STEEM-CEYPTOACADEMY/ SEASON3/WEEK2/ HOME-WORK POST FOR PELON53 HASH AND CRYPTOGRAPHY
Hello professor @pelon53, it's really nice reading through your fantastic lecture at this particular time you really explain well and I really appreciate. Let's go straight to the home-work.
Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Nice question from my own understanding I will say resistance to collision constitutes or is part of cryptographic hash functions that is structured to been a collision resistant. this different hash functions been tagged has been regarded to be collision resistance later it was disintegrated.
Let me pick out MD5 and SHA-1, this two or the both has great technique that is very reliable and at the same time efficient, it reduces the action of making use of man power while trying to find a collision. Sometimes hash functions makes us to understand that to find a collision is totally difficult, the functions of those hashes are called probably secure.
Collision in resistance can't necessarily be differenciated from a second preimage resistance, of course I will get to that in due time, but moving forward it is simply because the collision resistance can be referred to as weak collision resistance remember before we call a hash function or refer it to a collision resistance, it must require a minimum of 160bit length.
Hash functions has so many resistance preimage resistance, second preimage resistance, and finally collision resistance, all constituents to as properties of hash functions. If you watch closely well you will understand that they are all similar.
what does resistance to preimage mean??
Fantastic question once again resistance to preimage constitutes of hash functions, this hash functions is very difficult to turn. Now let's get this clear of a hash is functioning within an axis of a given circle its expectations is vital and it's computional this quickens that location that tends to imput the various laps of such circle or element.
Let's not forget in the year 1976, Diffic and his compatriot Hellman invented the total use of a one-way side functions is computional shall, and it functions in any given direction, it can reverse too. It's lines is in linear functions, thus it became very eazy to be protected by a line.
It takes alot for a hash function to be preimaged it must have a minimum requirement of 80 bits, this particular resistance is totally different from the other hashes pit together. Check out before a particular hash function can be plunged to been in a one-way, firstly it must be preimaged reisitance.
Preimage resistance has a specified output, it is in a computional manner and it is infeasible to be detected, it has imput charges example Y it is hard for you to detect X, prior to that H(k)=Y this is mathematical.
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking
In the quest of verifying the hash of the last block and the hash of the transaction I quick made a visit to https/etherscan.io
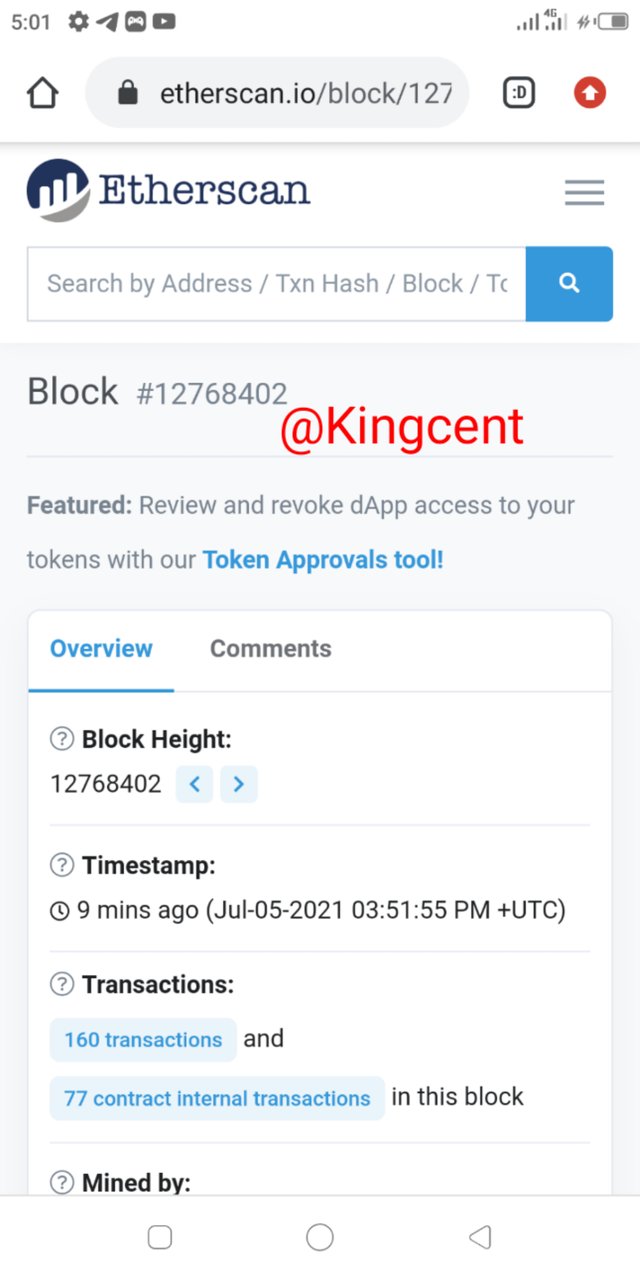
- After gaining access to the site I took a nap and screwed down to access the latest blocks. #12768402
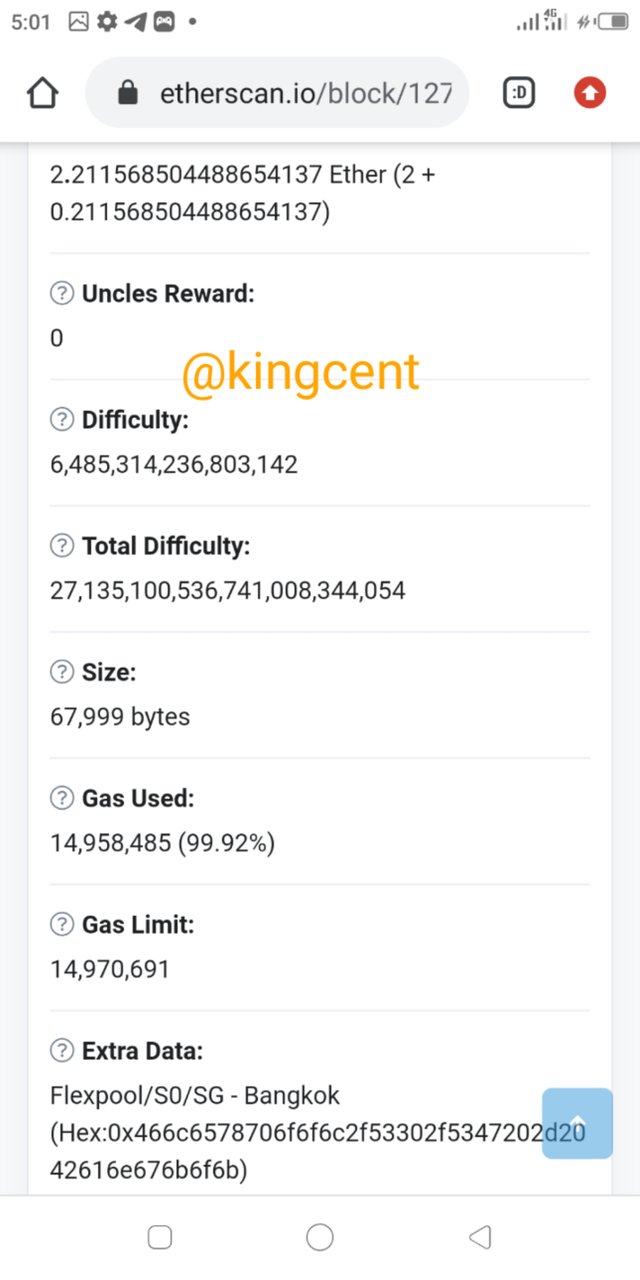
- I was able to explore the both the blocks and the hash too at the same time. Including the latest transactions too.
I further opened the transac to see more details,
Opening and getting and over view of it I was able to determine the block heigh, time stamp, and some key transactions.
- You will also get some key details, for example knowing when the block has been hacked, and knowing the timing too as well.
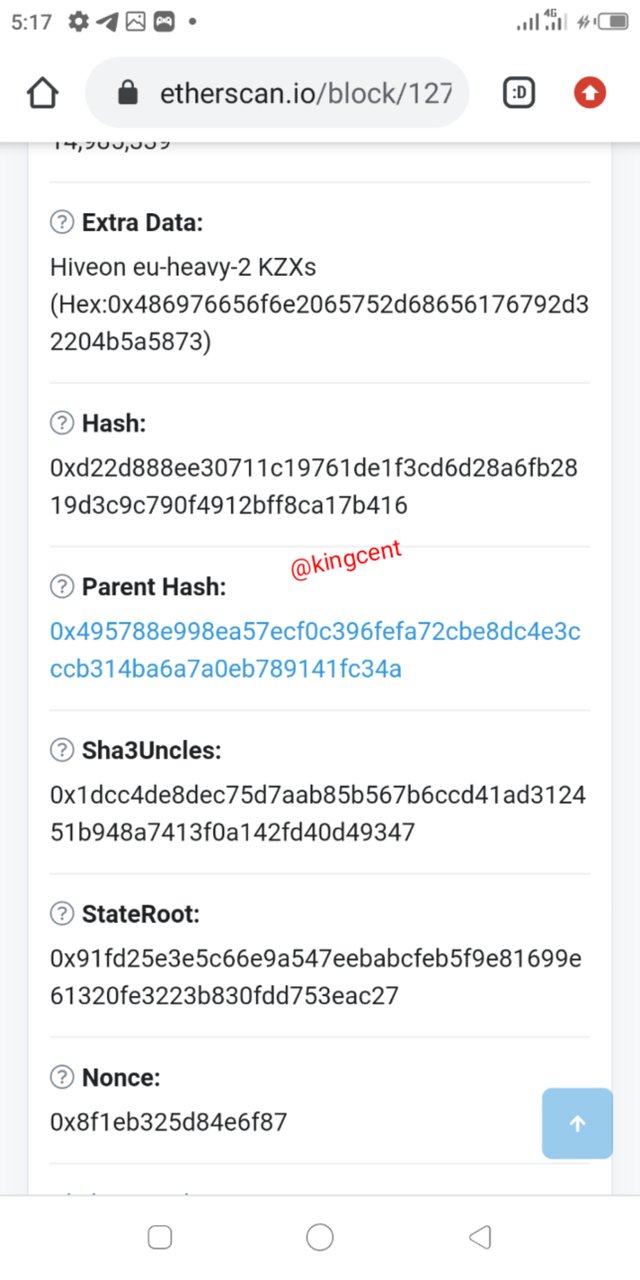
- The hash prior to the block is 0x495788e998ea57ecf0c396fefa72cbe8dc4e3cccb314ba6a7a0eb789141fc34a
- You can view the block using the block ID or the parent hash itself.
#0x495788e998ea57ecf0c396fefa72cbe8dc4e3cccb314ba6a7a0eb789141fc34a
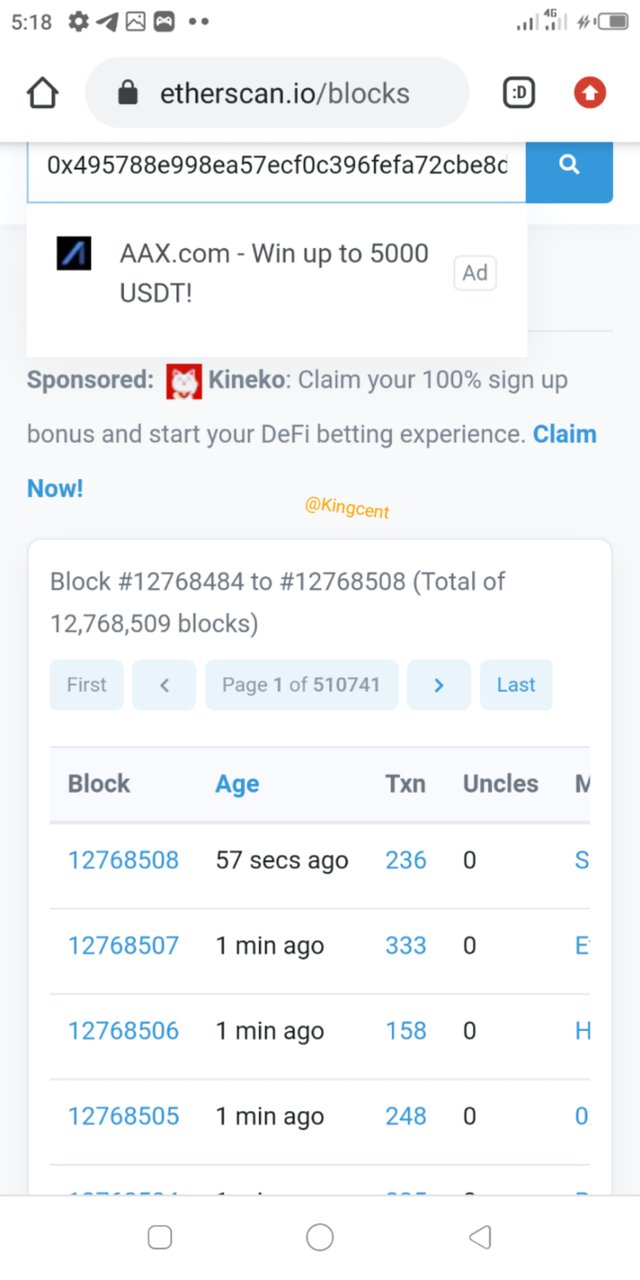
To view the transaction again you can input the parent Hash at the search axis at the etherscan please view it.
using tronscan to verify hash
Verifying hash through tronscan is very simple in this case I will be using my Tron link pro.
Open your Tron link pro click on tronscan and another phase will pop and and it will load slowgishly for some minutes.

- In the end another phase will surely pop up and you can proceed to exploring it to get further information's about the rescent block and it's parent hashes.
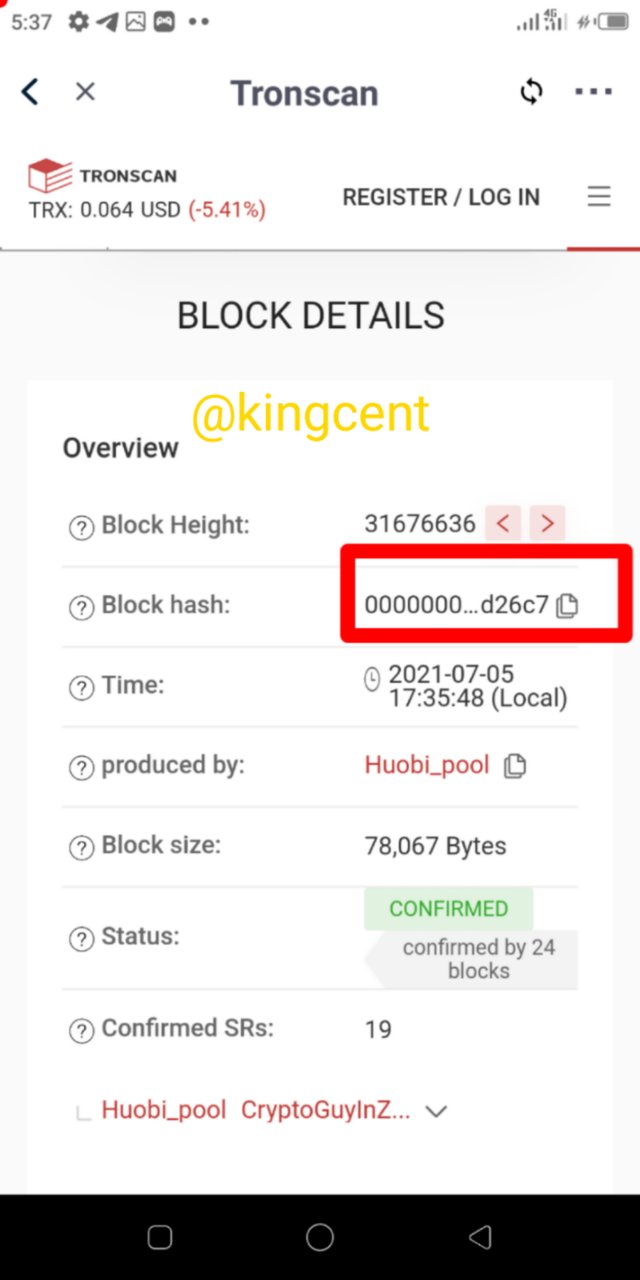
The next phase that will pop it will expose so many things the block details and all the rest.
And most expecially the block hash, it is very important because you can easily copy it and paste it at the search axis in the tronscan to view the blocks and the hashes too as well.
Block hash0000000001e358dc2f76317653e937c42d216c013b7150d488faac0ecead26c7
Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain
- Generating Cryptoacademy through SHA-256 you will understand that the first one has an upper case please view some snap-shots below.
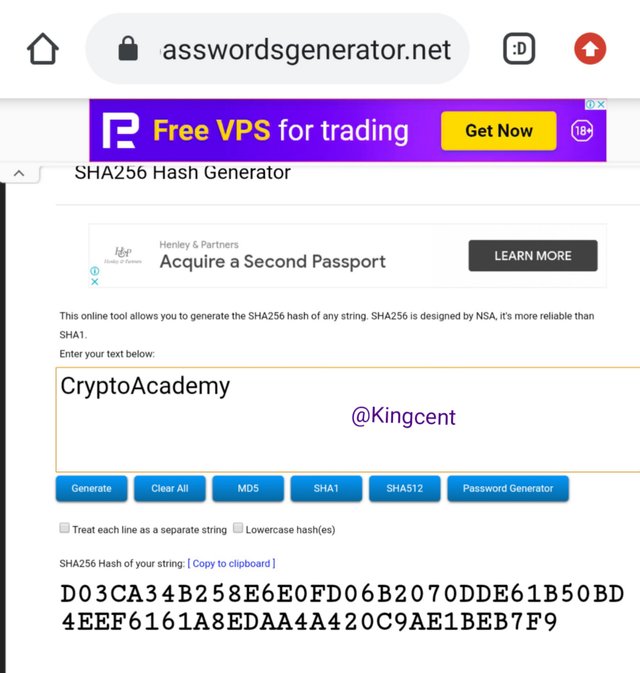
From the image I uploaded above you will see that there are different numbers and alphabets mixed up together and this phase I used cryptoacademy that has the upper case, the next one I will use the one that has lower case so that you can see the difference very clearly.
- Generating using the lower case please view and hopefully you will see the clear difference
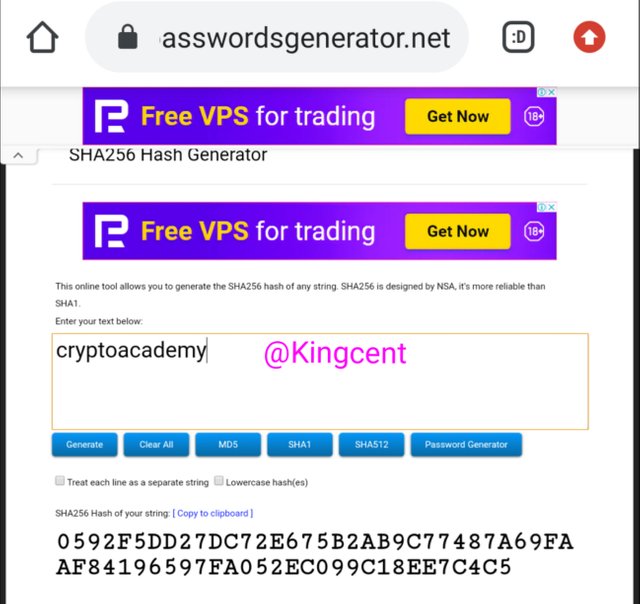
- Here at this axis you you can see the clear different here I used the lower case, at this particular one you will surely understand that the mixture of alphabets, and numbers are totally different.
In your own words explain the difference between hash and cryptography.
Hash
When we talk about hash we are talking about some form of conversion here, hash converts an input of a length be it arbitrary or not to an encrypted message, it occurs as a result of a fixed length. The size of the file involved is unique and the size of the hash remains the same.
Hashes can be reversible, remember hash functions in a straight line hashing is very important to crypto blockchain. However hashes can't be used to "turn over -engineer" the input from the hashed output, is key since hash functions in a direct straight way.
Cryptography
Cryptography can be defined as the process of keeping an information or data in a safe and secured place so that it can be read and processed when time due. Cryptography doesn't only protect data but in real sense it can be used for authentication purpose.
Cryptography was previously similar with encryption but courtesy this our 21st century things have officially changed it is now seen as a mathematical theory and indeed a computer based practice, this is truly a computer age we are in.
Difference between hash and cryptography
| Hash | cryptography |
|---|---|
| hash are encrypted they are much needed in blockchain technology | cryptography is very confidential basic informations are very difficult to understand |
| Hash length are static, that's why it's very difficult to detect the length | cryptography integrity is superb thereby making information to be difficult to be altered |
| Same hash value is equivalent to the same data value there is no divination | cryptography is basically been valued because there is a sharing of keys between both the sender and the receiver |
| Hash plays a vital role on blockchain, I call it the strength of blockchain | cryptography has key strength too as it mandated a sender of an information not to deny access to the information sent |
| Hash converts input of large arbitrary to an encrypted message at a fixed length and the size remains constant | cryptography keeps and process information or data in a safe and secure axis |
conclusion
From the my homework I was able to figure out strategic points about the various questions that was asked.
Hash is very important to block-chain technology, for me I think a blockchain can't function without hash, it is built at a computerized system and it's elements are super vital.
Let's not forget that in 1976, Diffic and Hellman invented the total use of a one-way side functions on cryptography.
Preimage resistance has a specified output, it's in a computerized manner this our generation everything is super computed, it is infeasible to be detected.
Cryptography was previously similar to encryption, but currently now as we speak it is basically seen as a mathematical theory and indeed a computer based practice
In cryptography if you send a message you can't deny access to the information you sent, the information you have sent is been represented in a greather axis.
parent hash in etherscan or in tronscan is very important just as you can see from my post it was showcased there, you can see the various hashes and blocks, through the parent hash or the hash blocks, all you need to do is to copy the address and paste it in the search section of the scan.
Let me use this means to thank you once again professor @Pelon53, you presented a simple and understandable lecture here once again many thanks to you
Cc:@pelon53