Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u | Let's Open the Cryptography
You Are Highly Welcome My Season 3 / Week 8 Homework Task That Was Given By Professor @stream4u
1. Explain the Blockchain CryptoGraphy
Blockchain cryptography is not just a simple topic to understand. Although, the topic can be understand if we know the fundamentals working of cryptography. Before i continue with the blockchain cryptography, let's look at how communication is broadcast through radio signals. The communication through radio signals help us to listen to broadcast on our handset, radio set vehicle's etc because the broadcast is open for everyone to have access to it.
Generally, cryptography is serve/stand as the technology that is put in place to handle the transmission of secured messages between two or more users. This mean that the sender leverages a special kind of key and algorithm for encryption of the message before the message was send to the receiver. At this point the receiver will employs decryption before receiving the message. We can now see that encryption keys is very important when it comes to cryptography, as it prevent unauthorized users from reading our messages, information or transaction.
With the simple explanation on how cryptography work, we can also perfectly now understand, blockchain cryptography.
Blockchain CryptoGraphy is the system that prevents third parties from accessing and viewing information. Blockchain cryptography converts the information of users into a format that is undecipherable for third parties without authorization to read and view information. When studying blockchain cryptography there are some words that one would likely come across words like encryption, decryption, cipher and keys. Cipher is an algorithm that in used in the blockchain cryptography to assist in executing of encryption and decryption by following a numbers of steps that are being program. Keys is what gives users the permission to access from the cryptography algorithm. Only users with the required keys can have access to obtain information. The below image is a description of what we're discussing about.
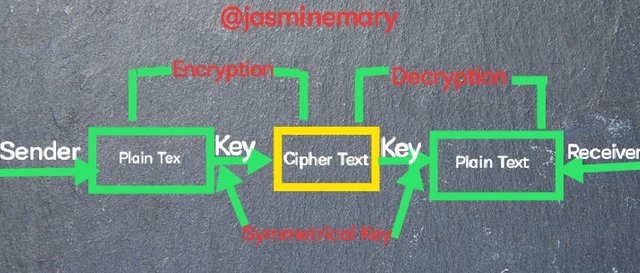
Image design by me
Objectives of blockchain cryptography
Integrity: Blockchain cryptography help to protect our Information from unauthorized users in a way that is not altered or detectable by third parties.
Confidentiality: Another objectives of blockchain cryptography is to ensures users information are kept secret within a certain circle of users not intended to be known publicly.
Authentication: Is to ensures that users identity is being proof before accessing the network.
Non-repudiation: Is to ensures that the message that is send by the sender is deliver to the sender without the support of third parties.
Mention few names which are the Blockchain Platforms?
Some of the few blockchain platforms are;
EOS blockchain, Ethereum blockchain, Stellar blockchain, Cardano blockchain, Ripple blockchain, Binance Chain, Tezos blockchain, Hyperledger Fabric blockchain and many others.
2. Explain the Public Key CryptoGraphy
Public key is usually referred to as asymmetric keys cryptography, the public key is the key that is shared openly which requires two separate keys known as the public and private key. The public key is the key that we use to proof the ownership of our private key, as the name implies public key it help two parties that are unknown to each other to share information in a secure way using a pair of keys to encrypt and decrypt their message from another user with authorized access. The function of the public key is for the receiver to decrypt the message that the sender send using the public key of the sender's, once the message reach, the receiver decrypts the message using a private key, that is hidden from others.
The benefits of public key cryptography
Public key cryptography provide users digital signature that cannot be deny or manipulated.
Public key cryptography ensures every user to be in control of their private key by probably safeguarding the key from unathorized users.
The public key stand out to be the most secure protocol than the private key since it doesn't permit users to transmit or shared out their private keys to anyone, which limit the chance of their account from being compromise.
3. Explain the Private Key CryptoGraphy.
The private key is also called secret key and is also part of asymmetric keys cryptography. The private key as the other name implies secret is the key that is only known to the owner and to kept private. Private key is meant to be shared with the key's generator or authorised third alone as it's okay an important function role in asymmetric cryptography. Example the used of private key in steemit is very important,in Steemit wallet. Without private key Steem and SDB cannot bevtransfer out of our wallet, which is always advisable for we to keep it safe and secret from unathorized users because losing access to our private key means losing access to our wallet. Private key is a long pseudo-randomly generated sequence of bits that cannot be guessed by users because of how complicated the key is. Since we have now known how important our private key, I can say that the best way for storing private keys are storing them on an offline computer, storing them in hard copies that are very secured and writing them on our personal journal.
The benefits of private key CryptoGraphy
Private key cryptography is more secure in such a way that it cannot be easily hack.
Private key is good for encryption when transmitting data.
Private is faster when used compared to asymmetric encryption or with the use of password.
4. Explain the Digital Signatures CryptoGraphy
The words signatures is use as identification or to signify approval, presented in handwritten form. But that is not what we are going to discuss about instead we are going to discuss about digital signatures cryptography. Let's us get started....
Digital Signatures CryptoGraphy is simply a form of electronic signature for verifying the authenticity of information that is exchange over the web such as card transactions, cryptocurrency transactions, emails and any other transactions that is perform online. In a nutshell, digital signatures cryptography is a mathematical technique that is program on the internet to verify digital messages or electronic transactions before getting approval.
Digital signatures cryptography has it own identity that is very unique to protect both the sender and the information that is send digitally. Digital signatures cryptography is usually used in the areas of software distribution, financial transactions, email and many others to ensure that the verification of authentic transactions are approved.
Importance of Digital Signatures CryptoGraphy
Digital signatures cryptography is considered to be one of the Vital tool when it comes to online security traits. Aside the non-repudiation of message that is provided by digital signature there also several important that it provides to users which are: Authentication of message,Integrity of users data and Non-repudiation.
Signing a Transaction/message
Signing a transaction/message is a way to proof that you are the rightful owner of the address by providing your private keys as a means of verifying the authentication of the transaction/message. For your transaction/message to be sign in,the transaction/message is to put into a function known as sign in, together with your private key. As soon as your transaction/message is sign in the result of your sign in will be known as the signature, that approved your transaction/message and sent it to the network that allow you to login and view your information. Some platforms requires the use of verification to proof that transaction was signed in by the owner of the private key of the address that is attached to the key to confirm their authentication.
5. Explain what is Symmetric and Asymmetric cryptography?
Symmetric Cryptography
Symmetric cryptography is focused on a single shared key that all the users know about which is use for encryption and decryption of data. Data is translated in such a way that it cannot be read or understood by another person that does not have access to the private key. The symmetric cryptography, is consists of two different types of encryption algorithm which is the Stream algorithm and the block algorithms. And also Data Encryption Standard (DES) and Advanced Encryption Standard (AES) are part of examples of symmetric cryptography encryption that are widely used on the internet. Although there are some other examples like Rivest Cipher 6 (RC6), International Data Encryption Algorithm (IDEA) etc that are also examples of symmetric cryptography encryption algorithm.
As earlier said,if you make use of symmetric cryptography algorithm, your data will be translated in a form that another person without the screte key to decrypt it cannot understood or read except the receiver with the secret key that is to him/her by the sender, can be the only person who can read and understand the message.
Asymmetric Cryptography
Asymmetric cryptography, is refered as public key cryptography since it make uses of the public key to encrypt and decrypt data. Here I can say is the opposite of symmetric cryptography which make of private key to encrypt and decrypt data. The asymmetric cryptography is consists of two unique keys known as the private key and the public keys which are used to encrypt and decrypt data. As earlier said, private key is a personal key and is meant to be kept safe, whereas the public key is open to the public. For example, i @jasminemary (sender), and @stream4u (receiver) we both want to send a secret document across each other, we will both share our public keys that is to say, I will give out my public key to @stream4u and he also will do the same by giving me his own public key. Once I receive the key I will then use it an encrypt the document since the document is meant to be send to him once I send the document @stream4u will make use of his private key to access the document and no one else can access it with the use of the his private key.
6. How Blockchain Wallets CryptoGraphy works
In other to understand how blockchain cryptography wallet work it would be better for us to know what is blockchain wallet cryptography. Now let's get started with the word blockchain wallet that we have. Blockchain wallet, is simply a cryptocurrency wallet that allows us to store, manage and also trade our various types of cryptocurrencies.The blockchain wallets cryptography work with two types of keys, the public and the Private keys. The private key is the key that is uses for any transaction that involves funds. If you want to transfer your crypto to another person is the private key that you will use to authorize the transaction. Without the private key your transfer of coins will not works. Blockchain wallet cryptography also works with the public key as it's the get that give you access into your wallet. The key allow you to sign in into your wallet.
The available types of Crypto Wallets.
Basically there are two types of crypto wallet which is Hot and Cold Wallets based on their functions.
Hot Crypto Wallets
This is the type of wallet that are access online. Hot wallets are connected to the internet through which we can login into the platform online and access our cryptos. Hot wallets has a lot of features which make it user friendly. The hit wallet is mainly users for daily transactions like buying, storing and selling of crypto. An example of hot wallets are wallets like Blockchain.info, Coinbase and other few wallet .
Cold Crypto Wallet
Cold Crypto Wallets is known as the offline wallet it doesn't require the use of internet for one to store his/her crypto everything concerning it transactions are done offline and then disclose into online. The essence of this wallet is the high security assurance that it has. An example of cold wallets are Ledger, Exodus and Trezor
7. What is the Merkle trees and it important
What Is The Merkle Tree?
The Merkle tree is also called binary hash trees, is a structure of data that is used to encode cryptocurrency data in and efficient and secured manner. In a other way round, it's a data structure that is used in the applications of computer science in blockchains to give out reliable and secured data.
In blockchain,like bitcoin's a block of transactions is passed through an algorithm to produce a hash,of which a long number, letters with structure can serve as a means of verification to the data if it's the same as the original data,the markle tree will only check if there are the same by separating the original from the new data.
importance of Markle tree in blockchain
Markle tree is important in blockchain as it authorized users to verify certain transaction with the user trying to download all the blockchain.
It is also allow users to verify and checked that has to do with hashes are accounted for.
It minimize the memory space that is needed to perform data storage and validation in blockchain.
It improve the efficiency of data and transactions in the blockchain.
8. Practical + Theory- The functionality of Key, Signature, Transaction and Blockchain
In other to understand the functionality of key, signature, transaction and blockchain in this homework task we will be using the Anders Brownworth Demo in exploring them. Let's get started.
Key's
Here in this part we will be discussing about the public key and the private key. As started early in the beginning of this homework I make mention that the both keys are linked together as part of asymmetric keys. Okay let's now see if the both keys are the same by visiting Anders Brownworth Demo.
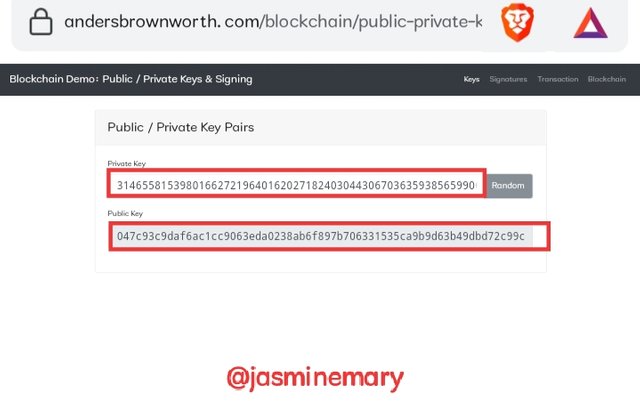
Looking at the screenshot above, we can see that on the landing page of Anders Brownworth there is a unique Private Key and Public Key link to each other which I have copied and pasted below.
Private Key
3146558153980166272196401620271824030443067036359385659900608696275147518825
Public Key
047c93c9daf6ac1cc9063eda0238ab6f897b706331535ca9b9d63b49dbd72c99ce2937c8dc23665e1ce27d6bb98dd6440e5ca20c55b2c8c070fc785763baa043db
After l have finished looking at the key above, I then clicked on random to see and I got a new Private and Public Keys was generated. Below is the screenshot.
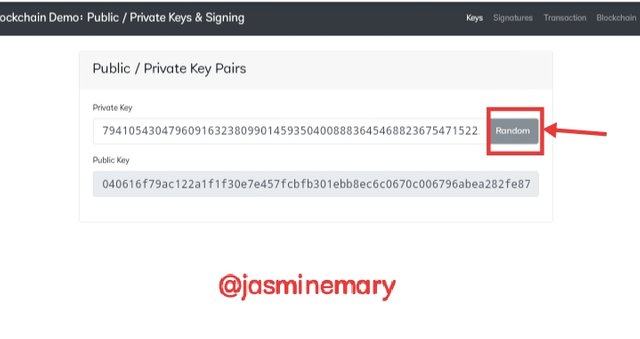
Private Key
79410543047960916323809901459350400888364546882367547152221242007344455219148
Public Key
040616f79ac122a1f1f30e7e457fcbfb301ebb8ec6c0670c006796abea282fe87b553469f9fa9f60de1a5d5fe29e36cd8e35611caee43adce076101911d14dce79
After looking at the two screenshots above I then discovered that the both keys are unique to each other but have different function. This is because there are all part of the asymmetric-keys algorithm. Let's take a look at the below screenshot where I change the private key to Digit number below.
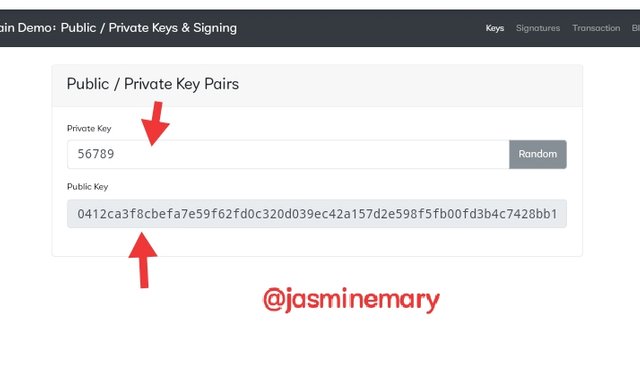
Looking at the screenshot above,you will see that I changed the private key to Digit number as 56789 and the public key is; 0412ca3f8cbefa7e59f62fd0c320d039ec42a157d2e598f5fb00fd3b4c7428bb19e95e351cc220209d9d411faefa585c8012516e25ee219395cd555d062820c26c . From the screenshot it has proof to us that truly the private and public keys are unique and link to each other with a different function.
Signature
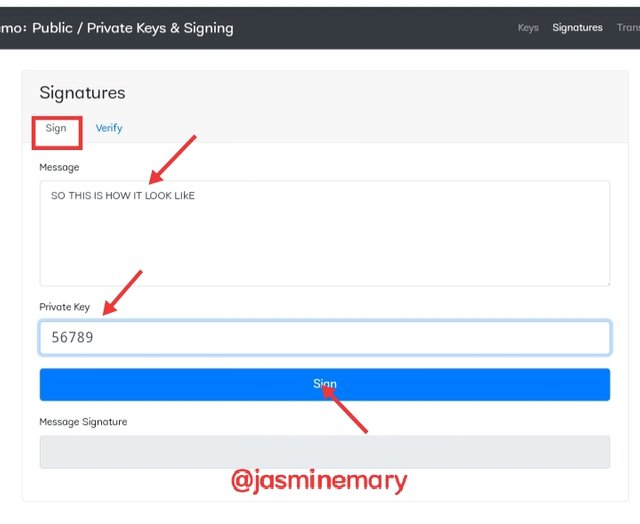
Here we will be discussing about sign transaction/message using private key to create digital signature and the public key to validate the authentication of the private key to Iadded block transaction. In this section I make use of 56789 as my private key. Let's get started to the section of the signature below.
The sign section under the signature is where I entered a message as; SO THIS IS HOW IT LOOK LIkE.
After entering the message, I then enter my private key as 56789 and click on the Sign and a Digital Signatures was generated. Below the screenshots.
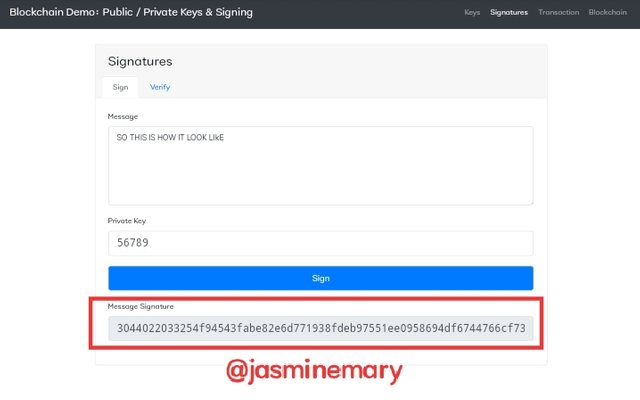
Looking at the above screenshot, we can see that the message signature is; 3044022033254f94543fabe82e6d771938fdeb97551ee0958694df6744766cf73d0d7b6402207ed26e0ba22c5388b40b1e0d577c66f878f6bc644f134d1c47686b1078428250 which is the transaction signature.
- Now at this point I clicked on the Verify section which is supposed to be the work of a miner to validate the authenticarion of transaction using the private key. Since my public key that is link with my private key has been share with the miner, I clicked on Verify to finalize the verification process.
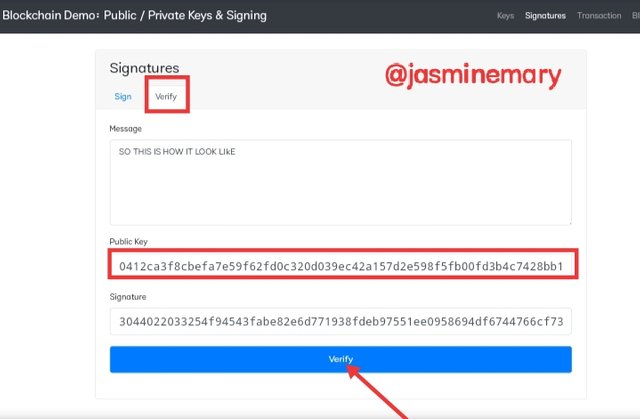
Public key:
0412ca3f8cbefa7e59f62fd0c320d039ec42a157d2e598f5fb00fd3b4c7428bb19e95e351cc220209d9d411faefa585c8012516e25ee219395cd555d062820c26c
Signature:
3044022033254f94543fabe82e6d771938fdeb97551ee0958694df6744766cf73d0d7b6402207ed26e0ba22c5388b40b1e0d577c66f878f6bc644f134d1c47686b1078428250
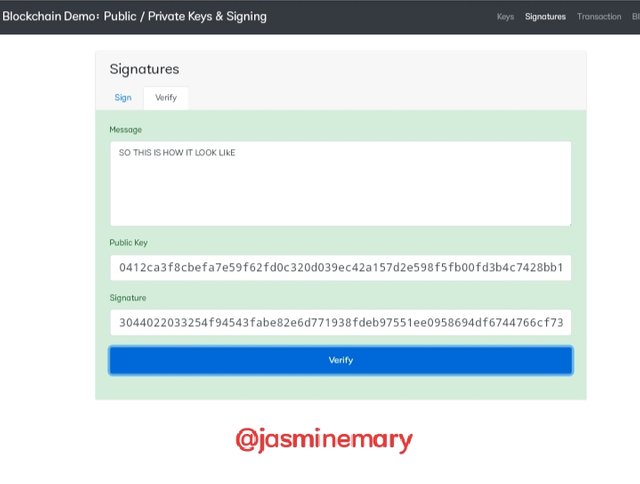
Looking at the above screenshot, you can see a green color at the last screenshot indicating that the private key is valid with the public key.
Transaction
This section requires the use of private key to sign in and the public key to verified transaction. Now is time for we to take a look on how the transaction is been carry out in a simple way.
- First, at the Sign section I entered $20 as my sending amount. My private key was supplied as 56789 and also my public key.
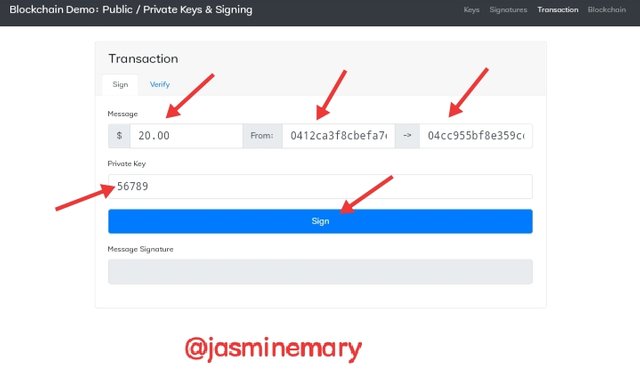
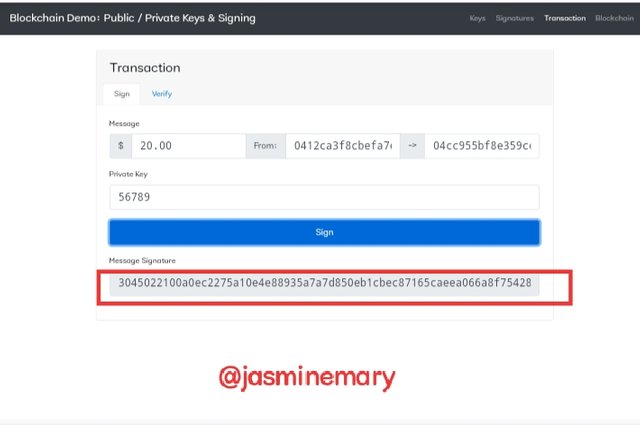
- As i clicked, on Sign and a Digital Signature was generated as; 3045022100a0ec2275a10e4e88935a7a7d850eb1cbec87165caeea066a8f754283ab8d23ab022021651eccd5eafee70aaaf7cfb004149466f04d55b99c5a7bafd719cfb3aeca6a
- At this point, I did what I did at the signature section by clicking on Verify button wich is the work of a miner to validate the authenticarion of transaction using the private key.
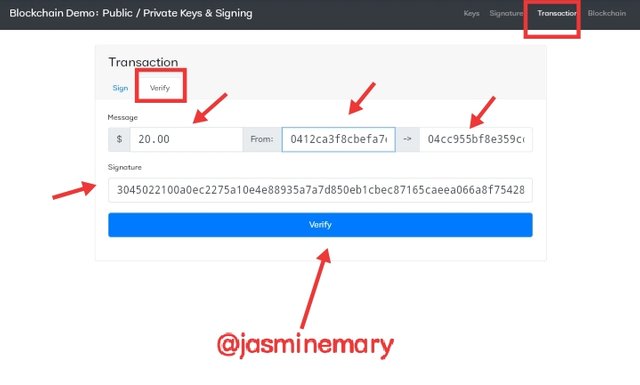
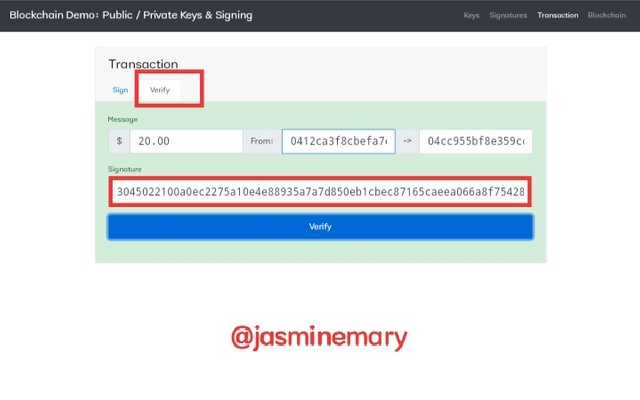
- Since my public key that is link with my private key, it was shared with the miner, I clicked on Verify to finalize the verification process.
Blockchain
This section, is where we will discuss briefly and look how transaction are stored in blocks with a valid hash that is generated using part of the cryptography hash. From the screenshot below are valid blocks that is added to after Verification has been done.
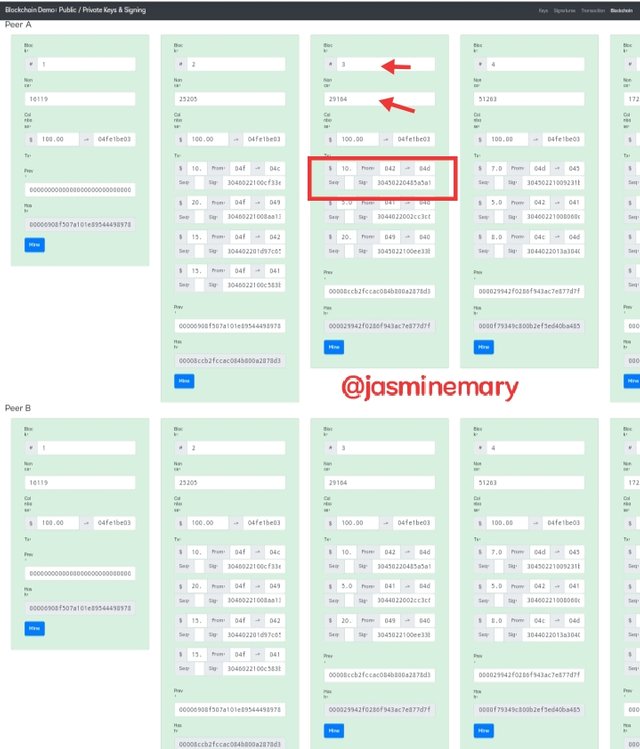
We can see that I have change the block 4 transaction to $15, and below is the result that I got.
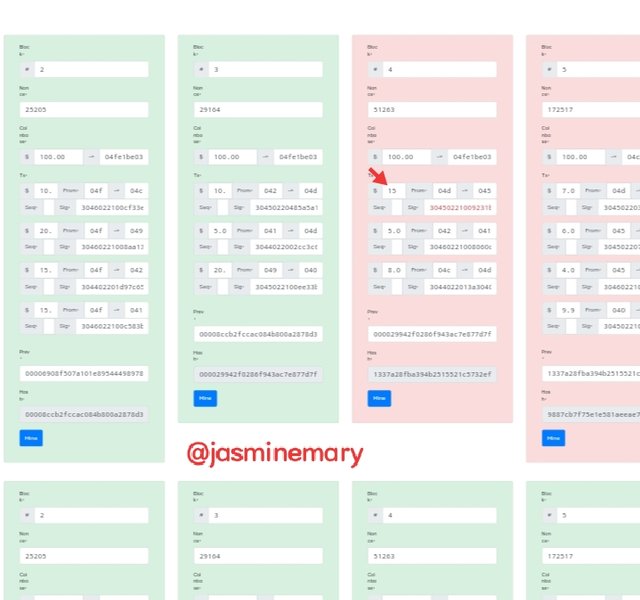
We can also see again that as I also try to change the information of block 4, it turn to read indicating invalid block, and in other for me to me it a valid block that means I have to re-mine, all the blocks that come with the one I changed, we can also see red in the Block let's see if the block can be re-mine below.
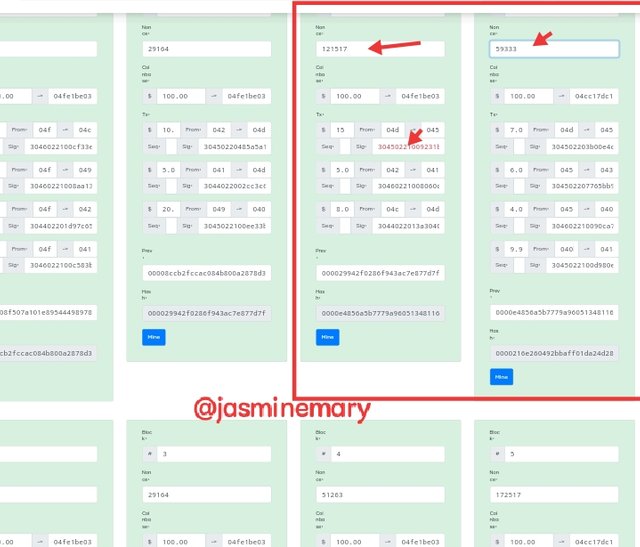
Looking at the above screenshot, I have suçcessfully re-mined the blocks 4 and 5 using a new Nonce as 121517 and 59333. We can also see that the block 4 digital signature is still invalid because I make used of another private key and public keys to signed in.
Conclusion:
The Blockchain cryptography has taught us so meaning things like we knowing what is cryptography, asymmetric and symmetric cryptography, how private/public keys works, Digital Signatures and a lot more that we have learned in this homework task, things that we have no ideas before we have now have and ideas on them........