Crypto Academy Week 3 Homework Post for [@sapwood] (100% powered up)
Hope everything will be fine especially my brilliant professor @sapwood , in this third week we will be dealing with an interesting new topic related to wallet decentralization and what is its contribution that made to the world of cryptocurrency. Enjoy your reading and feel free to leave your comments below.

What is a wallet?
A wallet refers to a supposedly secure storage solution for cryptocurrencies. Desktop wallet, hardware wallet, web wallet ... Several types of process coexist.
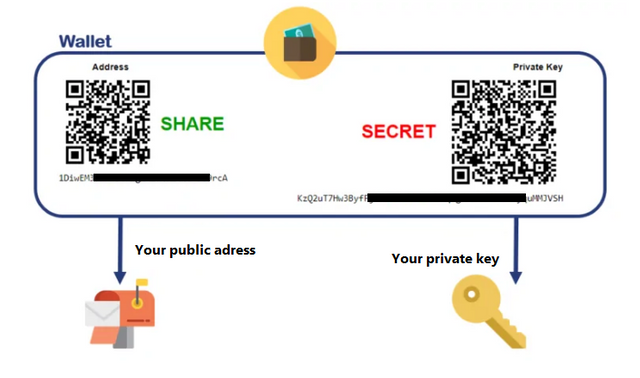
The name wallet covers different storage methods. But in practice, a wallet - whether it is client software, an application, an encrypted and secure file or a simple piece of paper - almost invariably incorporates two elements: a public key. , known to all and corresponding, for example, to a bitcoin address, or to the address of another cryptocurrency, and a private key, known only to the owner of the wallet. This key is used to sign transactions and to prove to all the peers of a network that one is indeed the owner of a particular amount of a cryptocurrency.
Which wallet to choose?
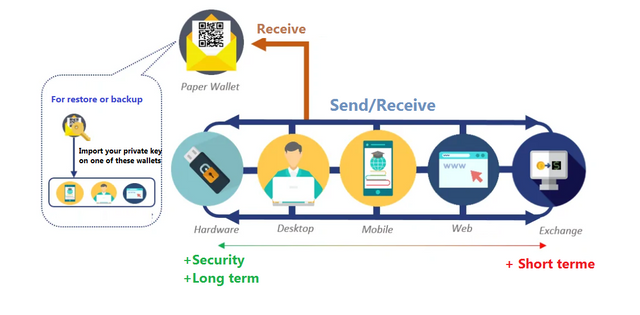
A wallet can take the form of a mobile application, present on a smartphone. This practical solution makes it possible to make purchases online, but also in the physical world, from merchants who accept payment by means of a particular cryptocurrency. But it is also risky, in that it exposes the owner of this type of wallets to the disappointments that can constitute a hacking or theft of smartphone. It is therefore strongly recommended not to store large amounts of cryptocurrency on this type of application.
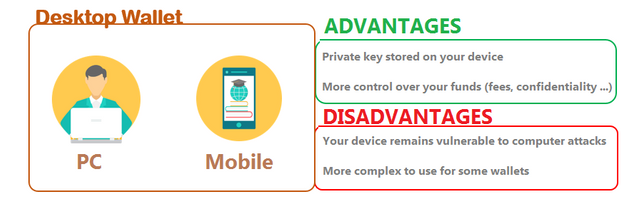
The wallet can also take the form of software that you install on your personal computer. We then speak of "desktop wallet". Regardless of the level of security of this type of wallet, its user must always ensure that the computer that hosts the said wallet is not vulnerable to viruses, malware and other digital infections of the same type.
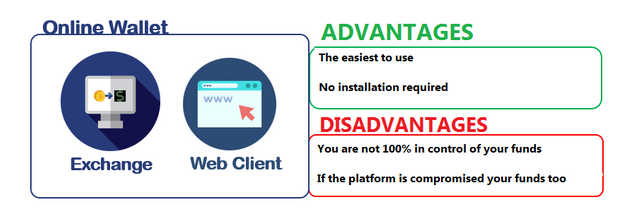
Another variant, with the hybrid wallet: installed on a personal computer, this type of software allows exchanges between different cryptocurrencies. The web wallet (or cloud wallet) is, for its part, a cryptocurrency wallet that is installed remotely, at a service provider, wallet supplier. Here, what can turn out to be extremely risky is that the user delegates the securing and safeguarding of his wallet to a third party.
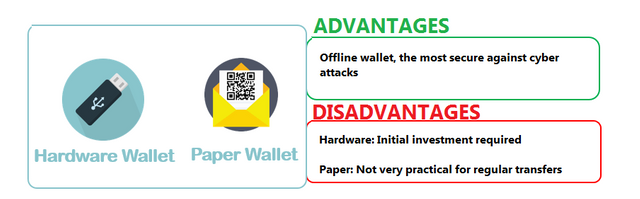
Another solution: the hardware wallet. These are devices offering an optimal level of security in that they store the private keys on an onboard chip, the processor being the only one capable, independently of a computer, of signing a transaction.
The paper wallet can be generated offline. You then write down your public key and your private key on a medium that you put away. This wallet can then receive the corresponding currency without it being connected to the Internet network. It is the safest way to keep your crypto-currencies. That said, this type of wallet also has the major drawback that it cannot be used to make outgoing transfers. To be able to do this, you must import your private key into a wallet (desktop, mobile or web client).
My advice on which one you choose :
Don't put all your eggs in one basket. For example, you can store your cryptos on a hardware wallet which would be a bit like your personal safe, keep some on the platforms to be able to trade with, put some in a mobile application to spend on a daily basis like if you put a few bills in a wallet, and to give gifts, go to paper format, much like writing a check. All of this is managed and measured. There will always be some risk, but it's up to you to reduce it as much as possible.

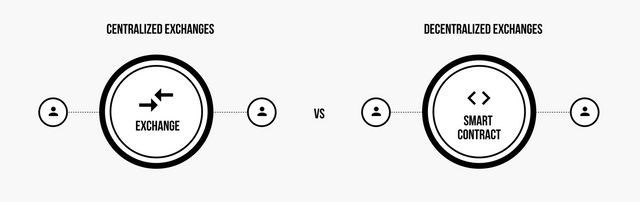
Exchange Wallet(Centralized) & Decentralized crypto wallet.
Source
Cryptocurrency exchanges are the foundation for the development of the Internet of Value. A cryptocurrency exchange provides a gateway to a world of hundreds of digital assets that can be traded peer-to-peer and used to access a multitude of payments networks and decentralized applications.
For many users, their first cryptocurrency purchase will have been made on an exchange, so it's no wonder that some platforms have become industrial giants.
Ironically, however, for an industry that emphasizes decentralization and the ability to transact without a middleman, centralized exchanges play a crucial role in market growth.
As centralized exchange platforms have accumulated a lot of wealth and power over time, some people have questioned whether this vocation to "decentralize the world" had not been compromised by excessive centralization. Large, centralized platforms have the same security and privacy loopholes, and censorship issues, that traditional financial institutions have.
Decentralized exchanges are an alternative solution more in line with the original philosophy and values of cryptos with regard to security, privacy and autonomy.
How do you secure/restore Exchange Wallet(Centralized) ?
To secure access to your account, and therefore access to your assets that you have deposited therein, the platforms provide you with various tools in addition to the mandatory password. I strongly recommend that you enable as many security options as possible.
- Secure password (required by default)
- Two-factor authentication 2FA adds a layer of security, which is essential (in my opinion)
- Complete the KYC. If you lose access to your account, having completed the KYC can greatly facilitate its recovery
- Connection notifications. Each time someone logs into your account, a notification will be sent to your email address or mobile. So, if you receive one when you were not the source of it, you can react as soon as possible. If this were to happen:
--> Change your password
--> Withdraw your assets
--> Contact the platform - The PIN code . It is a code with several digits that can be used to further secure operations carried out on the platform such as withdrawals, purchase or sale of assets ...
- The anti phishing code or anti-phishing code that is used to verify the authenticity of an email. Once configured, if this code does not appear on the email supposedly coming from the platform, there is a good chance that this email is fraudulent.
- A whitelist of IP addresses. I only recommend activating this option if you are familiar with it. This will only authorize the IP addresses previously entered on the platform. This assumes having a fixed IP
Finally, as soon as you have finished using the platform, you log out of the account by clicking on "log out" or "disconnect". You don't leave your session open!
How do you secure/restore Decentralized crypto wallet ?
A Mnemonic Phrase :
While setting up the wallet, you are prompted to save a 12 word recovery phrase. As said, this phrase gives full access to the funds in the wallet and should be kept safe. On the one hand, it will be useful if you lose access to your device (breakage, loss, theft) or if you forget your password. On the other hand, it can also be used to pair several devices, that is to say to make your funds accessible from several different devices (a computer and a smartphone for example).
A Keystore File :
This method consists of creating a backup file containing your private keys.
First choose a password. This password will be used to encrypt the file. It must therefore be complicated enough to withstand brute force attacks: contain capital letters, special characters, etc.
You will then need to save the file to your computer. Try copying this file to one or more other media, such as a USB key.
A Private key
The private key is a 64 character string permanently linked to a public address. This is sometimes provided to users when creating wallets and is sometimes kept encrypted (in the case of the MEW wallet application, MetaMask, and hardware wallets). Using your own private key should always be a last-ditch effort, only to be used when all else fails. This should not be the primary method of access for anyone who can access their wallet. Private keys are the most sensitive information anyone can have for a wallet, because private keys allow instant access and cannot be changed. Hence, it is extremely important to keep it safe, secure and secret.

Web 3.0 :
1.0 corresponds to the beginnings of the Internet and then to its development thanks to browsers, with the main use for the user to benefit from the available data and to multiply them. 2.0 sees the arrival of social networks, the user interacting with the content and thus generating a large amount of data. Thanks to the blockchain, we are now arriving at Web 3.0, that of transactions, which allows the exchange of values, transforming the Internet user into a consumer and economic actor in the internet sphere.
Why did I choose Metamask as a web3.0 wallet?
In the evolving Ethereum universe, MetaMask's offering is seen as a pioneering project. This is a dedicated wallet for ETH and ERC20 tokens, but not only. Its system also allows direct interaction with decentralized applications (Dapps) that populate Decentralized Finance (DeFi) for example. Which makes it a web3 type wallet.
MetaMask’s service does more than just manage user ERC20 funds. Its formula is very clearly focused on respecting private data. The latest V8 update of the project thus allows the user to fully manage what websites may or may not have access to when logging in to the application. It is also possible to create specific accounts for certain sites in order to control the data concerned.
MetaMask also benefits from a very powerful anti phishing system that is directly integrated into the tool. All linked to a list of corrupted websites that is regularly updated for optimal security. This is not to mention the fact that MetaMask keeps the private keys related to funds held to prevent theft by a malicious site.

Cc:-
@steemitblog
@steemcurator01
@steemcurator02
@sapwood




Thank you for attending the lecture in Steemit-Crypto-Academy & doing the homework task-3.
Excellent, I simply loved reading this piece.
In time, Web 2.0 will become obsolete. Even the semantic web (the idea behind web 3.0) fits perfectly in a decentralized technology like Blockchain. The kind of infrastructure web 3.0 applications need can only be supplemented with Blockchain infrastructure.
That said, we have already witnessed how the Blockchain wallets and their use have gone Web 3.0 at the end of the decade. They are now more popular than any other types.
Matamask is definitely one of the popular Web 3.0 wallet and DeFi has further galvanized the use-case of a Web 3.0 wallet.
Thank you.
Homework Task -3 accomplished successfully.
[8.5]
Thank you Sir,@sapwood for these valuable adding.
Interesting and very good explanation about the wallets. I will take note of these tips.
Regards.
Welcome!
Twitter promotio