CRYPTO ACADEMY SEASON 2 | PRIVACY COIN HOMEWORK FOR @levycore
Based on this week’s homework task, here is my article for the homework task given this week, I will like to given attention to them as follows:
- Choose a Privacy Coin and perform a fundamental analysis of the coin in detail.
- Describe the steps in creating a wallet for the privacy coin of my choice (Screenshot required)
- Explain the reason I chose the privacy Coin (State the advantages and disadvantages)
- Conclusion

TALK ON PRIVACY COIN
 Image source
Image source‘Privacy’ as the name implies, has to do with something, information or data that is off public attention which is meant for an individual or a user or occasionally for a group of authorized persons or people.
Privacy Coin is known as a cryptocurrency which allows a user to hide it identities, transactions or data from other users, securing it privately along with-it originalities making it undetectable or even unacknowledged from third party users.
WHY NEED PRIVACY COIN
Cryptocurrency and the digital or internet world has been a base where people earn both the users based on transactions and investments along with programmers who with the use of the subscribers or users personal data to make money alongside it founders, For instance, Google, Facebook and Microsoft are known to be a internet companies who earn through the use of users data entry or more.
Same with the crypto world, it programmers or founders of a particular private coin makes it easy for users to access or have power to their investments, earns or money, in that case, the need for users having not a limited but full access to its own privacy is essential because more users or traders are been attracted and are flooding into the crypto world, so the need of a user having power over it privacy coins is important in order to protect is coins.
CHOOSE A PRIVACY COIN AND PERFORM A FUNDAMENTAL ANALYSIS OF THE COIN IN DETAILS
PRIVACY COIN: ZCASH

Image source
In October 2016, Zooko Wilcox-O’Hearn founded ‘Zcash’ along with-it currency (ZEC) which was a response to the demand from users for a financial system with more modifiable and privacy features.
Zcash is a cryptocurrency which has a regionalized block chain that aids it users or traders, in its transactions or data’s anonymity, it uses unspent transaction output (UTXO), Zcash was build based on bitcoin core and protocol but with the difference of encrypted privacy preservation.
Unlike other Coins for example Bitcoin, they are traceable, while Zcash has zK-SNARK which shields transactions made and makes them untraceable, when transacting through bitcoin it determines whether a transaction is spendable with the use of the (UTXO) But as for Zcash, it’s centers on Commitment. The commitment process is recorded in every node and all the nullifiers can then be quickly produced using it shielded equivalent of UTXO.
Zcash keeps users in the space of using either a private or transparent transaction, It cryptographic tools used, allows users to engage in transactions without revealing their payment addresses to the other user which makes it untraceable, this is made possible with the use of the cryptographic tool known as (zk-SNARKS (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge)
WHAT ARE ZK-SNARKS AND HOW DOES IT WORKS
 Image source
Image sourcezk-SNARKS is a proof construction where one proves possession of a data or information without the interference of the verifier or the prover.
“Zero-knowledge” allows the prover to prove to a verifier of a true statement, without the divulge of any data or information.
"Succinct" zero-knowledge proofs can be verified within a few couples of seconds. During the first zero-knowledge protocols, the prover and verifier had to communicate constantly for many times.
"non-interactive" constructions proof consists of a particular message sent from a prover to a verifier and the best way to produce zero-knowledge proofs that are non-interactive and relatively brief to publish in a block chain is to have an initial setup phase that Initiate a common reference string between a prover and verifier.
With the zero-knowledge privacy in Zcash, the function which determine whether a transaction is valid or not without unveiling any information on where the calculations where performed which is done by encoding some network’s consensus rules in zk-SNARKs. Here is an overview of how the rules determine a valid transaction get it into an equation that can be evaluated without revealing any data or information to the verifier.
Computation → Arithmetic Circuit → R1CS → QAP → zk-SNARK
A transaction has to be turned into a mathematical representation to break down the logical steps in smallest possible ways for easy operation, this is done by creating an arithmetic circuit which breaks down into smaller steps that consist of basic arithmetic operations of addition, subtraction, multiplication.
Example of what an arithmetic circuit looks like for computing the expression (a+b)(bc)
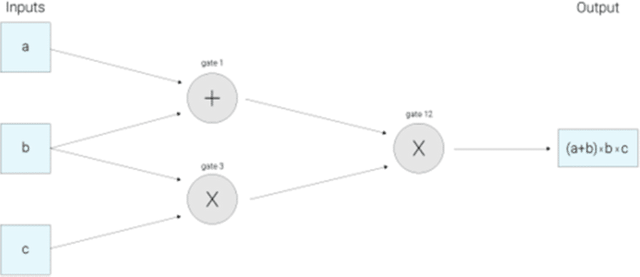 Image source
Image sourceThe value coming out of the multiplication gate where b and c went in is b*c.
From the circuit above, we see the input values a, b, c is traveling left-to-right on the wires in connection with the output wire, to confirm if the wires are travelling in the right path, the next step is to build a R1CS (Rank 1 Constraint System).
A representation method for the circuit called Quadratic Arithmetic Program (QAP) was founded by Gennaro, Raykova Gentry, in a 2012.The single constraint that needs attention is between polynomials rather than the numbers. it might hold at a certain point because it’s huge and the identity does not hold between polynomials. however, the two polynomials have to match which requires verification in order to correctly verify the proof with high probability.
With the explanation made, I have been able to know how to get a non-interactive, single message proof and how to get the S and N in “SNARKs”, as for the “zk” (zero-knowledge) it allows the prover to maintain the concealment of their secret inputs. It turns out that at this stage the “zk” part can easily add by having the prover use a random shift of the original polynomials which might satisfy the required identity.
TRANSPARENT AND SHIELDED ZCASH ADDRESS DIFFERENCE
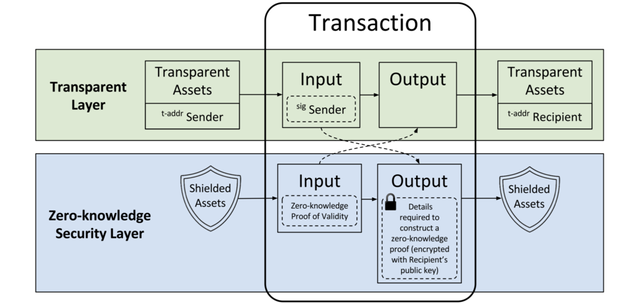 Image source
Image sourceZcash has two types of keys
- View key: Is used as a means of sharing data or information or for an audit without public attention.
- Spend key: Is used to spend funds.
Transparent addresses start with "t" which exposes addresses and balances on the block chain, while shielded addresses start with "z" which include the privacy enhancements provided by zero-knowledge proofs, as for the Sapling network upgrade which introduced a new shielded address for more functionality and improved efficiency which starts with a "zs" while the legacy shielded addresses start with a "zc".
TIP ON SHIELDED TRANSACTION
- When a shielded payment is made, a commitment is published that consists of a hash of the address to which the note was sent, a number ‘rho’ which is unique to the note amount sent along with a variable cryptographic nonce.
COMMITMENT = HASH (recipient address, rho, amount, r)
- The sender uses their spending key to publish a nullifier when transaction is spent which is the hash of the secret special number (“rho”) from an existing commitment that has not been spent.
NULLIFIER = HASH (spending key, rho)
- A shielded transaction with the aid of the zero-knowledge proof verifies that in every input there must be a revealing commitment made visible and the notes are entered correctly. Zcash uses a set of verifying and proving keys that create and check proofs apart from the spending keys.
NOTE: Zcash runs a multisignature transaction but does not encrypt data for multisignature but blur IP addresses at the same time protect against connection made with public transactions.
ZCASH CHART
The chart below represents the past to future of the coin along with current plans for Zcash and some historical release dates
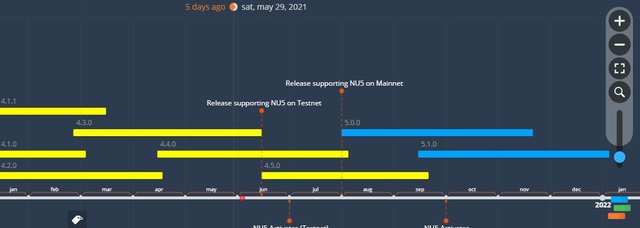 Image source
Image source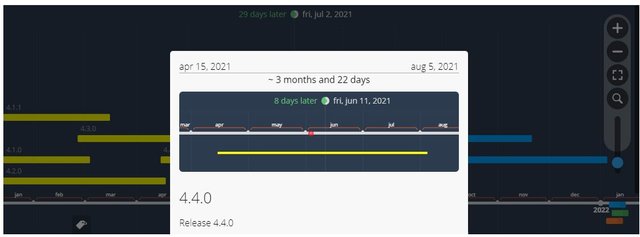 Image source
Image source
- Describe the steps in creating a wallet for the privacy coin of my choice (Screenshot required)
WALLET CREATING PROCESS FOR ZCASH
1: Open the official website of Zcash in the browser, then select get a wallet option at the down right hand side of the page.
2: Scroll down to see the list wallets available.
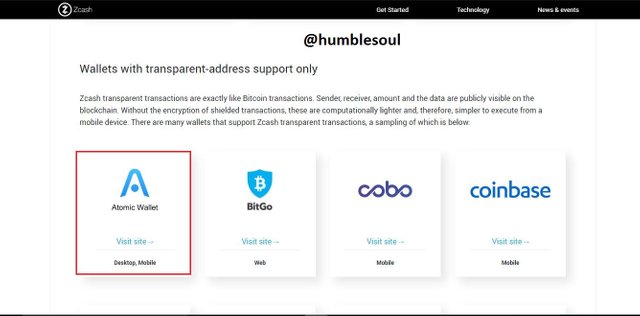
3: Choose a wallet you went to use, for me, I will use 'Atomic Wallet' (wallet with a transparent addresses support), so click on it.
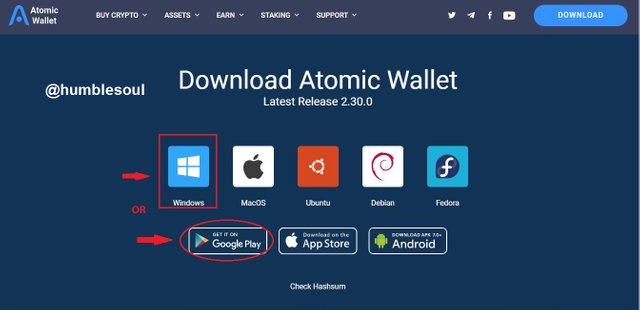
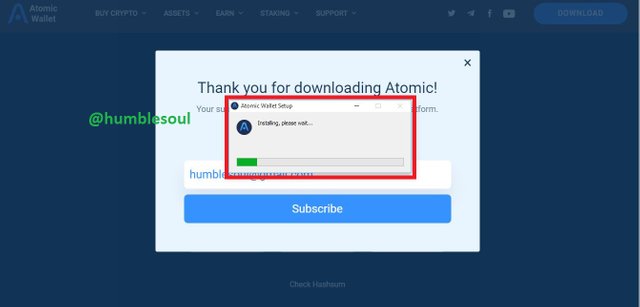
4: A new tab loaded, click on 'download' either the up or down one.
5: Choose the means of installation and click on it(am using a windows laptop)
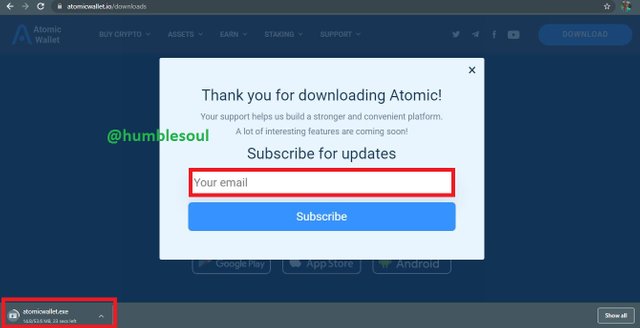
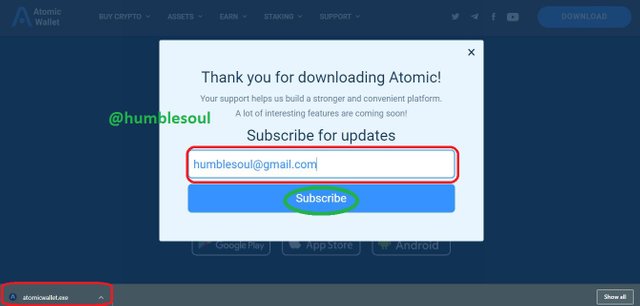
6: Fill in your email address and subscribe, wait until the instilling package is done.
7: Click on the installed package and allow to complete the instilling process
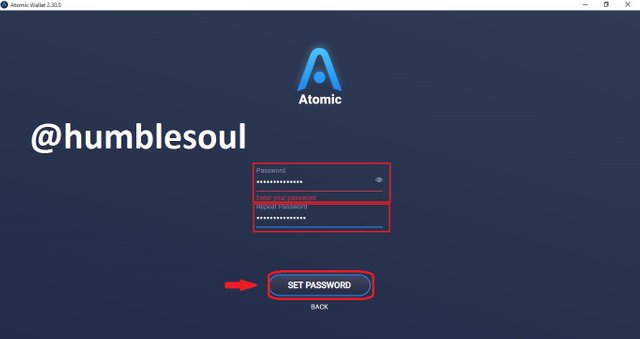
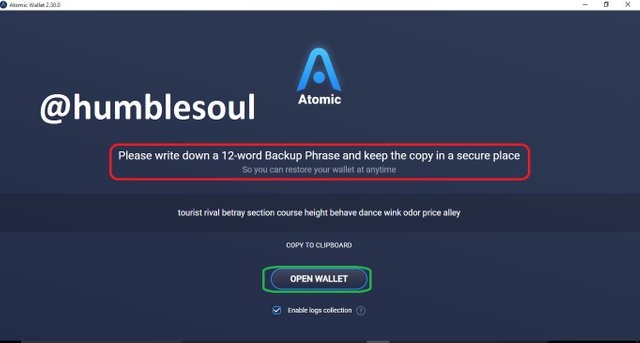
8: Click on 'new wallet' and put in your new password and click 'open wallet'
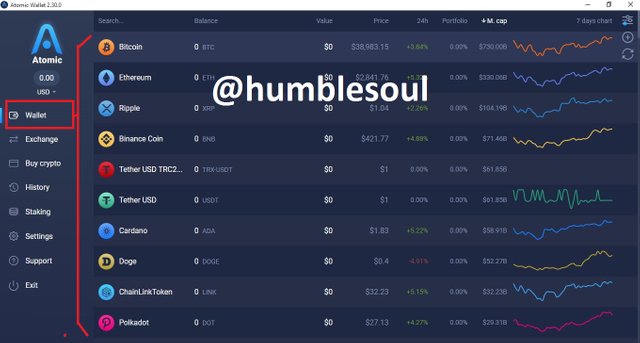
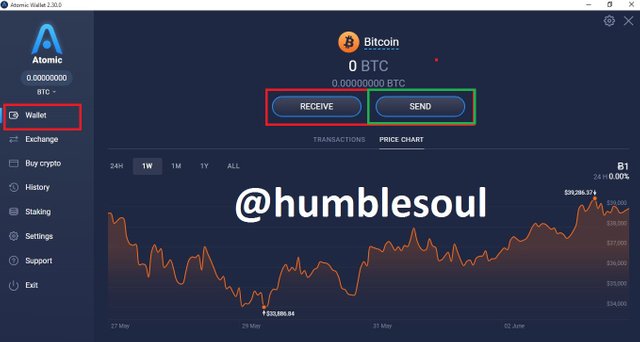
9: Click on 'wallet' to see different coins you can trade or buy, 'click on bitcoin' to buy or sell if interested.
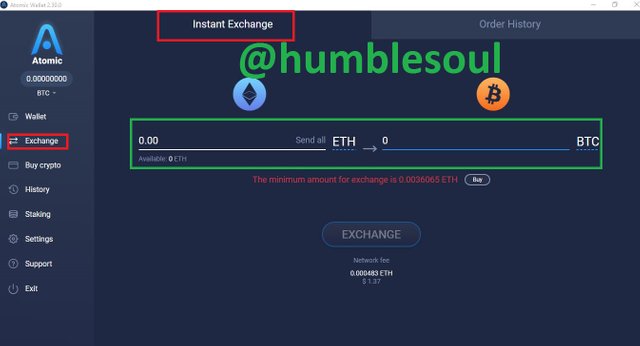
10: Click on 'exchange' if you have any coins to swap with instantly
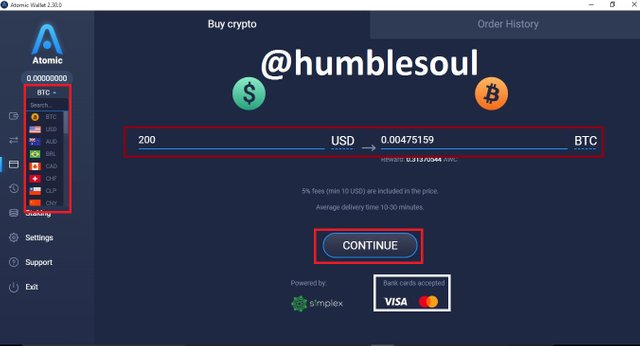
11: Click on 'buy crypto', if you want to buy any cryptocurrency available in the table, you can add your bank to it for easy transaction
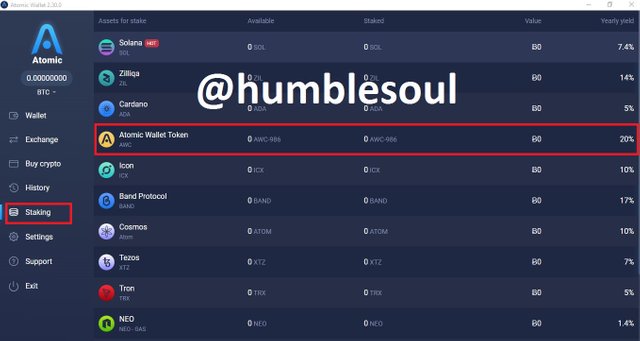
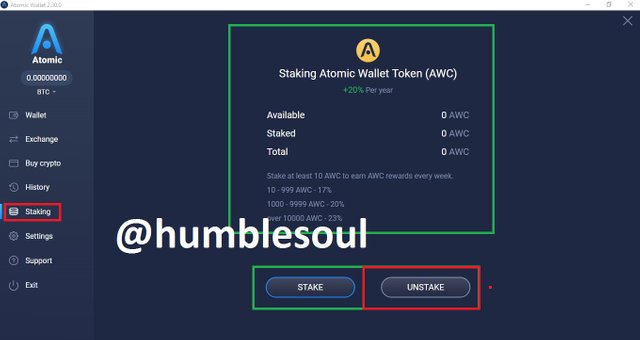
12: Click on 'Staking' and select any coins you wish to do so
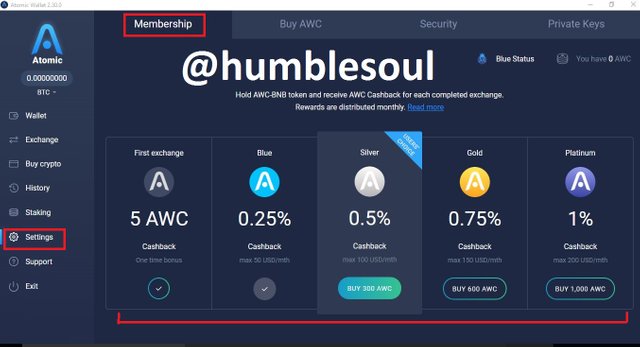
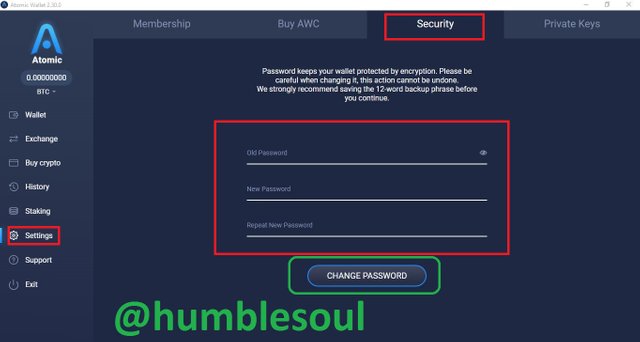
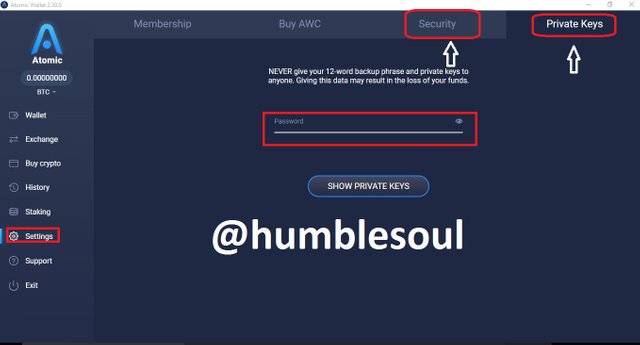
13: Click on 'setting' to run some minor setup both the membership, security and private key management
14: click on 'support' to see your atomic anonymous ID and support it where possible
15: Click on 'exist' to leave the app and log in next time.
ANOTHER WALLET UNDER ZCASH (ANDORID OR IPHONE USE ONLY)
- NIGHTHAWK WALLET
1: Search on apple or play store for the above app and install\download the app to your phone by clicking on the highlighted icons.


2: After downloading the app, open it, and run the manual setup by clicking at the spotted icons.

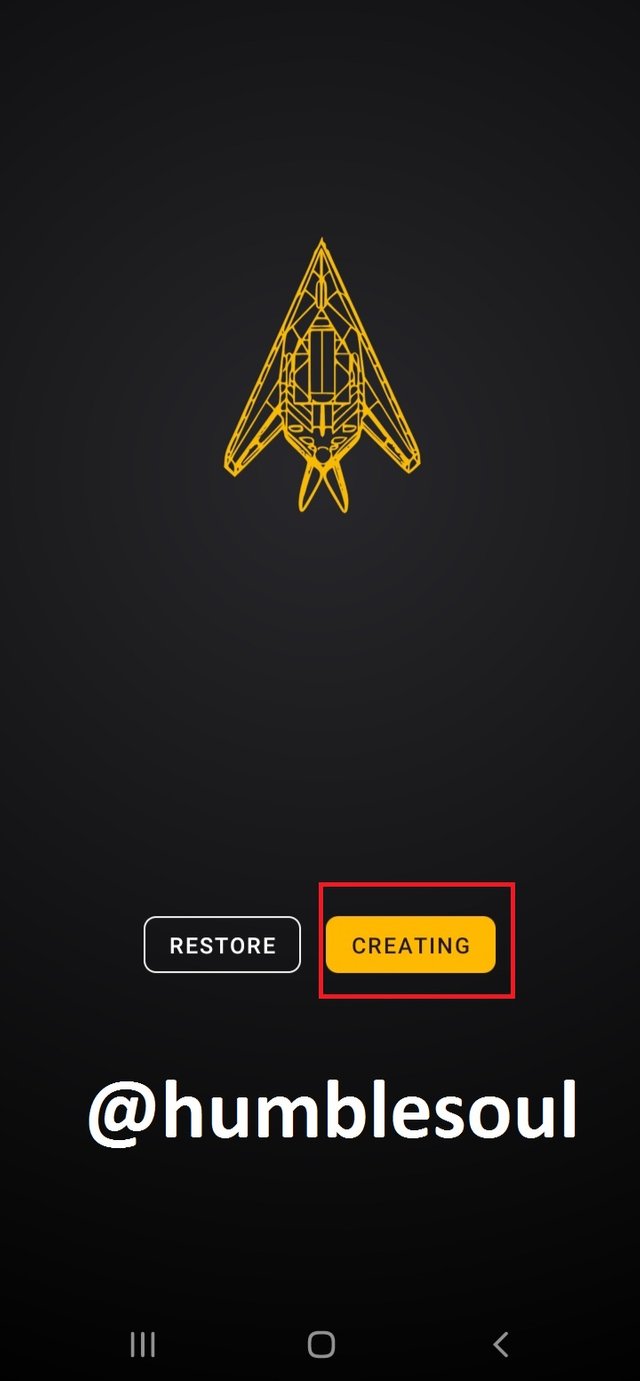
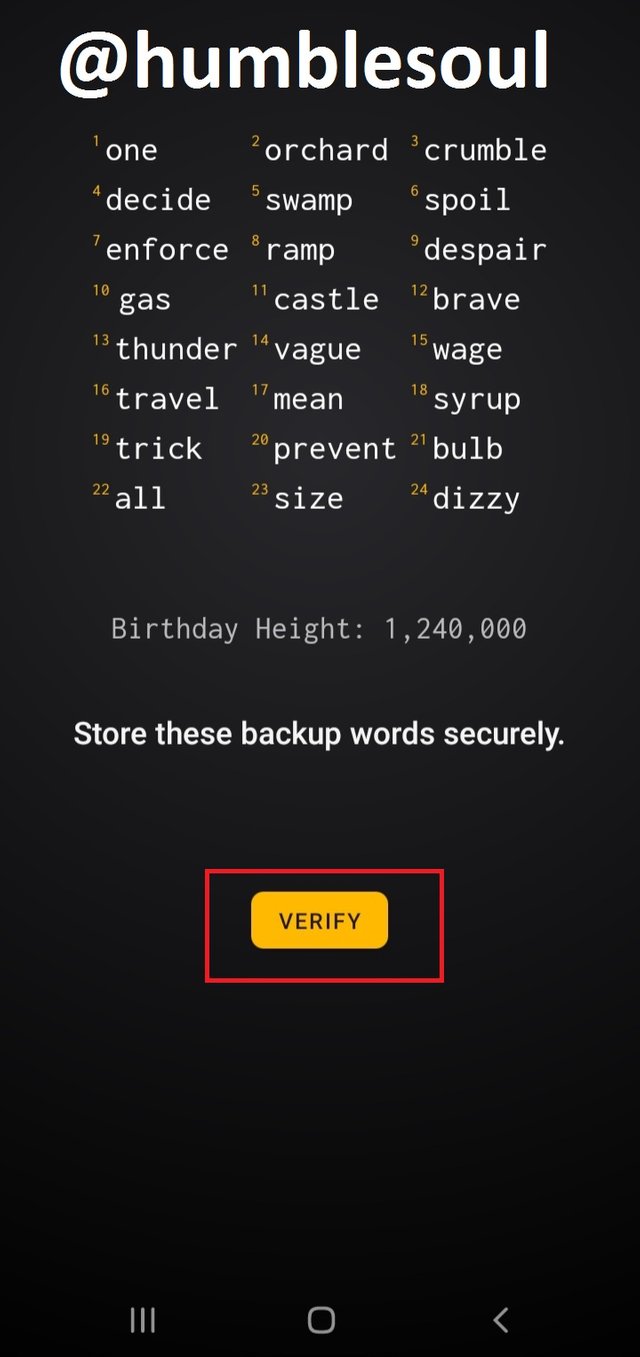
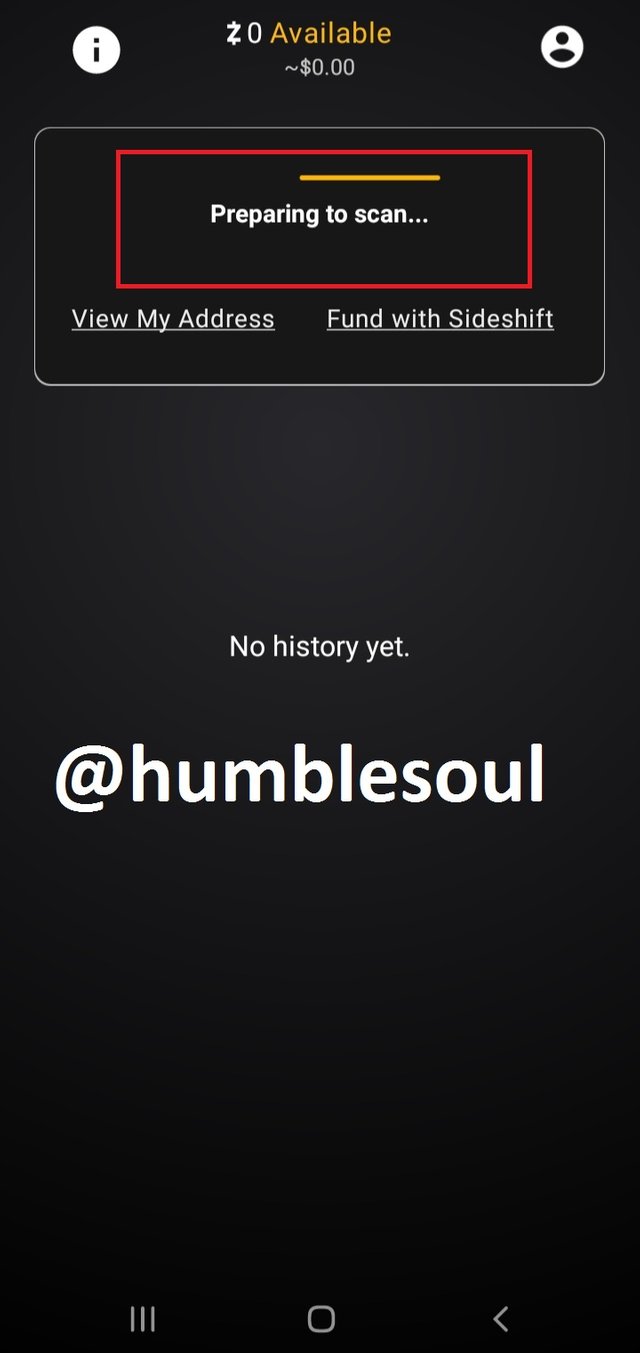
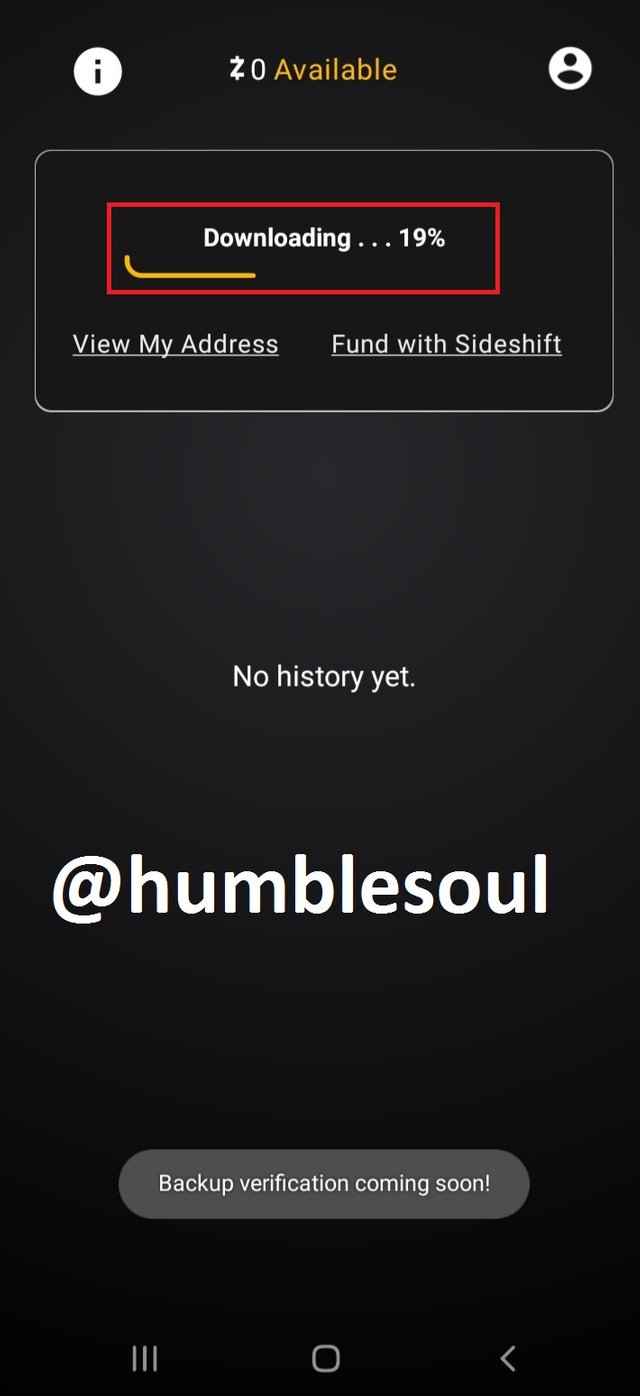
3: Click on that icon, it will provide the QR Code for your ID
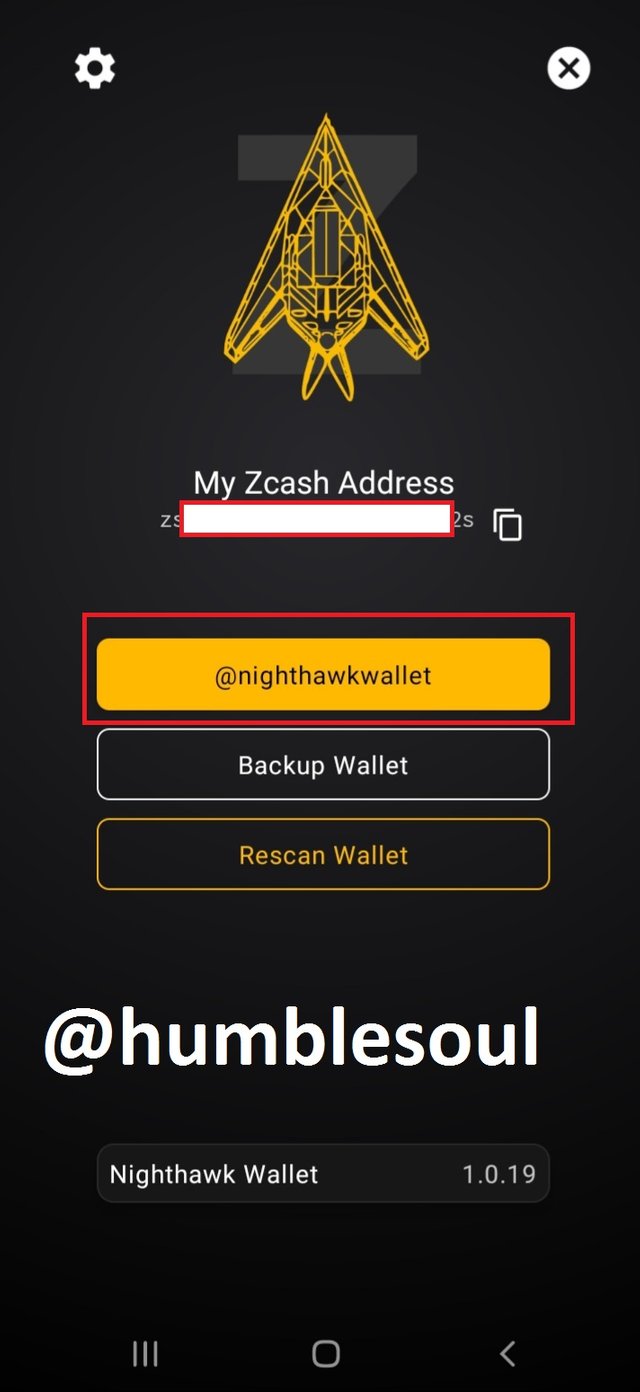
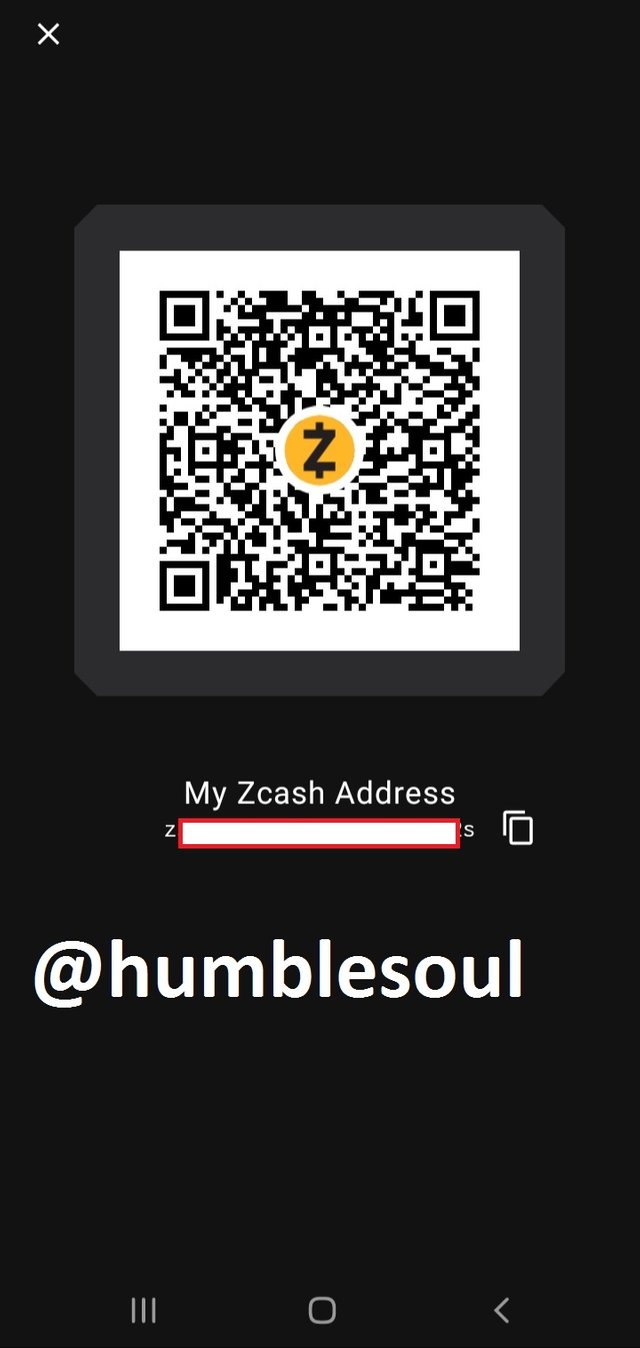
4: Yow now have an active, empty wallet by the above app.
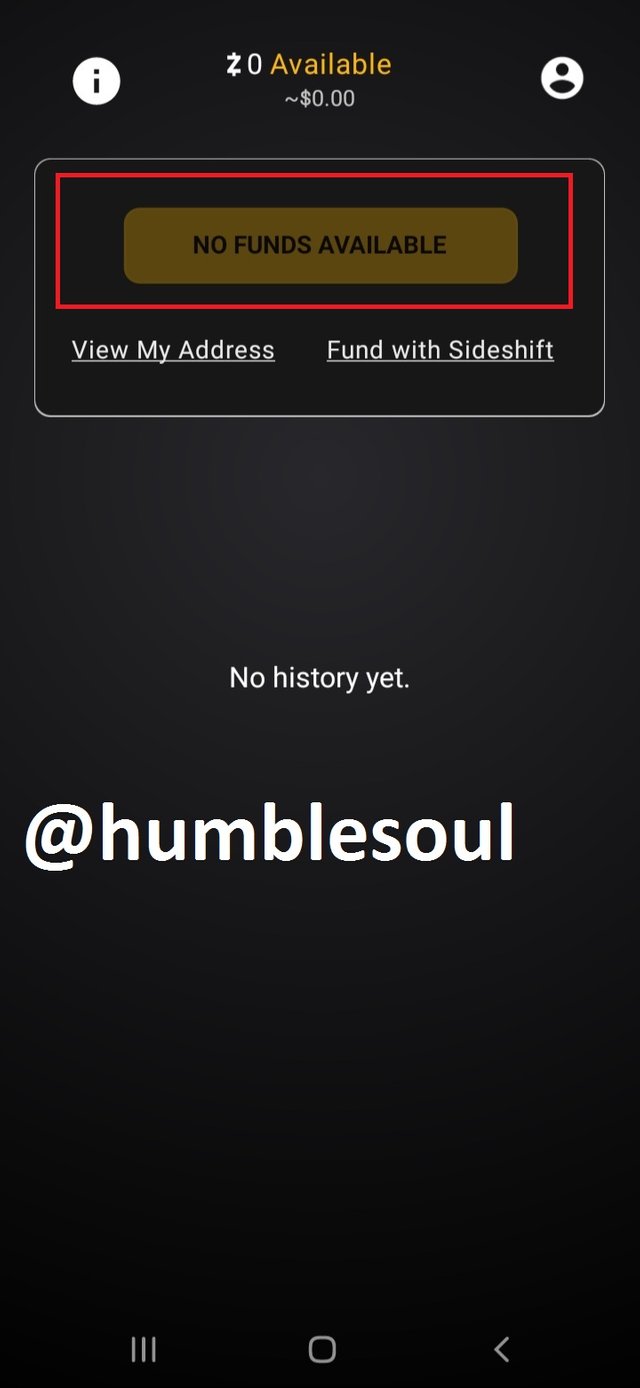

- Explain the reason I chose the privacy Coin (State the advantages and disadvantages)
ADVANTAGES
- High level of enhanced privacy features with cryptocurrency confidentially.
- Easy mining Accessibility with the use of Equihash proof-of-work system
- use a cryptographic privacy technology known as zero-knowledge proofs (ZKPs)
- use of shielded transaction which makes it highly secured and keep off from hackers.
DISADVANTAGES
- In a transaction, series of calculations is needed to be completed.
- the privacy tool used (Zk-SNARK) can be applied by others cryptocurrency because nothing special is found in it.
- the business is polarized by one company (Electric Coin Company)
- free-will of creating a public key

CONCLUSION
As world population increases along with inventors and traders flooding into the data based and cryptocurrency world, Zcash with its tool ‘zero-knowledge proofs’ is the best step towards protecting traders along with the commerce activity from public attention or an outsider prying into one’s data or transaction, Zcash can do it best to keep, as well as protects and enhance anonymity of data through the different shielded or transparent addresses, transaction or wallet.
Interestingly, Zcash is coded in TeX, C++, Rust, Kotlin and Python for more programmed and enhanced usage. Zcash is a fork of the bitcoin block chain previously known as the Zero coin protocol but later transformed to the Zero cash system, Zcash. Coin-Market Cap ranking now is #56, the live market cap of $1,847,279,186 USD. Has in possession circulating supply of 11,915,213 ZEC coins and a maximum supply of 21,000,000 ZEC coins, according to report in the last 24 hours, but truly, Zcash is the best to trade or invest in.





Hi @humblesoul, Thank you for taking my class in the 8th week.
You didn't put the source of the image you used correctly, I can't verify the source you created. Please review the rules and guidelines.
Am very sorry sir, @levycore, it was an oversight, I have corrected and inserted the link in accordance with the pictures.
@levycore, Please pardon my negligence.