Crypto Academy Season 3|| Week 2 Homework || Hash and Cryptography|| by @hydra1


Explain what does the resistance to collision mean? And what does resistance to preimage mean?

In the world of blockchain technology, hashes play an important role and should not be undermined and one can say hashes are fundamental building blocks of the blockchain technology.
Resistance to Collision and Resistance to Preimage can not be properly comprehended without knowing what hashes are.
A hash is a mathematical algorithm that transforms an inputted data with respect to its length into a fixed output encrypted length. Hashes boast of their secured nature in the sense that it is highly impossible to reverse their computation or crack them.
We can go ahead and define what Resistance to Collision and Resistance to Preimage is.
Resistance To Collision is considered to be a property of hash function, to be able to appreciate what it means, let's know what Collision means.
Collision simply refers to the process by which two inputted data generate or produce the same results or output. Now one can say that, Resistance To Collision is a property of the hash function, where two different input data should not generate or produce output. We can mathematically express it as X and Y, where they are two distinct variables, X≠Y, But H(X)=H(Y). where H(X) is the hash of X and H(Y) is the hash of Y.
Resistance To Preimage: When it is computationally impossible or infeasible to find the input to any defined cryptographic hash output, this is referred to as resistance to preimage. Finding the input that corresponds to a hash output is impossible with resistance to preimage.

Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.

Using Etherscan
- Visit https://etherscan.io/ where you will be able to see the latest block and latest transaction
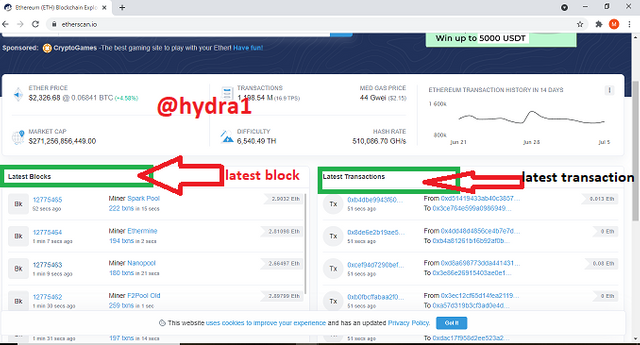
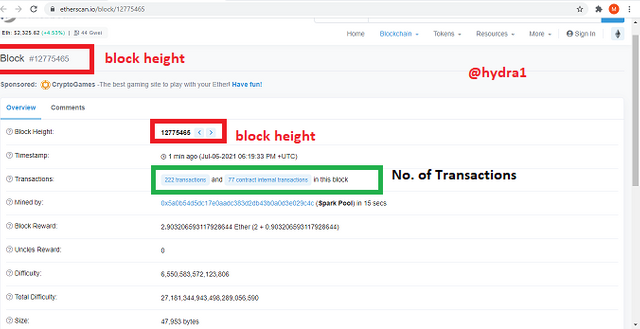
- Click on the first Latest Block where you will be able to see the block height 12775465 and the block hash
0x6f125c38dc6f1156883f79288f54b73c4fa7015621640689ef63facbe661747f
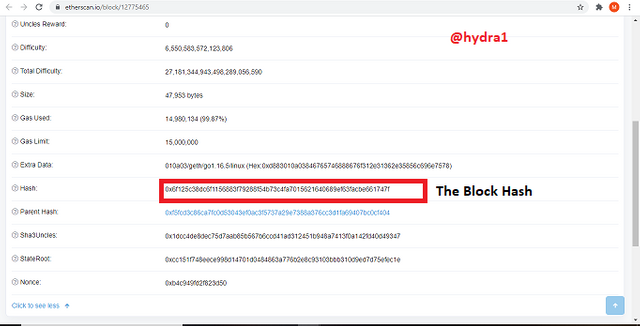
the hash
To view the first transaction, click on the first transaction.
In the transaction details, you will the transaction hash 0xb4dbe9943f600320175103e61fd7f1281a1169dfeccb21e50460ea506fb461b5 and the block number 12775465
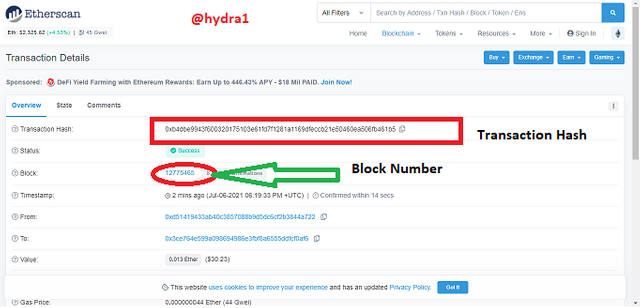
- To confirm this, copy the transaction hash and search for it. If it appears as the same then it is confirmed.
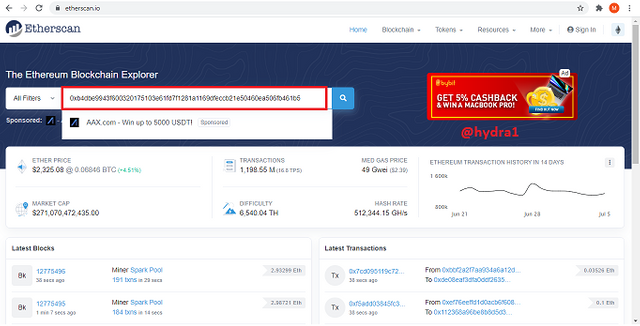 transaction hash search
transaction hash search
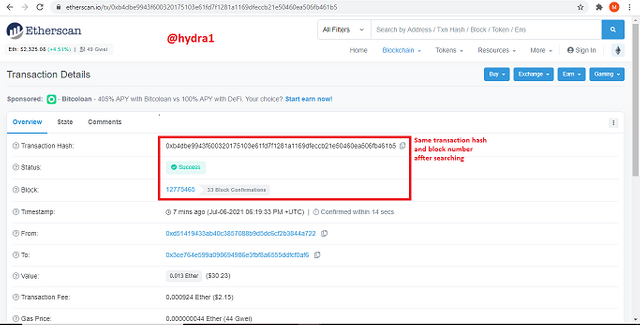
after searching for the transaction hash
Using TronScan
- visit https://tronscan.org/
- From there, you will be able to see the latest block and latest transactions.
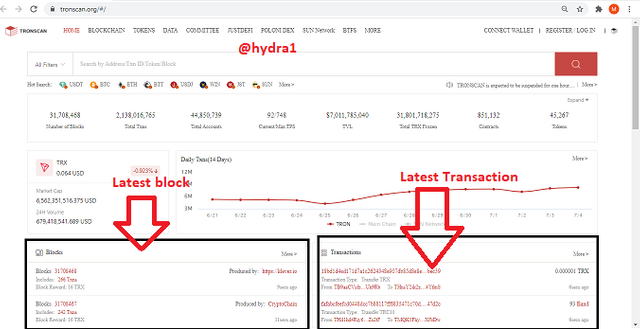
- click on the first block to view the details, you will see the height to be 31708478 and the Block Hash to be 0000000001e3d53e354156a14bb25b1f07b0cf3e369bb881062e64b07e6dee8e
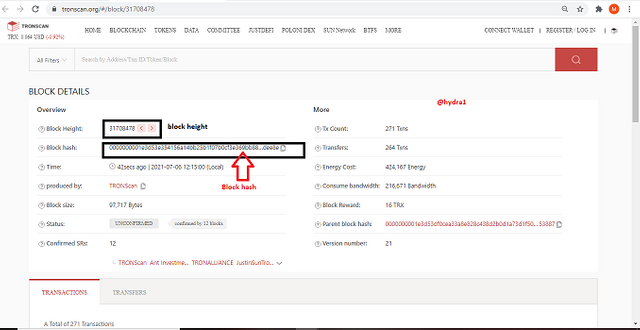
block hash
- To view the block transaction click on the first transaction, from there you can view the transaction details, where the hash is 6bcde722172652c364e44babb41abf093f065f4818cdedfdf1949dbd81ac9516 and the with the block height 31708479
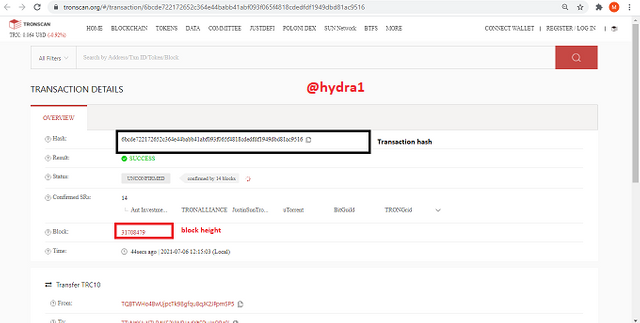
- To confirm this, copy the transaction hash 6bcde722172652c364e44babb41abf093f065f4818cdedfdf1949dbd81ac9516 and search for it. If it matches, then its confirmed
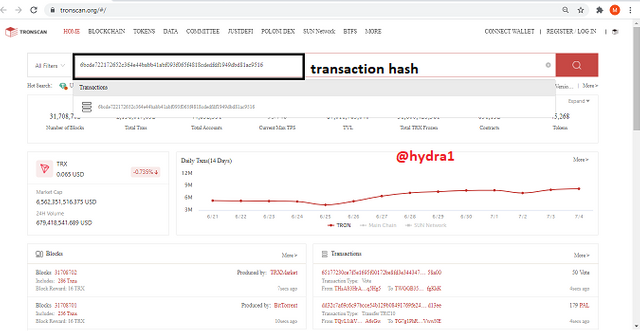
transaction hash search
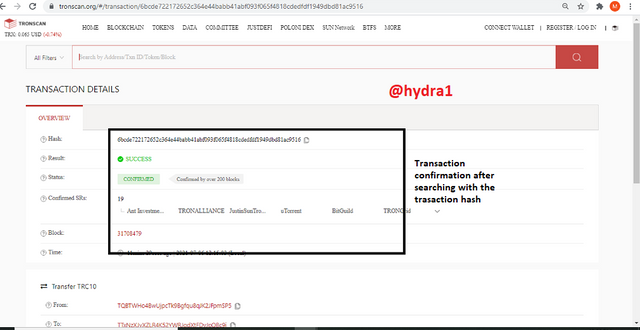
transaction confirmation after searching

Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.

To Generate Hash using https://passwordsgenerator.net/sha256-hash-generator/ follow these simple steps.
CrptoAcademy
- visit the official site https://passwordsgenerator.net/sha256-hash-generator/
- Type in your data you want to convert, in this case CryptoAcademy and click on generate
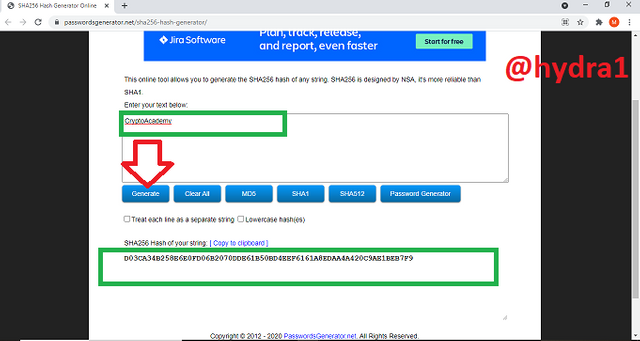
Our generated hash keys= D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
cryptoacademy
- Visit the official site https://passwordsgenerator.net/sha256-hash-generator/
- Type in your data you want to convert, in this case cryptoacademy and click on generate
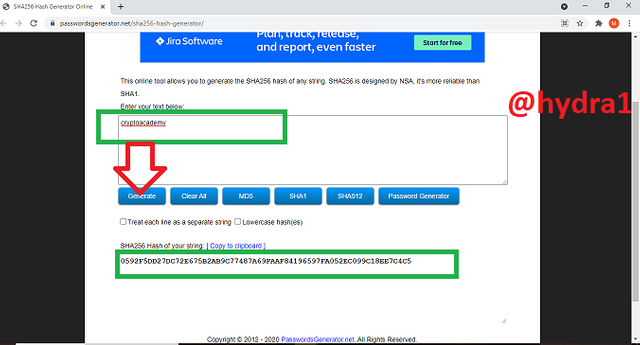
- Our generated hash = 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
OBSERVATION
In respect to the CryptoAcademy it generates the hashes D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9 and cryptoacademy 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5 there is a clear difference between the two. In the word CryptoAcademy there are two capital words C & A so it generates a different hash. To say that it is case sensitive. As we all can see in the word cryptoacademy they are all in smaller cases, so therefore it generates a different hash to mean that it is case sensitive. This is a clear interpretation of Resistance to collision. same words with different cases with the same meaning are generating different output.

In your own words explain the difference between hash and cryptography.

HASHES
As already stated, hashes are, they are mathematical algorithms that convert inputted data with respect to its length into fixed encrypted output. It generates an alphanumeric code by encoding data into a unique code with characters of 64 and prevents the repetition of such characters. Hashes over the years have evolved with MD2 being the first of the generation to SHA-256 being the latest.
Characteristics of hashes
- Irreversible
- They are secured
- They are Unique
Uses of Hashes
Addresses: Wallets addresses of blockchain are always unique from each other and how it was achieved was due to the hash functions where generation of both private and public keys is done.
Mining: Mining can not be left out as one of the uses of hashes, as we all know that in mining, much computational work is needed to be able to generate blocks and hashing tends to solve that problem, thereby making it easy.
Smart Contracts: For versatility to be achieved in smart contracts, hashes are used to store sensitive information in the blockchain. Examples of such smart contracts include Ethereum, TRON, Bitcoin and many more.
CRYPTOGRAPHY
Cryptography technology is used to secure user data while also enabling anonymity. As the world of crypto is all about secret, cryptography can not be left out in its operation. The basic purpose of cryptography is to ensure the security of transactions.
Types of Cryptography
Symmetric Cryptography: Symmetric cryptography is used to ensure that no unauthorized third party has access to the data.
Asymmetric Cryptography:Asymmetric cryptography makes use of two kinds of keys. The keys are public and private. Private keys should be kept secret and should not be shared with anyone, but with public keys can be shared so as to receive assets as they tend to be the receiving addresses of assets.
Hybrid Cryptography: It is a combination of Symmetric cryptography and Asymmetric cryptography to acquire speed and accuracy of encryption and decryption.
DIFFERENCES BETWEEN CRYPTOGRAPHY AND HASHES
| Cryptography | Hashing |
|---|---|
| Keys are required in cryptography in the Decryption process | They Do not require keys |
| Its primary purpose is to transfer data in a secure and timely manner While maintaining its user friendly interface | Its primary Goal and method of operation is to validate the input data and secure it with their codes |
| The primary goal is to conceal the meaning behind data | It entails converting data into a fixed value in order to reflect original data |
| Encryption and Decryption are its main processes | It is one way process that merely converts data to codes |

CONCLUSION

To conclude, hashes and cryptography are essential in the world of blockchain and should be strengthened more for maximum security. And I would like to say this lecture has been one of the best as the concepts were straight forward with simple understanding.
Thank you
Cc:
@pelon53
👆Es difícil, pero los atacantes pueden lograr su objetivo.
Muy buen trabajo, felicitaciones. Continué así.
Recomendaciones:
Justificar el texto.Calificación: 9.5
Grçias