Crypto Academy / Season 3 / Week 2 - Homework Post for @pelon53 | Hash and Cryptography
Introduction
It's my pleasure to attend the academy for another session this week, and this time around, I've attended the lecture presented by professor @pelon53 which was centered on the topic Hash and Cryptography. The lecture was an awesome one and I will be using this piece of article to attend the task given by the professor.
Overview of Hash and Cryptography
Hash functions in the blockchain technology is used for the storage of information on the blockchain, as such, Hash is the combination of alphanumeric characters that stores information about a transaction on the blockchain. The information stored includes, the sender and receiver's address, the type of transaction, the amount of asset involved in the transaction, the time of transaction and so on. This has helped to contain large volume of information in just a few combination of alphabets and numbers which enhance quick and efficient record of transaction on the blockchain.
Speaking of Cryptography, it is the technology utilized in the blockchain to secure users information such that third parties
can't alter them, although, it's visible to sender/receiver but there is restriction of who can actually access it. A typical example is the case of Public and Private keys, as the name sounds, public keys can be shared with anyone for the purpose of deposit and the public can look up to your account and see the amount of crypto asset you are holding in your wallet but can't access it. And the private keys are the real deal that secure the account of a user, as they only can access their individual account with the private keys and alter the wallet at will, that's the art of cryptography. Let's look more into task.
1. Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Resistance to Collision
Collision in this context refers to two different inputs coming out with identical output having the same hash, as such, this can be so misleading. Resistance to collision is characterized with hash functions to make sure the hash output from several transactions carried out on the blockchain becomes hard to appear more than once. It is recorded that the earliest hash function algorithm gives output that are identical and that tends to be disturbing, and insecure.
The recently designed hash functions used in the blockchain technology are said to be more efficiently designed such that they are collision-resistant and prevent the occurrence of same hash output for two separate inputs. Notably, SHA-2 (which includes SHA 224, SHA 256, SHA 384 and SHA 512) hashing function are said to be hash functions technology that has proven to be very efficient in resisting collision and as such prevent identical outputs from different inputs' background.
When the cryptographic hash function is resistance to collision then it becomes impossible/hard to find an identical outputs and as such, prevents
frivolous swapping of original hash for the fake one that can lead to confusion. Resistance to collision is an important context in cryptographic hash function to maintain the intactness of genuine inputs and outputs which remains unique for each transaction.
Points to ponder
Resistance to Preimage
Resistance to preimage is also a characteristics of the hash function that makes it computational impossible for attackers to find a matching input for the output hash. That's a big technology to talk about, this makes it hard for any attacker to alter the resulting hash of any transaction as it becomes impossible to fetch out the input that gave birth to the new hash output. Resistance to preimage in the hash function helps to secure the hash from likely attackers that might want to alter the hash by replacing it with fake ones.
Let's talk about the First preimage resistance as this attribute is referred to be one way function as it's impossible to invert it to get the inputs that give birth to the output' hash and this enhance the security of data stored in the hash while the Second preimage resistance ensure that it's impossible to find the output of another input to be identical to the first input.
Points to ponder
2. Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
For this section of the task, I will be exploring the duo of Tronscan and Etherscan to verify the hash of the last block and the hash of the transaction.
Verifying on Tronscan
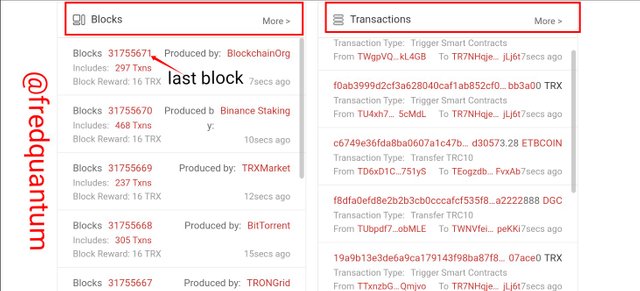
blocks and transactions
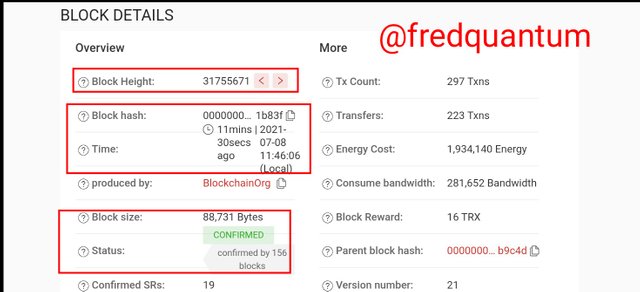
Block details
From the information given on the page uploaded above, the block hash is; 0000000001e48d973c9bd69eb3376179e667d3c2a80fb98d366605108461b83f.
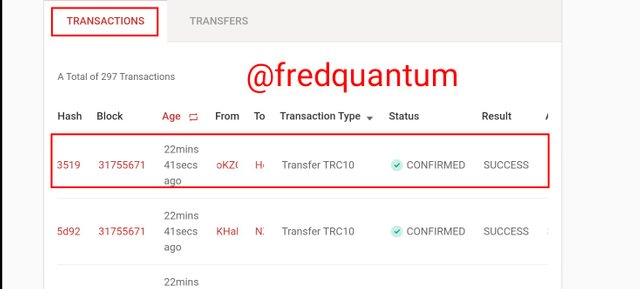
Transactions
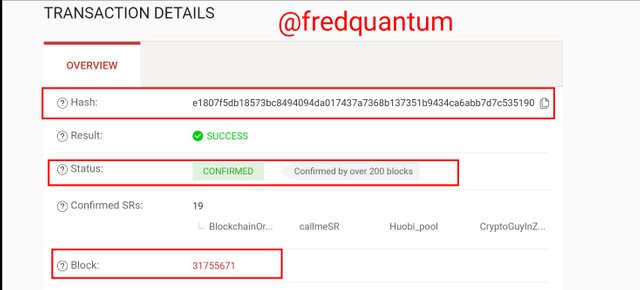
Transaction details
Verifying on Etherscan
The first step in the process of verifying the hash here is by visiting etherscan.io/ and locate the last block by scrolling down the page.
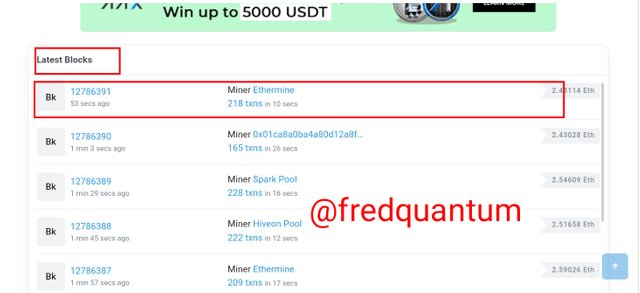
Latest block on Etherscan.io
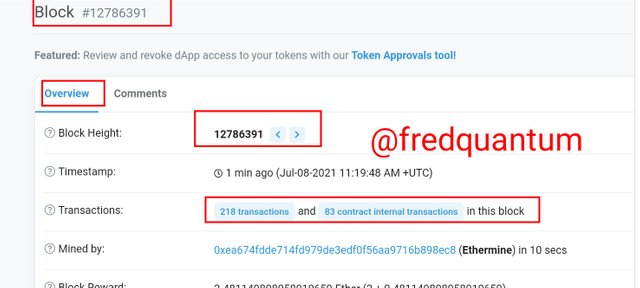
Overview of the block
Click to see more
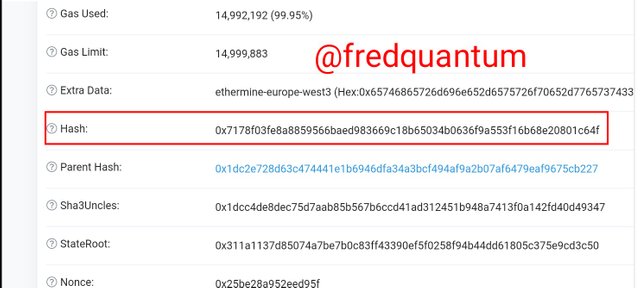
Block hash
Now to verify the hash of the last transaction, from the block overview page, I located transactions and clicked on it.
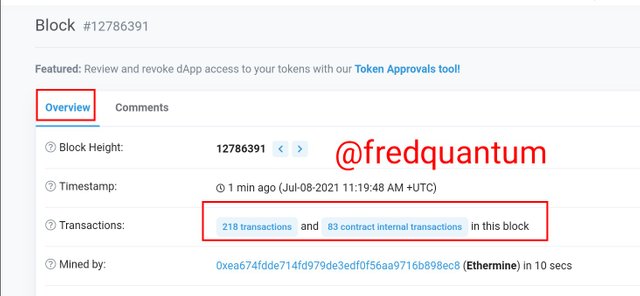
Transactions
I selected the last transaction on the list and the details like hash, addresses involved, block height, time of the transaction, transaction type and so on, were revealed.
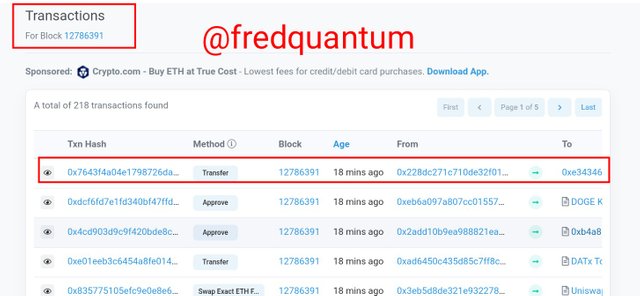
Transactions
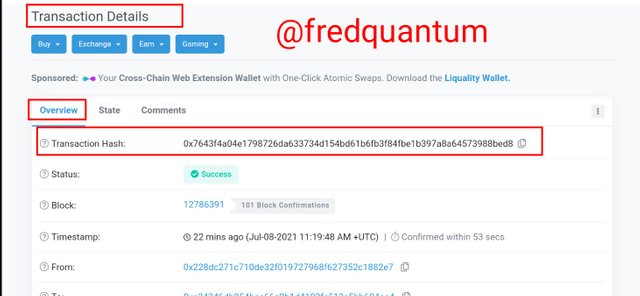
Transaction details

3. Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
The passwordsgenerator landing page
For the word- CryptoAcademy
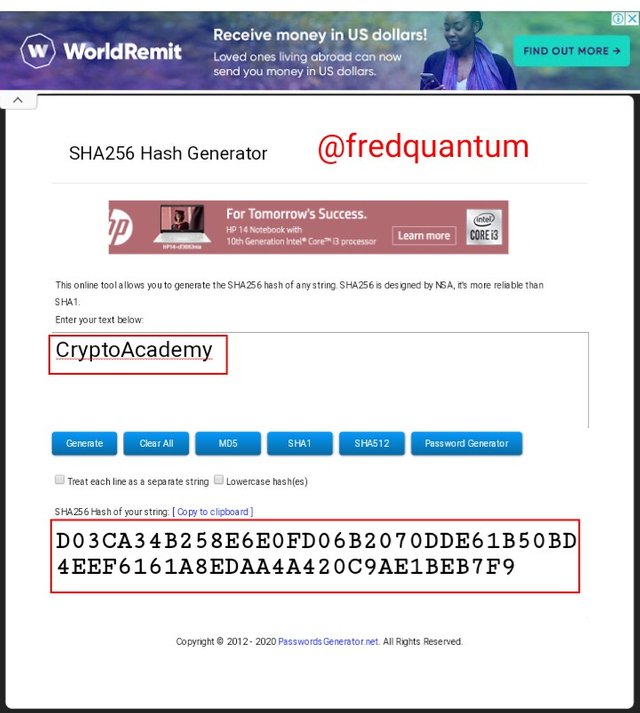
SHA-256 hash for the word "CryptoAcademy"
For the word- cryptoacademy
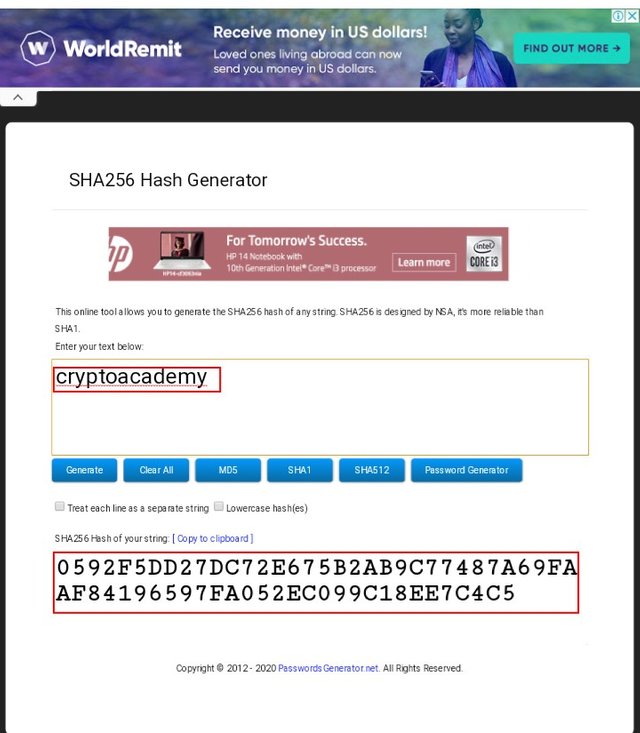
SHA-256 hash for the word "cryptoacademy"
Observations

4. In your own words explain the difference between hash and cryptography
The differences between the duo of hash and cryptography would be given in the list below;

Conclusion
In conclusion, the hash function is a one-way function which securely store data which cannot be reversed or replaced with fake ones while we see cryptography as the secured means of communication to exclude certain set of people from seeing the conversation.
It is also very important to know that, the input matters in hashing as different inputs produce different outputs, an attribute that can be credited to its one-way function while the input in cryptography remains visible at the destination using the designated key. Thanks to professor @pelon53 for this awesome lecture.

Cc: @pelon53

Written by;
@fredquantum
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Buen trabajo, felicitaciones.
Calificación: 10.0
Thanks for the review professor @pelon53. I'm so glad that I participated in the lecture, it adds a whole lot to me. Thank you.
Dear @steemcurator02, please I am missing out your curation on this post as I've only been rewarded by steemcurator01 for making the top 3 for this course. Thank you.