Crypto Academy / Season 3 / Week 8 - Homework Post for [@stream4u]--Let's Open the Cryptography.
Hey everyone, i am so excited for this week's crypto academy lecture on Cryptography by @stream4u. It was a good and detailed one because you took your time to explain. So i will go ahead to attempt the homework task.
Explain the Blockchain CryptoGraphy and Mention few names which are the Blockchain Platforms?.
In my own understanding, CryptoGraphy is a process at which messages can be altered in a way that it is hidden even in the presence of a third party. It is the study of secret writing that uses numerical techniques to protect information that are found in an unreadable format such that only the receiver of the information can understand and convert the information to a readable one with the help of the encryption and key method.
Let me give an instance of how CryptoGraphy works. Now user A wants to send a message to user B, user A first converts his message from a readable format to an unreadable format using some random numbers and uses a key to encrypt the message. As this encrypted message passes through the communition channel, he doesnt worry about any third party seeing this message. Now, for user B to receive this message, he needs a key also to decrypt the message and convert it to a readable one. However, when the message comes out as an Error, user B knows that the message he has received is not what A has sent, which means that it has been tampered with, but if not, user B gets the exact message by using his own private key to decrypt the message.
The blockchain Platforms.
- Steem Blockchain
- Ripple Blockchain
- Ethereum Blockchain
- TRON Blockchain
- Hyperledger Blockchain
Explain the Public Key Cryptography.
Public key cryptography also known as asymmetric key is an encryption technique that makes use of two pairs of keys (public and private key) to encrypt and decrypt information. Here, the sender of the information uses the receiver's public key to encrypt the information while the receiver uses his private key to decrypt the information. The Rivest-Sharmir-Adleman algorithm is one of the popular cryptography system that allows both public and private keys to be used to encrypt information so that it can not be altered.
Algorithms used to generate public keys are:
- Rivest-Shamir-Adleman(RSA)
- Elliptic curve cryptography
- Digital signature algorithm
Properties of Public key CryptoGraphy
- it make use of two different keys to encrypt and decrypt messages.
- The receiver possesses a private key thats use for decryption and also a public key for encryption.
- The encryption algorithm is well protected that cyber hackers can not attack.
- The private and public key can not be calculated to be same even if they are mathematically related.
Benefits
Public Key Encryption: this helps to protect an information and ensures that messages are not been altered. Here, the message is been encrypted with the receiver's public key and can not be accessed by anyone who doesnt have the receiver's private key.
Digital Signature: this provides a digital signature in which a message is been signed with a sender's private key and can only be verified by anyone that has the sender's public key. So this ensures that the message is not tampered with. Non-repudiation systems uses this function to ensure that the sender can not deny sending the message.
Limitations
Speed: The public key cryptography is usually slower than other methods in the sense that the encryption and decryption process works with two different keys which are mathematically complex so it takes more time for the process to be completed.
Compromised certification authorities: The certification authority which is also known as the third party can be compromised and false information can be sent to the receiver.
Explain the Private Key Cryptography.
In the case of a private key cryptography, it makes use of a single private key for both encryption and decryption of information. It is usually a fast process because of the single key that is been used. It is also known as a secret key that is shared by only the generator to the other party to decrypt an information.
Moreso, the private key is relatively long and can not be guessed, its complexity and length makes it hard for hackers to find it. Now, private key works in a way that encryption softwares generates new key randomly and once they are generated, it is important to store them securely. However, due to the fact that this key involves exchange to be able to encrypt and decrypt information, it is very important to do this exchange with trusted parties.
Advantages
- Faster: private key cryptography works faster because it makes use of just the private key.
- More secured: when the keys are longer and randomized, its very hard for the information to be tampered with.
- Works for stream and block ciphers: the private key works for stream cipher one bit at a time while the block cipher uses the private key to set information in blocks.
- Best for encryption: private key are used for cryptographic processes to encrypt and decrypt information.
Limitations
- Continual updating: if the private keys that are used to encrypt data are not updated continuously, they can easily be hacked.
- Recoverability and loss: if a private key that has been used to encrypt data can not be accessed, the data can not be recovered.
- Overall Management: when the private key are not managed properly, cryptographic keys can be lost or corrupted.
Explain the Digital Signatures CryptoGraphy and what is Signing of Transaction/Message?
Digital Signatures is a type of electronic signing that is used to verify uniqueness and integrity of an information. It makes use of the sender's private key in the sense that it confirms that the sender actually sent the messages. Moreso, it increases trust between business partners and customers due to the high rate of transparency.
Digital signature works in a way that it proves that a message is not altered from the time it was signed to when the receiver receives it by generating unique hash for the messages and using the sender's private key to encrypt this message. However, the hash that is been generated is totally unique to the information as changing any part will alter the hash.
Furthermore, once the message has been signed and sent by the sender, the receiver generates his own hash of the message to be able to decrypt the sender's hash using the sender's public key. So the message becomes authenticated if the receiver compares the his own hash with sender's hash and found them matching.
Advantages
- The private key can not be generated from the public key.
- The signature is unique to each message so it can not be forged.
- if the message is altered, it can easily be detected with the digital signature.
Signing of Transaction/Messages.
Signing of a transaction involves different digital signature which depends on a user's private key and with the public key and signature of the user, the message or transaction can easily be verified that the sender sent the message. So once the message or transaction is been signed by the user, the transaction goes in to the memory pools and waits for the miners to pick it up, once the miner picks it, he verifies the digital signature on the transaction using the sender's public key so as to avoid hackers from altering the transaction made. However, if the transaction ends up being valid, then the digital signature is verified and the transaction or money is then sent to the designated wallet and the transaction is then added to the block.
Explain what is Symmetric and Asymmetric Cryptography?.
Symmetric Cryptography
Symmetric Cryptography is based on the use of a single key which is shared to all the parties involved in the transaction and can be used for both encrypting and decrypting information. This is the opposite of asymmetric cryptography, the data is been converted to a format that can not be translated by anyone that does not have the secret key that was used to encrypt it. The few popular symmetric cryptography used are AES-128, 195, 256.
Moreso, its algorithm is usually fast when carrying out a transaction as it has a lower computational intensity. the symmetric cryptography generates random numbers or hashing and are used to secure the personally identity of the user during payment to avoid identity thief. It is also ensures that validations are been done so as to be sure that the message was from the right sender.
Asymmetric Cryptography.
This is also know as Public key Cryptography and it makes use of a pair of different keys to encrypt and decrypt information which is just the opposite of symmetric cryptography. In this asymmetric cryptography, the public key is used to encrypt the message which can be shared to other parties without risking the security while the private key is used to decrypt the message, so only the receiver can have that. It works in a way that when a user sends an encrypted message, it uses the receiver's public key and the receiver uses their private key to decrypt the message.
Moreso, it is used to verify the authenticity of information using digital signatures. It is applicable to the Bitcoin blockchain where the public keys is make available to everyone and private key is been hidden which ends up been slow due to the high computational intensity. However the cryptography guarantees that funds belongs to the rightful owners. Some of the commonly used asymmetric cryptography are DCA, RSA and PKCS.
How Blockchain Wallets CryptoGraphy works and explain the available types of Crypto Wallets.
A blockchain Wallet Cryptography is a little bit similar to the usual traditional banking system, though a few difference there too. It comprises of a wallet address which is used to send or receive funds/assets from other wallets. Just like in the traditional finance system where a person has an account detail to himself, so is the wallet address attached to a user.
However, it is very important to verify a wallet address before carrying out a transaction so as not to loss funds/assets because the blockchain wallet cryptography does not disclose the identity of the sender's wallet. Unlike in the usual traditional banking system where you can verify address before starting the transaction.
Furthermore, the Blockchain wallet cryptograhy also make use of the public key which is been distributed to the users and private key which is the most important in the transaction process, without the private key, the transaction can not be completed. The private key is used to authorize a transaction.
Features
- It is very secured when carrying out a transaction, once the private key is store properly.
- It allows transaction to be carried across multiple cryptocurrencies and helps in converting currencies easily.
- The transaction fee is very low compared to that of traditional banking.
- it is very easy to use, just like using your normal software or wallet for transactions.
Types of Crypto Wallets
There are two wallets that make use of the private keys, they are:
Hot Wallet: they are online wallets that could be used to execute a transaction quickly, with private key stored online too. This makes the wallet prone to malicious attacks, so it requires a high level to security when using it so as it is easy to access and also avoid the risk losing funds. Example: Coinbase etc.
Cold Wallet: They are offline digital wallets that are not prone to malicious attack. The private key are stored and maintained offline which makes it very secured and hard for any sort of attack. In this wallet, transactions are been signed and verified offline but then disclosed online. Example: Ledger etc.
Some other forms of wallets are as follows:
- Hardware wallets: this is a type of wallet that is used to store the private key of a user and for a transaction to take place with this wallet, it has to be plugged to a computer.
- Software Wallet: This is an application that can be downloaded to a computer or a mobile device and be used online. Further break down to desktop wallet, online wallet and mobile wallet.
- Paper Wallet: This is a process of storing cryptocurrency offline. It has both the private and public key printed on paper which can be accessed by the use of QR codes. This wallet works with software wallet to carry out a transaction.
What is the Merkle Trees and What its importance in Blockchain.
What is the Merkle Trees?
Before the emergence of Merkle Trees, the ordinary Blockchain system requires high computational power, storage space and memory to access information from it's block. Remember a block is estimated to have an average of 500 transaction IDs stored in it which are all hash to a block. However, The Merkel tree solved some of the ambiguities of the blockchain by hashing each of this transaction Unique IDs and making them readily available for use each time they are called up rather than downloading the entire block with an estimated size of 350gigabytes.
Merkel tree is just a data structure that helps to bring in efficiency in the Blockchain. One does not necessarily need to continue in ambiguity in accessing the Blockchain network anymore, all you need to do is input the transaction ID details that you need, and Merkel Tree concept helps you generate the required information with specificity to details entered and Therefore, they save time, you don't need to engage in high computational power to harness the block, you need less Data as well as memory/storage in doing so too.
Merkle Tree adds up all transactions in a block by creating a new digital fingerprint which enables a user carry out a transaction and at the same time check if its been stored in the block. The Merkle tree generates new branches by repeating the hashing pairs of nodes until only one of the hash is remaining and this is called Merkle Root. However, this leaf nodes are regarded as hash of transactional data so any non-leaf node is the hash for its previous hash.
Importance
Just as i have mentioned before, the Merkle tree has shown a high level of efficiency and also have some importance that i will be listing below:
- The Merkle tree ensures adequate security during the process of transaction verification.
- it does not require much memory/storage capacity.
- the Merkle tree does not need to download the entire block, making it faster when verifying transactions.
- it saves time because it doesn't need high computational power to harness the blocks.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
So for this task, i will be explaining the functions of Key, Signature, Transaction and Blockchain with the proper screenshots from Blockchain Demo: Public/Private Keys & Signing
Keys
For the keys section, the Public key and the Private key have a direct link and every time a private key is been inputted that is either manually or when a user clicks on the Random button, a new public key is been generated. So i will go ahead show what happens when the private key is been inputted manually and when the random button is clicked.
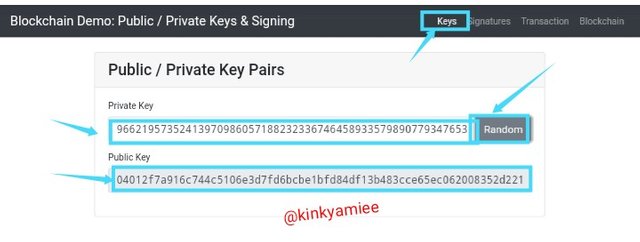
First Click On The Random Button
When i click on the random button the first time, i got Private Key as 96621957352413970986057188232336746458933579890779347653790117999953160513233 and then Public key as 04012f7a916c744c5106e3d7fd6bcbe1bfd84df13b483cce65ec062008352d221334752d8dd363beac6fb455a1c6f09b206a2fa4d0720bea7704a0f7c4210c924a
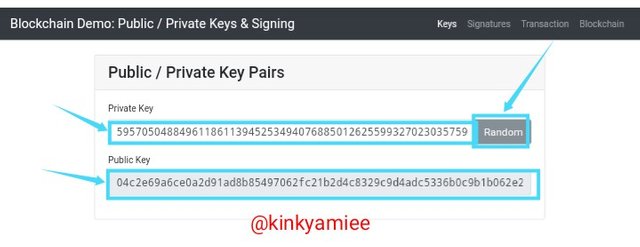
Second Click On The Random Button.
When i clicked on the random button for the second time, i got Private Key as 59570504884961186113945253494076885012625599327023035759219733311705941465016 and Public Key as 04c2e69a6ce0a2d91ad8b85497062fc21b2d4c8329c9d4adc5336b0c9b1b062e27ae0dcd34390e519152f2b7581d848b6324a13f525ed46985d3607993e344b89d
So from the screenshots above, we can see that every time the random button is been click a new Private key and Public Key is generated. This shows a high level of security as the Private key can not be traced from the Public key.
Next, i will manually input the Private key so as to generate the Public key.
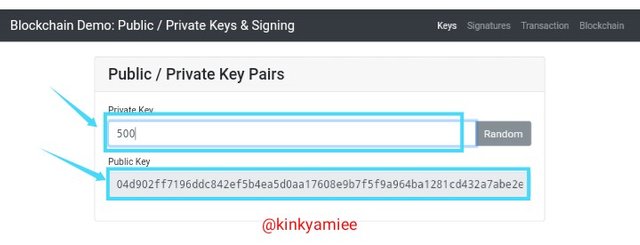
Inputting Manually for the first time.
Private key inputted was 500.
Public key was 04d902ff7196ddc842ef5b4ea5d0aa17608e9b7f5f9a964ba1281cd432a7abe2e9ff49e905efb160049826f5327bfdd80ec0691b77afafd59d65ea4db7f6fa955b
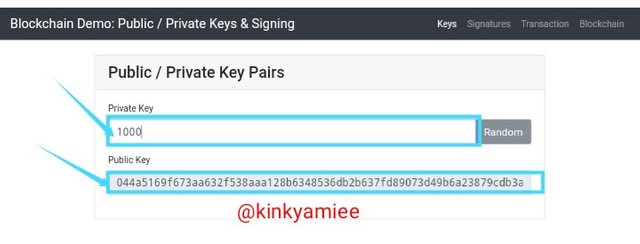
Inputting Manually for the second time
Private key was inputted as 1000
Public key was 044a5169f673aa632f538aaa128b6348536db2b637fd89073d49b6a23879cdb3adbaf1e702eb2a8badae14ba09a26a8ca7cb1127b64b2c39a1c7ba61f4a3c62601
SIGNATURE
For this section, i will be adding a message which i am going to be signing in the box and to sign this message, i will be using the first Private key i inputted manually.
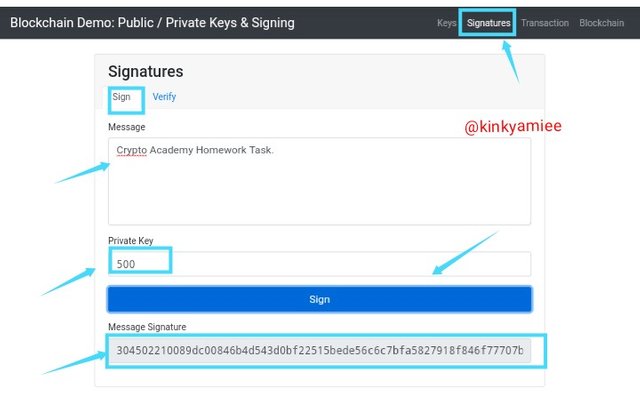
Private key used was 500.
Message to be signed: Crypto Academy Homework Task.
Signature Generated: 304502210089dc00846b4d543d0bf22515bede56c6c7bfa5827918f846f77707b91b00c8a002203e23c7496f4f825575bf18c753f9e1a8cd2343848f2ede5ed3189534d2bc7db4
Next is to Verify the transaction /Message generated, and to do this, i will be using the Verify icon on this page.
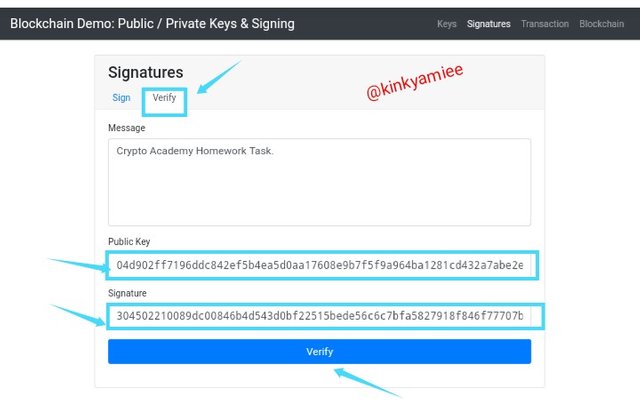
So once i clicked on the Verify button, the message that was signed, Public key and Signature generated, all automatically updated and then i clicked on the verify button below to confirm the message and the message got verified as you can see from the screenshot below.
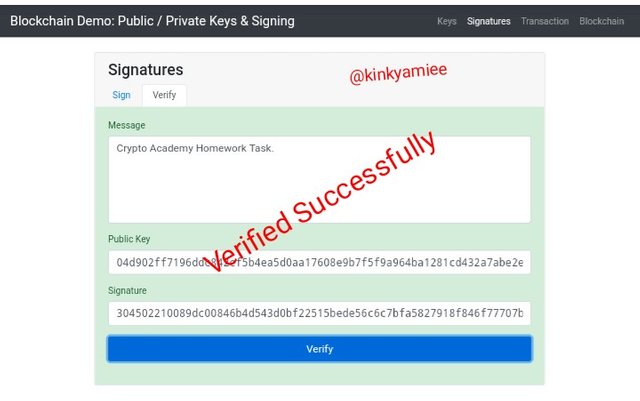
TRANSACTION
In this section, i will be taking the actions i have taken above, that is, Signing and Verifying. Now lets start with the Sign icon.
To Sign a transaction, we first click on the Transaction icon on top of the front page, Next i will be inputting the amount i would like to send which is $500 in the message box, once i do this, my Public key and the receiver's Public key automatically comes up. Next i input my Private key which will be use to execute the transaction, lastly, i clicked on the Sign icon to confirm my transaction.
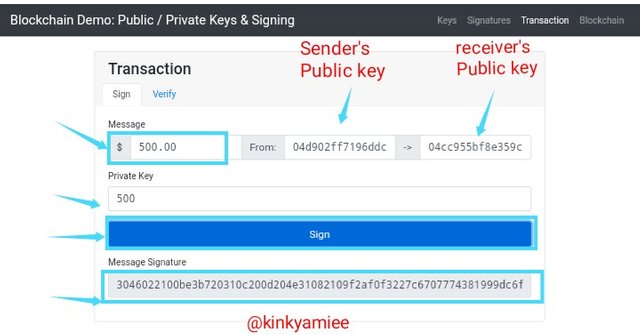
As you can see from the screenshot above, a new message signature was generated and that will be used to verify the transaction.
Next is to Verify the transaction. To do this i clicked on the Verify Icon and this quickly update the message signature and the Public key of the transaction, that would enable the transaction to be completed.
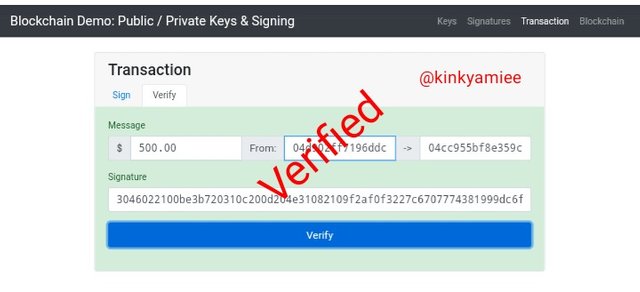
So we can see from the screenshot above that the transaction has been verified and completed.
BLOCKCHAIN
In the section of the blockchain, i will be showing how to carry out a transaction using BLOCK-2 and BLOCK-3. On these Block we can find the Block, Nonce, Coinbase, Previous hash for block 1 and Block-2 hash. The Nonce on Block one is 25205. So i will be using my Public key and message signature to carry out this transaction.
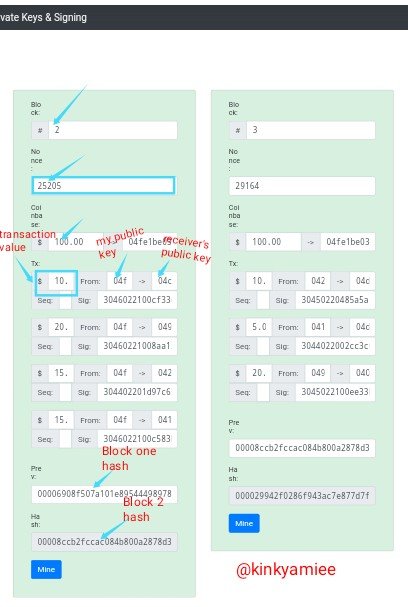
So from the screenshot above, we see that the transaction value is $10 with the public key of the sender and receiver. Now i am going to be changing the transaction value to $20.
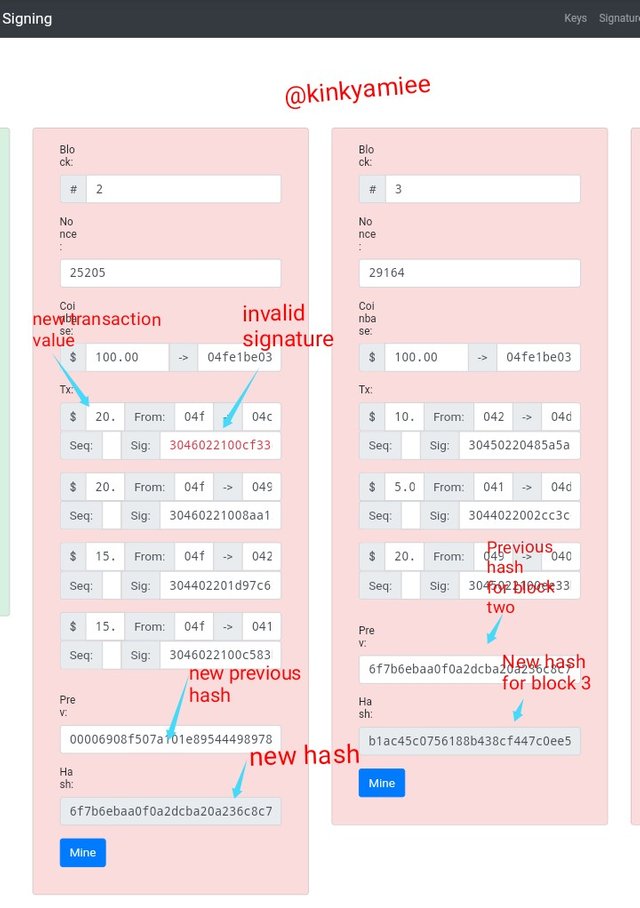
We can see that after inputting $20, the message signature turn out Red meaning that the message was invalid and has to be re-mined, this ended up affected block 3 and the rest of the blocks making them all turn red and this is because the hash of the previous block affected the new block. So i will go ahead to mine the block agin and make sure that the Nonces of the blocks are right.
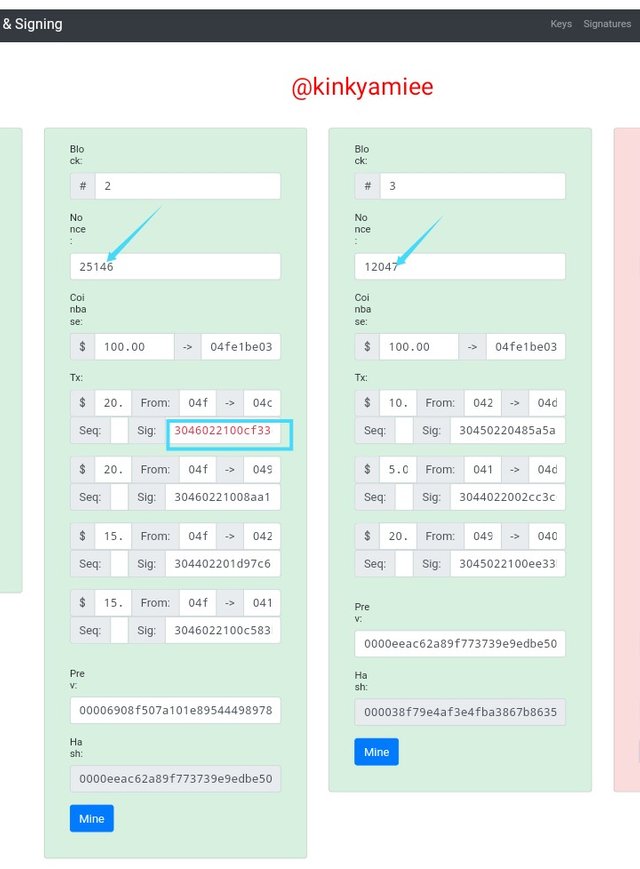
Now, from the screenshot above, we have seen that after clicking on the Mine button, the Nonce changed for both blocks respectively but then the signature of block two remained invalid. So from this, we can see that when a transaction is invalid, it can affect the rest of the blocks.
Conclusion.
Cryptography has shown a great deal of usefulness when it comes to carrying out transactions. It has shown a high level of security, efficiency in storing information and making sure that transactions get to the right user. The cryptographic algorithm make use of a Public/Private key in such a way that the Private key protect and signs a transaction while the Public key ensures that the transaction is verified.
Thank you very much for a well detailed lecture.
.png)
Congratulations! Your post has been selected as a daily Steemit truffle! It is listed on rank 21 of all contributions awarded today. You can find the TOP DAILY TRUFFLE PICKS HERE.
I upvoted your contribution because to my mind your post is at least 9 SBD worth and should receive 30 votes. It's now up to the lovely Steemit community to make this come true.
I am
TrufflePig, an Artificial Intelligence Bot that helps minnows and content curators using Machine Learning. If you are curious how I select content, you can find an explanation here!Have a nice day and sincerely yours,

TrufflePigCongratulations, your post has been upvoted by @scilwa, which is a curating account for @R2cornell's Discord Community. We can also be found on our hive community & peakd as well as on my Discord Server