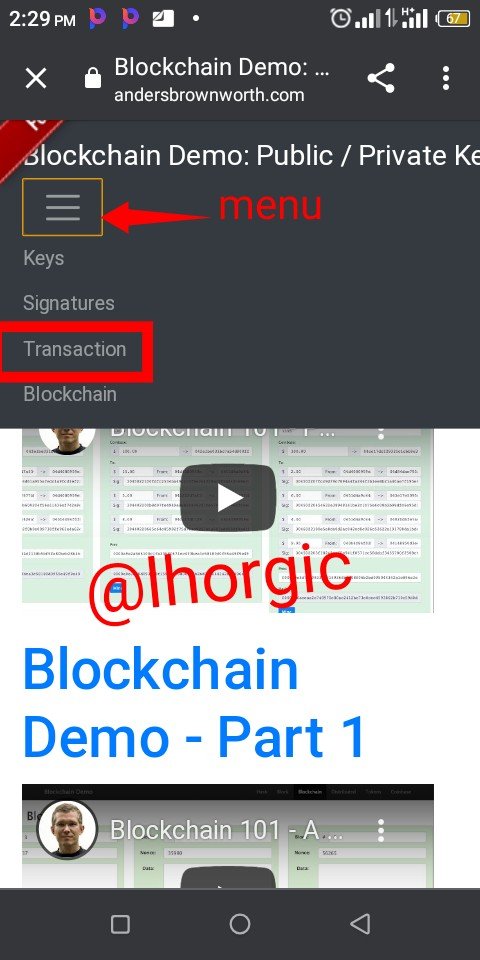
The landing page has some information already supplied as example. Let us carefully examine what we have here.
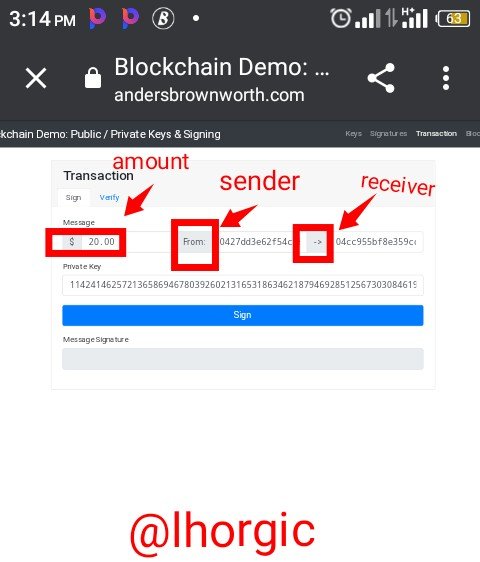
- From: this is the address of the person initiating a transaction,he is the sender and his address is what we have in the box
- To : this is the the receiver who makes the transaction complete and his address is what we have in the box.
- $20: this is the amount that the sender want to send to the receiver,it's the message in this case.
Let's do our practical.
Let's assume these are the address of the parties that want to transact below
Senders address
0427dd3e62f54c58f68219bbffc5ccc76629db5f8424f4cea696e6c78be936e073eb77e757ea18ac1870ddd822c1de5095b10dad3980d01bb1132472c1e47c0053
Receivers address
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Step 1: I will click "sign" using my private key which authorizes me.
Step 2: my message signature is generated for my transaction
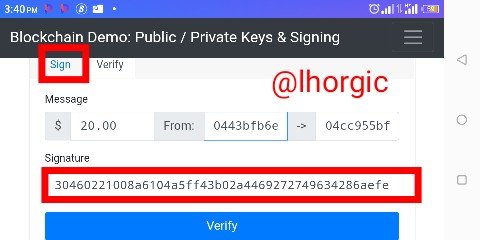
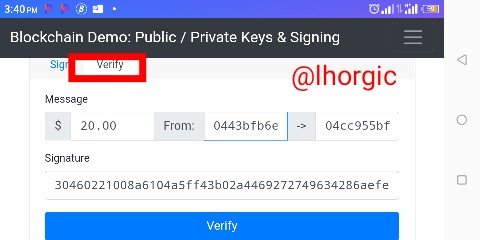
Step 3: I will then click on "verify" above
Step 4: it bring me to the final phase where I finally verify to validate my transaction.
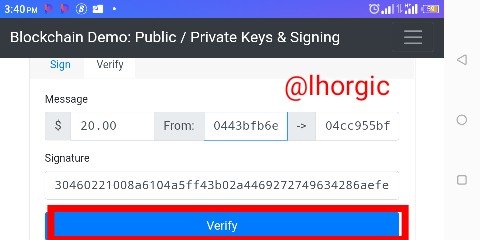
Step 5: the transaction was successful,I knew this because the interface became green.
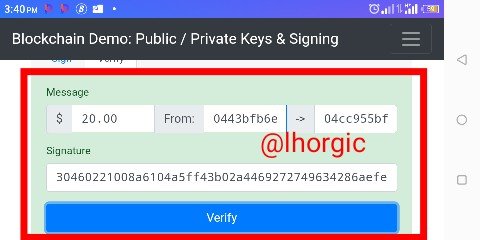
Blockchain session
From my observation,the blocks are already mined successfully and are arranged sequencially that's the reason why we have the green Colour we could spot from the screenshot.
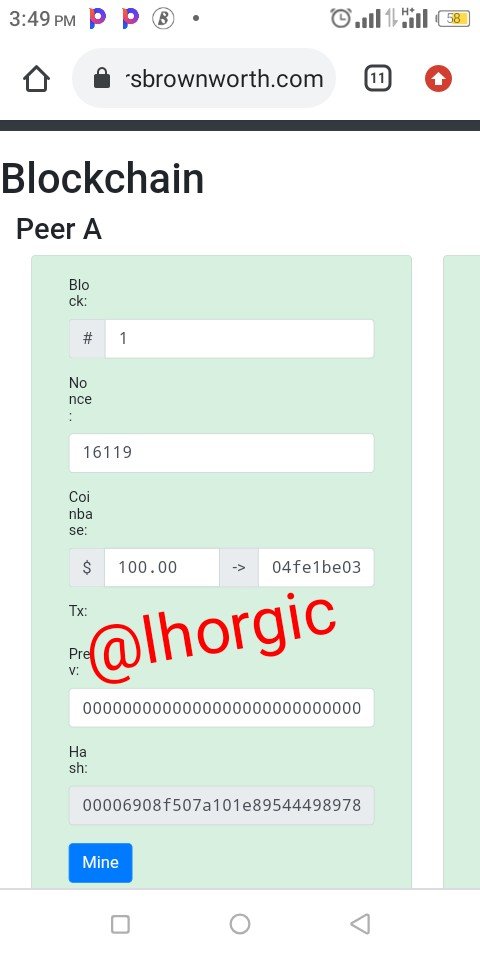
On the other hand,out of curiosity I tried tweaking the block number and then everything got distorted making it come out in red,meaning whatever I planned to carryout wasn't successful
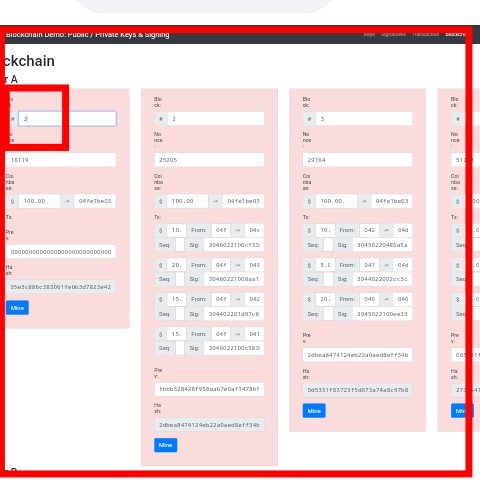
This are the result I got from exploring the demo blockchain,I just hope this meets your expectation.
Conclusion.
Thanks for the lecture well delivered I hope you find my entry interesting.
Cc: @stream4u