Steemit Crypto Academy, Season 3: Week 4 || ROOT HASH AND MERKLE TREE. By @hydra1


Explain in detail the hash rate.

The hash rate can not be ignored in the world of cryptocurrency and the blockchain at large as it plays an important role in the computation of large mathematical computations.
What Is Hash Rate?
Hash Rate can be simply defined as the unit of measurement that measures the processing power of a computer network during the mining process. In short, it refers to the total number of hashes that can be calculated by a specific computer processor in seconds. For example, if we are to mine 10m/s on a particular network, what it means is that the miner can complete the algorithm 10 million times in a matter of seconds. As it stands, a blockchain with an extremely high hash rate indicates that the blockchain network is highly secured, thereby making it extremely difficult for intruders to breach the network.
As it is stands, there is no specific formula used in the calculation of hash rate, and this has brought about differences in algorithms in the calculation of hash rate. This means that the hash rate of Ethereum will be different from the hash rate of bitcoin even if the computation was done on the same machine.
Some popular hash Rate
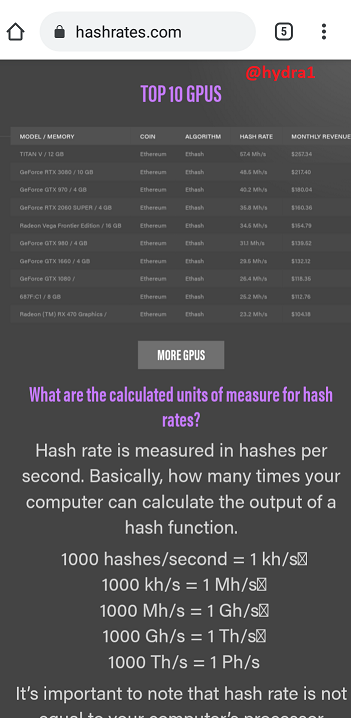
screenshot taken from hashrates.com
The Importance of Hash Rate
As decentralization is the core mandate of blockchain, verification of transactions is not done on a single computer but rather on a multiple of them, thereby making hash rates extremely secure and hard to breach. Moreover, hash rate computation for the lone miner tends to be much more profitable in their prediction process.

Make the following Merkle Tree: Transaction (tree leaves): Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8, Made it to the Root Hash. And put every hash generated using SHA-256, show screenshots, Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
To be able to get the hashes of the leaves given, one has to open the browser and visit https://passwordsgenerator.net/sha256-hash-generator/ and type in the leaves you wish to convert to get the hashes.
Now let’s convert the leaves given to get the hashes.
| Tree Leaves |
|---|
| Steem1 |
| Steem2 |
| Steem3 |
| Steem4 |
| Steem5 |
| Steem6 |
| Steem7 |
| Steem8 |
Hash codes for the various tree leaves
Steem1
Hash: 7760E25BCB80ADF1DD92DB339BF5790A59E90CD54EFA072F1250DCE13FA97045
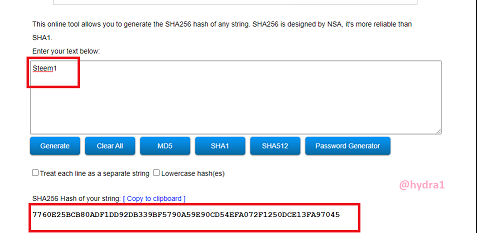
Steem2
Hash: FE00506E91CF52BC4B35321E6B978D1A7349397B19C6C1C01E095971FDEC9741
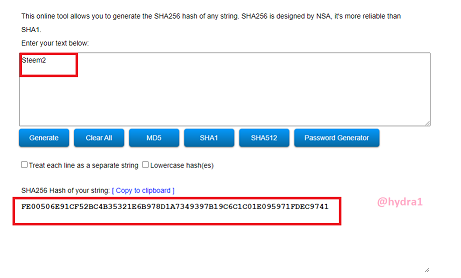
Steem3
Hash: A9418332E0C351D6A50C835AA9E57D514F0573C231D491E97726DB8A5844F2DC
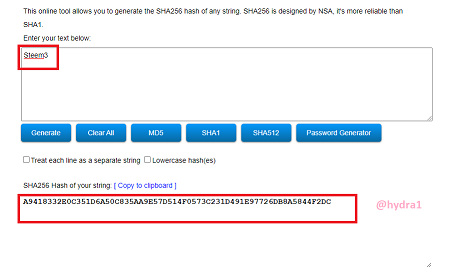
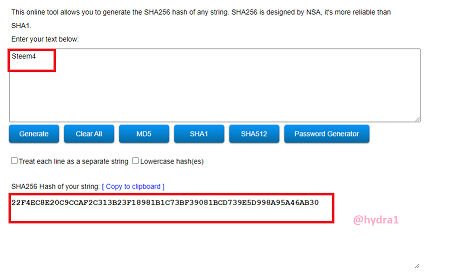
Steem4
Hash: 22F4EC8E20C9CCAF2C313B23F18981B1C73BF39081BCD739E5D998A95A46AB30
Steem5
Hash: 2A3C87336683AB0DDFA56AFEFC740E6C13A02FEA0A43D6797343B26D7AF0C57B
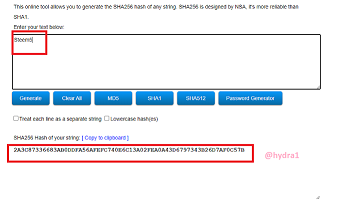
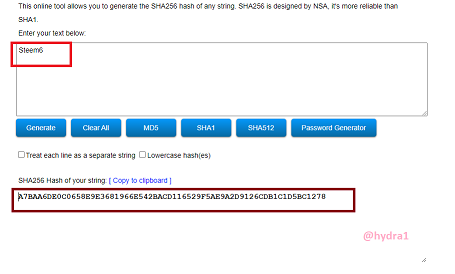
Steem6
Hash: A7BAA6DE0C0658E9E3681966E542BACD116529F5AE9A2D9126CDB1C1D5BC1278
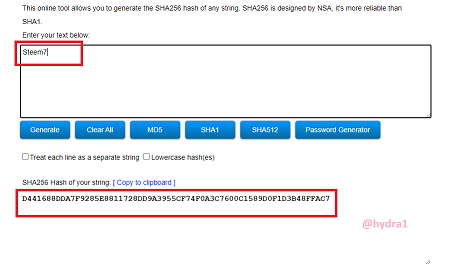
Steem7
Hash: D441688DDA7F9285E8811728DD9A3955CF74F0A3C7600C1589D0F1D3B48FFAC7
Steem8
Hash: F2E38ED4FF662087B6E9BEAFA4158EBC488B995732057BDA019A6A77FFB5F9F5
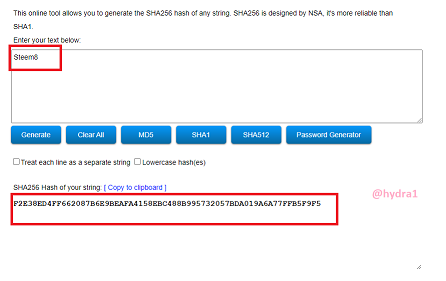
Steem1Steem2
Hash: A5568957014F6AC3866923C7DE20D375E706B8D8C9F453636E90B9965ABEC62B
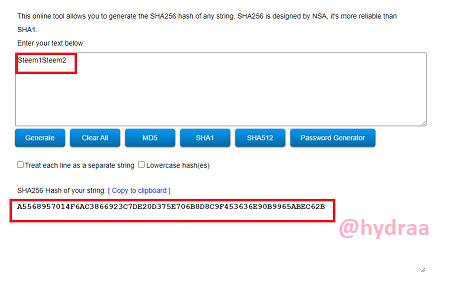
Steem3Steem4
Hash: 18D25196DB699F6AB9222B7302EB8A6F6EBFADEC703C07DD5DB8D9455913A499
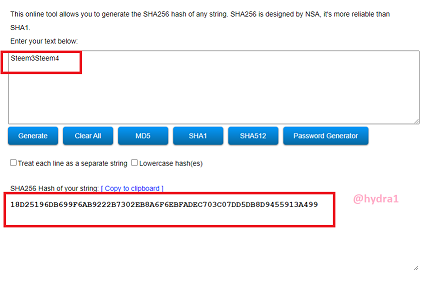
Steem5Steem6
Hash: D118E137F92A0DBEA138B6BF70C7714153A7BC393CD0272A44BD94864645224B
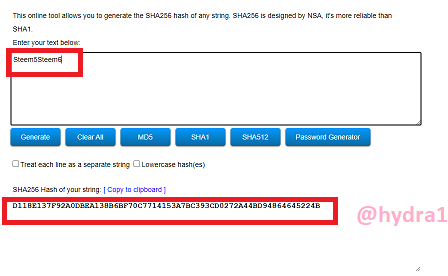
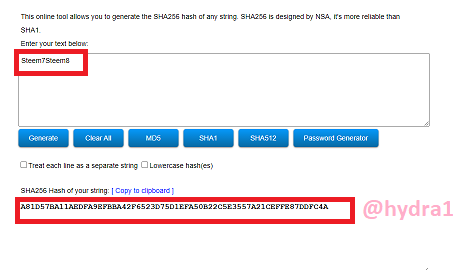
Steem7Steem8
Hash: A81D57BA11AEDFA9EFBBA42F6523D75D1EFA50B22C5E3557A21CEFFE87DDFC4A
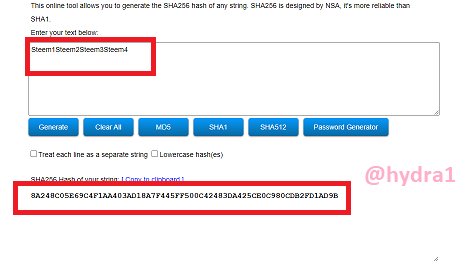
Steem1Steem2Steem3Steem4
Hash: 8A248C05E69C4F1AA403AD18A7F445FF500C42483DA425CE0C980CDB2FD1AD9B
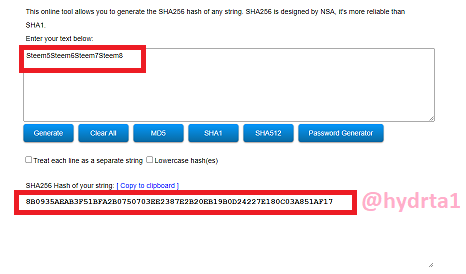
Steem5Steem6Steem7Steem8
Hash: 8B0935AEAB3F51BFA2B0750703EE2387E2B20EB19B0D24227E180C03A851AF17
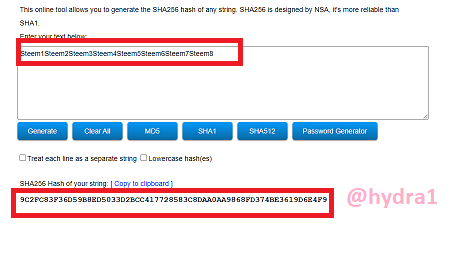
Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8
Hash: 9C2FC83F36D59B8ED5033D2BCC417728583C8DAA0AA9868FD374BE3619D6E4F9
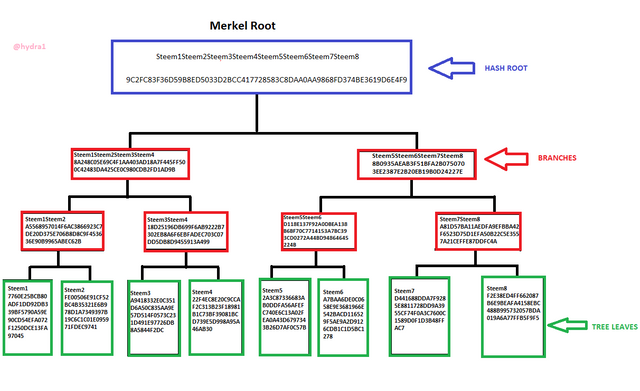
Merkel Tree
Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
As we all know, a merkel tree consists of a root, branches and leaves. With the help of the tree branches, one can easily be able to know whether a particular leaf is verified in the merkele tree by tracing it to the tree leave, then tracing it to the branch and lastly tracing it to the root. So, in this case, we crosscheck to see whether Steem6 is verified in the Merkel tree. We can see that Steem6 is part of the node leaves, as well as in the branch, and finally part of the root.
Verification Process of Steem6
- Firstly, we calculate the hash of Steem6 as a leave
- We already know the hash of Steem5. We calculate the hashes of Steem5 and Steem6 together to get the two hashes combined as a sub-branch.
- We then calculate the hashes of the main branch which Steem6 is part of. That gives us Steem5Steem6Steem7Steem8 hashes.
- Since we know the hashes of Steem1Steem2Steem3Steem4 as another branch, we calculated them together with Steem5Steem6Steem7Steem8. That gives us
Steem1Steem2Steem3Steem4 Steem5Steem6Steem7Steem8 to get the Merkel Root.

Using the SHA-256; you must place each complete hash in the Merkle Tree.
Transaction (tree leaves): SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8. Explain each step, show screenshots.
If the number of leaves on the tree is odd, what should you do? Explain.
SCA1
Hash: EE4A6793EC56CB92DA3EC9967B3F35658DA02B779AAB72AB9E59131AD9E0B47B
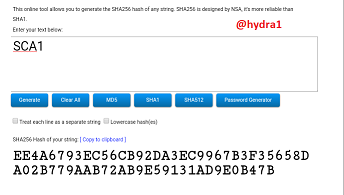
SCA2
Hash: C309F7BD3D55C00E6B5B553DECCF75F522F3A3C6A13DB9CDD392C6CB796F79CB
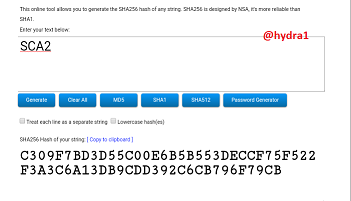
SCA3
Hash: 26D48266FAD546F60B3A15D40272D1EB85CEAFD66BD35C077AE8C81589C60E54
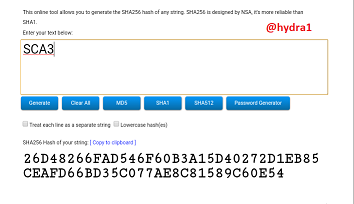
SCA4
Hash: 256E38765FAB36625D16D90AAFDFCDD284CC9615F5F4A9E25D6286A257A24429
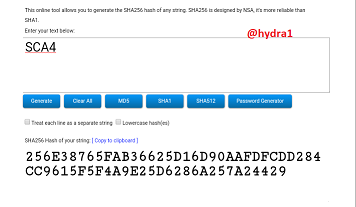
SCA5
Hash: C34118E435ED40C28CC16D8FACA614520DF6473B28122334F4FCF344262AF2CB
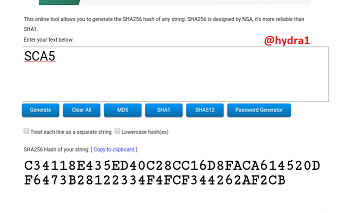
SCA6
Hash: B0DE3285E96E700389819959E35436C6D1FF503F43B63CEDEDE53EFBE03075E0
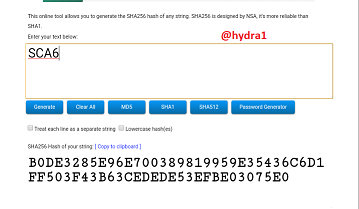
SCA7
Hash: 289DA20BDFDEB1DEB9AA8B0E1E14E72D646902C9329A2E784261CB0E6C7071CF
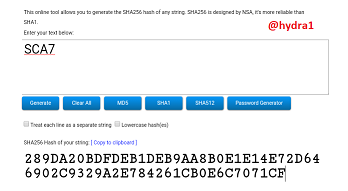
SCA8
Hash: 8B5B3E43BD6CA6F2B337AD2236A69EFD944519BDE4D83620F80C6BF05E81DAE6
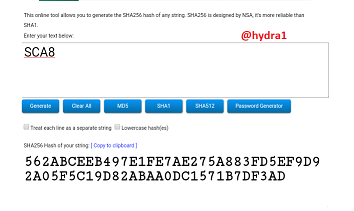
SCA1SCA2
Hash: 91B09BBA815748166FB36413342C7E4E7E809F4BAC538C0418841A4476B527EF
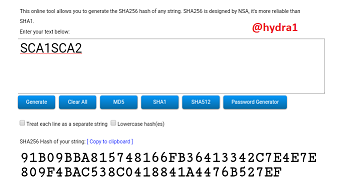
SCA3SCA4
Hash: B49B48697A3ACBC5E3D2E36B6EE49C44020D88E664C5C1AA7A7CF34058177379
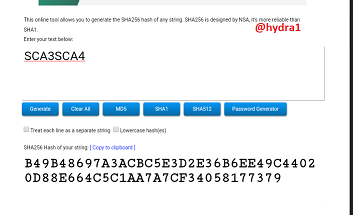
SCA5SCA6
Hash: F026924CD1285FF92C2A2DE9B9313027EB67273A82375C939348C887F6B52F77
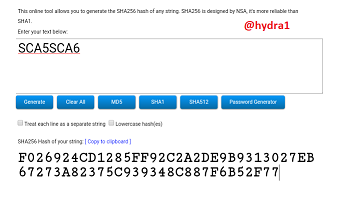
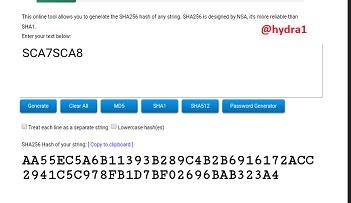
SCA7SCA8
Hash:
AA55EC5A6B11393B289C4B2B6916172ACC2941C5C978FB1D7BF02696BAB323A4
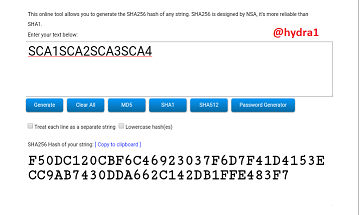
SCA1SCA2SCA3SCA4
Hash:
F50DC120CBF6C46923037F6D7F41D4153ECC9AB7430DDA662C142DB1FFE483F7
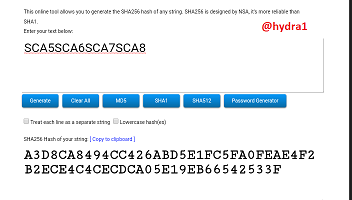
SCA5SCA6SCA7SCA8
Hash: A3D8CA8494CC426ABD5E1FC5FA0FEAE4F2B2ECE4C4CECDCA05E19EB66542533F
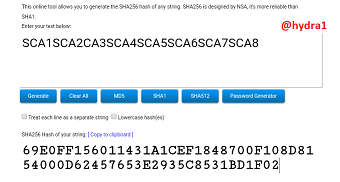
SCA1SCA2CA3SCA4SCA5SCA6SCA7SCA8
Hash: 69E0FF156011431A1CEF1848700F108D8154000D62457653E2935C8531BD1F02
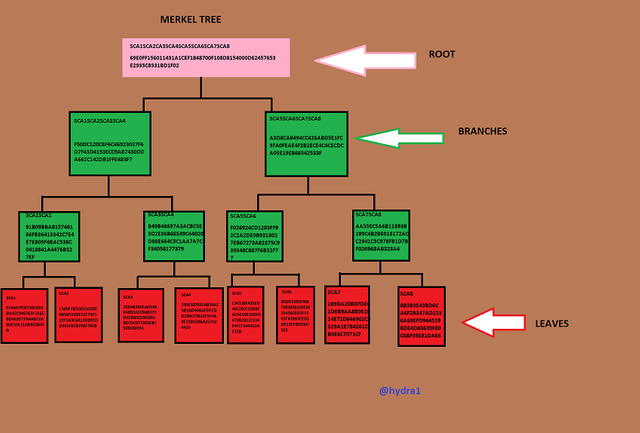
Merkel Tree
Well, by the nature of a merkel tree, it must be an even number, but there are instances where we may arrive at an odd number and how we solve that situation is simple. If we happen to have an odd number of nodes at any level, the last number is always duplicated and hashed with itself. To be able to understand this, let’s take an illustration for a better understanding. An illustration of 3 transactions (T1,T2,T3) on the merkel tree below.
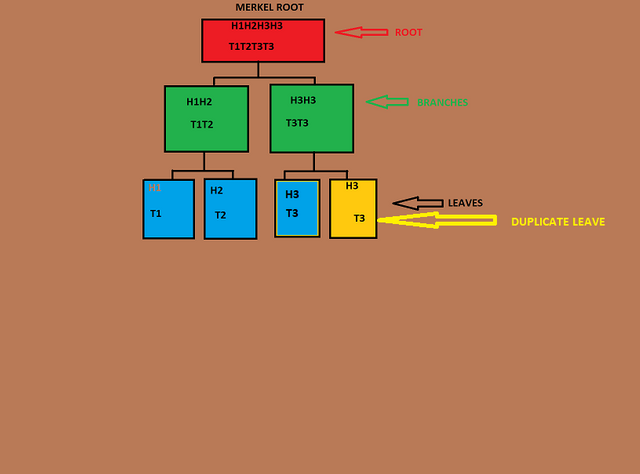

Conclusion

To conclude with, merkel tree are essential as it combines series of transactions together and as well makes it easy to single out a particular transaction when in pursuit.
Thanks for your time
Cc:
@pelon53

- 50 SP- 75 SP- 100 SP- 250 SP- 500 SP- 750 SP- 1000 SP- 2000 SP