Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u | Let's Open the Cryptography
Good day beautiful Steemians, welcome to my Steemit crypto academy season 3 week 8 homework for professor @stream4u on: Let's Open The CryptoGraphy.
Privacy is a key concern in this century, and with increasingly more messages being passed using the internet, it has become paramount to both private, corporate, and government entities to send messages securely over it.

"1. Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms"
Cryptography is the science that seeks to quench this thirst, creating a secure link between the originator of a message and its recipient and restricting any third parties from viewing its contents. This it does by the use of algorithms that transform the data making it hard to decipher. More interestingly, data encryption and decryption using cryptography aside from ensuring that there is no modification of the data between sender and receiver, also ensures the sender of the data cannot disclaim the data once sent and both the sender and recipient of the data can verify both each other’s identification as well as the source and destination of the data.
Cryptography also seeks to protect static data such as those stored in organizational and government websites, devices, and databases from unauthorized third parties.
Basic applications of cryptography will be examplified by Arin who is part of the IT personnel in her organization and helps encrypt email messages and other sensitive documents shared within the organization. Another is Garin who encrypts the hard drives of government-issued devices to security personnel and security databases to ensure the privacy of the data. Financial systems such as the bitcoin blockchain system also use cryptography to encrypt, decrypt and secure data sent over it between or among users.

"5. Explain what is Symmetric and Asymmetric cryptography?"
Cryptographic encryption can be largely divided into single key or symmetric key encryption and Public key or asymmetric key encryption. The basic differences between the above-mentioned types of encryption are the number of keys produced and parties to which knowledge of the key/keys are available. While the former generates only a single private key used to both encrypt and decrypt the data and known to both sender and receiver, the latter generates a pair of keys; one key (the public key) used by the sender to encrypt the message or data and another (the private key) known only to the originator of the message/data for decrypting it.
Symmetric key encryption is mostly generated using the Advanced Encryption Standard (AES) which is mandated by the United States government and is a replacement of the Data Encryption Standard (DES). It uses either a fixed 128 bit, 192 bit or 256-bit key length to encrypt data. Asymmetric key encryption on the other hand is usually generated using the Rivest Shamir-Adleman (RSA) algorithm, Elliptic curve digital signature algorithm used by the bitcoin blockchain, and Digital Signature Algorithm (DSA). Both the symmetric and asymmetric encryption methods should be fully understood by the activities of Binta and Larry in the following paragraphs.
Binta intends to send a mail message to Lara containing very sensitive content. She goes ahead to generate a single secret key (symmetric key) with which she uses to encrypt the plain text, effectively converting it into computer language. Lara, the recipient of the message, then inputs this key and receives the message intended for her in a corresponding decryption process.
For asymmetric keys, Larry intends to receive 3BTC over the lighting network on the bitcoin blockchain from Manny but doesn’t have a direct link to Manny. He however has links through Danny and Gary. He then generates a pair of keys (asymmetric key), gives the encryption keys to Manny, who in turn gives it to Danny and Gary, while he keeps the decryption key (secret key). When the encrypted message passes through the channel and comes back to him, he uses his decryption private key to unlock the message, retrieve his funds, and also other payment funds to the other nodes (Danny and Gary) in the network.
From the foregoing, we’d have noticed that there are two basic keys with which blockchains and their users protect their assets from malicious third parties- The private and the public key.

"2. Explain the Public Key Cryptography."
Public keys being part of the asymmetric keys are cryptographic alphanumeric numbers and letters that let blockchain users receive coins and tokens into their accounts. It is usually a long alphanumeric character string generated by a user when a transaction is first initiated. The public keys can be used to generate a public address by hashing it. Public addresses can be likened to conventional bank account numbers so that coins and tokens can be sent from one public address to another.

"3. Explain the Private Key CryptoGraphy."
Private keys on the other hand are cryptographic codes that are known only to the users, enabling them to access their coins and tokens, and also serves as digital identification for all blockchain authorizations. It usually also comprises alphanumeric characters and it ensures the security of the assets of the user. It can also be likened to the PIN in conventional banking transactions. It is interesting to note that the public key is formed from the private key and the reverse of this process is almost impossible, making assets unavailable to hackers despite the public key being out in the open.

"4. Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?"
Just like we store our PINs in safe places, Private keys can be stored in digital wallets. When transactions are done, the wallet generates a digital signature which can only be signed by using the private key. These signatures serve as digital footprints ensuring that transactions cannot be changed after they are broadcasted to the network.
So, digital signatures are an authentication that we approve of a transaction that may involve our assets, personal messages, etc by using our private keys to hash them cryptographically.
Signing of Message/transaction
Like we said earlier, signing a transaction or message is the use of our private keys to harsh the message, therefore, producing a unique digital signature for that message.
This serves as strong evidence of authentication and confirmation that a certain cryptographic message is from a certain sender.

"6. How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets."
Losing a private key is a nightmare that spells denial of access to all assets. It is therefore advisable to safely store private keys. One common way is using offline hardware wallets such as USB devices, offline software wallets, and also paper wallets. This way, transactions are moved offline to be signed before being taken back online to be broadcasted. They are also referred to as cold wallets. On the other hand, wallets which store keys on devices that are connected to the internet are called hot wallets. An example of this is the coinbase wallet.
Elaborating more on wallets, the types of crypto wallets available are:
• Hot Wallets
• Cold Wallets
Hot Wallet
A hot wallet is a crypto wallet connected to the internet. This means accessing it one needs to be connected to the internet.
With hot wallets, one’s private and public keys are saved on the hot wallet’s companies server so this may seem as a security concern say the company’s server gets hacked.
But on the other hand, the hot wallet makes users crypto very accessible and easy to transact with.
Examples of hot wallets are the coinbase wallet, Binance wallet, Steemit wallet, Roku wallet, etc.
Cold Wallet:
Cold wallets usually considered the safest wallet, are crypto wallets that are not connected to the internet. This means they range from offline software wallets, hardware wallets and even scribbling down your private and public keys on a piece of paper (paper wallet).
This way users are more certain they have total control of their assets and also have control over their security.
Examples of cold wallets are: Trezor USB wallet, coinkite coldcard wallet, Nano ledger software and hardware wallet.

"7. What is the Merkle trees and What its importance in blockchain?"
Now let’s look at verifying transactions while saving time and storage using Merkle roots.
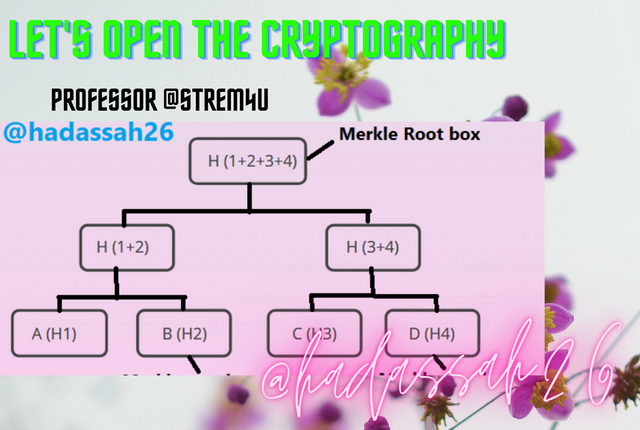
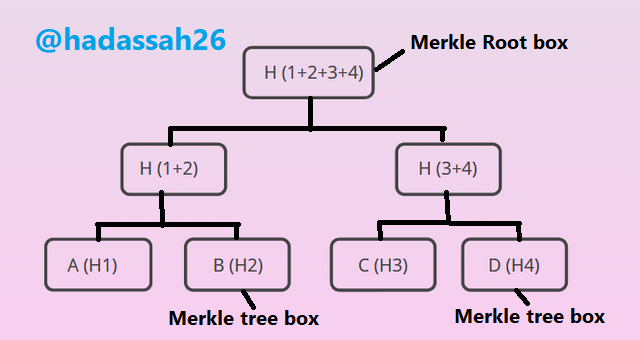
A Merkle root is the cumulative hash of every transaction hash contained in a block of a blockchain. It is usually at the top of the Merkle tree and is derived by the cumulative hashes of the leaf nodes, which are at the base of the tree, and the non-leaf nodes, which are all hashes between the leaves and the root.
Merkle trees are used to ensure efficient and secure verification and transfer of data between nodes or peers in a blockchain. Using Merkle roots also saves time and storage space. This will be shown by Meghan who needs to verify data from a non-trusted source.
The Merkle tree works in blocks with a bottom to top approach, such that multiple transactions are stored in leaf boxes and hashed through hashing pair until there is one box left which is the Merkle root. This way there is an ease in getting information about a specific transaction through a single block.
Meghan knows that jumping into the net to download a program that ends up being malicious or damaged is a waste of time and storage space. What she smartly does is download the root hash from the main developers of the program, which she uses to compare other programs she gets from the non-trusted sources from which she has access to download programs. That saves her from downloading malware or getting defective programs and the time to re-download the right program for her needs.
This also applies to blockchains as we will see from Richard who wants to confirm his transaction in a block. Richard knows that going through all the hashes in the block just to verify his transaction is both time and space inefficient. He, therefore, requests Merkle proof which will show that his transaction is contained in that particular block. If the Merkle roots correspond to the comparison, then it's proof that his transaction is contained in that block.

"8. Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper"
As discussed earlier, keys are the privacy to one's crypto wallet and assets. In the asymmetric encryption system, we have the public and private keys.
The public keys are pegged to the private keys and can be shared with the sender, while the private keys are unique to every individual. This means that while the public keys are linked to the private keys, the private keys are linked to the individual. this brings about anonymity in the crypto space. Below we can see that on changing the private keys a new public key is generated.
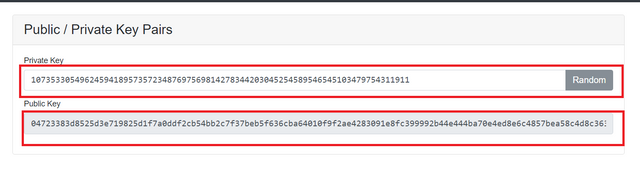
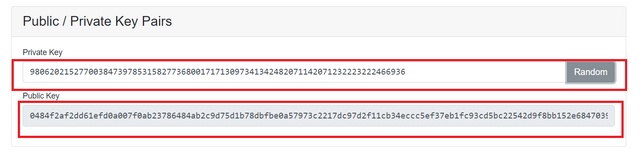
Here we see the Public key changes as the private key is changed.
Signatures or digital signatures are like the normal manual signatures or say a stamp that can be dynamically hashed using one's private keys. They show that a certain message is authentic and from a specific sender. With the idea of cryptography and hashing messages producing digital signatures, one can constantly harsh his messages producing different signatures but all linked to a specific private key. A simulation of digital signature is shown below:
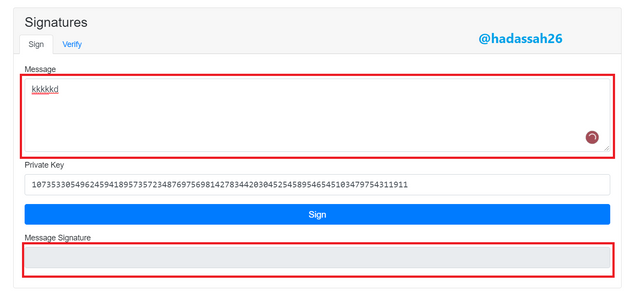
From the above screenshot, we see that the message has not been hashed, so it has no "Message Signature"
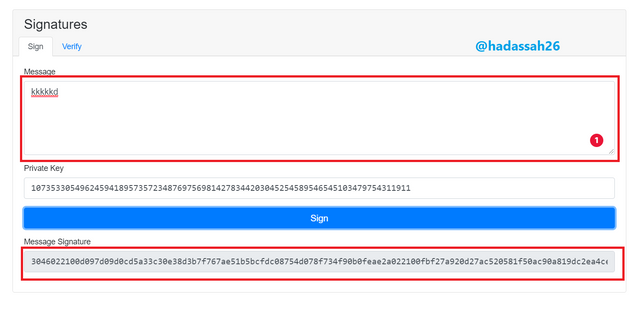
With the message hashed, we can now confirm a digital signature of alphanumeric keys.
Verifying Signatures
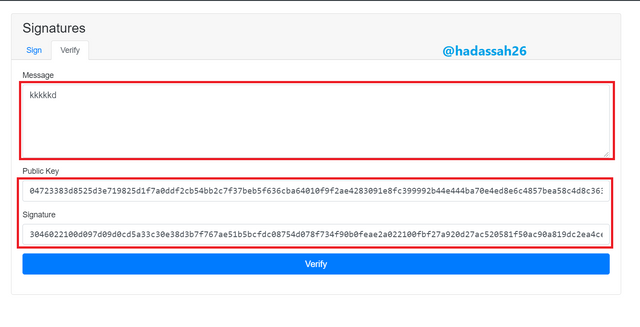
Clicking on the verify tab, we see that we have to message, public key, and the "message signature"
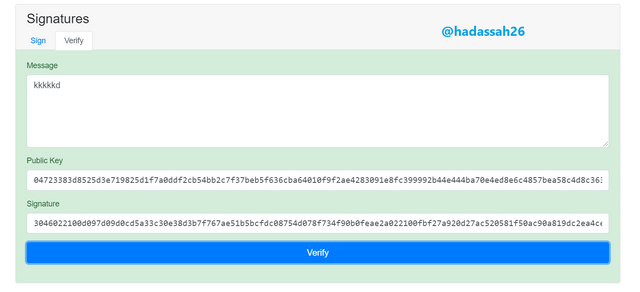
Clicking on "Verify" we can see the blockchain has been able to verify and confirm that this message and message signature is for the public key.
Here just like the signatures, every transaction can now be signed and a digital signature produced for it. This shows that the transaction is authentic to that private key and can now be harshed by the network.
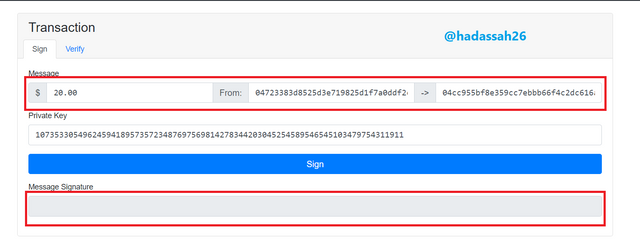
Here we see the transaction has not been signed so there is no "message signature" for it.
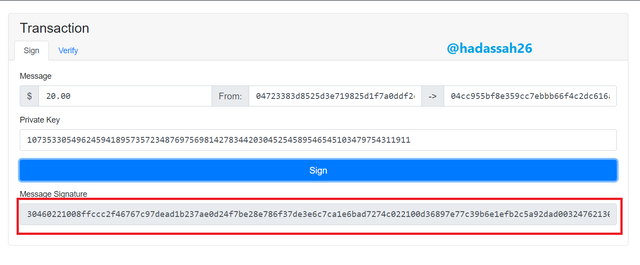
With the transaction signed, it has gained a message signature.
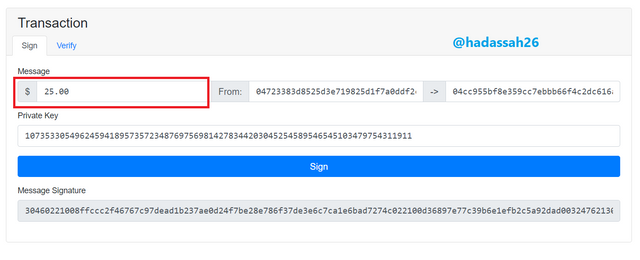
Now say I change a part of the transaction, watch what will then happen in the verify tab below.
Verifying the Transaction
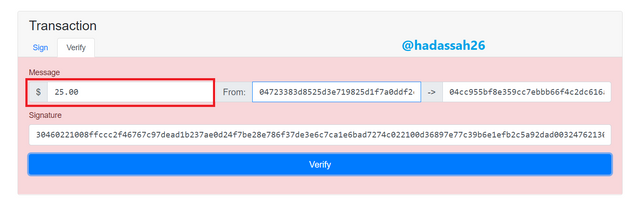
Verifying the transaction shows an error because the message had been tampered with after signing.
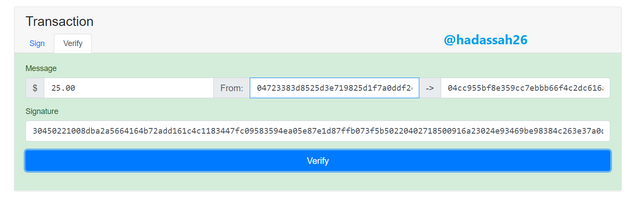
I have then gone back to resign the message before coming back to verify it. As we can see it is now green meaning it is "Good to go"
With the Block hashed with a specific private key, the network can now verify the transaction and confirming that "Message signature" if it corresponds to the private key and transaction. If it does, then the transaction it verified, else it remains unverified.
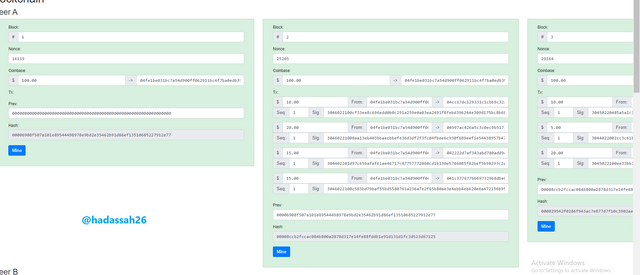
Blockchain as a cryptographic ledger, verifies each block and creates a hash which can be likened to a digital signature, On completion of each block and its hash, a new block is started but included in this block is the previous hash. This way each block is linked to the previous block. So when a transaction in the previous block is changed, it reflects on the succeeding blocks as they become unverified and will need to be re-hashed before they are now completed. A simulation is shown below:
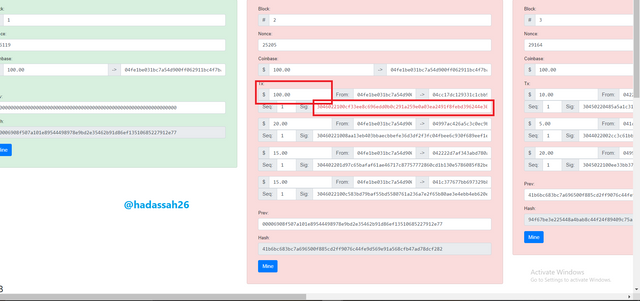
Now say I want to maliciously play the system, trying to go back to a previous block to edit my transaction on, changing it from $10 from coinbase to say $100, and then remaining the block,
Even after remaining, the transaction signature still remains red, because it doesn't match the private key.
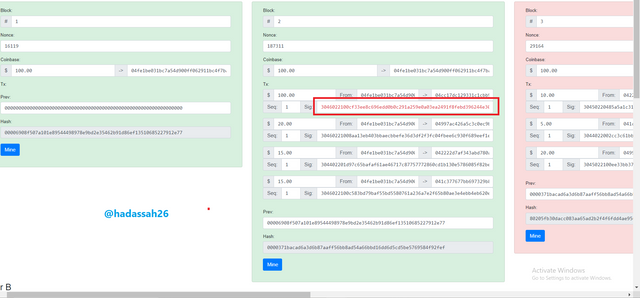
We see I will then need to remine other blocks which may not be in my power, and more with a red-flagged signature on the edited block.
This method crosscheck for tampareing with the blockchain network and securing it.

"9. Conclusion. (The overall understanding of CryptoGraphy)"
Cryptography is the science of private messaging and keeping track of every member of the communication during communication. the private and public asymmetric keys make it's messaging more anonymous and secure.
Private keys can be stored in crypto wallets from hot wallets to cold wallets such as your piece of paper.
The importance of cryptography to secure transactions cannot be overemphasized as can be seen above. Not only are transactions secure by using keys and wallets, but they can also be confirmed efficiently using Mekle roots and trees.
Thanks.
CC @Stream4u