Crypto Academy | Season 3 Week 2 - Homework Post for Prof @pelon53 | Hash and Cryptography
Hello Prof. @pelon53. I really enjoyed your wonderful lecture, here is my homework post
Hash is a function in cryptography capable of changing input data into compressed characters that comprise both numbers and alphabets in such a unique way that it cannot be duplicated.
The purpose of hash is to serve as a security measure to protect the integrity of data. The output data of a hash is of a fixed length irrespective of the length of the input data. The computation of a hash function is one-way and cannot be reversed.
The hash function is used to create wallet addresses and confirm the integrity of data in Blockchain technology. It can convert large transaction data into minimum-sized data which is very helpful for Blockchain as it can be used by blockchain to compress large transaction data into a hash function.
Hash has the following basic properties;
• Collision resistance
• Preimage resistance
• second preimage resistance
Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Resistance to collision was made to avoid any kind of collision in the generation of the hash output data. This means different inputs must not collide to generate the same output but they should generate different output data.
It is mathematically impossible for two inputs to create the same output. For instance, inputs c and d should not generate h(c) = h(d)
When it can be shown or proven that the hash produces different outputs when two different inputs are given, then the hash is collision-resistant. Technically, when a hash is collision-resistant, it should have an output of at least 160bits in length.
It is a hash feature that prevents data compressed into a hash from being discovered through reversal. However, this can be done but with a very small probability, there are times that attackers can predict the inputted data by observing the output data. Resistance to preimage is a one-way feature used for functions with the same size input and output and it cannot be reversed. It is slightly impossible to map out the imputed data that was used to generate the hash. For instance, it will be difficult and almost impossible to find the input value (p) from a hash function (r) that produced a hash with value j.
The output of a function that is resistant to preimage should be 90bits at a minimum.
Use tronscan and etherscan to verify the last block's hash and the hash of that transaction. A screenshot is required for checking.
Go to https://tronscan.org/#/
Select blockchain from the top menu
Select Blocks from the options
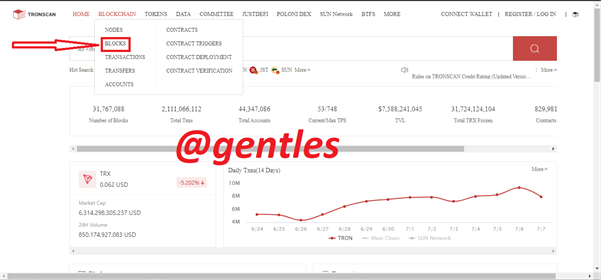
A lot of Tron blocks will be seen on this page and this is as a result of ongoing transactions. The current last block height is 31764273.
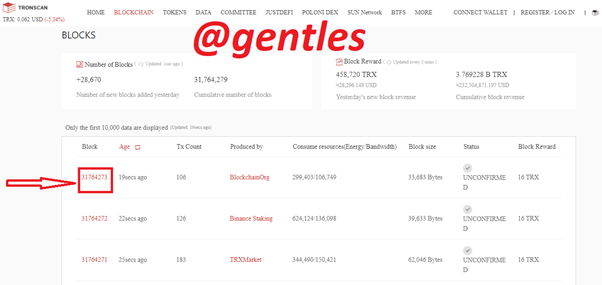
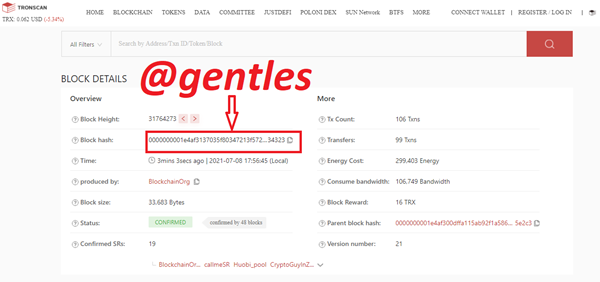
Click on the block to show the block details. From the info below, the block height as stated earlier is 31764273 with a block hash of 0000000001e4af3137035f80347213f5722308cc1b996499177d8293d2834323
Here is the link https://tronscan.org/#/block/31764273
To verify the hash, find and select transactions.
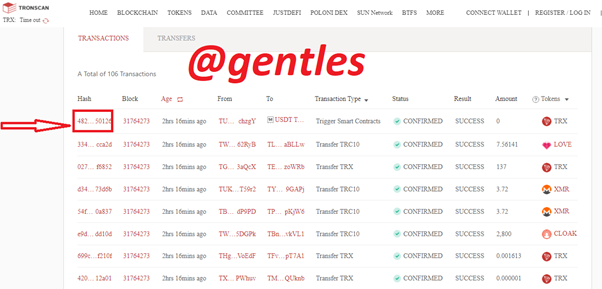
Click on the Hash to show the transaction details of the Hash.
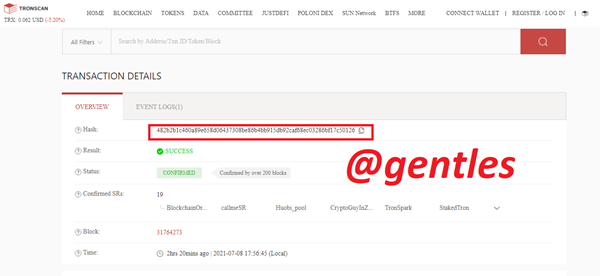
• The Hash of the transaction was 482b2b1c460a89e658d06437308be86b4bb915db92caf68ec03286bf17c50126
Here is the link to the hash https://tronscan.org/#/transaction/482b2b1c460a89e658d06437308be86b4bb915db92caf68ec03286bf17c50126
Using Etherscan to verify Block
First, go to www.etherscan.io and select Blockchain from the top menu.
Click on View Blocks from the list
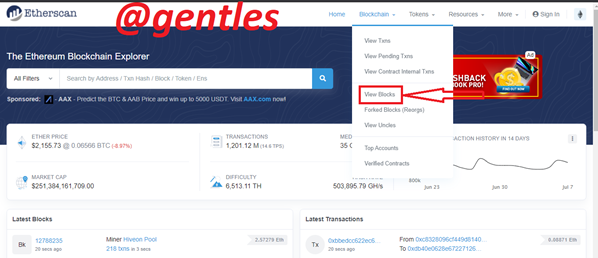
The latest block shown here is 12788241. Select it to show the block details.
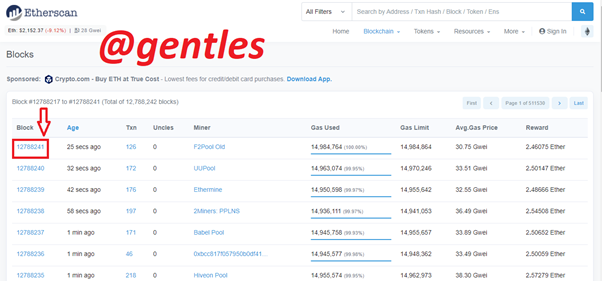
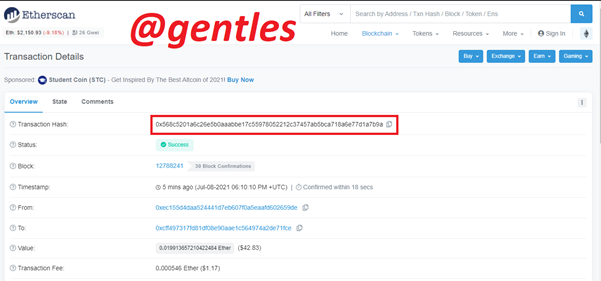
The transaction hash shown here is 0x568c5201a6c26e5b0aaabbe17c55978052212c37457ab5bca718a6e77d1a7b9a
The link for the transaction is https://etherscan.io/tx/0x568c5201a6c26e5b0aaabbe17c55978052212c37457ab5bca718a6e77d1a7b9a
Generate the hash using SHA-256, from the word CryptoAcademy and cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
To generate the hash for the words CryptoAcademy and cryptoacademy using SHA-256, I will be using https://passwordsgenerator.net/sha256-hash-generator/ platform.
• Visit the page
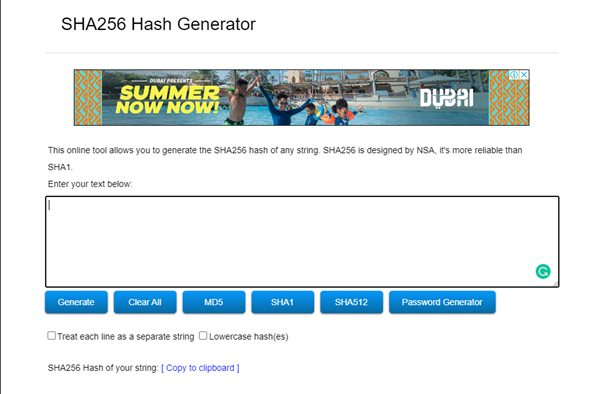
• Enter the word (CryptoAcademy) into the box to automatically generate the hash as shown below.
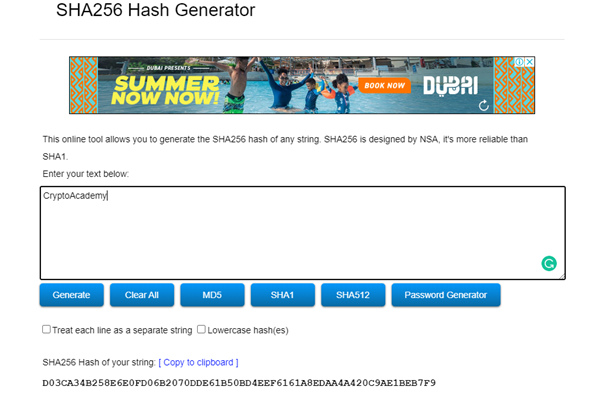
The hash generated was D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
• Type in the second word (cryptoacademy) into the box the generate the hash.
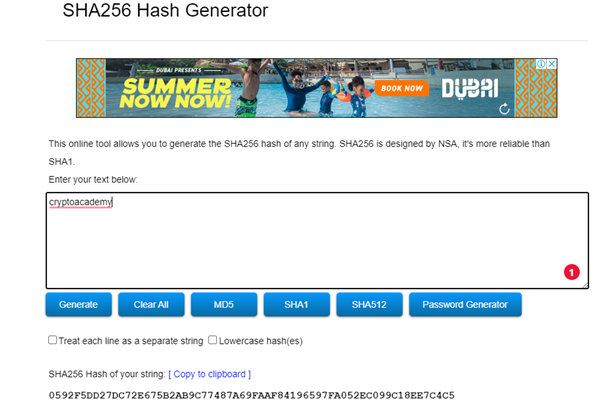
The hash generated was 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
CryptoAcademy and cryptoacademy are of different contents therefore the system gave two hash outputs. This is because SHA-256 is resistant to collision. With this feature, it is almost impossible for the two hash outputs to collide.
The two inputs are similar but are not the same and the hash function does not allow two different inputs to produce the same hash output because of the resistance collision function. This is the reason why CryptoAcademy and cryptoacademy do not generate the same hash function.
In your own words explain the difference between hash and cryptography.
• It is used to validate the receiver and sender by authenticating their identity and location
• Cryptography is used to provide security for data
• Data is encrypted in cryptography to make sure of its confidentiality
• It makes sure data is not manipulated when being transferred or stored
• All cryptography is hash
• The same input will at all times produce the same hash output
• It is irreversible. The hash output cannot be reversed to reveal the input that generated the output
• Any slight change made to the input will cause a great change in the output. This is called the avalanche effect.
• No two different inputs can produce the same output
• It helps in the identification of data tampering when it is signed
• Hash functions are not cryptography
| Cryptography | Hash |
|---|---|
| Keys are sometimes required in cryptography | private keys are not needed in hash |
| Cryptography data are retrievable by a key | hash data are not retrievable |
| There are differences in the length of cryptography codes | The code length of hash are fixed |
| All cryptography are hash functions | hash is not cryptography |
This was a great lecture that enabled me to learn a lot about hash and cryptography. I learned that Hash functions are unrepeatable and this does not allow different data to produce the same output.
In the first question, I explained what resistance to collision was. The explanation was that it is a function that aids hash to produce unique outputs. Preimage was also explained as a feature that does not allow output data to be reversed.
In question two, I demonstrated how to verify the hash of a block and the hash of a transaction using Etherscan and Tronscan.
In the third question, I generated a hash from CryptoAcademy and cryptoacademy using SHA-256 and showed why different hash outputs were produced.
Finally, I wrote about the difference between Hash and cryptography. One basic difference was that all cryptography is hash whiles all hash is not cryptography.
Thank you
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Buen trabajo, felicitaciones.
Recomendaciones:
Debes colocar el nombre de usuario a cada capture de pantalla.
Cada respuesta debe ser explicada de forma clara y sencilla para que sea entendible por cualquier persona.
Calificación: 9.3