Crypto Academy Season 3 Beginners' Course- Homework Post For Task 2: Blockchain , Decentralization, Block Explorer by @giftye for @yousafharoonkhan
QUESTION
WRITE THE DEFINITION OF BLOCKCHAIN. AND HOW OUR DATA ON BLOCKCHAIN IS PROTECTED FROM HACKERS . AND WRITE DETAILS ABOUT DATA,HASH AND PREVIOUS HASH TAGAND EXPLAIN THROUGH SCREENSHOT.
DEFINITION OF BLOCKCHAIN
Blockchain in simple words means a system of storing or recording information or data in a manner that makes it very hard or quite impossible to change.
It can be easily referred to as a digital ledger of transactions reproduced and passed across the whole network of computer systems in the blockchain .
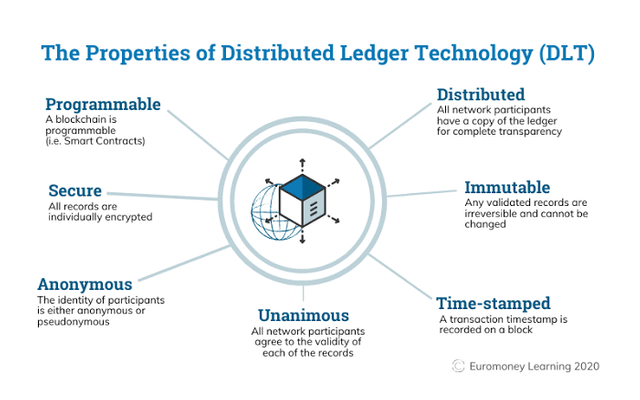
The blockchain functions as a distributor ledger,which makes the data stored in it to be well secured and protected.
Blockchains essentially function as a decentralized system which shields it from a middle man's interference,any information can be stored and viewed by many blockchain users(nodes)
Blockchain is a type of DLT in which transactions are recorded with an immutable cryptographic signature called a hash. source
HOW OUR DATA ON BLOCKCHAIN IS PROTECTED FROM HACKERS
The ability of blockchain to be immutable or impossible to change is what makes it unhackable.
From the diagrammatic illustration above,it's obvious that if a block in a chain was changed it would be noticed that it has been tampered with,so if hackers want to get into a blockchain system to corrupt it,then they would have to change the blocks in that chain one after the other. So imaging if the blockchain to be hacked contains a million blocks
Let me give a mathematical illustration on the matter using Bitcoin as an example
144 blocks are mined per day on average,and each block contains 6.25 Bitcoins. Taking a statistics of how many blocks have been created so far from 2009-2021 we have:
144×365=52,560 per year
2009 to 2021= 12years
Total amount of blocks for 12years(12×52,560)= 630,720 blocks
This is too frustrating for hackers to try.
OTHER REASONS WHY BLOCKCHAINS ARE PROTECTED FROM HACKERS
IT IS DECENTRALIZED : Blockchain is formed by many contributing technological factors that works together towards a singular goal. So mechanisms like proof-of-work(PoW) and proof-of-stake(PoS) protects the network by lessening cyber -attacks from hackers
IT USES HASHING ALGORITHM : This hashing algorithm is what determines the network's details. A set of data from the previous block is contained in the new block, therefore,even if the hash is tampered with,the tampered block won't be in synchronization with the other blocks because it will have a different hash output,which will trigger the system to reject it.
Another factor to consider is that,for a hacker to tamper with the transaction's hash,they need to have a 51% control of the blockchain's power at the least. So a blockchain that has been in existence for quite some time would definitely have a large amount of users which increases it's hash power , making it almost impossible to suffer a 51% attack.
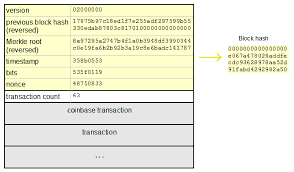
DATA
Data is first and foremost an information desk. You can find data in each block of a blockchain,it contains all the information one would need as pertaining transactions in that block; informations of transactions from both sender and recipient are stored in the block in form of data,and these informations cannot be manipulated or modified.
HASH
Hash is contained by all blocks. Each block has a hash that is unique to it. The hash code is able to convert an input data that might be lengthy into a sizable encrypted output,which is of the same size with other hash codes.
The hash code of a block enables us verify and ascertain whether the information in that block is correct or not. Since the format of the blocks in the blockchain are decentralized, editing or making changes is impossible.
PREVIOUS HASHTAG
The previous hash tag is all about the hash code of the previous block in a blockchain. When a block gets filled up in a blockchain another block is created,so in order for this new block to also contain information from that old block,the previous hash tag(code) needs to be entered. In that way the information now exist in both blocks.
The previous hash tag connects the previous and new block which brings about a decentralized blockchain.
CONCLUSION
The decentralized strategy adopted by blockchain has made it security tight,which means users can relax and carry on with their transactions.
Thanks professor @yousafharoonkhan for this wonderful opportunity,hope I meet up to your standards.
.jpeg)
Hello @giftye , I’m glad you participated in the 2nd Task of the Beginner’s class at the Steemit Crypto Academy. Your grades in this task are as follows:
Recommendation / Feedback:
Thank you for submitting your homework task 2. We hope to see the rest of your submissions.
Thank you @reminiscence01,I will put in more effort in my next posts