CRYPTOACADEMY SEASON3 WEEK2 ASSIGNMENT POST FOR @pelon53 BY @jimah1k

THIS IMAGE WAS DESIGNED BY ME
Hello guys
It’s another week of this season’s crypto academy, this weeks lecture was all about Hash and cryptography. I must our professor @pelon53 did a very good job in explaining the above terms. After reading the lecture notes and doing my own research I will now answer the home work take given.
QUESTION 1
EXPLAIN WHAT DOES THE RESISTANCE TO COLLISION MEAN? AND WHAT DOES RESISTANCE TO PREIMAGE MEAN?
Before I answer the question above I want to explain what a HASH is so that any time I mention it in my assignment we will all have known what it is.
Hash has been into existence since 1961, hash is a cryptographic function that receives data from the users and converts the data received into codes and the output of this codes are alphanumeric characters of fixed length. Which are very likely impossible to Memorize. According to the lectures notes given hash functions can summarize a huge data into a hash. Let’s look at this example
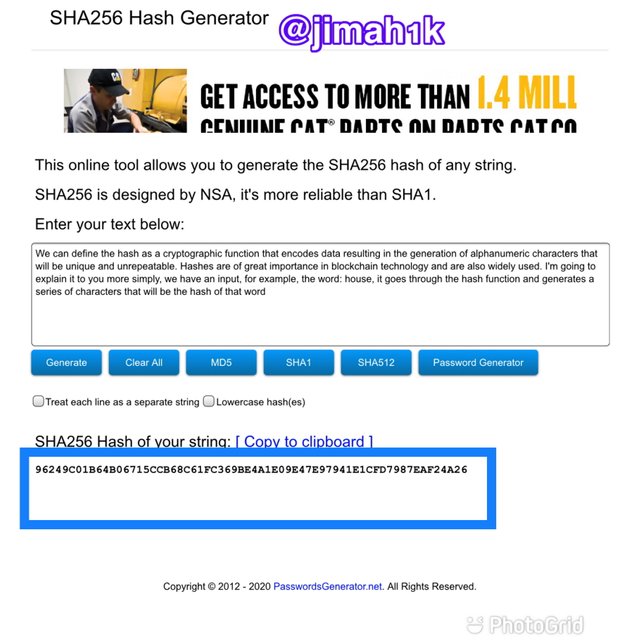
I typed plenty information in the SHA-256 hash generator and this hash was generated
96249C01B64B06715CCB68C61FC369BE4A1E09E47E97941E1CFD7987EAF24A26 Which is a summarized version of the data I have typed in
Let as look at certain advantages of a hash function.
Firstly, I made mention that hash functions can summarize plenty data into a single hash for example let’s say the user inputs ‘Steemit cryptoacademy is the best community in the world and deserves the attention of everyone one in steemit’ this entire data can be summarize in a unique alphanumeric hash
5E248940F3545EF253E3E51D0BE0E11FA2821A2697F6379D232EE15F8CC8F048
Secondly, hash functions are very secured the data that has been encoded are very safe since breaking the encryption is very much impossible to do. It would take years for a super computer to decrypt the hash function.
Thirdly, Hash can not be reversed into the data that it was created from let’s say this statement Steemit cryptoacademy is the best community in the world and deserves the attention of everyone one in steemit once it is converted into a hash, you can not convert the hash back into the original data.
Also, Hash functions are used in blockchain for different functions one of them is the unique address of every wallet. Let’s take steemit for instance we all have our unique private keys in which we use to login now this private keys have been created using hash functions, everyone has his unique wallet address he or she uses to receive his assets all these address are from hash functions.
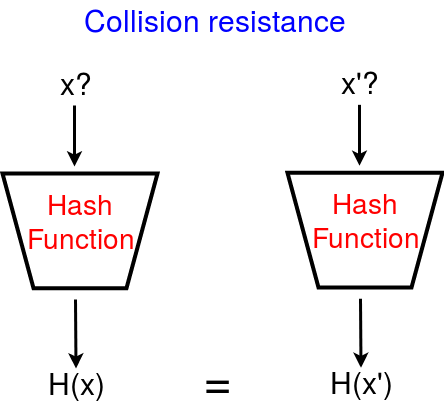
We all know resistance means not to agree with whiles collision means two or more objects let’s say a and b meet or clash. So now Resistance to collision is a property of a hash function, which sole function is to make sure that different data inputs do not output the same hash. Let’s look at this scenario let’s say an input A with data ‘this is my house’ and B with data ‘I am a boy’ now This two Data should not have the same hash since they are of different information. SHA-256 is a hash function that has 64 alphanumeric hash is currently one of the best when it comes to zero resistance collision.
H is collision resistant, if it is hard to find find x and x’ (x’ ≠ x) such that H(x) = H(x’)
source
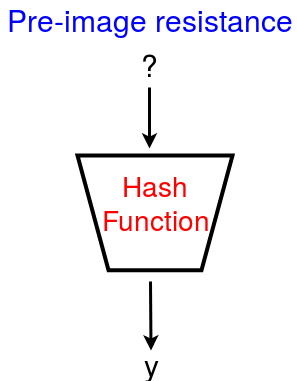
In my explanation of hash I made mention that it’s very hard or impossible to convert a hash to the data it was created from it is the Resistance Preimage(one way)that makes this possible. It is feature of a hash function that makes very impossible for anyone to have a hash and be able to trace or convert it to raw data because it moves in one way. This feature helps protect the data and information of people. SHA-256 is an example of a hash function that can not be converted from hash to raw data
Let H be the hash function, with domain D and co domain C.
H is said to be pre-image resistant, if for any y from C, it’s hard to find x in D, such that H(x) = y
source

QUESTION 2
USE TRONSCAN AND ETHERSCAN TO VERIFY THE HASH OF THE LAST BLOCK AND THE HASH OF THAT TRANSACTION. SCREENSHOT IS REQUIRED FOR CHECKING.
Let’s start with ETHERSCAN below are the steps to follow in verifying the hash of the last block and the hash of that transaction.
first of all you can navigate to the etherscan website using this LINK
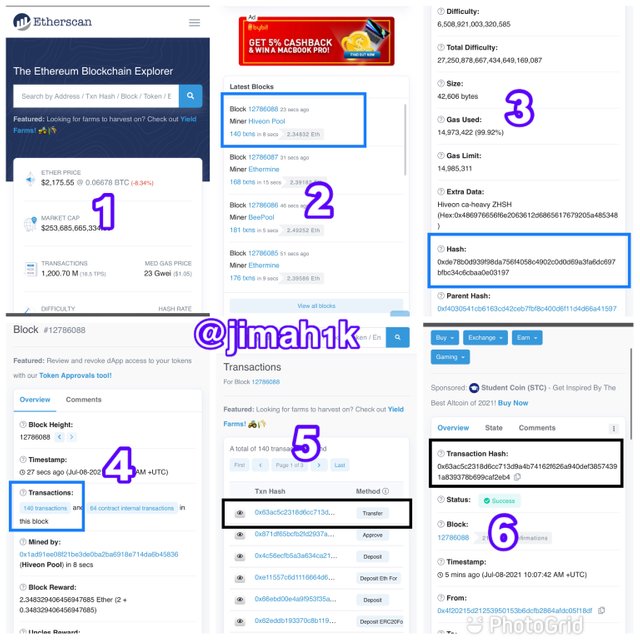
click on the last block to view its details.
After clicking on it several details will be showed since we are interested in the hash of that block scroll down and locate the hash.
For the hash of this block we have
0xde78b0d939f98da756f4058c4902c0d0d69a3fa6dc697bfbc34c6cbaa0e03197
Now if you want to check the transaction hash of that block on that same page scroll up and click on transactions
click on the first transaction
after you have click one the first transaction, the transaction hash will be shown
0x63ac5c2318d6cc713d9a4b74162f626a940def38574391a839378b699caf2eb4
BELOW ARE SCREENSHOTS TO GUIDE YOU
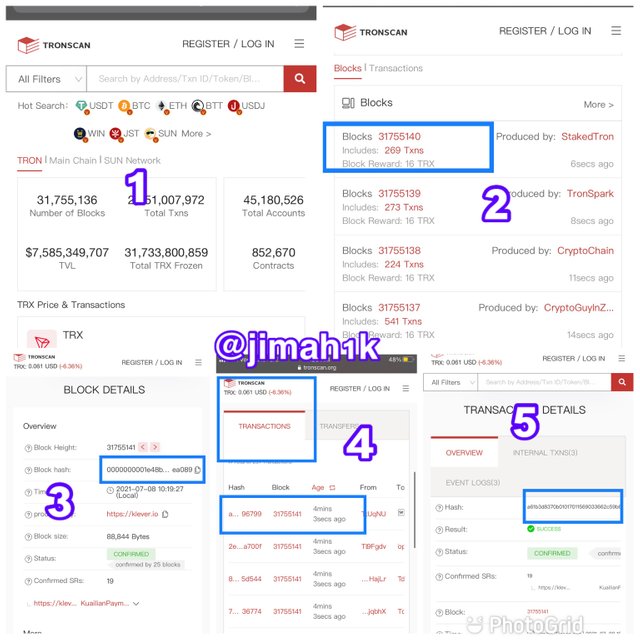
GO to their website you can do so using this LINK
click on the last block to revel its details
Just below the block height we can find out block hash which is
0000000001e48b85a3697dcdf3fe82a84621bb4c3d78d88672d4e78f0a0ea089To find out our transaction hash, on the same page scroll down you will see a section labeled transaction.
select the last block and click on it to view the details
the transaction hash is first on the details as
a61b3d8370b01017011569033662c59b6d069ecb031836bd82f971f7ab496799
BELOW ARE SCREENSHOTS TO GUIDE YOU

QUESTION 3
GENERATE THE HASH USING SHA-256 , FROM THE WORD CryptoAcademy AND FROM cryptoacademy. SCREENSHOT REQUIRED. DO YOU SEE ANY DIFFERENCES BETWEEN THE TWO WORDS? EXPLAIN.
Go to the website
type ‘CryptoAcademy’ and click on generate
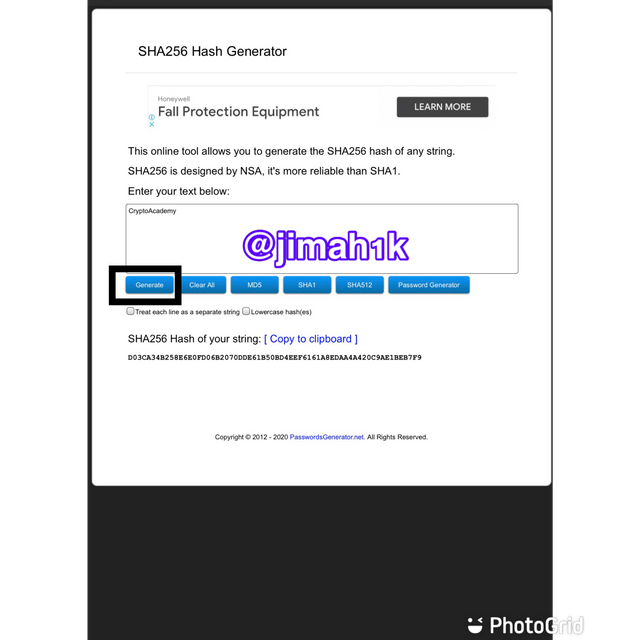
- the hash of the word ‘CryptoAcademy’ is
D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
With the second case we will be using ‘cryptoacademy’
Go to the website
type the word ‘cryptoacademy’ and click on generate.
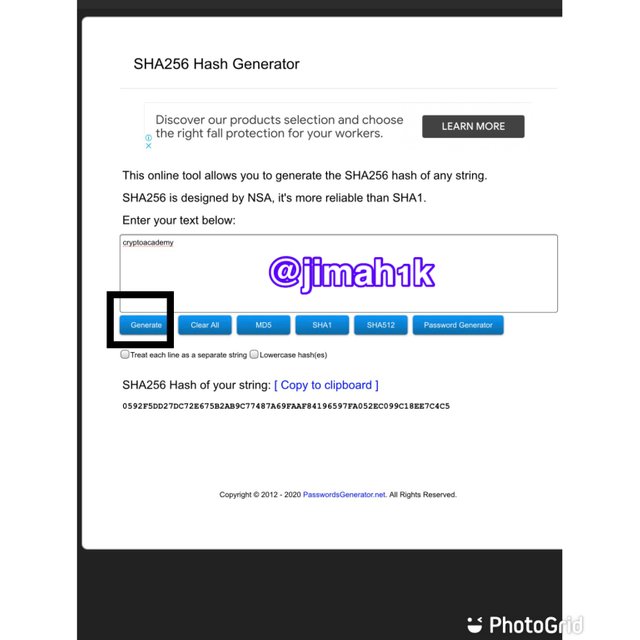
- the hash for the word ‘cryptoacademy’ is
0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Yes! The first word ‘CryptoAcademy’ is made up of capital letters and small letter whiles the second word ‘cryptoacademy’ is only small letters making the words completely different. So therefore making the hash outputs completely different. This is a pure example of resistance collision since the two words aren’t the same the output hash will never collide. The hash of capital C is different from the hash of small c. I also made mention of SHA-256 being resistance to collision.

QUESTION 4
IN YOUR OWN WORDS EXPLAIN THE DIFFERENCE BETWEEN HASH AND CRYPTOGRAPHY.
Before I begin with the difference I have already explained what a hash is let me also explain what cryptography is, I would say it is the encryption and decryption of data or information for example let’s say I want to send a message that I want only my friend to read I can encrypt it and send it to him so that he can decrypt with a key.
| HASH | CRYPTOGRAPHY |
|---|---|
| When the data is encoded into hash it cannot be reversed | The data encrypted can be reversed. |
| Security in hash are very secured especially SHA-256 hash, since no keys are involved in storing the data | keys are involved in storing information once you misplace your keys and someone gets access to them you can be hacked |
| In hash it has a fixed size | the size of the encryption code depends on the data |
| Examples of hash functions are SHA-256, MD5 and many more | cryptography uses algorithms like RAS, DES, AES |

I want to say this lecture has been very good to me it has exposed me to research on hash functions and cryptography both the hash and the cryptography all ensure our safety in the blockchain and are very important, I also found out that it very difficult to break a hash it can take up to many years and also our steemit private keys are made from hash functions. I have really learnt a lot from this lecture I hope to continue in the coming weeks.
THANK YOU.

Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Las captures de pantalla para corroborar los hash estaban muy unidas y me costó poder hacer el rastreo. Sin embargo, noté que tronscan el último bloque y el bloque de la transacción son diferentes. 31755140 y 31755141.
Recomendaciones:
Calificación: 8.1