Crypto Academy / Season 3 / Week 8 - Homework Post for [@stream4u]

GOOD DAY TO MY PROFESSOR AND FELLOW STUDENT YOU ARE WELCOME TO MY HOMEWORK.
Am so happy to be part of my professor @stream4u assignment once again, to participate on his asseement base on his topic on Cryptograph, i really understood a lot of things behind the Cryptograph,
Thanks alot for this Wonderful opportumity and lesson.
I hope u will enjoy my assement.

QUESTION ONE
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?

Before i explain what Blockchain CryptoGraphy is all about i have to give an instance and what really and how the crytograph operate in the world of cryptocurrency.
For an instance taking the radio frequency as an example, is known to every one the radio frequency from the radio station is actually made for all listeners and is not a radio to an individual communication, the broadcast is open on air where by any one that have ear can hear it out while broadcasting its his gadget where by the radio staion serves as the sender while the lister is the receiver.
In the other way round using a Military battle field as an example where sodiers are at battle having there men camped in different location, is known for any communication to take place within the sodiers or the locational communication that the message is highly encrypted in such that the opposition cannot detect, know or figure out the message behind the frequency what there plan is, the same
is applicable to the world of crytograph blockchain.
Technically the crytograph serves as a means of communication between two or more participants, the sender known to be the host encrypt a secured key and algorithm for a message highly configured before sending it to the receiver which can only interpreat the message by decryting it through the help of the receiver key, and the receiver can be the audience. therefor the main important aspect of cryptograph is the encryption key.
What is the function of the encryption key?, the function of this particular key is to secure the transmission of data, value and information that is passed throughthrough without droping along the transmission until it gets to the receiver point where is main to be delivered.
Majority of the blockchain we see today do not use secret encryted message especially on the public blockchain, mean while the new blockchain known to be new generation now utilize different variant encrytion methods in sending messages in other to keep the message secured, mean while many tools are now in place of which the most known ones out of all is known as the the hash and the signature.
However the main focus of the blockchain crytograph is about the encryption and decryption, cipher and keys.
The Digital Signature
The is a mathematical approach in coding, configuring creation and generation of digital codes which are used in verifying messages. Attachment of the digital signature electronically serves as authentification and specification of the content of a message and verification form the sender.
How ever the digital signature serves and is preferable in addressing messages.
Cryptograph Hashing
Base on this we have the symmetric, the Symmetric encryption-key deal with similar keys for encrytion for encryption of information, this is done in HTTP website. the Symmetric key encrytion refer as secret key cryptograph.
Asymmetric-Key Encryption
The second part of the encrytion have a role on crytograph in the blockchain, the encryption keys known to be the public-key cryptograph, and this particular one involves the use of the different key for for the encryption and dencrytion process.
The public and the private key can plays the role for encryption key and as well the decryption respectively.
The asymetric cryptograph is known as the public key which can be shared openly while that of the private key is secured within an individual interest making it private and secured.
The application of th cryptograph in blockchain really focus on the transaction aspect and ownership verification.
History Of Cryptograph
"Cryptograph" is derived from a greek word Kryptos meaning heading. this was actually dated to happened far back in 2000 BC with an Egyptian practising hieroglyphics.
The hieroglyphics consist of complex pictograms.
The modern cipher is the first used by
Julius Caesar in 100 B.C. to 44 B.C.), who do not actually have trust in his messager when ever he is having conversation with the officers and the Governor, for this reason he now have to strategies himself to develop a system to replace each character in his messages with a three character positions ahead of it in the Roman alphabet.

QUESTION TWO
Explain the Public Key CryptoGraphy.

As a regards to to crytogragh as partaining to the question is that the public key is a long numerical values and aphabet combined together to encrypt data, mean while they are generated by a software which is known to be secured and as well trusted.
Public key Crytograph this made for the management of identity and security through the Public key infrastructure (PKI). The PKI is known to be a public key for crytograph
And the public key Cryptograph make use of the crytograph to protect the interest of the identities and datas from unknown source.
The public key is uses to encrypt a message also or information and as well to verify the legitimacy of the source of the message which is accompanied by the private key. the work of the private key here is used to decrypt the public key as well to create signature.
The public key is said to secure the data while private key unlock it. And
meanwhile they are created through Assymettic algorithm which are use to generate the below algorithm, example the, elliptic curve cryptography, Rivest-Shamir-Adleman and Digital Signature
The public key is only made for those who are intersted over open conversation or communication while the private is strictly made an individual for personal usages and public saved in the public infrastructure saver.
Asymetric Cryptogragh means of sending and receiving data are as follows.
Key Generation: The public and the private key are generated individually.
Key Exchange: The sender and the receiver exchange public key.
Encryption: There is encrytion exchange of the public and the private key between the sender and he receiver.
Sending Encrypted Data: The encryped data or info is sent to the receiver known as the receipent.
Decryption: The receiver receives the massage and decrypt it with his private key.
They public key technically can applied through encryption and digital signature.
Based on historical story, we are told that the generation of the public key of crytograph came up on the year 1976 by Whitfield Diffie, Martin Hellman and Ralph Merkle, they introduce the public key and as well describe the first function and its crytograph protocol, since the introduction of this till date the use of the public key have found it function in different sectors like e-business, finance and e-commerce in other secure data and vital information by using mathematics keys.

Quesion Three
Explain the Private Key CryptoGraphy.

A cryotograph is actually a practice and tchniques to secure data and communication across it boundary.
The private key is just a numbers and it corresponding alphabetical characters but in the current degital encryption, the keys are now difficult algorithms that even the morden computer cannot crack or decrypt it in other to source out informations.
Some time the private keys is symmetric encryption in the sense that it can encrypt and as well decrypt.
Also a private key can be a secret key which is variable in cryptograph which is used in an algorithm in encrypting and in decrypting datas. the private is only made for the owner and the authorized one who decrypt the information being passed through from the generator, and is known that the private key plays a role in symmetric, Assymetric and in crytocurrencies.
Private key is known also to be symmetric encryption can work base on encryption and decryption, base on this now the private key can work on the following:
•Generating a new pruvate key
••Securing and storing of private key
•Key exchange
•Key management
•And can be used in asymmetric cryptograph
•Generating a public-private key pair
Uses Of Private Keys
• They are used un creating digital signature which are used to authenticate values transfer and as well to symmetric encryption and to protect the data exchanges.

QUESTION FOUR
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?

Digital signature is mathematics method used in verifying and authericating a message technically which appears in software or by digital documents, The digital signature was formulated to elliminate the problem behind tampering impersonation in communication.
The digital signature prove evidence of identity, origin and transactions. the signer use it the absence of conscent to give go ahead in his absent.
How Digital Signature Works
The digital signature rely on the public key Cryptograph which in the other way round is assymetric cryptograph.
With the public key algorithm like RSA (Rivest-Shamir-Adleman), in this the main key generated are the public and private keys.
Digital Signature in crytograph works in mutually in authenticating crytograph keys. the private key is made to encrypt the data while the public is for decryption.
The Basic Benefits Of Digital Signature
Security is one of the most imortant aspect of digital signature, security depends highly on digital signature in other to ensure that the coded information is not tampered.
The method utilized in digital signature are the following:
•Personal identification numbers
•Checksum
•Certificate authority (CA) validation.
•Trust service provider (TSP) validation
Other are:
•Timestamping
•Time savings.
•Cost savings.
•Traceability
Positive environmental impact.
How Digital Signature Work.
With a digital signature the private key is encrypted where by the hash for that data is created which can be decrypted along side with the correspondent.
Uses Of Digital Signature
•The use of digital signature is to improve streamline process of document integrity.
•• Medically the digital signature are use to improve the effeciency of e-prescribing, strengthing data security and admistrative process.
what is Signing Of Transaction/Message?
Signing of transaction is known to be new security method imported to verify transactions and as well credentials by formulating a unique code for the transaction based on digital signature.
Signing transaction create one time code for a a particular trasaction, mean while it increases the security setting against malicious attack.

QUESTION FIVE
Explain what is Symmetric and Asymmetric cryptography?

The initiator of the asymetric Cryptograph is by name
Whitfield Diffie and Martin Hellman, researchers at Stanford University,was the first set of people who publically establish asymmetric encryption in 1977 paper, this was in exiting proposal until when James Ellis several years ago when he was working with
Government Communications Headquarters (GCHQ), when the brittish intellegence
The story narrated that Diffie-Hellman outline paper wasa actuallly used to raise power for the decryption in 1974 with his collegues in order to solve the problem.
The algorithm was based on th Diffie which was named in place of the investors Ronald Rivest, Adi Shamir and Leonard Adleman. They invented the RSA algorithm in 1977 of which thhe communicaation.
As of today RSA, the standard assymetric encryption algorithm are utilizeing on SSL, TLS SSH Digital signs and digital.
Asymmetric cryptography is a public key Cryptograph which use pair of mutual keys of which one is private and the other public to encrypt and decrypt a message or data and to protect it from unauthorized access.
Is used to authenticate data with the help of digital signature, also they are used in validation.
while
Symmetric this is a process of using one secret key in order to encypt and decrypt with the help of special security key, using symmetric encryption algorithm, the information conveyed cannot be undersyood by any one that do not have the key in other to decrypt it.
Since symmetric encryption feature well than assymetric, encrytion is used for bulk encrytion, encryption of large data volume and as well in hashing.

QUESTION SIX
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets

.jpeg)
Link
Blockchain wallets is cryptocurrency wallet which gives full ownership in terms of management of different kinds of currrencies in the wallet.
For an example steem, Bitcoin, Ehereum and many more.
The blockchain give the opportunity the exchange and to have full ownership of the currency and the transaction are well secure with the full backup from crytograph in terms of authentification.
Blockchain wallet is the act of sending and receing different kind of cryptocurrency through some many gateway
Example of blockchain wallet
Jaxx, Electrum, Blockchain, Mycelium, Samurai, Electrum, Bitcoin paper
HOW BLOCKCHAIN WALLET WORKS
On a blockchain wallet the private and the public key are necessary in place to access the wallet, mean while the key serves as a hook to hook in current from a different account and to push out currency to another account.
Features Of The Blockchain
•Easy to use.
•Highly secure
•Low transaction fees
Types Wallet
•Hot wallet: This are known to be online wallets where by crytocurrencies can be transfered and saved. Example of this is the Blockchain.info coinbase.
•Cold Wallet: This are known as tthe offline wallet where by currencies can be tranfered and got saved, the are not internet incline or internet base and they are highy secured. example of the cold wallet is the Ledger Trezor.
Type Of Block Chain Wallet
•Software Wallets;
•Mobile Wallets
•Hardware Wallet
•Software Wallets
•This a wallet that is installed in the mobile device which can be in a mobile phone, web base wallet even in the destop which are internet connected and can be accesses online examples are jaxx, breadwallet and copay.
•Mobile Wallets
•Mobile wallet is almost the same with the online wallet but they are built for mobile phone use and they are friendly in their interfaces.
•Hardware Wallet
This is type of wallet which is located in a USB which as well store the the user's key in a hardware, Here is slow in security and is prone to be attacked by virus and others.

QUESTION SEVEN
What is the Merkle trees and What its importance in blockchain?

Markle tree is a means of arrangement a large information, data in a sequential manner and as well verifying them accurately which is effient and quick in response to result or output, mean while markle tree is a component of the blockchain.
History
Markle Tree was brought to existence in the year 1070 by Ralph Merkle at standard university where he unknown create a blockchain, here he was able to achieve a new method creating proofs, mean while markle tree is main to verify datas which enhance the computer to work fast as possible.
Today the markle tree are used in the blockchain in verifying datas also it have gone wide in the encrypting computer protocols when it comes to cryptocurrency.
The Markle root is responsible in the grouping and merging and paring of the value in a arranging order, in order to form a single code to achieve a single root known as the markle root.
The harsh generated are arrange to in pairs to fomulate the root known as the Markle root, the root can be in this formate.
Hash A
Hash B
Hash C
Hash D
When they are paired.
Hash AB
and
Hash CD
The two hash are hased to give MARKLE TREE.
Important Of Markle Tree
Merkle Trees have four sizable benefits:
•They provides integrity and as well validate the datas.
•They reduce and as well compress the size of the file
• It have Simplified Payment Verification (SPV) use to verify trasaction made in the block without downloading the whole block.

QUESTION EIGHT
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)

THEORITICAL PART
THE PUBLIC KEY:
The public Key: is a key which give you access to receive token transaction. And is a code wich is paired with to the private key. mean while as the public key is used to send, the other way round the private key is used to unlock it.
The Private Key: The private key assure you full control and ownership, mean while the the private key can be in 256 character binary code or 64 digit hexadecimal code, QR code.
In other to complete a transaction in the blockchain, is necessary to authenticate it in form of SIGNING the TRANSACTION, Below is the step to send trandaction are follows.
The transaction inputed is being encrypted by the public key while the transaction can only be decryted by the private key.
After that the transaction is said to be signed by the private key to show approval, meanwhile the digital signature is being generated by the combination of the private Key along sidewith the data of the transaction.
Lastly the the transaction can be autheticated with using the public key
The Node verify the transaction and authericate it, if the transaction is invalid is be rejected while the valide is being accepted.
Practical Part
Key
With the private key the public are generate depending on your input as you can seen the two screeshot bellow.
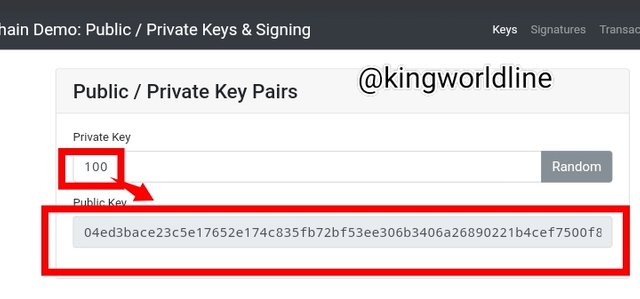
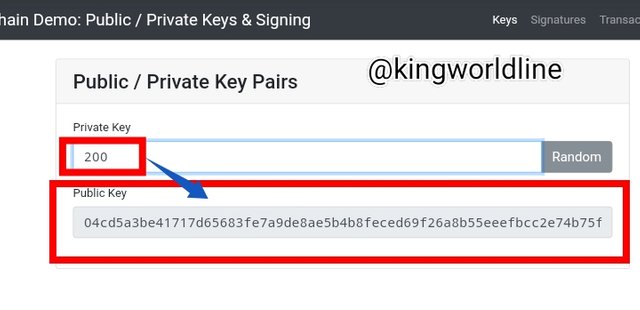
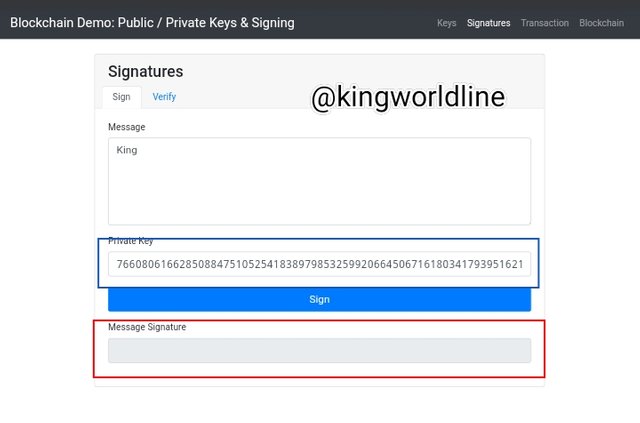
Signature:
As of the input ''King'' in the message box and i verified it with a unique Private key, then verifying it that way will be valid by showing green background while any detachment from the mesage box will render it invalid. as shown in the screenshot below.
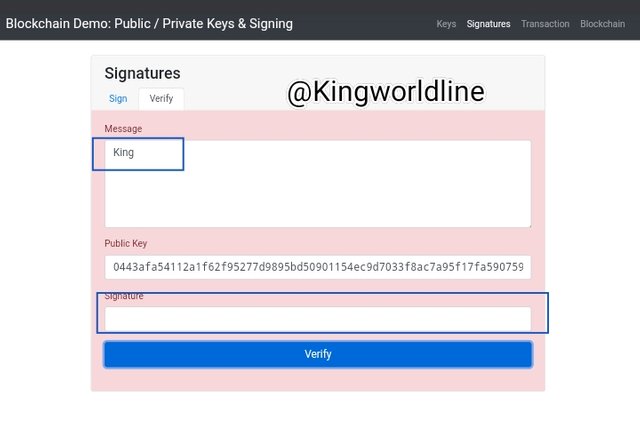
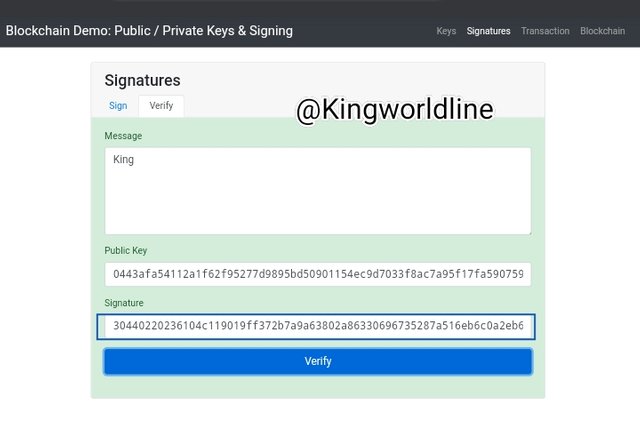
Transaction:
In transaction, signing, with the unique private key generates it's message signature for that particular transaction with the specified amount, getting it varified will show a green background showing the transaction is valid while any contrary adjustments in the input render it invalid as shown in the screen shot below.
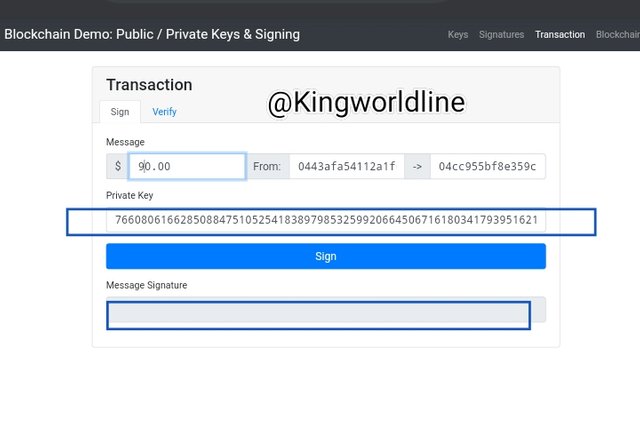
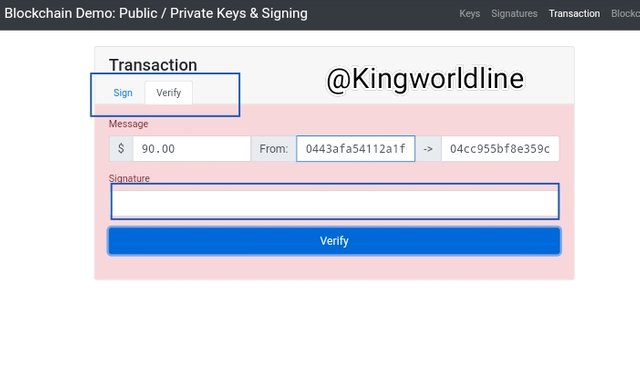
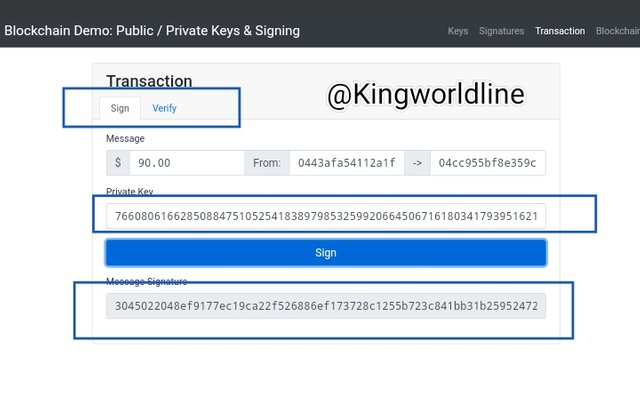
Blockchain :
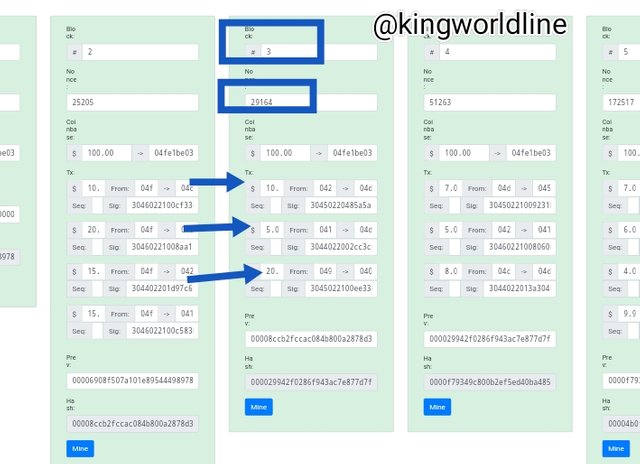
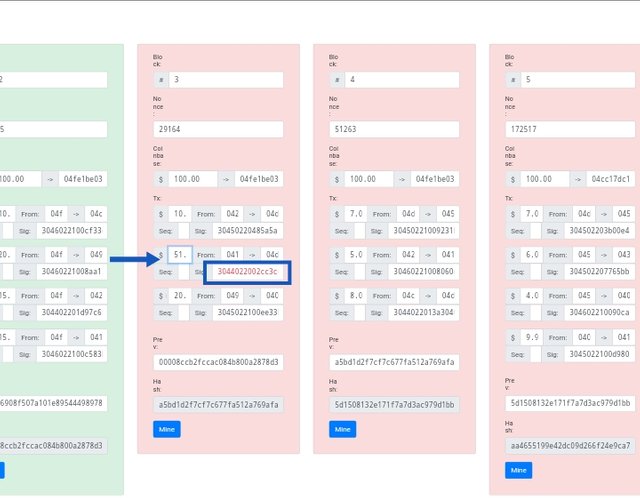
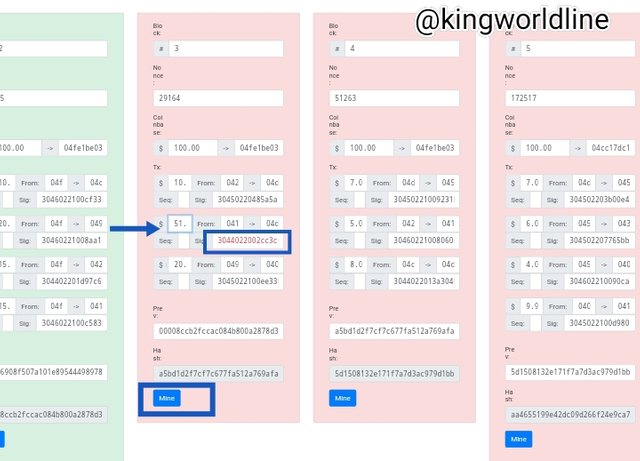
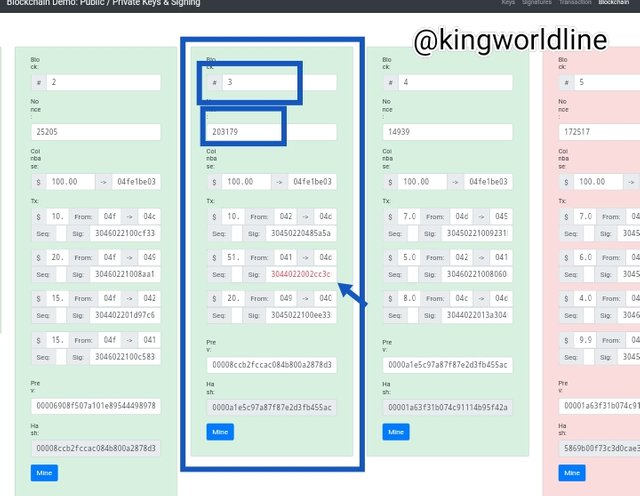
Is known that once an infomation of data are registered in a blockchain that it can't be changed rather it will altered process and rendering invalid. base on the screen shot i made my nonce is 29164 on block 3, as verified transactiom of 100.00, 10, 5.0, and 20, if there is any alteration in the value in the block will render it to be invalid as which also will affect the other block due to they are linked together.
Now i click on mine to validate the block but it doesn't really validate because of the signature of the block three (2) is tampered will remain incorrect which means that the transaction was carried out without it conscent of the previous which means is out of the knowledge of the 2nd.
As shown in the screenshot below

QUESTION NINE
Conclusion

The public Key: is a key which give you access to receive token transaction. And is a code wich is paired with to the private key. mean while as the public key is used to send, the other way round the private key is used to unlock it.
The Private Key: The private key assure you full control and ownership, mean while the the private key can be in 256 character binary code or 64 digit hexadecimal code, QR code.
In other to complete a transaction in the blockchain, is necessary to authenticate it in form of SIGNING the TRANSACTION, Below is the step to send trandaction are follows.
The transaction inputed is being encrypted by the public key while the transaction can only be decryted by the private key.
After that the transaction is said to be signed by the private key to show approval, meanwhile the digital signature is being generated by the combination of the private Key along sidewith the data of the transaction.
Lastly the the transaction can be autheticated with using the public key
The Node verify the transaction and authericate it, if the transaction is invalid is be rejected while the valide is being accepted.

My Regards To
Professor @Stream4u
THANKS
AM @kingworldline
.png)
.jpeg)
.png)
.png)